|
Tamarin Prover
Tamarin Prover is a computer software program for formal verification of cryptographic protocols. It has been used to verify Transport Layer Security 1.3, ISO/IEC 9798, DNP3 Secure Authentication v5, WireGuard,; and the PQ3 Messaging Protocol of Apple iMessage. Tamarin is an open source tool, written in Haskell, built as a successor to an older verification tool called Scyther. Colin Boyd, Anish Mathuria, Douglas Stebila. "Protocols for Authentication and Key Establishment", Second Edition Springer, 2019. pg 48 Tamarin has automatic proof features, but can also be self-guided. In Tamarin ''lemmas'' that representing security properties are defined.Celi, Sofía, Jonathan Hoyland, Douglas Stebila, and Thom Wiggers. "A tale of two models: Formal verification of KEMTLS via Tamarin." In European Symposium on Research in Computer Security, pp. 63-83. Cham: Springer Nature Switzerland, 2022. After changes are made to a protocol, Tamarin can verify if the security properties are maint ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cas Cremers
Casimier Joseph Franciscus "Cas" Cremers (born 16 June 1974) accessed January 2018. is a computer scientist and a faculty member at the CISPA Helmholtz Center for Information Security in Saarbruecken, Germany. Career Cremers received his PhD from in 2006, under the supervision of Sjouke Mauw and Erik de Vink. Between 2006 and 2013, he worked at the Information Security Group at |
Free Software Programmed In Haskell
Free may refer to: Concept * Freedom, the ability to act or change without constraint or restriction * Emancipate, attaining civil and political rights or equality * Free (''gratis''), free of charge * Gratis versus libre, the difference between the two common meanings of the adjective "free". Computing * Free (programming), a function that releases dynamically allocated memory for reuse * Free software, software usable and distributable with few restrictions and no payment *, an emoji in the Enclosed Alphanumeric Supplement block. Mathematics * Free object ** Free abelian group ** Free algebra ** Free group ** Free module ** Free semigroup * Free variable People * Free (surname) * Free (rapper) (born 1968), or Free Marie, American rapper and media personality * Free, a pseudonym for the activist and writer Abbie Hoffman * Free (active 2003–), American musician in the band FreeSol Arts and media Film and television * ''Free'' (film), a 2001 American dramedy * ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Software
Encryption software is software that uses cryptography to prevent unauthorized access to digital information. Cryptography is used to protect digital information on computers as well as the digital information that is sent to other computers over the Internet. Classification There are many software products which provide encryption. Software encryption uses a cipher to obscure the content into ciphertext. One way to classify this type of software is the type of cipher used. Ciphers can be divided into two categories: public key ciphers (also known as asymmetric ciphers), and symmetric key ciphers. Encryption software can be based on either public key or symmetric key encryption. Another way to classify software encryption is to categorize its purpose. Using this approach, software encryption may be classified into software which encrypts " data in transit" and software which encrypts " data at rest". Data in transit generally uses public key ciphers, and data at rest generally us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hybrid Argument (cryptography)
In cryptography, the hybrid argument is a proof technique used to show that two distributions are computationally indistinguishable. History Hybrid arguments had their origin in a papers by Andrew Yao in 1982 and Shafi Goldwasser and Silvio Micali in 1983. Formal description Formally, to show two distributions ''D''1 and ''D''2 are computationally indistinguishable, we can define a sequence of ''hybrid distributions'' ''D''1 := ''H''0, ''H''1, ..., ''H''''t'' =: ''D''2 where ''t'' is polynomial in the security parameter ''n''. Define the advantage of any probabilistic efficient (polynomial-bounded time) algorithm A as :\mathsf_^(\mathbf) := \left, \Pr \stackrel H_i : \mathbf(x)=1- \Pr \stackrel H_ : \mathbf(x)=1\, where the dollar symbol ($) denotes that we sample an element from the distribution at random. By triangle inequality, it is clear that for any probabilistic polynomial time algorithm A, :\mathsf_^(\mathbf) \leq \sum_^\mathsf_^(\mathbf). Thus there must exist som ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dolev–Yao Model
The Dolev–Yao model, named after its authors Danny Dolev and Andrew Yao, is a formal model used to prove properties of interactive cryptographic protocols. The network The network is represented by a set of abstract machines that can exchange messages. These messages consist of formal terms. These terms reveal some of the internal structure of the messages, but some parts will hopefully remain opaque to the adversary. The adversary The adversary in this model can overhear, intercept, and synthesize any message and is only limited by the constraints of the cryptographic methods used. In other words: "the attacker carries the message." This omnipotence has been very difficult to model, and many threat models simplify it, as has been done for the attacker in ubiquitous computing. The algebraic model Cryptographic primitives are modeled by abstract operators. For example, asymmetric encryption for a user x is represented by the encryption function E_x and the decryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Halting Problem
In computability theory (computer science), computability theory, the halting problem is the problem of determining, from a description of an arbitrary computer program and an input, whether the program will finish running, or continue to run forever. The halting problem is ''Undecidable problem, undecidable'', meaning that no general algorithm exists that solves the halting problem for all possible program–input pairs. The problem comes up often in discussions of computability since it demonstrates that some functions are mathematically Definable set, definable but not Computable function, computable. A key part of the formal statement of the problem is a mathematical definition of a computer and program, usually via a Turing machine. The proof then shows, for any program that might determine whether programs halt, that a "pathological" program exists for which makes an incorrect determination. Specifically, is the program that, when called with some input, passes its own s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Haskell
Haskell () is a general-purpose, statically typed, purely functional programming language with type inference and lazy evaluation. Designed for teaching, research, and industrial applications, Haskell pioneered several programming language features such as type classes, which enable type-safe operator overloading, and monadic input/output (IO). It is named after logician Haskell Curry. Haskell's main implementation is the Glasgow Haskell Compiler (GHC). Haskell's semantics are historically based on those of the Miranda programming language, which served to focus the efforts of the initial Haskell working group. The last formal specification of the language was made in July 2010, while the development of GHC continues to expand Haskell via language extensions. Haskell is used in academia and industry. , Haskell was the 28th most popular programming language by Google searches for tutorials, and made up less than 1% of active users on the GitHub source code repository ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IMessage
iMessage is an instant messaging service developed by Apple Inc. and launched in 2011. iMessage functions exclusively on Apple platforms – including iOS, iPadOS, macOS, watchOS, and visionOS – as part of Apple ecosystem, Apple's approach to inter-device integration, which has been described by media outlets as a means of achieving vendor lock-in. iMessage is accessed and used using the Messages (Apple), Messages app client. Core features of iMessage, available on all supported platforms, include sending Text messaging, text messages, images, videos, and documents; getting delivery and read statuses (read receipts); and end-to-end encryption so only the sender and recipient can read the messages, and no one else; even Apple itself cannot read them. The service also allows sending location data and Sticker (messaging), stickers. On iOS and iPadOS, third-party developers can extend iMessage capabilities with custom extensions, an example being quick sharing of recently played ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apple Inc
Apple Inc. is an American multinational corporation and technology company headquartered in Cupertino, California, in Silicon Valley. It is best known for its consumer electronics, software, and services. Founded in 1976 as Apple Computer Company by Steve Jobs, Steve Wozniak and Ronald Wayne, the company was incorporated by Jobs and Wozniak as Apple Computer, Inc. the following year. It was renamed Apple Inc. in 2007 as the company had expanded its focus from computers to consumer electronics. Apple is the largest technology company by revenue, with billion in the 2024 fiscal year. The company was founded to produce and market Wozniak's Apple I personal computer. Its second computer, the Apple II, became a best seller as one of the first mass-produced microcomputers. Apple introduced the Lisa in 1983 and the Macintosh in 1984, as some of the first computers to use a graphical user interface and a mouse. By 1985, internal company problems led to Jobs leavin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
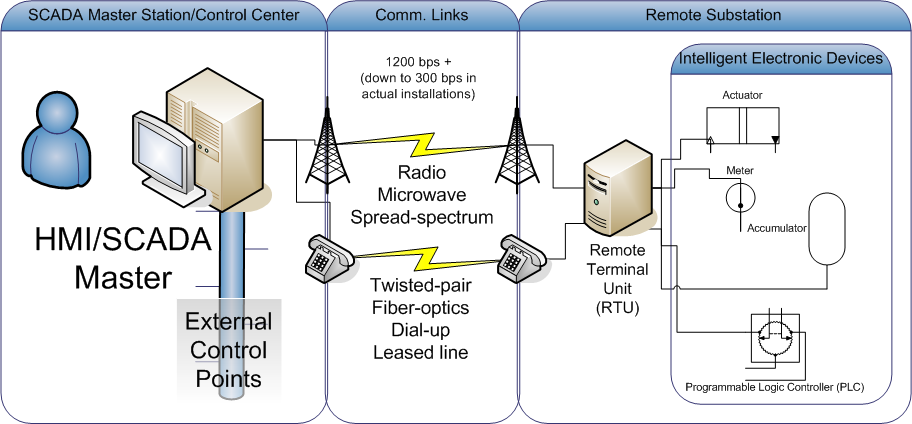
DNP3
Distributed Network Protocol 3 (DNP3) is a set of communications protocols used between components in process automation systems. Its main use is in utilities such as electric and water companies. Usage in other industries is not common. It was developed for communications between various types of data acquisition and control equipment. It plays a crucial role in SCADA systems, where it is used by SCADA Master Stations (a.k.a. Control Centers), Remote Terminal Units (RTUs), and Intelligent Electronic Devices (IEDs). It is primarily used for communications between a master station and RTUs or IEDs. ICCP, the Inter-Control Center Communications Protocol (a part of IEC 60870-6), is used for inter-master station communications. Competing standards include the older Modbus protocol and the newer IEC 61850 protocol. History While IEC 60870-5 was still under development and had not been standardized, there was a need to create a standard that would allow interoperability betw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Haskell (programming Language)
Haskell () is a General-purpose programming language, general-purpose, static typing, statically typed, purely functional programming, purely functional programming language with type inference and lazy evaluation. Designed for teaching, research, and industrial applications, Haskell pioneered several programming language #Features, features such as type classes, which enable type safety, type-safe operator overloading, and Monad (functional programming), monadic input/output (IO). It is named after logician Haskell Curry. Haskell's main implementation is the Glasgow Haskell Compiler (GHC). Haskell's Semantics (computer science), semantics are historically based on those of the Miranda (programming language), Miranda programming language, which served to focus the efforts of the initial Haskell working group. The last formal specification of the language was made in July 2010, while the development of GHC continues to expand Haskell via language extensions. Haskell is used in a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |