EAPOL on:
[Wikipedia]
[Google]
[Amazon]
IEEE 802.1X is an
 # Initialization On detection of a new supplicant, the port on the switch (authenticator) is enabled and set to the "unauthorized" state. In this state, only 802.1X traffic is allowed; other traffic, such as the
# Initialization On detection of a new supplicant, the port on the switch (authenticator) is enabled and set to the "unauthorized" state. In this state, only 802.1X traffic is allowed; other traffic, such as the
IEEE page on 802.1X
GetIEEE802 Download 802.1X-2020
GetIEEE802 Download 802.1X-2010
GetIEEE802 Download 802.1X-2004
GetIEEE802 Download 802.1X-2001
Ultimate wireless security guide: Self-signed certificates for your RADIUS server
WIRE1x
Wired Networking with 802.1X Authentication
on Microsoft TechNet {{IEEE standards IEEE 802.01x Networking standards Computer access control protocols Computer network security
IEEE Standard
The Institute of Electrical and Electronics Engineers Standards Association (IEEE SA) is an operating unit within IEEE that develops global standards in a broad range of industries, including: power and energy, artificial intelligence systems, ...
for port-based network access control
Network access control (NAC) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host intrusion prevention, and vulnerability assessment), user or system authentication and network security ...
(PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with iden ...
mechanism to devices wishing to attach to a LAN
Lan or LAN may refer to:
Science and technology
* Local asymptotic normality, a fundamental property of regular models in statistics
* Longitude of the ascending node, one of the orbital elements used to specify the orbit of an object in space
* ...
or WLAN
A wireless LAN (WLAN) is a wireless computer network that links two or more devices using wireless communication to form a local area network (LAN) within a limited area such as a home, school, computer laboratory, campus, or office buildin ...
.
The standard directly addresses an attack technique called Hardware Addition where an attacker posing as a guest, customer or staff smuggles a hacking device into the building that they then plug into the network giving them full access. A notable example of the issue occurred in 2005 when a machine attached to Walmart
Walmart Inc. (; formerly Wal-Mart Stores, Inc.) is an American multinational retail corporation that operates a chain of hypermarkets (also called supercenters), discount department stores, and grocery stores in the United States and 23 other ...
's network hacked thousands of their servers.
IEEE 802.1X defines the encapsulation of the Extensible Authentication Protocol
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by .
EAP is an authentication framework for providing the transport ...
(EAP) over wired IEEE 802
IEEE 802 is a family of Institute of Electrical and Electronics Engineers (IEEE) standards for local area networks (LANs), personal area networks (PANs), and metropolitan area networks (MANs). The IEEE 802 LAN/MAN Standards Committee (LMSC) main ...
networks and over 802.11 wireless networks, which is known as "EAP over LAN" or EAPOL. EAPOL was originally specified for IEEE 802.3
IEEE 802.3 is a working group and a collection of standards defining the physical layer and data link layer's media access control (MAC) of wired Ethernet. The standards are produced by the working group of the Institute of Electrical and Electro ...
Ethernet, IEEE 802.5
Token Ring is a Physical layer, physical and data link layer computer networking technology used to build local area networks. It was introduced by IBM in 1984, and standardized in 1989 as IEEE Standards Association, IEEE 802.5. It uses a sp ...
Token Ring, and FDDI
Fiber Distributed Data Interface (FDDI) is a standard for data transmission in a local area network.
It uses optical fiber as its standard underlying physical medium.
It was also later specified to use copper cable, in which case it may be c ...
(ANSI X3T9.5/X3T12 and ISO 9314) in 802.1X-2001, but was extended to suit other IEEE 802 LAN technologies such as IEEE 802.11
IEEE 802.11 is part of the IEEE 802 set of local area network (LAN) technical standards, and specifies the set of medium access control (MAC) and physical layer (PHY) protocols for implementing wireless local area network (WLAN) computer com ...
wireless in 802.1X-2004. The EAPOL was also modified for use with IEEE 802.1AE ("MACsec") and IEEE 802.1AR (Secure Device Identity, DevID) in 802.1X-2010IEEE 802.1X-2010, page ivIEEE 802.1X-2010, § 5 to support service identification and optional point to point encryption over the internal LAN segment. 802.1X is part of the logical link control
In the IEEE 802 reference model of computer networking, the logical link control (LLC) data communication protocol layer is the upper sublayer of the data link layer (layer 2) of the seven-layer OSI model. The LLC sublayer acts as an interface ...
(LLC) sublayer of the 802 reference model.
Overview
802.1X authentication involves three parties: a supplicant, an authenticator, and an authentication server. The supplicant is aclient
Client(s) or The Client may refer to:
* Client (business)
* Client (computing), hardware or software that accesses a remote service on another computer
* Customer or client, a recipient of goods or services in return for monetary or other valuable ...
device (such as a laptop) that wishes to attach to the LAN/WLAN. The term 'supplicant' is also used interchangeably to refer to the software running on the client that provides credentials to the authenticator. The authenticator
An authenticator is a means used to confirm a user's identity, that is, to perform digital authentication. A person authenticates to a computer system or application by demonstrating that he or she has possession and control of an authenticator. I ...
is a network device that provides a data link between the client and the network and can allow or block network traffic between the two, such as an Ethernet switch
A network switch (also called switching hub, bridging hub, Ethernet switch, and, by the IEEE, MAC bridge) is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destinat ...
or wireless access point
In Computer networking device, computer networking, a wireless access point (WAP) (also just access point (AP)) is a networking hardware device that allows other Wi-Fi devices to connect to a wired network or wireless network. As a standalone ...
; and the authentication server is typically a trusted server that can receive and respond to requests for network access, and can tell the authenticator if the connection is to be allowed, and various settings that should apply to that client's connection or setting. Authentication servers typically run software supporting the RADIUS
In classical geometry, a radius (: radii or radiuses) of a circle or sphere is any of the line segments from its Centre (geometry), center to its perimeter, and in more modern usage, it is also their length. The radius of a regular polygon is th ...
and EAP protocols. In some cases, the authentication server software may be running on the authenticator hardware.
The authenticator acts like a security guard to a protected network. The supplicant (i.e., client device) is not allowed access through the authenticator to the protected side of the network until the supplicant's identity has been validated and authorized. With 802.1X port-based authentication, the supplicant must initially provide the required credentials to the authenticator - these will have been specified in advance by the network administrator and could include a user name/password or a permitted digital certificate
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a public key. The certificate includes the public key and information about it, informa ...
. The authenticator forwards these credentials to the authentication server to decide whether access is to be granted. If the authentication server determines the credentials are valid, it informs the authenticator, which in turn allows the supplicant (client device) to access resources located on the protected side of the network.
Protocol operation
EAPOL operates over thedata link layer
The data link layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. The data link layer p ...
, and in Ethernet II framing
In computer networking, an Ethernet frame is a data link layer protocol data unit and uses the underlying Ethernet physical layer transport mechanisms. In other words, a data unit on an Ethernet link transports an Ethernet frame as its payload ...
protocol has an EtherType
EtherType is a two- octet field in an Ethernet frame. It is used to indicate which protocol is encapsulated in the payload of the frame and is used at the receiving end by the data link layer to determine how the payload is processed. The same ...
value of 0x888E.
Port entities
802.1X-2001 defines two logical port entities for an authenticated port—the "controlled port" and the "uncontrolled port". The controlled port is manipulated by the 802.1X PAE (Port Access Entity) to allow (in the authorized state) or prevent (in the unauthorized state) network traffic ingress and egress to/from the controlled port. The uncontrolled port is used by the 802.1X PAE to transmit and receive EAPOL frames. 802.1X-2004 defines the equivalent port entities for the supplicant; so a supplicant implementing 802.1X-2004 may prevent higher-level protocols from being used if it is not content that authentication has successfully completed. This is particularly useful when an EAP method providingmutual authentication
Mutual authentication or two-way authentication (not to be confused with two-factor authentication) refers to two parties authenticating each other at the same time in an authentication protocol. It is a default mode of authentication in some prot ...
is used, as the supplicant can prevent data leakage when connected to an unauthorized network.
Typical authentication progression
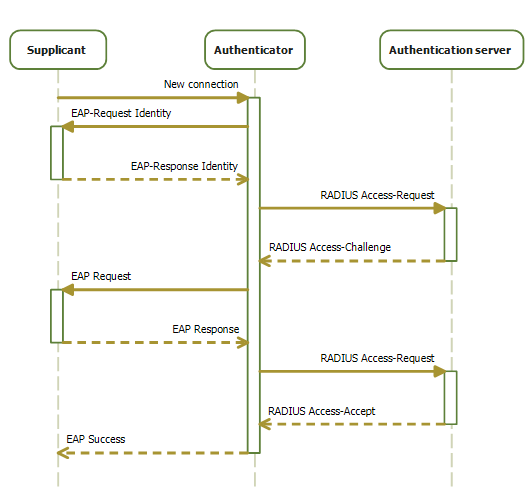
The typical authentication procedure consists of: # Initialization On detection of a new supplicant, the port on the switch (authenticator) is enabled and set to the "unauthorized" state. In this state, only 802.1X traffic is allowed; other traffic, such as the
# Initialization On detection of a new supplicant, the port on the switch (authenticator) is enabled and set to the "unauthorized" state. In this state, only 802.1X traffic is allowed; other traffic, such as the Internet Protocol
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet.
IP ...
(and with that TCP and UDP), is dropped.
# Initiation To initiate authentication the authenticator will periodically transmit EAP-Request Identity frames to a special Layer 2 MAC address
A MAC address (short for medium access control address or media access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use i ...
() on the local network segment. The supplicant listens at this address, and on receipt of the EAP-Request Identity frame, it responds with an EAP-Response Identity frame containing an identifier for the supplicant such as a User ID. The authenticator then encapsulates this Identity response in a RADIUS
In classical geometry, a radius (: radii or radiuses) of a circle or sphere is any of the line segments from its Centre (geometry), center to its perimeter, and in more modern usage, it is also their length. The radius of a regular polygon is th ...
Access-Request packet and forwards it on to the authentication server. The supplicant may also initiate or restart authentication by sending an EAPOL-Start frame to the authenticator, which will then reply with an EAP-Request Identity frame.''
# Negotiation ''(Technically EAP negotiation)'' The authentication server sends a reply (encapsulated in a RADIUS
In classical geometry, a radius (: radii or radiuses) of a circle or sphere is any of the line segments from its Centre (geometry), center to its perimeter, and in more modern usage, it is also their length. The radius of a regular polygon is th ...
Access-Challenge packet) to the authenticator, containing an EAP Request specifying the EAP Method (The type of EAP based authentication it wishes the supplicant to perform). The authenticator encapsulates the EAP Request in an EAPOL frame and transmits it to the supplicant. At this point, the supplicant can start using the requested EAP Method, or do a NAK ("Negative Acknowledgement") and respond with the EAP Methods it is willing to perform.
# Authentication If the authentication server and supplicant agree on an EAP Method, EAP Requests and Responses are sent between the supplicant and the authentication server (translated by the authenticator) until the authentication server responds with either an EAP-Success message (encapsulated in a RADIUS
In classical geometry, a radius (: radii or radiuses) of a circle or sphere is any of the line segments from its Centre (geometry), center to its perimeter, and in more modern usage, it is also their length. The radius of a regular polygon is th ...
Access-Accept packet), or an EAP-Failure message (encapsulated in a RADIUS
In classical geometry, a radius (: radii or radiuses) of a circle or sphere is any of the line segments from its Centre (geometry), center to its perimeter, and in more modern usage, it is also their length. The radius of a regular polygon is th ...
Access-Reject packet). If authentication is successful, the authenticator sets the port to the "authorized" state and normal traffic is allowed. If it is unsuccessful, the port remains in the "unauthorized" state. When the supplicant logs off, it sends an EAPOL-logoff message to the authenticator, the authenticator then sets the port to the "unauthorized" state, once again blocking all non-EAP traffic.
Implementations
An open-source project named Open1X produces a client, Xsupplicant. This client is currently available for both Linux and Windows. The main drawbacks of the Open1X client are that it does not provide comprehensible and extensive user documentation and that most Linux vendors do not provide a package for it. The more general wpa_supplicant can be used for802.11
IEEE 802.11 is part of the IEEE 802 set of local area network (LAN) technical standards, and specifies the set of medium access control (MAC) and physical layer (PHY) protocols for implementing wireless local area network (WLAN) computer c ...
wireless networks and wired networks. Both support a very wide range of EAP types.
The iPhone
The iPhone is a line of smartphones developed and marketed by Apple that run iOS, the company's own mobile operating system. The first-generation iPhone was announced by then–Apple CEO and co-founder Steve Jobs on January 9, 2007, at ...
and iPod Touch
The iPod Touch (stylized as iPod touch) is a discontinued line of iOS-based mobile devices designed and formerly marketed by Apple Inc. with a touchscreen-controlled user interface. As with other iPod models, the iPod Touch can be used as a po ...
support 802.1X since the release of iOS
Ios, Io or Nio (, ; ; locally Nios, Νιός) is a Greek island in the Cyclades group in the Aegean Sea. Ios is a hilly island with cliffs down to the sea on most sides. It is situated halfway between Naxos and Santorini. It is about long an ...
2.0.
Android has support for 802.1X since the release of 1.6 Donut.
ChromeOS
ChromeOS, sometimes styled as chromeOS and formerly styled as Chrome OS, is an operating system designed and developed by Google. It is derived from the open-source operating system and uses the Google Chrome web browser as its principal user ...
has supported 802.1X since mid-2011.
macOS
macOS, previously OS X and originally Mac OS X, is a Unix, Unix-based operating system developed and marketed by Apple Inc., Apple since 2001. It is the current operating system for Apple's Mac (computer), Mac computers. With ...
has offered native support since 10.3.
Avenda Systems provides a supplicant for Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sec ...
, Linux
Linux ( ) is a family of open source Unix-like operating systems based on the Linux kernel, an kernel (operating system), operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically package manager, pac ...
and macOS
macOS, previously OS X and originally Mac OS X, is a Unix, Unix-based operating system developed and marketed by Apple Inc., Apple since 2001. It is the current operating system for Apple's Mac (computer), Mac computers. With ...
. They also have a plugin for the Microsoft NAP
A nap is a short period of sleep, typically taken during daytime hours as an adjunct to the usual nocturnal sleep period. Naps are most often taken as a response to Somnolence, drowsiness during waking hours or as a means to supplement before ...
framework. Avenda also offers health checking agents.
Windows
Windows defaults to not responding to 802.1X authentication requests for 20 minutes after a failed authentication. This can cause significant disruption to clients. The block period can be configured using the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\dot3svc\BlockTime DWORD value (HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\wlansvc\BlockTime for wireless networks) in the registry (entered in minutes). Ahotfix
A hotfix is a software update that is released outside the normal update cycle or intended to be applied to a live system; often to fix a bug.
Originally, ''hotfix'' referred to patching a ''hot'' system a production server that is actively ser ...
is required for Windows XP SP3 and Windows Vista SP2 to make the period configurable.
Wildcard server certificates are not supported by EAPHost, the Windows component that provides EAP support in the operating system. The implication of this is that when using a commercial certification authority, individual certificates must be purchased.
Windows XP
Windows XP has major issues with its handling of IP address changes resulting from user-based 802.1X authentication that changes the VLAN and thus subnet of clients. Microsoft has stated that it will not backport the SSO feature from Vista that resolves these issues. If users are not logging in with roaming profiles, a hotfix must be downloaded and installed if authenticating via PEAP with PEAP-MSCHAPv2.Windows Vista
Windows Vista-based computers that are connected via an IP phone may not authenticate as expected and, as a result, the client can be placed into the wrong VLAN. A hotfix is available to correct this.Windows 7
Windows 7 based computers that are connected via an IP phone may not authenticate as expected and, consequently, the client can be placed into the wrong VLAN. A hotfix is available to correct this. Windows 7 does not respond to 802.1X authentication requests after initial 802.1X authentication fails. This can cause significant disruption to clients. A hotfix is available to correct this.Windows PE
Windows PE
Windows Preinstallation Environment (also known as Windows PE and WinPE) is a lightweight version of Windows used for the deployment of PCs, workstations, and servers, or troubleshooting an operating system while it is offline. It is intended t ...
does not have native support for 802.1X. However, support can be added to WinPE 2.1 and WinPE 3.0 through hotfixes that are available from Microsoft. Although full documentation is not yet available, preliminary documentation for the use of these hotfixes is available via a Microsoft blog.
Linux
MostLinux distribution
A Linux distribution, often abbreviated as distro, is an operating system that includes the Linux kernel for its kernel functionality. Although the name does not imply product distribution per se, a distro—if distributed on its own—is oft ...
s support 802.1X via wpa_supplicant and desktop integration like NetworkManager
NetworkManager is a daemon that sits on top of libudev and other Linux kernel interfaces (and a couple of other daemons) and provides a high-level interface for the configuration of the network interfaces.
Rationale
NetworkManager is a software ...
.
Apple devices
As ofiOS 17
iOS 17 is the seventeenth major release of Apple's iOS operating system for the iPhone. It is the direct successor to iOS 16. It was announced on June 5, 2023, at Apple's annual Worldwide Developers Conference alongside watchOS 10, iPadOS 1 ...
and macOS 14, Apple devices support connecting to 802.1X networks using EAP-TLS
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by .
EAP is an authentication framework for providing the transport ...
with TLS 1.3 (EAP-TLS 1.3). Additionally, devices running iOS/iPadOS/tvOS 17 or later support wired 802.1X networks.
Federations
eduroam
eduroam (''edu''cation ''roam''ing) is an international Wi-Fi internet access roaming service for users in research, higher education and further education. It provides researchers, teachers, and students network access when visiting an institut ...
(the international roaming service), mandates the use of 802.1X authentication when providing network access to guests visiting from other eduroam-enabled institutions.
BT (British Telecom, PLC) employs Identity Federation for authentication in services delivered to a wide variety of industries and governments.
Proprietary extensions
MAB (MAC Authentication Bypass)
Not all devices support 802.1X authentication. Examples include network printers, Ethernet-based electronics like environmental sensors, cameras, and wireless phones. For those devices to be used in a protected network environment, alternative mechanisms must be provided to authenticate them. One option would be to disable 802.1X on that port, but that leaves that port unprotected and open for abuse. Another slightly more reliable option is to use the MAB option. When MAB is configured on a port, that port will first try to check if the connected device is 802.1X compliant, and if no reaction is received from the connected device, it will try to authenticate with the AAA server using the connected device'sMAC address
A MAC address (short for medium access control address or media access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use i ...
as username and password. The network administrator then must make provisions on the RADIUS
In classical geometry, a radius (: radii or radiuses) of a circle or sphere is any of the line segments from its Centre (geometry), center to its perimeter, and in more modern usage, it is also their length. The radius of a regular polygon is th ...
server to authenticate those MAC addresses, either by adding them as regular users or implementing additional logic to resolve them in a network inventory database.
Many managed Ethernet switches offer options for this.
Vulnerabilities in 802.1X-2001 and 802.1X-2004
Shared media
In the summer of 2005, Microsoft's Steve Riley posted an article (based on the original research of Microsoft MVP Svyatoslav Pidgorny) detailing a serious vulnerability in the 802.1X protocol, involving aman in the middle attack
In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communi ...
. In summary, the flaw stems from the fact that 802.1X authenticates only at the beginning of the connection, but after that authentication, it's possible for an attacker to use the authenticated port if they have the ability to physically insert themselves (perhaps using a workgroup hub) between the authenticated computer and the port. Riley suggests that for wired networks the use of IPsec or a combination of IPsec and 802.1X would be more secure.
EAPOL-Logoff frames transmitted by the 802.1X supplicant are sent in the clear and contain no data derived from the credential exchange that initially authenticated the client. They are therefore trivially easy to spoof on shared media and can be used as part of a targeted DoS
DOS (, ) is a family of disk-based operating systems for IBM PC compatible computers. The DOS family primarily consists of IBM PC DOS and a rebranded version, Microsoft's MS-DOS, both of which were introduced in 1981. Later compatible syste ...
on both wired and wireless LANs. In an EAPOL-Logoff attack a malicious third party, with access to the medium the authenticator is attached to, repeatedly sends forged EAPOL-Logoff frames from the target device's MAC Address. The authenticator (believing that the targeted device wishes to end its authentication session) closes the target's authentication session, blocking traffic ingressing from the target, denying it access to the network.
The 802.1X-2010 specification, which began as 802.1af, addresses vulnerabilities in previous 802.1X specifications, by using MACsec IEEE 802.1AE to encrypt data between logical ports (running on top of a physical port) and IEEE 802.1AR (Secure Device Identity / DevID) authenticated devices.IEEE 802.1X-2010, § 5
As a stopgap, until these enhancements are widely implemented, some vendors have extended the 802.1X-2001 and 802.1X-2004 protocol, allowing multiple concurrent authentication sessions to occur on a single port. While this prevents traffic from devices with unauthenticated MAC addresses ingressing on an 802.1X authenticated port, it will not stop a malicious device snooping on traffic from an authenticated device and provides no protection against MAC spoofing, or EAPOL-Logoff attacks.
Alternatives
TheIETF
The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster ...
-backed alternative is the Protocol for Carrying Authentication for Network Access (PANA), which also carries EAP, although it works at layer 3, using UDP, thus not being tied to the 802 infrastructure.
See also
* AEGIS SecureConnect * IEEE 802.11i-2004References
External links
IEEE page on 802.1X
GetIEEE802 Download 802.1X-2020
GetIEEE802 Download 802.1X-2010
GetIEEE802 Download 802.1X-2004
GetIEEE802 Download 802.1X-2001
Ultimate wireless security guide: Self-signed certificates for your RADIUS server
WIRE1x
Wired Networking with 802.1X Authentication
on Microsoft TechNet {{IEEE standards IEEE 802.01x Networking standards Computer access control protocols Computer network security