Bullrun (decryption program) on:
[Wikipedia]
[Google]
[Amazon]
Bullrun (stylized BULLRUN) is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States
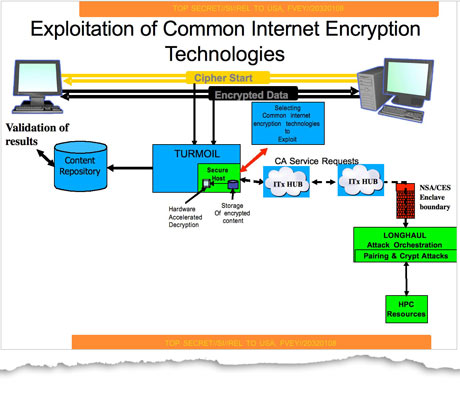 Through the NSA-designed Clipper chip, which used the Skipjack cipher with an intentional backdoor, and using various specifically designed laws such as CALEA, CESA and restrictions on export of encryption software as evidenced by '' Bernstein v. United States'', the U.S. government had publicly attempted in the 1990s to ensure its access to communications and ability to decrypt. In particular, technical measures such as key escrow, a euphemism for a backdoor, have met with criticism and little success.
The NSA encourages the manufacturers of security technology to disclose backdoors to their products or encryption keys so that they may access the encrypted data. However, fearing widespread adoption of encryption, the NSA set out to stealthily influence and weaken encryption standards and obtain master keys—either by agreement, by force of law, or by computer network exploitation ( hacking).
According to a Bullrun briefing document, the agency had successfully infiltrated both the
Through the NSA-designed Clipper chip, which used the Skipjack cipher with an intentional backdoor, and using various specifically designed laws such as CALEA, CESA and restrictions on export of encryption software as evidenced by '' Bernstein v. United States'', the U.S. government had publicly attempted in the 1990s to ensure its access to communications and ability to decrypt. In particular, technical measures such as key escrow, a euphemism for a backdoor, have met with criticism and little success.
The NSA encourages the manufacturers of security technology to disclose backdoors to their products or encryption keys so that they may access the encrypted data. However, fearing widespread adoption of encryption, the NSA set out to stealthily influence and weaken encryption standards and obtain master keys—either by agreement, by force of law, or by computer network exploitation ( hacking).
According to a Bullrun briefing document, the agency had successfully infiltrated both the
Crucial Unanswered Questions about the NSA's BULLRUN Program
John Gilmore * https://www.cs.auckland.ac.nz/~pgut001/pubs/crypto_wont_help.pdf American secret government programs Mass surveillance National Security Agency operations GCHQ operations Intelligence agency programmes revealed by Edward Snowden Encryption debate
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and proces ...
(NSA). The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the Bullrun classification guide published by ''The Guardian
''The Guardian'' is a British daily newspaper. It was founded in Manchester in 1821 as ''The Manchester Guardian'' and changed its name in 1959, followed by a move to London. Along with its sister paper, ''The Guardian Weekly'', ''The Guardi ...
'', the program uses multiple methods including computer network exploitation, interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques.
Information about the program's existence was leaked in 2013 by Edward Snowden
Edward Joseph Snowden (born June 21, 1983) is a former National Security Agency (NSA) intelligence contractor and whistleblower who leaked classified documents revealing the existence of global surveillance programs.
Born in 1983 in Elizabeth ...
. Although Snowden's documents do not contain technical information on exact cryptanalytic capabilities because Snowden did not have clearance access to such information, they do contain a 2010 GCHQ
Government Communications Headquarters (GCHQ) is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the United Kingdom. Primar ...
presentation which claims that "vast amounts of encrypted Internet data which have up till now been discarded are now exploitable". A number of technical details regarding the program found in Snowden's documents were additionally censored by the press at the behest of US intelligence officials. Out of all the programs that have been leaked by Snowden, the Bullrun Decryption Program is by far the most expensive. Snowden claims that since 2011, expenses devoted to Bullrun amount to $800 million. The leaked documents reveal that Bullrun seeks to "defeat the encryption used in specific network communication technologies".
Naming and access
According to the NSA's Bullrun Classification Guide, Bullrun is not aSensitive Compartmented Information
Sensitive compartmented information (SCI) is a type of United States classified information concerning or derived from sensitive intelligence sources, methods, or analytical processes. All SCI must be handled within formal access control systems ...
(SCI) control system or compartment, but the codeword has to be shown in the classification line, after all other classification and dissemination markings. Furthermore, any details about specific cryptographic successes were recommended to be additionally restricted (besides being marked Top Secret// SI) with Exceptionally Controlled Information labels; a non-exclusive list of possible Bullrun ECI labels was given as: APERIODIC, AMBULANT, AUNTIE, PAINTEDEAGLE, PAWLEYS, PITCHFORD, PENDLETON, PICARESQUE, and PIEDMONT without any details as to what these labels mean.
Access to the program is limited to a group of top personnel at the Five Eyes (FVEY), the NSA and the signals intelligence
Signals intelligence (SIGINT) is the act and field of intelligence-gathering by interception of ''signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly u ...
agencies of the United Kingdom (GCHQ
Government Communications Headquarters (GCHQ) is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the United Kingdom. Primar ...
), Canada ( CSE), Australia ( ASD), and New Zealand ( GCSB). Signals that cannot be decrypted with current technology may be retained indefinitely while the agencies continue to attempt to decrypt them.
Methods
 Through the NSA-designed Clipper chip, which used the Skipjack cipher with an intentional backdoor, and using various specifically designed laws such as CALEA, CESA and restrictions on export of encryption software as evidenced by '' Bernstein v. United States'', the U.S. government had publicly attempted in the 1990s to ensure its access to communications and ability to decrypt. In particular, technical measures such as key escrow, a euphemism for a backdoor, have met with criticism and little success.
The NSA encourages the manufacturers of security technology to disclose backdoors to their products or encryption keys so that they may access the encrypted data. However, fearing widespread adoption of encryption, the NSA set out to stealthily influence and weaken encryption standards and obtain master keys—either by agreement, by force of law, or by computer network exploitation ( hacking).
According to a Bullrun briefing document, the agency had successfully infiltrated both the
Through the NSA-designed Clipper chip, which used the Skipjack cipher with an intentional backdoor, and using various specifically designed laws such as CALEA, CESA and restrictions on export of encryption software as evidenced by '' Bernstein v. United States'', the U.S. government had publicly attempted in the 1990s to ensure its access to communications and ability to decrypt. In particular, technical measures such as key escrow, a euphemism for a backdoor, have met with criticism and little success.
The NSA encourages the manufacturers of security technology to disclose backdoors to their products or encryption keys so that they may access the encrypted data. However, fearing widespread adoption of encryption, the NSA set out to stealthily influence and weaken encryption standards and obtain master keys—either by agreement, by force of law, or by computer network exploitation ( hacking).
According to a Bullrun briefing document, the agency had successfully infiltrated both the Secure Sockets Layer
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network, such as the Internet. The protocol is widely used in applications such as email, instant messaging, and voice over IP, ...
as well as some virtual private networks (VPNs). The ''New York Times'' reported that: "But by 2006, an N.S.A. document notes, the agency had broken into communications for three foreign airlines, one travel reservation system, one foreign government's nuclear department and another's Internet service by cracking the virtual private networks that protected them. By 2010, the Edgehill program, the British counterencryption effort, was unscrambling VPN traffic for 30 targets and had set a goal of an additional 300."
As part of Bullrun, NSA has also been actively working to "Insert vulnerabilities into commercial encryption systems, IT systems, networks, and endpoint communications devices used by targets". ''The New York Times'' has reported that the random number generator Dual_EC_DRBG
Dual_EC_DRBG (Dual Elliptic Curve Deterministic Random Bit Generator) is an algorithm that was presented as a cryptographically secure pseudorandom number generator (CSPRNG) using methods in elliptic curve cryptography. Despite wide public criti ...
contains a back door, which would allow the NSA to break encryption keys generated by the random number generator. Even though this random number generator was known to be insecure and slow soon after the standard was published, and a potential NSA kleptographic backdoor was found in 2007 while alternative random number generators without these flaws were certified and widely available, RSA Security
RSA Security LLC, formerly RSA Security, Inc. and trade name RSA, is an American computer security, computer and network security company with a focus on encryption and decryption standards. RSA was named after the initials of its co-founders, ...
continued using Dual_EC_DRBG in the company's BSAFE toolkit and Data Protection Manager until September 2013. While RSA Security has denied knowingly inserting a backdoor into BSAFE, it has not yet given an explanation for the continued usage of Dual_EC_DRBG after its flaws became apparent in 2006 and 2007. It was reported on December 20, 2013, that RSA had accepted a payment of $10 million from the NSA to set the random number generator as the default. Leaked NSA documents state that their effort was “a challenge in finesse” and that “Eventually, N.S.A. became the sole editor” of the standard.
By 2010, the leaked documents state that the NSA had developed "groundbreaking capabilities" against encrypted Internet traffic. A GCHQ document warned however "These capabilities are among the SIGINT
Signals intelligence (SIGINT) is the act and field of intelligence-gathering by interception of ''signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly u ...
community's most fragile, and the inadvertent disclosure of the simple 'fact of' could alert the adversary and result in immediate loss of the capability." The document later states that "there will be NO 'need to know
The term "need to know" (alternatively spelled need-to-know), when used by governments and other organizations (particularly those related to military or intelligence), describes the restriction of data which is considered very confidential and ...
.'" Several experts, including Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is an Adjunct Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman ...
and Christopher Soghoian, had speculated that a successful attack against RC4, an encryption algorithm used in at least 50 percent of all SSL/TLS traffic at the time, was a plausible avenue, given several publicly known weaknesses of RC4. Others have speculated that NSA has gained ability to crack 1024-bit RSA/ DH keys. RC4 has since been prohibited for all versions of TLS by RFC 7465 in 2015, due to the RC4 attacks weakening or breaking RC4 used in SSL/TLS.
Fallout
In the wake of Bullrun revelations, some open source projects, includingFreeBSD
FreeBSD is a free-software Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version was released in 1993 developed from 386BSD, one of the first fully functional and free Unix clones on affordable ...
and OpenSSL
OpenSSL is a software library for applications that provide secure communications over computer networks against eavesdropping, and identify the party at the other end. It is widely used by Internet servers, including the majority of HTTPS web ...
, have seen an increase in their reluctance to (fully) trust hardware-based cryptographic primitive Cryptographic primitives are well-established, low-level cryptography, cryptographic algorithms that are frequently used to build cryptographic protocols for computer security systems. These routines include, but are not limited to, one-way hash fun ...
s.
Many other software projects, companies and organizations responded with an increase in the evaluation of their security and encryption processes. For example, Google doubled the size of their TLS certificates from 1024 bits to 2048 bits.
Revelations of the NSA backdoors and purposeful complication of standards has led to a backlash in their participation in standards bodies. Prior to the revelations the NSA's presence on these committees was seen as a benefit given their expertise with encryption.
There has been speculation that the NSA was aware of the Heartbleed
Heartbleed is a security bug in some outdated versions of the OpenSSL cryptography library, which is a widely used implementation of the Transport Layer Security (TLS) protocol. It was introduced into the software in 2012 and publicly disclos ...
bug, which caused major websites to be vulnerable to password theft, but did not reveal this information in order to exploit it themselves.
Etymology
The name "Bullrun" was taken from theFirst Battle of Bull Run
The First Battle of Bull Run, called the Battle of First Manassas
. by Confederate States ...
, the first major battle of the . by Confederate States ...
American Civil War
The American Civil War (April 12, 1861May 26, 1865; also known by Names of the American Civil War, other names) was a civil war in the United States between the Union (American Civil War), Union ("the North") and the Confederate States of A ...
. Its predecessor "Manassas", is both an alternate name for the battle and where the battle took place. "EDGEHILL" is from the Battle of Edgehill
The Battle of Edgehill (or Edge Hill) was a pitched battle of the First English Civil War. It was fought near Edge Hill, Warwickshire, Edge Hill and Kineton in southern Warwickshire on Sunday, 23 October 1642.
All attempts at constitution ...
, the first battle of the English Civil War
The English Civil War or Great Rebellion was a series of civil wars and political machinations between Cavaliers, Royalists and Roundhead, Parliamentarians in the Kingdom of England from 1642 to 1651. Part of the wider 1639 to 1653 Wars of th ...
.
See also
*HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It uses encryption for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protoc ...
* IPsec
* Mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by Local government, local and federal governments or intell ...
** Mass surveillance in the United Kingdom
The use of electronic surveillance by the United Kingdom grew from the development of signal intelligence and pioneering code breaking during World War II. In the post-war period, the Government Communications Headquarters (GCHQ) was formed a ...
** Mass surveillance in the United States
The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveill ...
* MUSCULAR
MUSCULAR (DS-200B), located in the United Kingdom, is the name of a surveillance program jointly operated by Britain's Government Communications Headquarters (GCHQ) and the U.S. National Security Agency (NSA) that was revealed by documents release ...
* PRISM
PRISM is a code name for a program under which the United States National Security Agency (NSA) collects internet communications from various U.S. internet companies. The program is also known by the SIGAD . PRISM collects stored internet ...
* Tailored Access Operations
The Office of Tailored Access Operations (TAO), structured as S32, is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA). It has been active since at least 1998, possibly 1997, but was not named or structured as ...
* Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network, such as the Internet. The protocol is widely used in applications such as email, instant messaging, and voice over ...
* Voice over IP
Voice over Internet Protocol (VoIP), also known as IP telephony, is a set of technologies used primarily for voice communication sessions over Internet Protocol (IP) networks, such as the Internet. VoIP enables voice calls to be transmitted as ...
References
{{reflist, 30emExternal links
Crucial Unanswered Questions about the NSA's BULLRUN Program
John Gilmore * https://www.cs.auckland.ac.nz/~pgut001/pubs/crypto_wont_help.pdf American secret government programs Mass surveillance National Security Agency operations GCHQ operations Intelligence agency programmes revealed by Edward Snowden Encryption debate