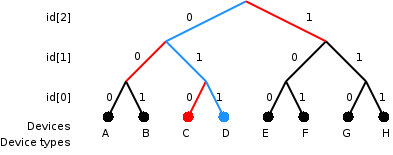
|
Singulation
Singulation is a method by which an RFID reader identifies a tag with a specific serial number from a number of tags in its field. This is necessary because if multiple tags respond simultaneously to a query, they will jam each other. In a typical commercial application, such as scanning a bag of groceries, potentially hundreds of tags might be within range of the reader. When all the tags cooperate with the tag reader and follow the same anti-collision protocol, also called singulation protocol, Technovelgy"Problems With RFID" then the tag reader can read data from each and every tag without interference from the other tags. Collision avoidance Generally, a collision occurs when two entities require the same resource; for example, two ships with crossing courses in a narrows. In wireless technology, a collision occurs when two transmitters transmit at the same time with the same modulation scheme on the same frequency. In RFID technology, various strategies have been devel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RFID
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods. Passive tags are powered by energy from the RFID reader's interrogating radio waves. Active tags are powered by a battery and thus can be read at a greater range from the RFID reader, up to hundreds of meters. Unlike a barcode, the tag does not need to be within the line of sight of the reader, so it may be embedded in the tracked object. RFID is one method of automatic identification and data capture (AIDC). RFID tags are used in many industries. For example, an RFID tag attached to an automobile during product ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Serial Number
A serial number (SN) is a unique identifier used to ''uniquely'' identify an item, and is usually assigned incrementally or sequentially. Despite being called serial "numbers", they do not need to be strictly numerical and may contain letters and other typographical symbols, or may consist entirely of a character (computing), character string (computer science), string. Applications of serial numbering Serial numbers identify otherwise identical individual units, thereby serving various practical uses. Serial numbers are a deterrent against theft and counterfeit products, as they can be recorded, and stolen or otherwise irregular goods can be identified. Banknotes and other transferable documents of value bear serial numbers to assist in preventing counterfeiting and tracing stolen ones. They are valuable in quality control, as once a defect is found in the production of a particular batch of product, the serial number will identify which units are affected. Some items with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Radio Jamming
Radio jamming is the deliberate blocking of or interference with wireless communications.https://apps.fcc.gov/edocs_public/attachmatch/DA-12-347A1.pdf Enforcement Advisory No. 2012-02 FCC Enforcement Advisory Cell Jammers, GPS Jammers, and Other Jamming Devices Consumer Alert: Using or Importing Jammers is Illegal In some cases, jammers work by the transmission of radio signals that disrupt telecommunications by decreasing the signal-to-noise ratio. The concept can be used in wireless data networks to disrupt information flow. It is a common form of censorship in totalitarian countries, in order to prevent foreign radio stations in border areas from reaching the country. Jamming is usually distinguished from interference that can occur due to device malfunctions or other accidental circumstances. Devices that simply cause interference are regulated differently. Unintentional "jamming" occurs when an operator transmits on a busy frequency without first checking whether it is in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Collision (telecommunications)
A collision is the situation that occurs when two or more demands are made simultaneously on equipment that can handle only one at any given instant.Source: from Federal Standard 1037C and from MIL-STD-188 It may refer to: * Collision domain, a physical network segment where data packets can "collide" ** Carrier-sense multiple access with collision avoidance, (CSMA/CA) used for example with wireless LANs ** Carrier-sense multiple access with collision detection, (CSMA/CD) used with Ethernet * Late collision, a specific type of collision that should not occur on properly operating networks * Local collision is a collision that occurs in the network interface rather than on the network itself See also * Collision (other) * Contention (telecommunications) In statistical time division multiplexing, contention is a media access method that is used to share a broadcast medium. In contention, any computer in the network can transmit data at any time (first come-first se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RFID Search Environment
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods. Passive tags are powered by energy from the RFID reader's interrogating radio waves. Active tags are powered by a battery and thus can be read at a greater range from the RFID reader, up to hundreds of meters. Unlike a barcode, the tag does not need to be within the line of sight of the reader, so it may be embedded in the tracked object. RFID is one method of automatic identification and data capture (AIDC). RFID tags are used in many industries. For example, an RFID tag attached to an automobile during production c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Auto-ID Labs
The Auto-ID Labs network is a research group in the field of networked radio-frequency identification (RFID) and emerging sensing technologies. The labs consist of seven research universities located on four different continents. These institutions were chosen by the former Auto-ID Center to design the architecture for the Internet of Things together with EPCglobal. The federation was established in 1999; the network they have developed is at the heart of a proposal sponsored by EPCglobal and supported by GS1, GS1 US, Wal-Mart, Hewlett-Packard, and others to use RFID and the Electronic Product Code (EPC) in the identification of items in the supply chain for companies. The areas of expertise range from hardware to software to business research related to RFID. History The Auto-ID Labs is the research-oriented successor to the MIT Auto-ID Center, founded by Kevin Ashton, David Brock, Dr. Daniel Engels, Sanjay Sarma, and Sunny Siu with funding from Procter & Gamble, Gillette, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSA Security
RSA Security LLC, formerly RSA Security, Inc. and trade name RSA, is an American computer security, computer and network security company with a focus on encryption and decryption standards. RSA was named after the initials of its co-founders, Ron Rivest, Adi Shamir and Leonard Adleman, after whom the RSA (algorithm), RSA public key cryptography algorithm was also named. Among its products is the SecurID authentication token. The BSAFE cryptography libraries were also initially owned by RSA. RSA is known for incorporating backdoors developed by the National Security Agency, NSA in its products. It also organizes the annual RSA Conference, an information security conference. Founded as an independent company in 1982, RSA Security was acquired by EMC Corporation in 2006 for US$2.1 billion and operated as a division within EMC. When EMC was acquired by Dell Technologies in 2016, RSA became part of the Dell Technologies family of brands. On 10 March 2020, Dell Technologies announced ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSA Blocker Tag
An RSA blocker tag (or RSA tag) is a RFID tag that responds positively to all unauthorized requests, thus blocking some scanners from reading any RFID tags placed nearby. The tags are designed to protect privacy, and are supposedly unable to be used for theft, denials of service, and other malicious uses. Other mechanisms designed to protect privacy for RFID item tagging for retail use are the EPCglobal kill command and the Clipped Tag proposed by IBM. External links RSA Labs press release See also * Contactless smart card A contactless smart card is a contactless credential whose dimensions are credit card size. Its embedded integrated circuits can store (and sometimes process) data and communicate with a terminal via NFC. Commonplace uses include transit ticket ... Radio-frequency identification Hardware device blockers {{tech-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ALOHAnet
ALOHAnet, also known as the ALOHA System, or simply ALOHA, was a pioneering computer networking system developed at the University of Hawaii. ALOHAnet became operational in June 1971, providing the first public demonstration of a wireless packet data network. The ALOHAnet used a new method of medium access, called ''ALOHA random access'', and experimental ultra high frequency (UHF) for its operation. In its simplest form, later known as Pure ALOHA, remote units communicated with a base station (Menehune) over two separate radio frequencies (for inbound and outbound respectively). Nodes did not wait for the channel to be clear before sending, but instead waited for acknowledgement of successful receipt of a message, and re-sent it if this was not received. Nodes would also stop and re-transmit data if they detected any other messages while transmitting. While simple to implement, this results in an efficiency of only 18.4%. A later advancement, Slotted ALOHA, improved the effi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ethernet
Ethernet ( ) is a family of wired computer networking technologies commonly used in local area networks (LAN), metropolitan area networks (MAN) and wide area networks (WAN). It was commercially introduced in 1980 and first standardized in 1983 as IEEE 802.3. Ethernet has since been refined to support higher bit rates, a greater number of nodes, and longer link distances, but retains much backward compatibility. Over time, Ethernet has largely replaced competing wired LAN technologies such as Token Ring, FDDI and ARCNET. The original 10BASE5 Ethernet uses a thick coaxial cable as a shared medium. This was largely superseded by 10BASE2, which used a thinner and more flexible cable that was both less expensive and easier to use. More modern Ethernet variants use Ethernet over twisted pair, twisted pair and fiber optic links in conjunction with Network switch, switches. Over the course of its history, Ethernet data transfer rates have been increased from the original to the lates ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ALOHA
''Aloha'' ( , Hawaiian: �ˈlohə is the Hawaiian word for love, affection, peace, compassion and mercy, that is commonly used as a greeting. It has a deeper cultural and spiritual significance to native Hawaiians, for whom the term is used to define a force that holds together existence. The word is found in all Polynesian languages and always with the same basic meaning of "love, compassion, sympathy, kindness." Its use in Hawaii has a seriousness lacking in the Tahitian and Samoan meanings. Mary Kawena Pukui wrote that the "first expression" of ''aloha'' was between a parent and child. Lorrin Andrews wrote the first Hawaiian dictionary, called ''A Dictionary of the Hawaiian Language''. In it, he describes ''aloha'' as "A word expressing different feelings: love, affection, gratitude, kindness, pity, compassion, grief, the modern common salutation at meeting; parting". Mary Kawena Pukui and Samuel Hoyt Elbert's ''Hawaiian Dictionary: Hawaiian-English, English-Haw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |