|
PKCS11
In cryptography, PKCS #11 is a Public-Key Cryptography Standards that defines a C programming interface to create and manipulate cryptographic tokens that may contain secret cryptographic keys. It is often used to communicate with a Hardware Security Module or smart cards. The PKCS #11 standard is managed by OASIS with the current version being 3.1 PKCS #11 is sometimes referred to as "Cryptoki" (from "cryptographic token interface" and pronounced as "crypto-key"). The API defines most commonly used cryptographic object types ( RSA keys, X.509 certificates, DES/Triple DES keys, etc.) and all the functions needed to use, create/generate, modify and delete those objects. Usage Most commercial certificate authority (CA) software uses PKCS #11 to access the CA signing key or to enroll user certificates. Cross-platform software that needs to use smart cards uses PKCS #11, such as Mozilla Firefox and OpenSSL (using an extension). It is also used to access smart cards and HS ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft CryptoAPI
The Microsoft Windows platform specific Cryptographic Application Programming Interface (also known variously as CryptoAPI, Microsoft Cryptography API, MS-CAPI or simply CAPI) is an application programming interface included with Microsoft Windows operating systems that provides services to enable developers to secure Windows-based applications using cryptography. It is a set of dynamically linked libraries that provides an abstraction layer which isolates programmers from the code used to encrypt the data. The Crypto API was first introduced in Windows NT 4.0 and enhanced in subsequent versions. CryptoAPI supports both public-key and symmetric key cryptography, though persistent symmetric keys are not supported. It includes functionality for encrypting and decrypting data and for authentication using digital certificates. It also includes a cryptographically secure pseudorandom number generator function CryptGenRandom. CryptoAPI works with a number of CSPs ( Cryptographic Serv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
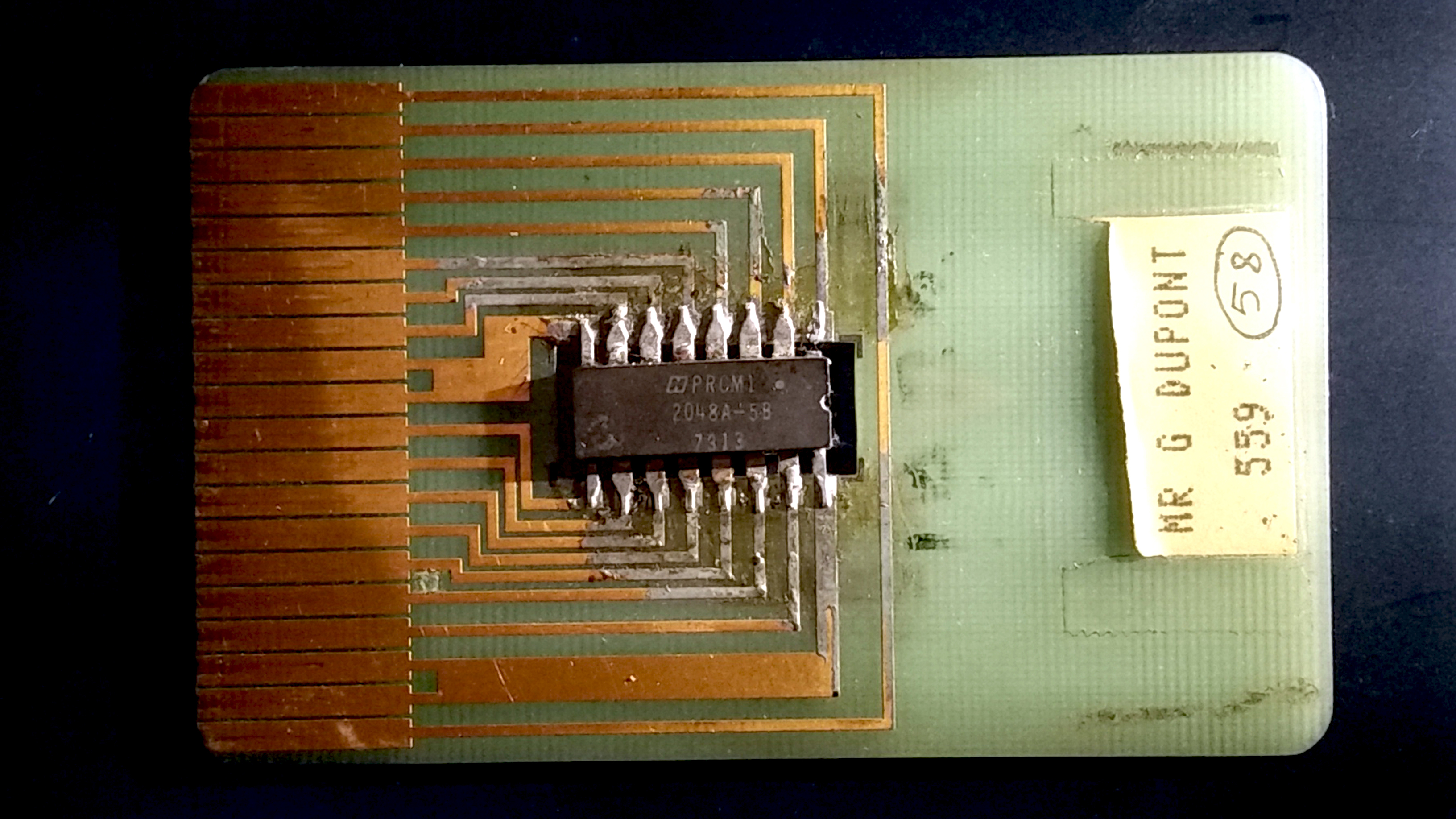
Smart Cards
A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an Embedded system, embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are Contactless smart card, contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card (UICC) for mobile phones, installed as pluggable SIM card or embedded eSIM, is also a type of smart card. , 10.5billion smart card IC chips are manufactured annually ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Application Programming Interface
The Microsoft Windows platform specific Cryptographic Application Programming Interface (also known variously as CryptoAPI, Microsoft Cryptography API, MS-CAPI or simply CAPI) is an application programming interface included with Microsoft Windows operating systems that provides services to enable developers to secure Windows-based applications using cryptography. It is a set of dynamically linked libraries that provides an abstraction layer which isolates programmers from the code used to encrypt the data. The Crypto API was first introduced in Windows NT 4.0 and enhanced in subsequent versions. CryptoAPI supports both public-key and symmetric key cryptography, though persistent symmetric keys are not supported. It includes functionality for encrypting and decrypting data and for authentication using digital certificates. It also includes a cryptographically secure pseudorandom number generator function CryptGenRandom. CryptoAPI works with a number of CSPs ( Cryptographic Serv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hardware Security Module
A hardware security module (HSM) is a physical computing device that safeguards and manages secrets (most importantly digital keys), and performs encryption and decryption functions for digital signatures, strong authentication and other cryptographic functions. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessor chips. Design HSMs may have features that provide tamper evidence such as visible signs of tampering or logging and alerting, or tamper resistance which makes tampering difficult without making the HSM inoperable, or tamper responsiveness such as deleting keys upon tamper detection. Each module contains one or more secure cryptoprocessor chips to prevent tampering and bus probing, or a combination of chips in a module that is protected by the tamper evident, tamper resistant, or tamper responsive packaging. A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-time Password
A one-time password (OTP), also known as a one-time PIN, one-time passcode, one-time authorization code (OTAC) or dynamic password, is a password that is valid for only one login session or transaction, on a computer system or other digital device. OTPs avoid several shortcomings that are associated with traditional (static) password-based authentication; a number of implementations also incorporate two-factor authentication by ensuring that the one-time password requires access to ''something a person has'' (such as a small keyring fob device with the OTP calculator built into it, or a smartcard or specific cellphone) as well as ''something a person knows'' (such as a PIN). OTP generation algorithms typically make use of pseudorandomness or randomness to generate a shared key or seed, and cryptographic hash functions, which can be used to derive a value but are hard to reverse and therefore difficult for an attacker to obtain the data that was used for the hash. This is necessa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PKCS
Public Key Cryptography Standards (PKCS) are a group of public-key cryptography standards devised and published by RSA Security LLC, starting in the early 1990s. The company published the standards to promote the use of the cryptography techniques for which they had patents, such as the RSA algorithm, the Schnorr signature algorithm and several others. Though not industry standards (because the company retained control over them), some of the standards have begun to move into the " standards track" processes of relevant standards organizations in recent years, such as the IETF The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster ... and the PKIX working group. Key Updates (2023–2024): * Integration of PKCS #7 and PKCS #12 into broader standards like S/MIME and TLS. * Evolu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSA Security
RSA Security LLC, formerly RSA Security, Inc. and trade name RSA, is an American computer security, computer and network security company with a focus on encryption and decryption standards. RSA was named after the initials of its co-founders, Ron Rivest, Adi Shamir and Leonard Adleman, after whom the RSA (algorithm), RSA public key cryptography algorithm was also named. Among its products is the SecurID authentication token. The BSAFE cryptography libraries were also initially owned by RSA. RSA is known for incorporating backdoors developed by the National Security Agency, NSA in its products. It also organizes the annual RSA Conference, an information security conference. Founded as an independent company in 1982, RSA Security was acquired by EMC Corporation in 2006 for US$2.1 billion and operated as a division within EMC. When EMC was acquired by Dell Technologies in 2016, RSA became part of the Dell Technologies family of brands. On 10 March 2020, Dell Technologies announced ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Management Interoperability Protocol
The Key Management Interoperability Protocol (KMIP) is an extensible communication protocol that defines message formats for the manipulation of cryptographic keys on a key management server. This facilitates data encryption by simplifying encryption key management. Keys may be created on a server and then retrieved, possibly wrapped by other keys. Both symmetric-key algorithm, symmetric and public-key cryptography, asymmetric keys are supported, including the ability to sign certificates. KMIP also allows for clients to ask a server to encrypt or decrypt data, without needing direct access to the key. The KMIP standard was first released in 2010. Clients and servers are commercially available from multiple vendors (e.g.Infisical KMIP. The KMIP standard effort is governed by the OASIS (organization), OASIS standards body. Technical details can also be found on the official KMIP page and kmip wiki. Description A KMIP server stores and controls ''Managed Objects'' like symmetric an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Hat Enterprise Linux
Red Hat Enterprise Linux (RHEL) is a commercial Linux distribution developed by Red Hat. Red Hat Enterprise Linux is released in server versions for x86-64, Power ISA, ARM64, and IBM Z and a desktop version for x86-64. Fedora Linux and CentOS Stream serve as its upstream sources. All of Red Hat's official support and training, together with the Red Hat Certification Program, focuses on the Red Hat Enterprise Linux platform. The first version of Red Hat Enterprise Linux to bear the name originally came onto the market as "Red Hat Linux Advanced Server". In 2003, Red Hat rebranded Red Hat Linux Advanced Server to "Red Hat Enterprise Linux AS" and added two more variants, Red Hat Enterprise Linux ES and Red Hat Enterprise Linux WS. As Red Hat Enterprise Linux is heavily based on open-source software and its source code is available to the public, it is used as the basis for several third-party derivatives, including the commercial Oracle Linux and the community-support ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Solaris (operating System)
Oracle Solaris is a proprietary software, proprietary Unix operating system offered by Oracle Corporation, Oracle for SPARC and x86-64 based workstations and server (computing), servers. Originally developed by Sun Microsystems as Solaris, it superseded the company's earlier SunOS in 1993 and became known for its scalability, especially on SPARC systems, and for originating many innovative features such as DTrace, ZFS and Time Slider. After the Acquisition of Sun Microsystems by Oracle Corporation, Sun acquisition by Oracle in 2010, it was renamed Oracle Solaris. Solaris was registered as compliant with the Single UNIX Specification until April 29, 2019. Historically, Solaris was developed as proprietary software. In June 2005, Sun Microsystems released most of the codebase under the CDDL license, and founded the OpenSolaris Open-source software, open-source project. Sun aimed to build a developer and user community with OpenSolaris; after the Oracle acquisition in 2010, the Open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sectors of the computing industry – Windows (unqualified) for a consumer or corporate workstation, Windows Server for a Server (computing), server and Windows IoT for an embedded system. Windows is sold as either a consumer retail product or licensed to Original equipment manufacturer, third-party hardware manufacturers who sell products Software bundles, bundled with Windows. The first version of Windows, Windows 1.0, was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). The name "Windows" is a reference to the windowing system in GUIs. The 1990 release of Windows 3.0 catapulted its market success and led to various other product families ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |