|
Apple Account
Apple Account, formerly known as Apple ID, is a user account by Apple for their devices and software. Apple Accounts contain the user's personal data and settings, and when an Apple Account is used to log in to an Apple device, the device will automatically use the data and settings associated with the Apple Account. Usage Account creation An Apple Account can be created by going to the associated website. As of December 2024, Apple has deprecated security questions and made two-factor authentication mandatory for activating iTunes & App Store functionality on a newly created account – a process that requires a device with iOS 13.4 (for iPhone or iPod Touch), iPadOS 13.4, macOS 10.15.4 or later. Modification Users can change their passwords or personal information on the My Apple Account page by selecting the "Manage your account" link. Changes that a user makes to an Apple Account, whilst they are using one Apple product, are also recognized by other applications wher ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apple Wallet
Apple Wallet (or simply Wallet, known as Passbook prior to iOS 9) is a digital wallet developed by Apple Inc. and included with iOS and watchOS that allows users to store Wallet passes such as coupons, boarding passes, Campus card, student ID cards, Identity document, government ID cards, business credentials, resort passes, car keys, home keys, event ticket (admission), tickets, public transportation passes, retail, store cards, and – starting with iOS 8, iOS 8.1 – credit cards, and debit cards for use via Apple Pay. History Apple Passbook was announced at the 2012 Worldwide Developers Conference, Apple Worldwide Developers Conference on June 11, 2012, and released with iOS 6 on September 19, 2012. It was renamed "Apple Wallet" with the release of iOS 9 on September 16, 2015. Features Wallet displays Aztec Code, Aztec, PDF417, and QR code, QR 2D barcodes and Code 128 1D barcodes beginning with iOS 9. Each digital coupon or ticket is known as a "pass". When th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ICloud
iCloud is the personal cloud service of Apple Inc. Launched on October 12, 2011, iCloud enables users to store and Data synchronization, sync data across devices, including Apple Mail, Calendar (Apple), Apple Calendar, Photos (Apple), Apple Photos, Notes (Apple), Apple Notes, contacts, settings, backups, and files, to collaborate with other users, and track Asset tracking, assets through Find My. iCloud's client app is built into iOS, iPadOS, watchOS, tvOS, macOS, and visionOS, and is available for Microsoft Windows. iCloud may additionally be accessed through a limited Web application, web interface. iCloud offers users 5 Gigabyte, GB of free storage which may be upgraded through optional paid plans to up to 12 TB; all paid plans include iCloud+ providing additional features. Optional end-to-end encryption has been available since 2022 for all iCloud data, except Calendar, Contacts, and Mail, which rely on legacy sync technologies for compatibility with third-party apps (CalDA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apple Developer
Apple Developer (formerly Apple Developer Connection) is Apple Inc.'s website for software development tools, application programming interfaces (APIs), and technical resources. It contains resources to help software developers write software for the macOS, iOS, iPadOS, watchOS, tvOS and visionOS platforms. The site also hosts the Apple Developer Forums. The applications are created in Xcode, or sometimes using other supported 3rd party programs. The apps can then be submitted to App Store Connect (formerly iTunes Connect), another one of Apple's website for approval the internal review team. Once approved, they can be distributed publicly via the respective app stores, i.e. App Store (iOS) for iOS and iPadOS apps, iMessage app store for Messages apps and Sticker pack apps, App Store (tvOS) for Apple TV apps, watchOS app store for Apple Watch apps with watchOS 6 and later, and via App Store (iOS) for earlier versions of watchOS. macOS apps are a notable exception to this, as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
App Store
An app store, also called an app marketplace or app catalog, is a type of digital distribution platform for computer software called applications, often in a mobile context. Apps provide a specific set of functions which, by definition, do not include the running of the computer itself. Complex software developed for personal computers may have a corresponding mobile app optimized for the device’s constraints. Today apps are normally designed to run on a specific mobile operating system—such as the contemporary iOS, iPadOS, Windows Phone Windows Phone (WP) is a discontinued mobile operating system developed by Microsoft Mobile for smartphones as the replacement successor to Windows Mobile and Zune. Windows Phone featured a new user interface derived from the Metro design languag ..., or Android (operating system), Android—but in the past mobile carriers had their own portals for apps and related media content. An app store can be thought as a restricted, commercial ve ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-to-end Encryption
End-to-end encryption (E2EE) is a method of implementing a secure communication system where only communicating users can participate. No one else, including the system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to read or send messages. End-to-end encryption prevents data from being read or secretly modified, except by the true sender and intended recipients. Frequently, the messages are relayed from the sender to the recipients by a service provider. However, messages are encrypted by the sender and no third party, including the service provider, has the means to decrypt them. The recipients retrieve the encrypted messages and decrypt them independently. Since third parties cannot decrypt the data being communicated or stored, services that provide end-to-end encryption are better at protecting user data when they are affected by data breaches. Such services are also unable to share user data with governm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key (cryptography)
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data. Based on the used method, the key can be different sizes and varieties, but in all cases, the strength of the encryption relies on the security of the key being maintained. A key's security strength is dependent on its algorithm, the size of the key, the generation of the key, and the process of key exchange. Scope The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography Symmetric cryptography refers to the practice of the same key being used for both encryption and decryption. Asymmetric cryptography Asymmetric cryptography has separate keys for encrypting and decrypting. These keys are known as the public and private keys, respectively. Purpose Since the key ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TechCrunch
TechCrunch is an American global online newspaper focusing on topics regarding high tech, high-tech and Startup company, startup companies. It was founded in June 2005 by Archimedes Ventures, led by partners Michael Arrington and Keith Teare. In 2010, AOL acquired the company for approximately $25 million. Following the 2015 Verizon Communications#Acquisition of AOL and Yahoo, acquisition of AOL and Yahoo! by Verizon, the site was owned by Verizon Media from 2015 through 2021. In 2021, Verizon sold its media assets, including AOL, Yahoo!, and TechCrunch, to the private equity firm Apollo Global Management. Apollo integrated them into a new entity called Yahoo! Inc. (2017–present), Yahoo! Inc. In addition to its news reporting, TechCrunch is also known for its annual Disrupt conference, a technology event hosted in several cities across the United States, Europe, and China. History TechCrunch was founded in June 2005 by Archimedes Ventures, led by partners Michael Arrington a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disposable Email Address
Disposable email addressing, also known as DEA, dark mail or masked email, refers to an approach that involves using a unique email address for each contact or entity, or using it for a limited number of times or uses. The benefit is that if the email address becomes compromised or utilized in connection with email abuse, the address owner can easily cancel (or "dispose" of) it without affecting any of their other contacts. Uses Disposable email addressing allows a different and unique email address for every sender or recipient combination. The method can be employed in scenarios where someone may sell or release an individual's email address to spam lists or other unethical entities. The most common situations of this type involve online registration for sites offering discussion groups, bulletin boards, chat rooms, online shopping, and file hosting services. Once an email address has been jeopardized by being sold, the result is often email spam or identity theft, both of whi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Social Login
Social login is a form of single sign-on using existing information from a social networking service such as Facebook, Twitter or Google Account, Google, to login to a third party website instead of creating a new login account specifically for that website. It is designed to simplify logins for end users as well as provide more reliable demographic information to web developers. How social login works Social login links accounts from one or more social networking services to a website, typically using either a Plug-in (computing), plug-in or a GUI widget, widget. By selecting the desired social networking service, the user simply uses his or her login for that service to sign on to the website. This, in turn, negates the need for the end user to remember login information for multiple electronic commerce and other websites while providing site owners with uniform demographic information as provided by the social networking service. Many sites which offer social login also offer mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenID Connect
OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party identity provider (IDP) service, eliminating the need for webmasters to provide their own ''ad hoc'' login systems, and allowing users to log in to multiple unrelated websites without having to have a separate identity and password for each. Users create accounts by selecting an OpenID identity provider, and then use those accounts to sign on to any website that accepts OpenID authentication. Several large organizations either issue or accept OpenIDs on their websites. The OpenID standard provides a framework for the communication that must take place between the identity provider and the OpenID acceptor (the "relying party"). An extension to the standard (the OpenID Attribute Exchange) facilitates the transfer of user attributes, such as name and gend ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
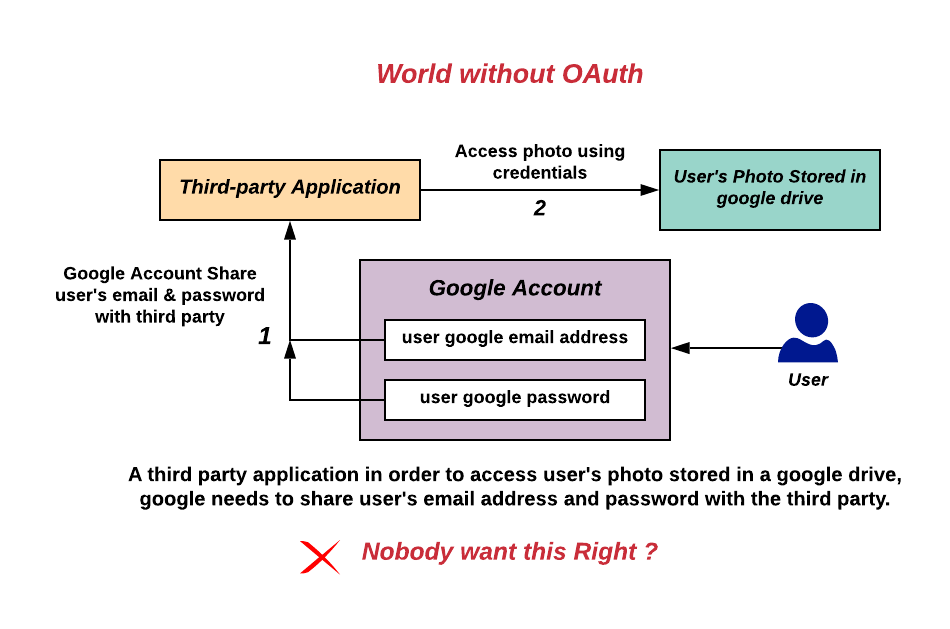
OAuth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |