|
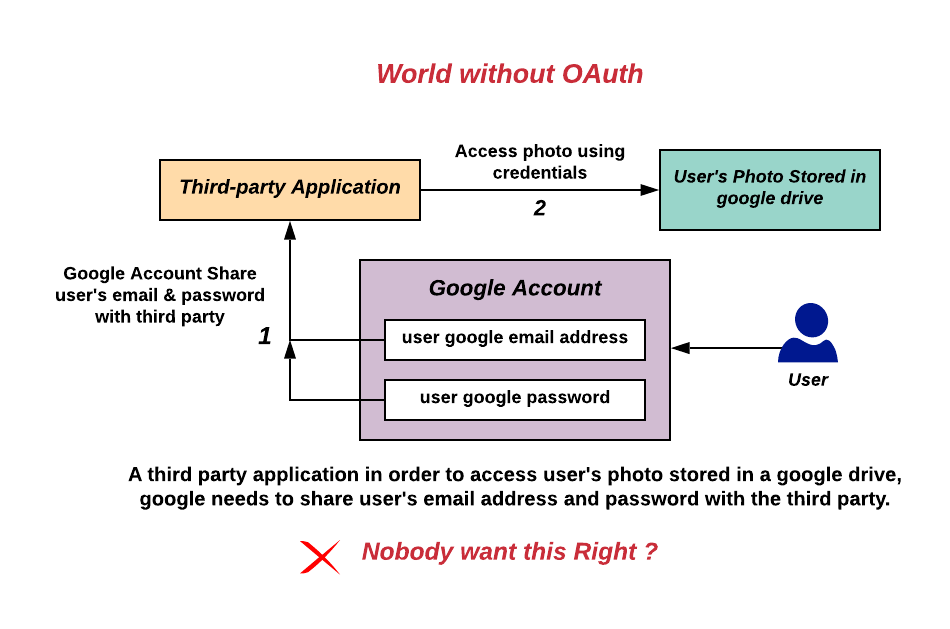
Oauth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenID
OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party identity provider (IDP) service, eliminating the need for webmasters to provide their own ''ad hoc'' login systems, and allowing users to log in to multiple unrelated websites without having to have a separate identity and password for each. Users create accounts by selecting an OpenID identity provider, and then use those accounts to sign on to any website that accepts OpenID authentication. Several large organizations either issue or accept OpenIDs on their websites. The OpenID standard provides a framework for the communication that must take place between the identity provider and the OpenID acceptor (the " relying party"). An extension to the standard (the OpenID Attribute Exchange) facilitates the transfer of user attributes, such as name and ge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gnolia
Gnolia, named Ma.gnolia until 2009, was a social bookmarking web site with an emphasis on design, social features, and open standards. In January 2009, Gnolia lost members' bookmarks in a widely reported data loss incident. It relaunched as a smaller service several months later and was ultimately shut down at the end of 2010. Users could rate bookmarks and mark bookmarks as private. Unlike its main competitor Delicious, Ma.gnolia stored snapshots of bookmarked web pages. One feature that distinguished it from other similar web sites was the ''group'' feature, which allowed several users to share a common collection of bookmarks, managed by a selected number of group managers. The design of the web site allowed for integration of the service into other applications via both a REST API and an API similar to the Delicious API. Open standards Ma.gnolia supported open standards and was often among early adopters of these standards. The bookmarking service provided support for sever ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
David Recordon
David Recordon (born September 4, 1986) is an American technologist with an open standards and open source background. He is currently the Chief Technology Officer at Rebellion Defense. From January 2021 to September 2022, he served as the Director of Technology in the White House under U.S. President Joe Biden. He previously served in a similar role during the last two years of the presidency of Barack Obama. Between his roles in government, he worked as Vice President of Infrastructure and Security at the Chan Zuckerberg Initiative. Earlier in his career, he played an important role in the development and evangelism for OpenID and OAuth. Biography Born in Portland, Oregon, Recordon began working with open source software and open standards in high school, including working for LiveJournal. At age 19, he played an important role in the development and popularization of OpenID and OAuth, and is probably best known for his evangelism on behalf of the decentralized single-si ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Twitter
Twitter, officially known as X since 2023, is an American microblogging and social networking service. It is one of the world's largest social media platforms and one of the most-visited websites. Users can share short text messages, images, and videos in Microblogging, short posts commonly known as "Tweet (social media), tweets" (officially "posts") and Like button, like other users' content. The platform also includes direct message, direct messaging, video and audio calling, bookmarks, lists, communities, a chatbot (Grok (chatbot), Grok), job search, and Spaces, a social audio feature. Users can vote on context added by approved users using the Community Notes feature. Twitter was created in March 2006 by Jack Dorsey, Noah Glass, Biz Stone, and Evan Williams (Internet entrepreneur), Evan Williams, and was launched in July of that year. Twitter grew quickly; by 2012 more than 100 million users produced 340 million daily tweets. Twitter, Inc., was based in San Francisco, C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blaine Cook (programmer)
Blaine Cook (born December 19, 1980) is a Canadian software engineer, now living and working in Nelson, British Columbia. Career Cook is the principal co-author of the OAuth and WebFinger specifications. He is the former lead developer of social networking site Twitter. He has also worked for Yahoo! on the Fire Eagle project and for BT Group as part of their open source Osmosoft team. He was founder of collaborative text editing startup Poetica. Poetica was acquired by Condé Nast in March 2016, and Cook remained with the company as a staff engineer. References External links Cook's Home pageby Stephen Baker, ''Business Week'' (May 15, 2008) "Twitter techie Blaine Cook talks about leaving"by Caroline McCarthy, CNET News (April 23, 2008) "Twitter to jump off Ruby on Rails?"by Anthony Ha, ''The Industry Standard'' (May 1, 2008) "Busy Twitter a poster child for new communications"by Stephen Lawson, ''Computerworld'' (March 14, 2008)) "Twitter’s to-do list: Become obsessive a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chris Messina (open-source Advocate)
Christopher Reaves Messina (born January 7, 1981) is an American blogger, product consultant and speaker who proposed the usage of the hashtag as it is currently used on social media platforms. In a 2007 tweet, Messina proposed vertical/associational grouping of messages, trends, and events on Twitter by the means of hashtags. The hashtag was intended to be a type of Tag (metadata), metadata tag that allowed users to apply dynamic, User-generated content, user-generated tagging, which made it possible for others to easily find messages with a specific digger theme or content. It allowed easy, informal markup of folksonomy without need of any formal Taxonomy (general), taxonomy or markup language. Hashtags have since been referred to as the "eavesdroppers", "wormholes", "time-machines", and "veins" of the Internet. Although Twitter's initial response to Messina's proposed use of hashtags was negative, stating that "these things are for nerds" a series of events, including the de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Birds Of A Feather (computing)
The Internet Engineering Task Force (IETF) is a standards organization for the Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, a non-profit organization with local chapters around the world. Organization There is no membership in the IETF. Anyone can participate by signing up to a working group mailing list, or registering for an IETF meeting. The IETF operates in a bottom-up task creation mode, largely driven by working groups. Each working group normally has appointed two co-chairs (occasionally three); a charter that describes its focus; and what it is expected to produce, and when. It is open to all who want to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Request For Comments
A Request for Comments (RFC) is a publication in a series from the principal technical development and standards-setting bodies for the Internet, most prominently the Internet Engineering Task Force (IETF). An RFC is authored by individuals or groups of engineers and computer scientists in the form of a memorandum describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems. It is submitted either for peer review or to convey new concepts, information, or, occasionally, engineering humor. The IETF adopts some of the proposals published as RFCs as Internet Standards. However, many RFCs are informational or experimental in nature and are not standards. The RFC system was invented by Steve Crocker in 1969 to help record unofficial notes on the development of ARPANET. RFCs have since become official documents of Internet specifications, communications protocols, procedures, and events. According to Crocker, the docu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Discussion Group
A discussion group is a group of individuals, typically who share a similar interest, who gather either formally or informally to discuss ideas, solve problems, or make comments. Common methods of conversing including meeting in person, conducting conference calls, using text messaging, or using a website such as an Internet forum. People respond, add comments, and make posts on such forums, as well as on established mailing lists, in news groups, or in IRC channels. Other group members could choose to respond by posting text or image. Brief history Discussion group was evolved from USENET which is a traced back to early 80's. Two computer scientists Jim Ellis and Tom Truscott founded the idea of setting a system of rules to produce "articles", and then send back to their parallel news group. Fundamentally, the form of discussion group was generated on the concept of USENET, which emphasised ways of communication via email and web forums. Gradually, USENET had developed t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Programming Interface
An application programming interface (API) is a connection between computers or between computer programs. It is a type of software Interface (computing), interface, offering a service to other pieces of software. A document or standard that describes how to build such a connection or interface is called an ''API specification''. A computer system that meets this standard is said to ''implement'' or ''expose'' an API. The term API may refer either to the specification or to the implementation. In contrast to a user interface, which connects a computer to a person, an application programming interface connects computers or pieces of software to each other. It is not intended to be used directly by a person (the end user) other than a computer programmer who is incorporating it into software. An API is often made up of different parts which act as tools or services that are available to the programmer. A program or a programmer that uses one of these parts is said to ''call'' that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Session Fixation
In computer network security, session fixation attacks attempt to exploit the vulnerability of a system that allows one person to fixate (find or set) another person's session identifier. Most session fixation attacks are web based, and most rely on session identifiers being accepted from URLs (query string) or POST data. Attack scenarios Alice has an account at the bank http://unsafe.example.com/ Mallory intends to target Alice's money from her bank. Alice has a reasonable level of trust in Mallory, and will visit links Mallory sends her. A simple attack scenario Straightforward scenario: # Mallory has determined that http://unsafe.example.com/ accepts any session identifier, accepts session identifiers from query strings and has no security validation. http://unsafe.example.com/ is thus not secure. # Mallory sends Alice an e-mail: "Hey, check this out, there is a cool new account summary feature on our bank, http://unsafe.example.com/?SID=I_WILL_KNOW_THE_SID". Mallor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |