|
Science DMZ Network Architecture
The term Science DMZ refers to a computer subnetwork that is structured to be secure, but without the performance limits that would otherwise result from passing data through a stateful firewall. The Science DMZ is designed to handle high volume data transfers, typical with scientific and high-performance computing, by creating a special DMZ (computing), DMZ to accommodate those transfers. It is typically deployed at or near the local network perimeter, and is optimized for a moderate number of high-speed flows, rather than for general-purpose business systems or Enterprise software, enterprise computing. The term ''Science DMZ'' was coined by collaborators at the US Department of Energy's ESnet in 2010. A number of universities and laboratories have deployed or are deploying a Science DMZ. In 2012 the National Science Foundation funded the creation or improvement of Science DMZs on several university campuses in the United States. The Science DMZ is a network architectu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Subnetwork
A subnetwork or subnet is a logical subdivision of an IP network. Updated by RFC 6918. The practice of dividing a network into two or more networks is called subnetting. Computers that belong to the same subnet are addressed with an identical most-significant bit-group in their IP addresses. This results in the logical division of an IP address into two fields: the ''network number'' or ''routing prefix'' and the ''rest field'' or ''host identifier''. The ''rest field'' is an identifier for a specific host or network interface. The ''routing prefix'' may be expressed in Classless Inter-Domain Routing (CIDR) notation written as the first address of a network, followed by a slash character (''/''), and ending with the bit-length of the prefix. For example, is the prefix of the Internet Protocol version 4 network starting at the given address, having 24 bits allocated for the network prefix, and the remaining 8 bits reserved for host addressing. Addresses in the range to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
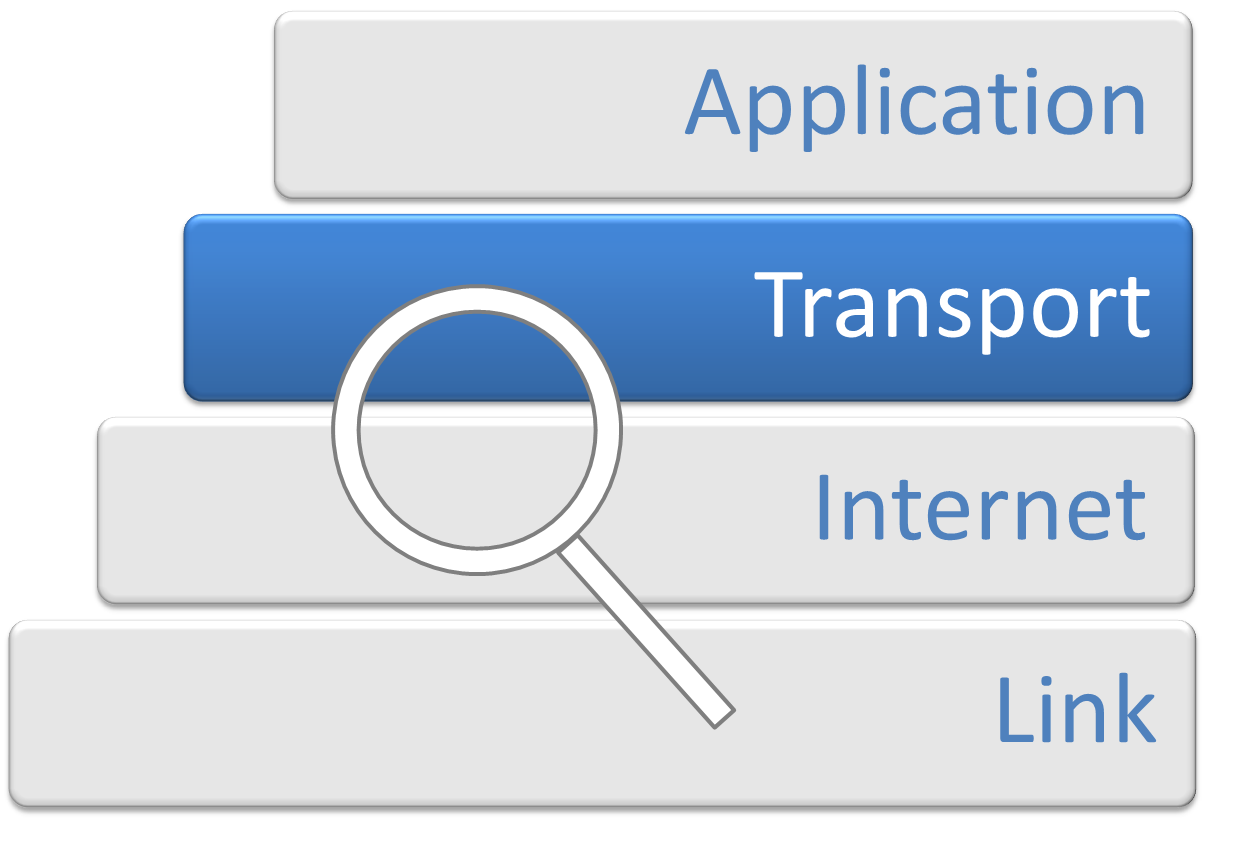
Transport Layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing. The details of implementation and semantics of the transport layer of the Internet protocol suite, which is the foundation of the Internet, and the OSI model of general networking are different. The protocols in use today in this layer for the Internet all originated in the development of TCP/IP. In the OSI model the transport layer is often referred to as Layer 4, or L4, while numbered layers are not used in TCP/IP. The best-known transport protocol of the Internet protocol suite is the Transmission Control Protocol (TCP). It is used for connection-oriented transmissions, whereas the co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network Security
A network security policy (NSP) is a generic document that outlines rules for computer network access, determines how policies are enforced and lays out some of the basic architecture of the company security/ network security environment. The document itself is usually several pages long and written by a committee. A security policy is a complex document, meant to govern data access, web- browsing habits, use of passwords, encryption, email attachments and more. It specifies these rules for individuals or groups of individuals throughout the company. The policies could be expressed as a set of instructions that understood by special purpose network hardware dedicated for securing the network. Security policy should keep the malicious users out and also exert control over potential risky users within an organization. Understanding what information and services are available and to which users, as well as what the potential is for damage and whether any protection is already in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Big Data
Though used sometimes loosely partly because of a lack of formal definition, the interpretation that seems to best describe Big data is the one associated with large body of information that we could not comprehend when used only in smaller amounts. In it primary definition though, Big data refers to data sets that are too large or complex to be dealt with by traditional data-processing application software. Data with many fields (rows) offer greater statistical power, while data with higher complexity (more attributes or columns) may lead to a higher false discovery rate. Big data analysis challenges include capturing data, data storage, data analysis, search, sharing, transfer, visualization, querying, updating, information privacy, and data source. Big data was originally associated with three key concepts: ''volume'', ''variety'', and ''velocity''. The analysis of big data presents challenges in sampling, and thus previously allowing for only observations and sampl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
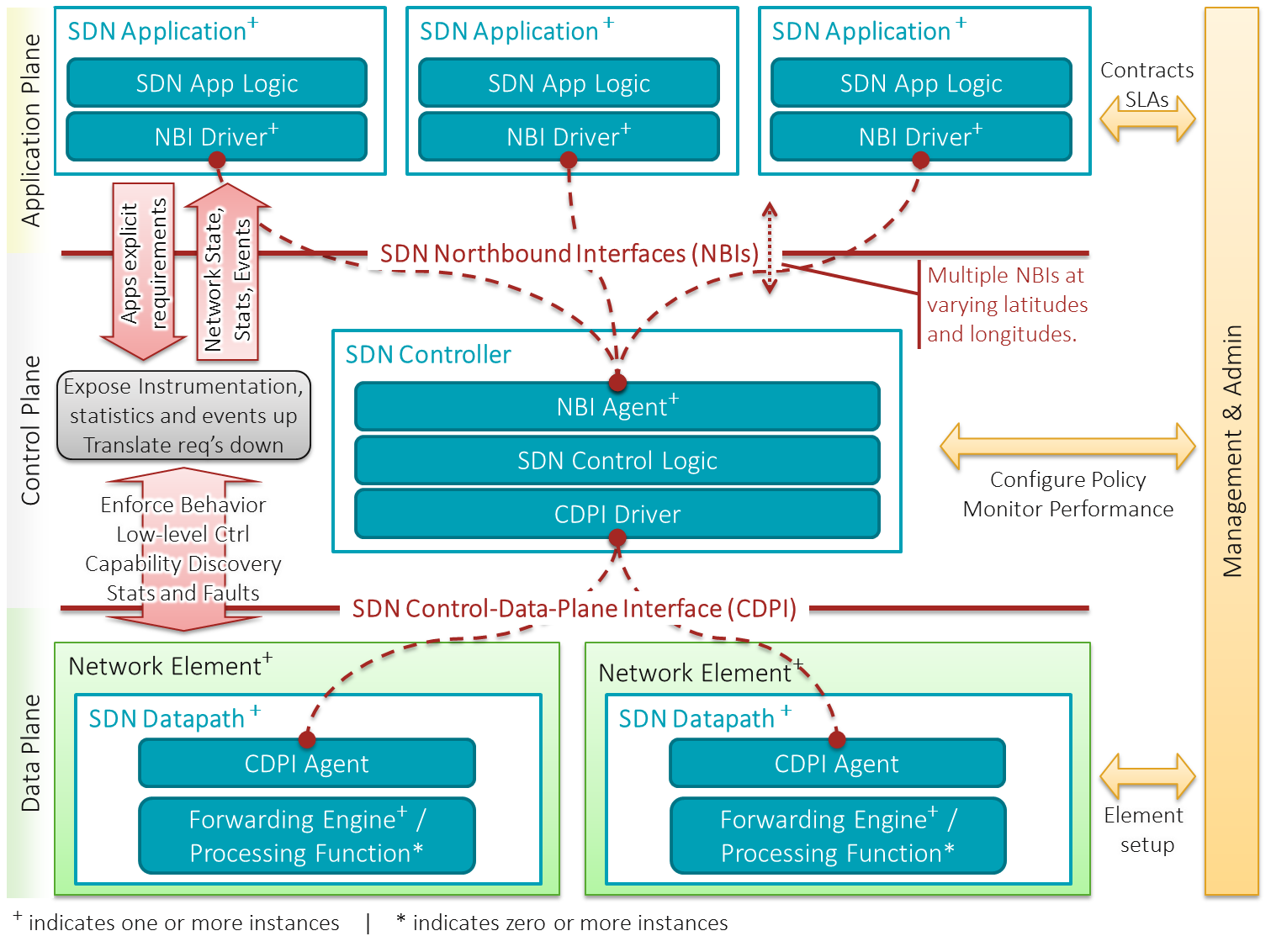
Software Defined Networking
Software-defined networking (SDN) technology is an approach to network management that enables dynamic, programmatically efficient network configuration in order to improve network performance and monitoring, making it more like cloud computing than traditional network management. SDN is meant to address the static architecture of traditional networks. SDN attempts to centralize network intelligence in one network component by disassociating the forwarding process of network packets (data plane) from the routing process (control plane). The control plane consists of one or more controllers, which are considered the brain of the SDN network where the whole intelligence is incorporated. However, centralization has its own drawbacks when it comes to security, scalability and elasticity and this is the main issue of SDN. SDN was commonly associated with the OpenFlow protocol (for remote communication with network plane elements for the purpose of determining the path of network packe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Layer 2 MPLS VPN
A Layer 2 MPLS VPN is a term in computer networking. It is a method that Internet service providers use to segregate their network for their customers, to allow them to transmit data over an IP network. This is often sold as a service to businesses. Layer 2 VPNs are a type of Virtual Private Network (VPN) that uses MPLS labels to transport data. The communication occurs between routers that are known as ''Provider Edge'' routers (PEs), as they sit on the edge of the provider's network, next to the customer's network. Internet providers who have an existing Layer 2 network (such as ATM or Frame Relay) may choose to use these VPNs instead of the other common MPLS VPN, Layer 3. There is no one IETF standard for Layer 2 MPLS VPNs. Instead, two methodologies may be used. Both methods use a standard MPLS header to encapsulate data. However, they differ in their signaling protocols. Types of Layer 2 MPLS VPNs BGP-based The BGP-based type is based on a draft specification by Kire ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PerfSONAR
A national research and education network (NREN) is a specialised internet service provider dedicated to supporting the needs of the research and education communities within a country. It is usually distinguished by support for a high-speed backbone network, often offering dedicated channels for individual research projects. In recent years NRENs have developed many 'above the net' services. List of NRENs by geographic area East and Southern Africa * UbuntuNet Alliance for Research and Education Networking - the Alliance of NRENs of East and Southern Africa * Eb@le - DRC NREN * EthERNet - Ethiopian NREN * iRENALA - Malagasy NREN * KENET - Kenyan NREN * MAREN - Malawian NREN * MoRENet - Mozambican NREN * RENU - Ugandan NREN * RwEdNet - Rwanda NREN * SomaliREN - Somali NREN SudREN- Sudanese NREN * TENET/ SANReN - South African NREN * TERNET - Tanzanian NREN * Xnet - Namibian NREN * ZAMREN - Zambian NREN North Africa ASREN- Arab States Research and Education Network * TU ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GridFTP
GridFTP is an extension of the File Transfer Protocol (FTP) for grid computing. The protocol was defined within the GridFTP working group of the Open Grid Forum. There are multiple implementations of the protocol; the most widely used is that provided by the Globus Toolkit. The aim of GridFTP is to provide a more reliable and high performance file transfer, for example to enable the transmission of very large files. GridFTP is used extensively within large science projects such as the Large Hadron Collider and by many supercomputer centers and other scientific facilities. GridFTP also addresses the problem of incompatibility between storage and access systems. Previously, each data provider would make their data available in their own specific way, providing a library of access functions. This made it difficult to obtain data from multiple sources, requiring a different access method for each, and thus dividing the total available data into partitions. GridFTP provides a unifo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Detection System
An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that analyzes incoming network traffic is an example of an NIDS. It is also possible to classify IDS by detection approach. The most well-known variants are signature-based detection (recogni ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Control Lists
In computer security, an access-control list (ACL) is a list of permissions associated with a system resource (object). An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject and an operation. For instance, if a file object has an ACL that contains , this would give Alice permission to read and write the file and give Bob permission only to read it. Implementations Many kinds of operating systems implement ACLs or have a historical implementation; the first implementation of ACLs was in the filesystem of Multics in 1965. Filesystem ACLs A filesystem ACL is a data structure (usually a table) containing entries that specify individual user or group rights to specific system objects such as programs, processes, or files. These entries are known as access-control entries (ACEs) in the Microsoft Windows NT, OpenVMS, and Unix-like operating sys ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bastion Host
A bastion host is a special-purpose computer on a network specifically designed and configured to withstand Cyberattack, attacks, so named by analogy to the bastion, military fortification. The computer generally hosts a single application or process, for example, a proxy server or Load_balancing_(computing), load balancer, and all other services are removed or limited to reduce the threat to the computer. It is Hardening (computing), hardened in this manner primarily due to its location and purpose, which is either on the outside of a Firewall (computing), firewall or inside of a demilitarized zone (demilitarized zone (computing), DMZ) and usually involves access from untrusted networks or computers. These computers are also equipped with special networking interfaces to withstand high-bandwidth Denial-of-service_attack, attacks through the internet. Definitions The term is generally attributed to a 1990 article discussing Firewall (networking), firewalls by Marcus J. Ranum, who de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DMZ Network Diagram 1 Firewall
A demilitarized zone (DMZ or DZ) is an area in which treaties or agreements between nations, military powers or contending groups forbid military installations, activities, or personnel. A DZ often lies along an established frontier or boundary between two or more military powers or alliances. A DZ may sometimes form a ''de facto'' international border, such as the Korean Demilitarized Zone. Other examples of demilitarized zones are a 9-mile wide area between Iraq and Kuwait; Antarctica (preserved for scientific exploration and study); and outer space (space more than from the earth's surface). Many demilitarized zones are considered neutral territory because neither side is allowed to control it, even for non-combat administration. Some zones remain demilitarized after an agreement has awarded control to a state which (under the DZ terms) had originally ceded its right to maintain military forces in the disputed territory. It is also possible for powers to agree on the de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |