|
Information-theoretic Security
A cryptosystem is considered to have information-theoretic security (also called unconditional security) if the system is secure against adversaries with unlimited computing resources and time. In contrast, a system which depends on the computational cost of cryptanalysis to be secure (and thus can be broken by an attack with unlimited computation) is called computationally, or conditionally, secure. Overview An encryption protocol with information-theoretic security is impossible to break even with infinite computational power. Protocols proven to be information-theoretically secure are resistant to future developments in computing. The concept of information-theoretically secure communication was introduced in 1949 by American mathematician Claude Shannon, one of the founders of classical information theory, who used it to prove the one-time pad system was secure. Information-theoretically secure cryptosystems have been used for the most sensitive governmental communications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptosystem
In cryptography, a cryptosystem is a suite of cryptographic algorithms needed to implement a particular security service, such as confidentiality (encryption). Typically, a cryptosystem consists of three algorithms: one for key generation, one for encryption, and one for decryption. The term ''cipher'' (sometimes ''cypher'') is often used to refer to a pair of algorithms, one for encryption and one for decryption. Therefore, the term ''cryptosystem'' is most often used when the key generation algorithm is important. For this reason, the term ''cryptosystem'' is commonly used to refer to public key techniques; however both "cipher" and "cryptosystem" are used for symmetric key techniques. Formal definition Mathematically, a cryptosystem or encryption scheme can be defined as a tuple (\mathcal,\mathcal,\mathcal,\mathcal,\mathcal) with the following properties. # \mathcal is a set called the "plaintext space". Its elements are called plaintexts. # \mathcal is a set called th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aaron D
According to Abrahamic religions, Aaron ''′aharon'', ar, هارون, Hārūn, Greek (Septuagint): Ἀαρών; often called Aaron the priest ()., group="note" ( or ; ''’Ahărōn'') was a prophet, a high priest, and the elder brother of Moses. Knowledge of Aaron, along with his brother Moses, exclusively comes from religious texts, such as the Hebrew Bible, Bible and the Quran. The Hebrew Bible relates that, unlike Moses, who grew up in the Egyptian royal court, Aaron and his elder sister Miriam remained with their kinsmen in the eastern border-land of Egypt ( Goshen). When Moses first confronted the Egyptian king about the enslavement of the Israelites, Aaron served as his brother's spokesman ("prophet") to the Pharaoh (). Part of the Law given to Moses at Sinai granted Aaron the priesthood for himself and his male descendants, and he became the first High Priest of the Israelites. Aaron died before the Israelites crossed the Jordan river. According to the Book of Numbe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pre-shared Key
In cryptography, a pre-shared key (PSK) is a shared secret which was previously shared between the two parties using some secure channel before it needs to be used. Key To build a key from shared secret, the key derivation function is typically used. Such systems almost always use symmetric key cryptographic algorithms. The term PSK is used in Wi-Fi encryption such as Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), where the method is called WPA-PSK or WPA2-PSK, and also in the Extensible Authentication Protocol (EAP), where it is known as EAP-PSK. In all these cases, both the wireless access points (AP) and all clients ''share'' the same key. The characteristics of this secret or key are determined by the system which uses it; some system designs require that such keys be in a particular format. It can be a password, a passphrase, or a hexadecimal string. The secret is used by all systems involved in the cryptographic processes used to secure the traffic between the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multiplicative Noise
In signal processing, the term multiplicative noise refers to an unwanted random signal that gets multiplied into some relevant signal during capture, transmission, or other processing. An important example is the speckle noise commonly observed in radar imagery. Examples of multiplicative noise affecting digital photographs are proper shadows due to undulations on the surface of the imaged objects, shadows cast by complex objects like foliage and Venetian blinds, dark spots caused by dust in the lens or image sensor, and variations in the gain of individual elements of the image sensor An image sensor or imager is a sensor that detects and conveys information used to make an image. It does so by converting the variable attenuation of light waves (as they pass through or reflect off objects) into signals, small bursts of curr ... array. Maria Petrou, Costas Petrou (2010Image Processing: The Fundamentals John Wiley & Sons. 818 pages. References {{reflist Signal proce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reconfigurable Antenna
A reconfigurable antenna is an antenna capable of modifying its frequency and radiation properties dynamically, in a controlled and reversible manner. In order to provide a dynamic response, reconfigurable antennas integrate an inner mechanism (such as RF switches, varactors, mechanical actuators or tunable materials) that enable the intentional redistribution of the RF currents over the antenna surface and produce reversible modifications of its properties. Reconfigurable antennas differ from smart antennas because the reconfiguration mechanism lies inside the antenna, rather than in an external beamforming network. The reconfiguration capability of reconfigurable antennas is used to maximize the antenna performance in a changing scenario or to satisfy changing operating requirements. Types of antenna reconfiguration Reconfigurable antennas can be classified according to the antenna parameter that is dynamically adjusted, typically the frequency of operation, radiation patte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Switched Array
Switched may refer to: * Switched (band) Switched (previously depicted as Sw1tched) was a nu metal band from Cleveland, Ohio. History Forming in 1999 as Sw1tch, the band played shows around Ohio and released a demo entitled ''Fuckin' Demo''. The songs "Anymore", "Wrongside", "Inside", ..., an American music group * ''Switched'' (novel), first book in the young adult Trylle series by Amanda Hocking * ''Switched!'' (American TV series) * ''Switched!'' (Singaporean TV series) * "Switched" (''Teen Titans''), an episode of the American TV series ''Teen Titans'' * Switched (2018 TV series), Japanese-language web television/Netflix Original series {{disambig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
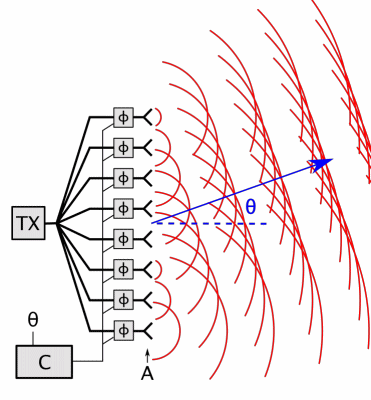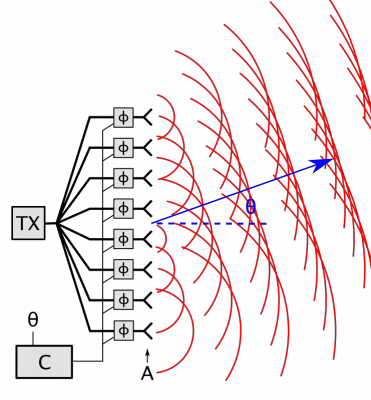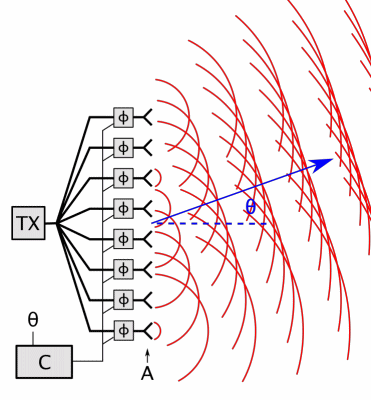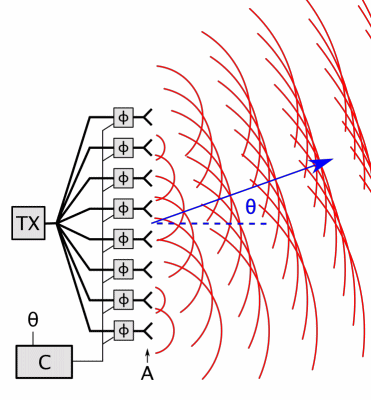
Phased Array
In antenna theory, a phased array usually means an electronically scanned array, a computer-controlled array of antennas which creates a beam of radio waves that can be electronically steered to point in different directions without moving the antennas. In a simple array antenna, the radio frequency current from the transmitter is fed to multiple individual antenna elements with the proper phase relationship so that the radio waves from the separate elements combine ( superpose) to form beams, to increase power radiated in desired directions and suppress radiation in undesired directions. In a phased array, the power from the transmitter is fed to the radiating elements through devices called ''phase shifters'', controlled by a computer system, which can alter the phase or signal delay electronically, thus steering the beam of radio waves to a different direction. Since the size of an antenna array must extend many wavelengths to achieve the high gain needed for narrow bea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Parasitic Array
Parasitism is a close relationship between species, where one organism, the parasite, lives on or inside another organism, the host, causing it some harm, and is adapted structurally to this way of life. The entomologist E. O. Wilson has characterised parasites as "predators that eat prey in units of less than one". Parasites include single-celled protozoans such as the agents of malaria, sleeping sickness, and amoebic dysentery; animals such as hookworms, lice, mosquitoes, and vampire bats; fungi such as honey fungus and the agents of ringworm; and plants such as mistletoe, dodder, and the broomrapes. There are six major parasitic strategies of exploitation of animal hosts, namely parasitic castration, directly transmitted parasitism (by contact), trophicallytransmitted parasitism (by being eaten), vector-transmitted parasitism, parasitoidism, and micropredation. One major axis of classification concerns invasiveness: an endoparasite lives inside the host's body; an ect ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Colluding
Collusion is a deceitful agreement or secret cooperation between two or more parties to limit open competition by deceiving, misleading or defrauding others of their legal right. Collusion is not always considered illegal. It can be used to attain objectives forbidden by law; for example, by defrauding or gaining an unfair market advantage. It is an agreement among firms or individuals to divide a market, set prices, limit production or limit opportunities. It can involve "unions, wage fixing, kickbacks, or misrepresenting the independence of the relationship between the colluding parties". In legal terms, all acts effected by collusion are considered void. Definition In the study of economics and market competition, collusion takes place within an industry when rival companies cooperate for their mutual benefit. Conspiracy usually involves an agreement between two or more sellers to take action to suppress competition between sellers in the market. Because competition among ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |