|
Tamperproofing
Tamperproofing is a methodology used to hinder, deter or detect unauthorised access to a device or circumvention of a security system. Since any device or system can be foiled by a person with sufficient knowledge, equipment, and time, the term "tamperproof" is a misnomer unless some limitations on the tampering party's resources is explicit or assumed. Tamper resistance is resistance to intentional malfunction or sabotage by either the normal users of a product, package, or system or others with physical access to it. Tamper resistance ranges from simple features like List of screw drives#Tamper-resistant types, screws with special drives and Security_seal, tamper-evident seals to more complex devices that render themselves inoperable or encrypt all data transmissions between individual chips, use of materials needing special tools and knowledge. Tamper-resistant devices or features are common on packages to deter package or product tampering or enable its detection. Anti-tam ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tamper-evident
Tamper-evident describes a device or process that makes unauthorized access to the protected object easily detected. Seals, markings, or other techniques may be tamper indicating. Tampering Tampering involves the deliberate altering or adulteration of information, a product, a package, or system. Solutions may involve all phases of product production, distribution, logistics, sale, and use. No single solution can be considered as "tamper proof". Often multiple levels of security need to be addressed to reduce the risk of tampering. Some considerations might include: *Identify who a potential tamperer might be and what level of knowledge, materials, tools, etc. might they have. *Identify all feasible methods of unauthorized access into a product, package, or system. In addition to the primary means of entry, also consider secondary or "back door" methods. *Control or limit access to products or systems of interest. *Improve the tamperproofing, tamper resistance by making tampering ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Misnomer
A misnomer is a name that is incorrectly or unsuitably applied. Misnomers often arise because something was named long before its correct nature was known, or because an earlier form of something has been replaced by a later form to which the name no longer suitably applies. A misnomer may also be a word that is used incorrectly or misleadingly. The word "misnomer" does not mean " misunderstanding" or " popular misconception", and a number of misnomers remain in common usage — which is to say that a word being a misnomer does not necessarily make ''usage'' of the word incorrect. Sources of misnomers * An older name being retained after the thing itself has changed (e.g., tin can, mince meat pie, steamroller, tin foil, clothes iron, digital darkroom). This is essentially a metaphorical extension with the name of the older item standing for anything filling the same role. * Transference of a well-known product brand name into a genericized trademark (e.g., Xerox f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
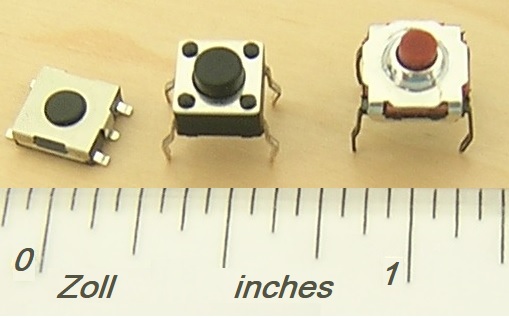
Normally Open
In electrical engineering, a switch is an electrical component that can disconnect or connect the conducting path in an electrical circuit, interrupting the electric current or diverting it from one conductor to another. The most common type of switch is an electromechanical device consisting of one or more sets of movable electrical contacts connected to external circuits. When a pair of contacts is touching current can pass between them, while when the contacts are separated no current can flow. Switches are made in many different configurations; they may have multiple sets of contacts controlled by the same knob or actuator, and the contacts may operate simultaneously, sequentially, or alternately. A switch may be operated manually, for example, a light switch or a keyboard button, or may function as a sensing element to sense the position of a machine part, liquid level, pressure, or temperature, such as a thermostat. Many specialized forms exist, such as the toggle switch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microwave
Microwave is a form of electromagnetic radiation with wavelengths shorter than other radio waves but longer than infrared waves. Its wavelength ranges from about one meter to one millimeter, corresponding to frequency, frequencies between 300 MHz and 300 GHz, broadly construed. A more common definition in radio-frequency engineering is the range between 1 and 100 GHz (wavelengths between 30 cm and 3 mm), or between 1 and 3000 GHz (30 cm and 0.1 mm). In all cases, microwaves include the entire super high frequency, super high frequency (SHF) band (3 to 30 GHz, or 10 to 1 cm) at minimum. The boundaries between far infrared, terahertz radiation, microwaves, and ultra-high-frequency (UHF) are fairly arbitrary and differ between different fields of study. The prefix ' in ''microwave'' indicates that microwaves are small (having shorter wavelengths), compared to the radio waves used in prior radio technology. Frequencies in the micr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Smartcards
A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an Embedded system, embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are Contactless smart card, contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card (UICC) for mobile phones, installed as pluggable SIM card or embedded eSIM, is also a type of smart card. , 10.5billion smart card IC chips are manufactured annually ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IBM 4758
The IBM 4758 PCI Cryptographic Coprocessor is a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCI expansion card. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed. IBM International Business Machines Corporation (using the trademark IBM), nicknamed Big Blue, is an American Multinational corporation, multinational technology company headquartered in Armonk, New York, and present in over 175 countries. It is ... supplies two cryptographic-system implementations, and toolkits for custom application development: * The PKCS#11, version 2.01 implementation creates a high-security solution for application programs developed for this industry-standard API. * The IBM Common Cryptographic Architecture implementation provides many functions of special interest in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Cryptoprocessor
A secure cryptoprocessor is a dedicated computer-on-a-chip or microprocessor for carrying out cryptographic operations, embedded in a packaging with multiple physical security measures, which give it a degree of tamper resistance. Unlike cryptographic processors that output decrypted data onto a bus in a secure environment, a secure cryptoprocessor does not output decrypted data or decrypted program instructions in an environment where security cannot always be maintained. The purpose of a secure cryptoprocessor is to act as the keystone of a security subsystem, eliminating the need to protect the rest of the subsystem with physical security measures. Examples A hardware security module (HSM) contains one or more secure cryptoprocessor chips. These devices are high grade secure cryptoprocessors used with enterprise servers. A hardware security module can have multiple levels of physical security with a single-chip cryptoprocessor as its most secure component. The cryptoproc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Money
Digital currency (digital money, electronic money or electronic currency) is any currency, money, or money-like asset that is primarily managed, stored or exchanged on digital computer systems, especially over the internet. Types of digital currencies include cryptocurrency, virtual currency and central bank digital currency. Digital currency may be recorded on a distributed database on the internet, a centralized electronic computer database owned by a company or bank, within digital files or even on a stored-value card. Digital currencies exhibit properties similar to traditional currencies, but generally do not have a classical physical form of fiat currency historically that can be held in the hand, like currencies with printed banknotes or minted coins. However, they do have a physical form in an unclassical sense coming from the computer to computer and computer to human interactions and the information and processing power of the servers that store and keep track o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Private Key
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. There are many kinds of public-key cryptosystems, with different security goals, including digital signature, Diffie–Hellman key exchange, public-key key encapsulation, and public-key encryption. Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols that offer assurance of the confidentiality and authenticity of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security (TLS), SSH, S/MIME, and P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microprocessor
A microprocessor is a computer processor (computing), processor for which the data processing logic and control is included on a single integrated circuit (IC), or a small number of ICs. The microprocessor contains the arithmetic, logic, and control circuitry required to perform the functions of a computer's central processing unit (CPU). The IC is capable of interpreting and executing program instructions and performing arithmetic operations. The microprocessor is a multipurpose, Clock signal, clock-driven, Processor register, register-based, digital integrated circuit that accepts binary code, binary data as input, processes it according to instruction (computing), instructions stored in its computer memory, memory, and provides results (also in binary form) as output. Microprocessors contain both combinational logic and sequential logic, sequential digital logic, and operate on numbers and symbols represented in the binary number system. The integration of a whole CPU on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |