|
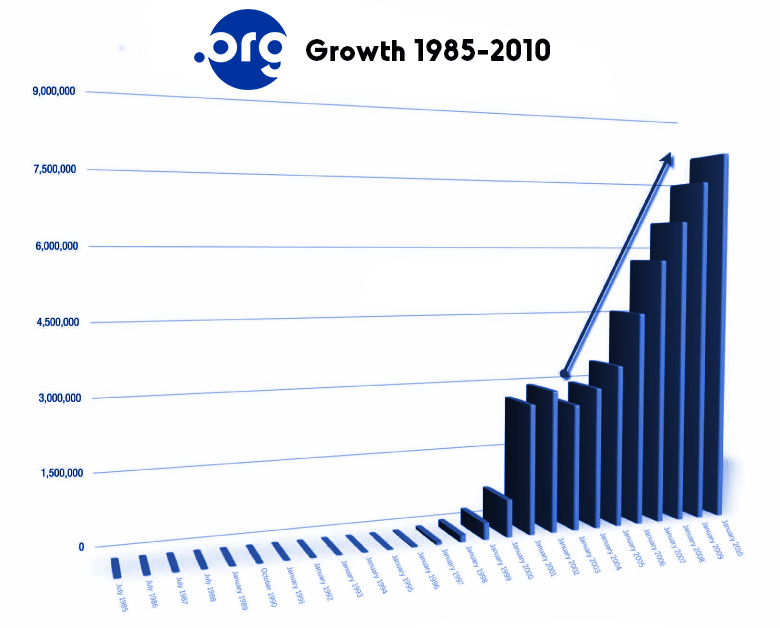
Public Interest Registry (2003)
Public Interest Registry is a not-for-profit based in Reston, Virginia, created by the Internet Society in 2002 to manage the .ORG top-level domain. It took over operation of .ORG in January 2003 and launched the .NGO and .ONG top-level domains in March 2015. In November 2019, it was announced the Public Interest Registry would be sold by the Internet Society to private equity investment firm Ethos Capital for 1.135 billion USD, but in April 2020, ICANN decided to reject the sale. Domains .ORG .ORG is the third largest generic top-level domain of the Domain Name System used in the internet. .ORG domains have been registered by Public Interest Registry since 2003. Craigslist.org and Wikipedia.org are among the more popular .org users. Since 2009, Public Interest Registry has published a bi-annual report called "The Dashboard" on the number of registered .ORG domains. There were more than 8 million registered .ORG in 2009, 8.8 million in 2010, and 9.6 million in 2011. Public In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nonprofit Organization
A nonprofit organization (NPO) or non-profit organisation, also known as a non-business entity, not-for-profit organization, or nonprofit institution, is a legal entity organized and operated for a collective, public or social benefit, in contrast with an entity that operates as a business aiming to generate a Profit (accounting), profit for its owners. A nonprofit is subject to the non-distribution constraint: any revenues that exceed expenses must be committed to the organization's purpose, not taken by private parties. An array of organizations are nonprofit, including some political organizations, schools, business associations, churches, social clubs, and consumer cooperatives. Nonprofit entities may seek approval from governments to be Tax exemption, tax-exempt, and some may also qualify to receive tax-deductible contributions, but an entity may incorporate as a nonprofit entity without securing tax-exempt status. Key aspects of nonprofits are accountability, trustworth ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spanish Language
Spanish ( or , Castilian) is a Romance languages, Romance language of the Indo-European language family that evolved from colloquial Latin spoken on the Iberian peninsula. Today, it is a world language, global language with more than 500 million native speakers, mainly in the Americas and Spain. Spanish is the official language of List of countries where Spanish is an official language, 20 countries. It is the world's list of languages by number of native speakers, second-most spoken native language after Mandarin Chinese; the world's list of languages by total number of speakers, fourth-most spoken language overall after English language, English, Mandarin Chinese, and Hindustani language, Hindustani (Hindi-Urdu); and the world's most widely spoken Romance languages, Romance language. The largest population of native speakers is in Mexico. Spanish is part of the Iberian Romance languages, Ibero-Romance group of languages, which evolved from several dialects of Vulgar Latin in I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DNS Spoofing
DNS spoofing, also referred to as DNS cache poisoning, is a form of computer security hacking in which corrupt Domain Name System data is introduced into the DNS resolver's cache, causing the name server to return an incorrect result record, e.g. an IP address. This results in traffic being diverted to the attacker's computer (or any other computer). Overview of the Domain Name System A Domain Name System server translates a human-readable domain name (such as example.com) into a numerical IP address that is used to route communications between nodes. Normally if the server does not know a requested translation it will ask another server, and the process continues recursively. To increase performance, a server will typically remember (cache) these translations for a certain amount of time. This means if it receives another request for the same translation, it can reply without needing to ask any other servers, until that cache expires. When a DNS server has received a false ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Name System Security Extensions
The Domain Name System Security Extensions (DNSSEC) are a suite of extension specifications by the Internet Engineering Task Force (IETF) for securing data exchanged in the Domain Name System (DNS) in Internet Protocol (IP) networks. The protocol provides cryptographic authentication of data, authenticated denial of existence, and data integrity, but not availability or confidentiality. Overview The original design of the Domain Name System did not include any security features. It was conceived only as a scalable distributed system. The Domain Name System Security Extensions (DNSSEC) attempt to add security, while maintaining backward compatibility. Request for Comments 3833 documents some of the known threats to the DNS, and their solutions in DNSSEC. DNSSEC was designed to protect applications using DNS from accepting forged or manipulated DNS data, such as that created by DNS cache poisoning. All answers from DNSSEC protected zones are digitally signed. By checking the digit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Marc Rotenberg
Marc Rotenberg is president and founder of the Center for AI and Digital Policy, an independent non-profit organization, incorporated in Washington, D.C. Rotenberg is the editor of ''The AI Policy Sourcebook'', a member of the OECD Expert Group on AI, and helped draft the Universal Guidelines for AI. He teaches the GDPR and privacy law at Georgetown Law and is coauthor of ''Privacy Law and Society'' (West Academic 2016) and ''The Privacy Law Sourcebook'' (2020). Rotenberg is a founding board member and former chair of the Public Interest Registry, which manages the .ORG domain. Center for AI and Digital Policy The Center for AI and Digital Policy (CAIDP) aims to promote a better society, more fair, more just — "a world where technology promotes broad social inclusion based on fundamental rights, democratic institutions, and the rule of law." CAIDP began as a project of the Michael Dukakis Institute. CAIDP has provided AI policy advice to the African Commission on Human and P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VeriSign
Verisign Inc. is an American company based in Reston, Virginia, United States that operates a diverse array of network infrastructure, including two of the Internet's thirteen root nameservers, the authoritative registry for the , , and generic top-level domains and the and country-code top-level domains, and the back-end systems for the , , and sponsored top-level domains. In 2010, Verisign sold its authentication business unit – which included Secure Sockets Layer (SSL) certificate, public key infrastructure (PKI), Verisign Trust Seal, and Verisign Identity Protection (VIP) services – to Symantec for $1.28 billion. The deal capped a multi-year effort by Verisign to narrow its focus to its core infrastructure and security business units. Symantec later sold this unit to DigiCert in 2017. On October 25, 2018, NeuStar, Inc. acquired VeriSign’s Security Service Customer Contracts. The acquisition effectively transferred Verisign Inc.’s Distributed Denial of Service ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Name
A domain name is a string that identifies a realm of administrative autonomy, authority or control within the Internet. Domain names are often used to identify services provided through the Internet, such as websites, email services and more. As of 2017, 330.6 million domain names had been registered. Domain names are used in various networking contexts and for application-specific naming and addressing purposes. In general, a domain name identifies a network domain or an Internet Protocol (IP) resource, such as a personal computer used to access the Internet, or a server computer. Domain names are formed by the rules and procedures of the Domain Name System (DNS). Any name registered in the DNS is a domain name. Domain names are organized in subordinate levels (subdomains) of the DNS root domain, which is nameless. The first-level set of domain names are the top-level domains (TLDs), including the generic top-level domains (gTLDs), such as the prominent domains com, info, net ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Afilias
Afilias, Inc. is a US corporation that is the registry operator of the .info, .mobi and .pro top-level domain, service provider for registry operators of .org, .ngo, .lgbt, .asia, .aero, and a provider of domain name registry services for countries around the world, including .MN (Mongolia), .AG (Antigua and Barbuda), .BM (Bermuda), .BZ (Belize), . AC (Ascension Island), .GI (Gibraltar), .IO (Indian Ocean) .ME (Montenegro), .PR (Puerto Rico), .SC (the Seychelles), .SH (Saint Helena), .VC (St. Vincent and the Grenadines), and .AU (Australia). Afilias also provided ancillary support to other domains, including .SG (Singapore), .LA (Laos), and .HN (Honduras). History Afilias was formed in October 2000 by a group of 19 major domain name registrars. CEO Hal Lubsen, CTO Ram Mohan, CMO Roland LaPlante and Compliance Officer Steven Pack were the founding management team (2001). In February 2010, Afilias acquired mTLD Top Level Domain Ltd., the sponsoring organization and registry oper ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim. As of 2020, phishing is by far the most common attack performed by cybercriminals, the FBI's Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime. The first recorded use of the term "phishing" was in the cracking toolkit AOHell created by Koceilah Rekouche in 1995; however, it is possible that the term was used before this in a print edition of the hacker magazin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ad Filtering
Ad blocking or ad filtering is a software capability for blocking or altering online advertising in a web browser, an application or a network. This may be done using browser extensions or other methods. Technologies and native countermeasures Online advertising exists in a variety of forms, including web banners, pictures, animations, embedded audio and video, text, or pop-up windows, and can even employ audio and video autoplay. Many browsers offer some ways to remove or alter advertisements: either by targeting technologies that are used to deliver ads (such as embedded content delivered through browser plug-ins or via HTML5), targeting URLs that are the source of ads, or targeting behaviors characteristic to ads (such as the use of HTML5 AutoPlay of both audio and video). Prevalence Use of mobile and desktop ad blocking software designed to remove traditional advertising grew by 41% worldwide and by 48% in the U.S. between Q2 2014 and Q2 2015. As of Q2 2015, 45 million A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WHOIS
WHOIS (pronounced as the phrase "who is") is a query and response protocol that is widely used for querying databases that store the registered users or assignees of an Internet resource, such as a domain name, an IP address block or an autonomous system, but is also used for a wider range of other information. The protocol stores and delivers database content in a human-readable format.RFC 3912, ''WHOIS Protocol Specification'', L. Daigle (September 2004) The current iteration of the WHOIS protocol was drafted by the Internet Society, and is documented in . Whois is also the name of the command-line utility on most UNIX systems used to make WHOIS protocol queries. In addition WHOIS has a sister protocol called ''Referral Whois'' ( RWhois). History Elizabeth Feinler and her team (who had created the Resource Directory for ARPANET) were responsible for creating the first WHOIS directory in the early 1970s. Feinler set up a server in Stanford's Network Information Center (NIC) w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Tasting
Domain tasting is the practice of temporarily registering a domain under the five-day Add Grace Period at the beginning of the registration of an ICANN-regulated second-level domain. During this period, a registration must be fully refunded by the domain name registry if cancelled. This was designed to address accidental registrations, but domain tasters use the Add Grace Period for illegal purposes. Overview In April 2006, out of 35 million registrations, about 2 million were permanent or actually purchased. By February 2007, the CEO of Go Daddy reported that of 55.1 million domain names registered, 51.5 million were canceled and refunded just before the 5 day grace period expired and only 3.6 million domain names were actually kept. ICANN's registry report for February 2007 shows that 55,794,877 .com and .net domain names were deleted in that month alone. Domain tasting is lucrative in a number of ways: # The registrant conducts a cost-benefit analysis on the viability of deri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |