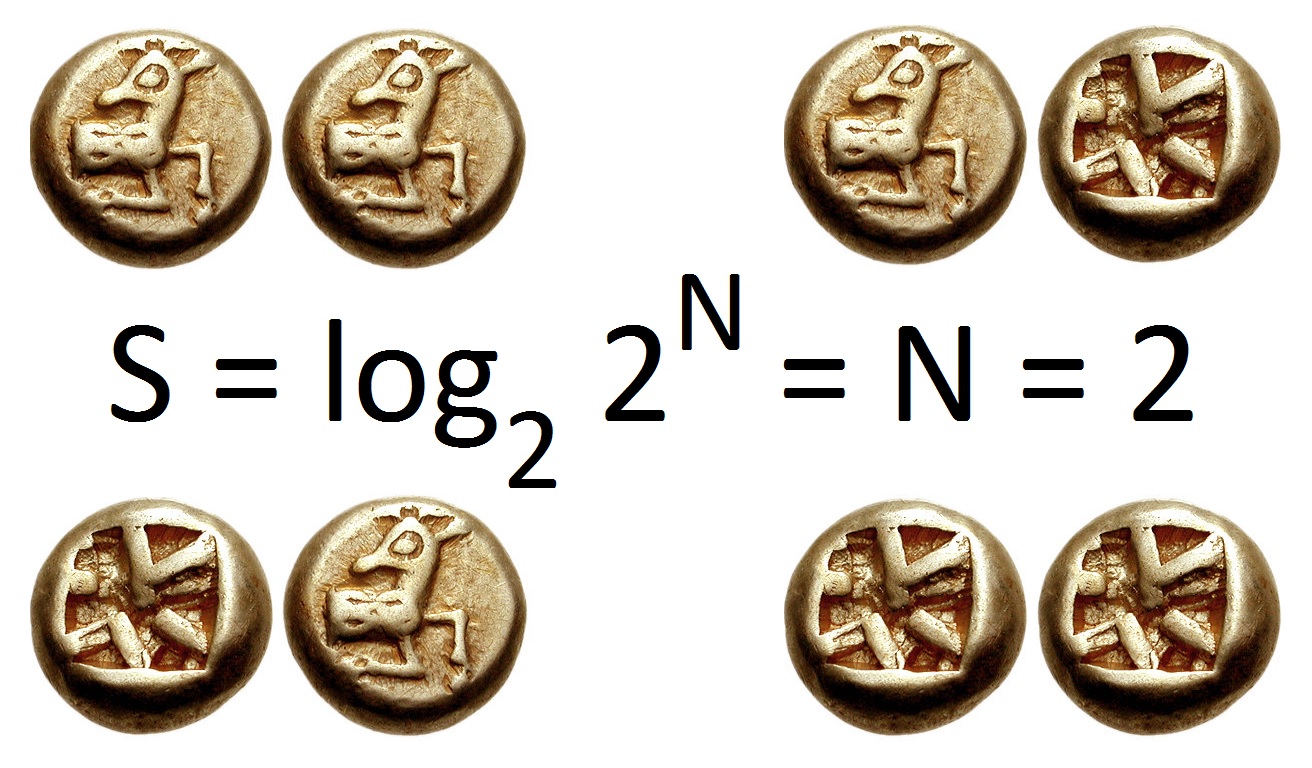|
Off-the-record Messaging
Off-the-record Messaging (OTR) is a cryptographic protocol that provides encryption for instant messaging conversations. OTR uses a combination of Advanced Encryption Standard, AES symmetric-key algorithm with 128 bits key length, the Diffie–Hellman key exchange with 1536 bits group size, and the SHA-1 hash function. In addition to authentication and encryption, OTR provides forward secrecy and Malleability (cryptography), malleable encryption. The primary motivation behind the protocol was providing deniable authentication for the conversation participants while keeping conversations confidential, like a private conversation in real life, or journalism sourcing#Using confidential information, off the record in journalism sourcing. This is in contrast with cryptography tools that produce output which can be later used as a verifiable record of the communication event and the identities of the participants. The initial introductory paper was named "Off-the-Record Communication, or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Protocol
A cryptographic protocol is an abstract or concrete Communications protocol, protocol that performs a information security, security-related function and applies cryptographic methods, often as sequences of cryptographic primitives. A protocol describes how the algorithms should be used and includes details about data structures and representations, at which point it can be used to implement multiple, interoperable versions of a program. Cryptographic protocols are widely used for secure application-level data transport. A cryptographic protocol usually incorporates at least some of these aspects: * Key agreement or establishment * Entity authentication * Symmetric encryption and message authentication key (cryptography), material construction * Secured application-level data transport * Non-repudiation methods * Secret sharing methods * Secure multi-party computation For example, Transport Layer Security (TLS) is a cryptographic protocol that is used to secure web (HTTPS) conne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kopete
Kopete was a multi-protocol, free software instant messaging client released as part of the KDE Software Compilation. Although it can run in numerous environments, it was designed for and integrates with the KDE Plasma Workspaces. Kopete was started because ICQ blocked Licq from their network in 2001. According to the original author, Duncan Mac-Vicar Prett, the name comes from the Chilean Spanish word ''copete'', meaning "a drink with your friends". Kopete has been nominated for multiple awards. (2nd place, Favorite Instant Messaging Client) (Best Communications Software, Runner Up) The designated successor is KDE Telepathy from the KDE RTCC Initiative. Protocols Kopete allows users to connect to the following protocols: MSNP (Microsoft Messenger service, commonly known as ''MSN'', ''.NET'', or ''Live'') was also supported until the protocol was discontinued by Microsoft. Features Plugins By default, Kopete supports the following plugins (not all of which are current ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OMEMO
OMEMO is an extension to the Extensible Messaging and Presence Protocol (XMPP) for multi-client end-to-end encryption developed by Andreas Straub. According to Straub, OMEMO uses the Double Ratchet Algorithm "to provide multi-end to multi-end encryption, allowing messages to be synchronized securely across multiple clients, even if some of them are offline". The name "OMEMO" is a recursive acronym for "OMEMO Multi-End Message and Object Encryption". It is an open standard based on the Double Ratchet Algorithm and the Personal Eventing Protocol (PEP, XEP-0163). OMEMO offers future and forward secrecy and deniability with message synchronization and offline delivery. Features In comparison with OTR, the OMEMO protocol offers many-to-many encrypted chat, offline messages queuing, forward secrecy, file transfer, verifiability and deniability at the cost of slightly larger message size overhead. History The protocol was developed and first implemented by Andreas Straub as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Silent Circle Instant Messaging Protocol
Silent Circle is an encrypted communications firm based in Washington DC. Silent Circle provides multi-platform secure communication services for mobile devices and desktops. Launched October 16, 2012, the company operates under a subscription business model. The encryption part of the software used is free software/open source and peer-reviewed. For the remaining parts of Silent Phone and Silent Text, the source code is available on GitHub, but under proprietary software licenses. History In November 2011, Mike Janke called Phil Zimmermann with an idea for a new kind of private, secure version of Skype. Zimmermann agreed to the project and called Jon Callas, co-founder of PGP Corporation and Vincent Moscaritolo. Janke brought in security expert Vic Hyder, and the founding team was established. The company was founded in the Caribbean island of Nevis, but moved its headquarters to Le Grand-Saconnex near Geneva, Switzerland in 2014 in search of a country with "stronger privacy la ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signal Protocol
The Signal Protocol (formerly known as the TextSecure Protocol) is a non- federated cryptographic protocol that provides end-to-end encryption for voice and instant messaging conversations. The protocol was developed by Open Whisper Systems in 2013 and was introduced in the open-source TextSecure app, which later became Signal. Several closed-source applications have implemented the protocol, such as WhatsApp, which is said to encrypt the conversations of "more than a billion people worldwide" or Google who provides end-to-end encryption by default to all RCS-based conversations between users of their Google Messages app for one-to-one conversations. Facebook Messenger also say they offer the protocol for optional "Secret Conversations", as did Skype for its "Private Conversations". The protocol combines the Double Ratchet Algorithm, prekeys (i.e., one-time ephemeral public keys that have been uploaded in advance to a central server), and a triple elliptic-curve Diffie–Hellm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptocat
Cryptocat is a discontinued open-source software, open-source Application software, desktop application intended to allow encrypted online chatting available for Microsoft Windows, Windows, OS X, and Linux. It uses end-to-end encryption to secure all communications to other Cryptocat users. Users are given the option of independently verifying their buddies' device lists and are notified when a buddy's device list is modified and all updates are verified through the built-in update downloader. Cryptocat was created by Nadim Kobeissi and further developed along with a community of open source contributors and is published under the terms of the GPLv3 license, although it has since been discontinued. History Cryptocat was first launched on 19 May 2011 as a web application. In June 2012, Kobeissi said he was detained at the U.S. border by the United States Department of Homeland Security, DHS and questioned about Cryptocat's censorship resistance. He tweeted about the incident aft ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Entropy (information Theory)
In information theory, the entropy of a random variable quantifies the average level of uncertainty or information associated with the variable's potential states or possible outcomes. This measures the expected amount of information needed to describe the state of the variable, considering the distribution of probabilities across all potential states. Given a discrete random variable X, which may be any member x within the set \mathcal and is distributed according to p\colon \mathcal\to[0, 1], the entropy is \Eta(X) := -\sum_ p(x) \log p(x), where \Sigma denotes the sum over the variable's possible values. The choice of base for \log, the logarithm, varies for different applications. Base 2 gives the unit of bits (or "shannon (unit), shannons"), while base Euler's number, ''e'' gives "natural units" nat (unit), nat, and base 10 gives units of "dits", "bans", or "Hartley (unit), hartleys". An equivalent definition of entropy is the expected value of the self-information of a v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Socialist Millionaires
In cryptography, the socialist millionaire problem is one in which two millionaires want to determine if their wealth is equal without disclosing any information about their riches to each other. It is a variant of the Millionaire's Problem whereby two millionaires wish to compare their riches to determine who has the most wealth without disclosing any information about their riches to each other. It is often used as a cryptographic protocol that allows two parties to verify the identity of the remote party through the use of a shared secret, avoiding a man-in-the-middle attack without the inconvenience of manually comparing public key fingerprints through an outside channel. In effect, a relatively weak password/passphrase in natural language can be used. Motivation Alice and Bob have secret values x and y, respectively. Alice and Bob wish to learn if x = y without allowing either party to learn anything else about the other's secret value. A passive attacker simply spying on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, where in actuality the attacker has inserted themselves between the two user parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. In this scenario, the attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within range of a Wi-Fi access point hosting a network without encryption could insert themselves as a man in the middle. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ejabberd
ejabberd is an Extensible Messaging and Presence Protocol (XMPP) application server and an MQ Telemetry Transport (MQTT) broker, written mainly in the Erlang programming language. It can run under several Unix-like operating systems such as macOS, Linux, FreeBSD, NetBSD, OpenBSD and OpenSolaris. Additionally, ejabberd can run under Microsoft Windows. The name ejabberd stands for Erlang Jabber Daemon (Jabber being a former name for XMPP) and is written in lowercase only, as is common for daemon software. ejabberd is free software, distributed under the terms of the GNU GPL-2.0-or-later. , it is one of the most popular open source applications written in Erlang. XMPP: The Definitive Guide (O'Reilly Media, 2009) praised ejabberd for its scalability and clustering feature, at the same time pointing out that being written in Erlang is a potential acceptance issue for users and contributors. The software's creator, Alexey Shchepin was awarded the Erlang User of the Year award at ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Olivier Goffart
Olivier is the French form of the given name Oliver. It may refer to: * Olivier (given name), a list of people and fictional characters * Olivier (surname), a list of people * Château Olivier, a Bordeaux winery *Olivier, Louisiana, a rural populated place in the United States * Olivier (crater), on the Moon * Olivier salad, a popular dish of Russian cuisine * ''Olivier'' (novel), the first published novel by French author Claire de Duras * The Olivier Theatre (named after the actor Laurence Olivier), one of three auditoria at the Royal National Theatre * The Laurence Olivier Awards, a theatrical award * Olivier (comics) Olivier is a supervillain appearing in American comic books published by Marvel Comics. The character is usually depicted as an enemy of the antihero the Punisher. Olivier was created by Bernie Wrightson, Christopher Golden and Thomas E. Sniegos ..., a foe of the Punisher See also * '' Olivier, Olivier'', a 1992 drama film {{disambiguation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Eric Brewer (scientist)
Eric Allen Brewer is professor emeritus of computer science at the University of California, Berkeley and vice-president of infrastructure at Google. His research interests include operating systems and distributed computing. He is known for formulating the CAP theorem about distributed network applications in the late 1990s. In 1996, Brewer co-founded Inktomi Corporation (bought by Yahoo! in 2003) and became a paper billionaire during the dot-com bubble. Working with the United States federal government during the presidency of Bill Clinton, he helped to create USA.gov, which launched in 2000. His research also included a wireless networking scheme called WiLDNet, which promises to bring low-cost connectivity to rural areas of the developing world. He has worked at Google since 2011. Education Brewer received a Bachelor of Science in electrical engineering and computer science (EECS) from UC Berkeley where he was a member of the Pi Lambda Phi fraternity.Membership Directory, 20 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |