|
Phone Phreak
Phreaking is a slang term coined to describe the activity of a culture of people who study, experiment with, or explore telecommunication systems, such as equipment and systems connected to public telephone networks. The term ''phreak'' is a sensational spelling of the word '' freak'' with the ''ph-'' from '' phone'', and may also refer to the use of various audio frequencies to manipulate a phone system. ''Phreak'', ''phreaker'', or ''phone phreak'' are names used for and by individuals who participate in phreaking. The term first referred to groups who had reverse engineered the system of tones used to route long-distance calls. By re-creating the signaling tones, phreaks could switch calls from the phone handset while avoiding long-distance calling charges which were common then. These fees could be significant, depending on the time, duration and destination of the call. To ease the creation of the routing tones, electronic tone generators known as blue boxes became a stap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Slang
A slang is a vocabulary (words, phrases, and linguistic usages) of an informal register, common in everyday conversation but avoided in formal writing and speech. It also often refers to the language exclusively used by the members of particular in-groups in order to establish group identity, exclude outsiders, or both. The word itself came about in the 18th century and has been defined in multiple ways since its conception, with no single technical usage in linguistics. Etymology of the word ''slang'' In its earliest attested use (1756), the word ''slang'' referred to the vocabulary of "low" or "disreputable" people. By the early nineteenth century, it was no longer exclusively associated with disreputable people, but continued to be applied to usages below the level of standard educated speech. In Scots dialect it meant "talk, chat, gossip", as used by Aberdeen poet William Scott in 1832: "The slang gaed on aboot their war'ly care." In northern English dialect it me ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Hacker Crackdown
''The Hacker Crackdown: Law and Disorder on the Electronic Frontier'' is a work of nonfiction by Bruce Sterling first published in 1992. The book discusses watershed events in the hacker subculture in the early 1990s. The most notable topic covered is Operation Sundevil and the events surrounding the 1987–1990 war on the Legion of Doom network: the raid on Steve Jackson Games, the trial of "Knight Lightning" (one of the original journalists of ''Phrack''), and the subsequent formation of the Electronic Frontier Foundation. The book also profiles the likes of " Emmanuel Goldstein" (publisher of '' 2600: The Hacker Quarterly''), the former assistant attorney general of Arizona Gail Thackeray, FLETC instructor Carlton Fitzpatrick, Mitch Kapor, and John Perry Barlow. In 1994, Sterling released the book for the Internet with a new afterword. Critical reception Cory Doctorow, who voiced an unabridged podcast of the book, said it "inspired me politically, artistically and socially ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
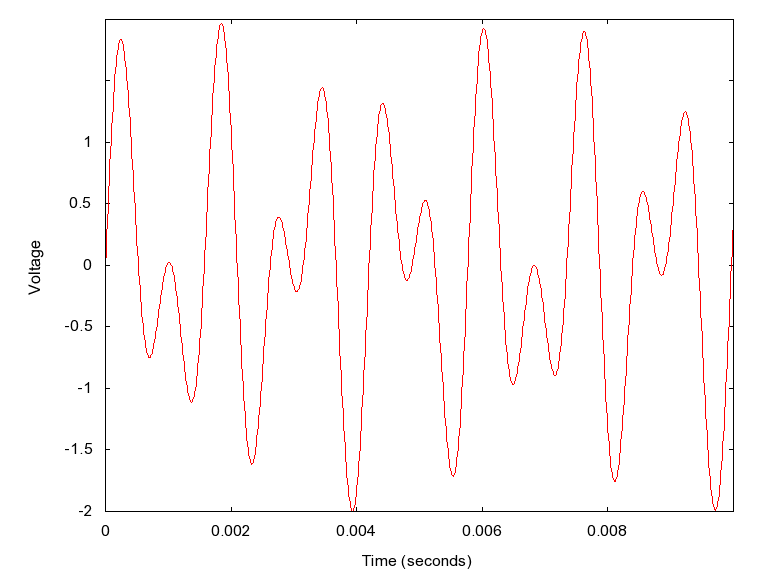
DTMF
Dual-tone multi-frequency (DTMF) signaling is a telecommunication signaling system using the voice-frequency band over telephone lines between telephone equipment and other communications devices and switching centers. DTMF was first developed in the Bell System in the United States, and became known under the trademark Touch-Tone for use in push-button telephones, starting in 1963. The DTMF frequencies are standardized in ITU-T Recommendation Q.23. The signaling system is also known as ''MF4'' in the United Kingdom, as ''MFV'' in Germany, and ''Digitone'' in Canada. Touch-tone dialing with a telephone keypad gradually replaced the use of rotary dials and has become the industry standard in telephony to control equipment and signal user intent. The signaling on trunks in the telephone network uses a different type of multi-frequency signaling. Multifrequency signaling Before the development of DTMF, telephone numbers were dialed with rotary dials for loop-disconnect (LD) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backward Compatibility
In telecommunications and computing, backward compatibility (or backwards compatibility) is a property of an operating system, software, real-world product, or technology that allows for interoperability with an older legacy system, or with Input/output, input designed for such a system. Modifying a system in a way that does not allow backward compatibility is sometimes called "wikt:breaking change, breaking" backward compatibility. Such breaking usually incurs various types of costs, such as Switching barriers, switching cost. A complementary concept is ''forward compatibility''; a design that is forward-compatible usually has a Technology roadmap, roadmap for compatibility with future standards and products. Usage In hardware A simple example of both backward and forward compatibility is the introduction of FM broadcasting, FM radio in stereophonic sound, stereo. FM radio was initially monaural, mono, with only one audio channel represented by one signal (electrical engineerin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dual-tone Multi-frequency Signaling
Dual-tone multi-frequency (DTMF) signaling is a telecommunication signaling system using the voice-frequency band over telephone lines between telephone equipment and other communications devices and Automatic telephone exchange, switching centers. DTMF was first developed in the Bell System in the United States, and became known under the trademark Touch-Tone for use in push-button telephones, starting in 1963. The DTMF frequencies are standardized in ITU-T Recommendation Q.23. The signaling system is also known as ''MF4'' in the United Kingdom, as ''MFV'' in Germany, and ''Digitone'' in Canada. Touch-tone dialing with a telephone keypad gradually replaced the use of rotary dials and has become the industry standard in telephony to control equipment and signal user intent. The signaling on trunks in the telephone network uses a different type of multi-frequency signaling. Multifrequency signaling Before the development of DTMF, telephone numbers were dialed with rotary dials ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Law Enforcement
Law enforcement is the activity of some members of the government or other social institutions who act in an organized manner to enforce the law by investigating, deterring, rehabilitating, or punishing people who violate the rules and norms governing that society. The term encompasses police, courts and corrections. These three components of the criminal justice system may operate independently of each other or collectively through the use of record sharing and cooperation. Throughout the world, law enforcement are also associated with protecting the public, life, property, and keeping the peace in society. The concept of law enforcement dates back to ancient times, and forms of law enforcement and police have existed in various forms across many human societies. Modern state legal codes use the term law enforcement officer or peace officer to include every person vested by the legislating state with police power or authority; traditionally, anyone sworn or badged who can arrest ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Toll (telecommunications)
Toll, in the telecom industry, refers to a charge collected by either an Incumbent Local Exchange Carrier, or a Competitive Local Exchange Carrier on a telephone call. Toll is one class of charges in telecom. Typically, it is charged for crossing a boundary, whether the boundary is a Local access and transport area (LATA), a Number Portability Administration Center The Number Portability Administration Center (NPAC) is a function of the Federal Communications Commission (FCC) in the United States. It administers the routing of telephone calls and text messaging, text messages (SMS) for the telecommunications i ... (NPAC) region, or an international border. References See also * Toll switching trunk Telecommunications economics {{telephony-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
History Of Hacking
The list of security hacking incidents covers important or noteworthy events in the history of security hacking and cracking. 1900 1903 * Magician and inventor Nevil Maskelyne disrupts John Ambrose Fleming's public demonstration of Guglielmo Marconi's purportedly secure wireless telegraphy Wireless telegraphy or radiotelegraphy is the transmission of text messages by radio waves, analogous to electrical telegraphy using electrical cable, cables. Before about 1910, the term ''wireless telegraphy'' was also used for other experimenta ... technology, sending insulting Morse code messages through the auditorium's projector. 1930s 1932 * Polish cryptologists Marian Rejewski, Henryk Zygalski and Jerzy Różycki broke the Cryptanalysis of the Enigma, Enigma machine code. 1939 * Alan Turing, Gordon Welchman and Harold Keen worked together to develop the codebreaking device Bombe (on the basis of Rejewski's works on Bomba (cryptography), Bomba). The Enigma machine's use of a reli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Box (phreaking)
A red box is a phreaking device that generates tones to simulate inserting coins in pay phones, thus fooling the system into completing free calls. In the United States, a nickel is represented by one tone, a dime by two, and a quarter by a set of five. Any device capable of playing back recorded sounds can potentially be used as a red box. Commonly used devices include modified Radio Shack tone dialers, personal MP3 players, and audio-recording greeting cards. History The term "red box" to refer to a phreaking box dates to 1973 or earlier. Red box use became more widespread in the 1990s following the publication in 2600 Magazine of instructions on how to make a red box by replacing a crystal oscillator in a tone dialer. Red boxes grew obsolete in the 2000s as phone systems in the US and other nations updated their signaling technology. Technical details United States The tones are made by playing back 1700 Hz and 2200 Hz tones together. One 66 ms tone represents a n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Black Box (phreaking)
Black boxes were devices which, when attached to home phones, allowed all incoming calls to be received without charge to the caller. The black box (as distinguished from blue boxes and red boxes) was a small electronic circuit, usually a resistor or zener diode in series with the line. It relied on (now-obsolete) telephone exchanges controlled by mechanical relays. These exchanges used a relay to detect a drop in line voltage (usually to less than -10V off-hook, compared to -48V when on-hook) to begin billing for a call; a separate relay controlled ringing on the line. The black box placed a resistor in series with the line, so that the off-hook voltage was closer to -36V: just enough to stop the ringing, but not enough to trigger billing. A bypass capacitor was often added to prevent the device from attenuating AC signals such as transmitted voice. A call originating from a telephone fitted with a black box would still be charged for by the telephone company unless some meth ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blue Box (phreaking)
A blue box is an electronic device that produces tones used to generate the in-band signaling tones formerly used within the North American long-distance telephone network to send line status and called number information over voice circuits. During that period, charges associated with long-distance calling were commonplace and could be significant, depending on the time, duration and destination of the call. A blue box device allowed for circumventing these charges by enabling an illicit user, referred to as a " phreaker", to place long-distance calls, without using the network's user facilities, that would be billed to another number or dismissed entirely by the telecom company's billing system as an incomplete call. A number of similar "color boxes" were also created to control other aspects of the phone network. First developed in the 1960s and used by a small phreaker community, the introduction of low-cost microelectronics in the early 1970s greatly simplified these devi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Social Engineering (security)
In the context of information security, social engineering is the use of psychological influence of people into performing actions or divulging Confidentiality, confidential information. This differs from psychological manipulation in that it doesn't need to be controlling, negative or a one-way transaction. Manipulation involves a zero-sum game where one party wins and the other loses while social engineering can be win-win for both parties. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional "con" in the sense that it is often one of many steps in a more complex fraud scheme. It has also been defined as "any act that influences a person to take an action that may or may not be in their best interests." Research done in 2020 has indicated that social engineering will be one of the most prominent challenges of the upcoming decade. Having proficiency in social engineering will be increasingly important for orga ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |