|
Identity Threat Detection And Response
Identity threat detection and response (ITDR) is a cybersecurity discipline that includes tools and best practices to protect identity management infrastructure from attacks. ITDR can block and detect threats, verify administrator credentials, respond to various attacks, and restore normal operations. Common identity threats include phishing, stolen credentials, insider threats, and ransomware. ITDR adds an extra layer of security to identity and access management (IAM) systems. It helps secure accounts, permissions, and the identity infrastructure itself from compromise. With attackers targeting identity tools directly, ITDR is becoming more important in 2023 : according to Gartner, established IAM hygiene practices like privileged access management and identity governance are no longer enough. ITDR can be part of a zero trust security model. ITDR is especially relevant for multicloud infrastructures, which have gaps between cloud providers' distinct IAM implementations. Closi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cybersecurity
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribut ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OAuth 2
OAuth (short for "Open Authorization") is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Facebook, Microsoft, and Twitter to permit the users to share information about their accounts with third-party applications or websites. Generally, OAuth provides clients a "secure delegated access" to server resources on behalf of a resource owner. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access the protected resources hosted by the re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Breach And Attack Simulation
Breach and attack simulation (BAS) refers to technologies that allow organizations to test their security defenses against simulated cyberattacks. BAS solutions provide automated assessments that help identify weaknesses or gaps in an organization's security posture. Description BAS tools work by executing simulated attacks against an organization's IT infrastructure and assets. These simulated attacks are designed to mimic real-world threats and techniques used by cybercriminals. The simulations test the organization's ability to detect, analyze, and respond to attacks. After running the simulations, BAS platforms generate reports that highlight areas where security controls failed to stop the simulated attacks. Organizations use BAS to validate whether security controls are working as intended. Frequent BAS testing helps benchmark security posture over time and ensure proper incident response processes are in place.BAS testing complements other security assessments like penetr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Team
A red team or team red are a group that plays the role of an enemy or competitor to provide security feedback from that perspective. Red teams are used in many fields, especially in cybersecurity, airport security, law enforcement, the military and intelligence agencies. Overview In military wargaming, the opposing force (or OPFOR) in a simulated conflict may be referred to as a red cell; this is an interchangeable term for red team. The key theme is that the adversary (red team) leverages tactics, techniques, and equipment as appropriate to emulate the desired actor. The red team challenges operational planning by playing the role of a mindful adversary. In United States wargaming simulations, the U.S. force is always the blue team, whereas the opposing force is always the red team. When applied to intelligence work, red-teaming is sometimes called alternative analysis. Cybersecurity In cybersecurity, a penetration test involves ethical hackers trying to break into a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SentinelOne
SentinelOne, Inc. is an American cybersecurity company listed on NYSE based in Mountain View, California. The company was founded in 2013 by Tomer Weingarten, Almog Cohen and Ehud ("Udi") Shamir. Weingarten acts as the company's CEO. Nicholas Warner is the company's COO. The company has approximately 970 employees and offices in Mountain View, Boston, Tokyo, and Berlin. The company uses machine learning for monitoring personal computers, IoT devices, and cloud workloads. The company's platform utilizes a heuristic model, specifically its patented behavioral AI. The company is AV-TEST certified. Funding In June 2019, SentinelOne received $120 million in a Series D funding round led by Insight Partners. The company received an addition $200 million in Series E funding in February 2020. The Series E round placed SentinelOne at a valuation of about $1.1 billion. In 2020, SentinelOne closed a round for $267 million in funding, bringing their total valuation to $3.1 billion. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft
Microsoft Corporation is an American multinational corporation, multinational technology company, technology corporation producing Software, computer software, consumer electronics, personal computers, and related services headquartered at the Microsoft Redmond campus located in Redmond, Washington, United States. Its best-known software products are the Microsoft Windows, Windows line of operating systems, the Microsoft Office Productivity software#Office suite, suite, and the Internet Explorer and Microsoft Edge, Edge web browsers. Its flagship hardware products are the Xbox video game consoles and the Microsoft Surface lineup of touchscreen personal computers. Microsoft ranked No. 21 in the 2020 Fortune 500 rankings of the largest United States corporations by total revenue; it was the world's List of the largest software companies, largest software maker by revenue as of 2019. It is one of the Big Tech, Big Five American information technology companies, alongside Alphabet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CrowdStrike
CrowdStrike Holdings, Inc. is an American cybersecurity technology company based in Austin, Texas. It provides cloud workload and endpoint security, threat intelligence, and cyberattack response services. The company has been involved in investigations of several high-profile cyberattacks, including the 2014 Sony Pictures hack, the 2015–16 cyber attacks on the Democratic National Committee (DNC), and the 2016 email leak involving the DNC. History CrowdStrike was co-founded by George Kurtz (CEO), Dmitri Alperovitch (former CTO), and Gregg Marston (CFO, retired) in 2011. In 2012, Shawn Henry, a former Federal Bureau of Investigation (FBI) official, was hired to lead the subsidiary CrowdStrike Services, Inc., which focused on proactive and incident response services. In June 2013, the company launched its first product, CrowdStrike Falcon, which provided endpoint protection, threat intelligence and attribution. In May 2014, CrowdStrike's reports assisted the United States ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
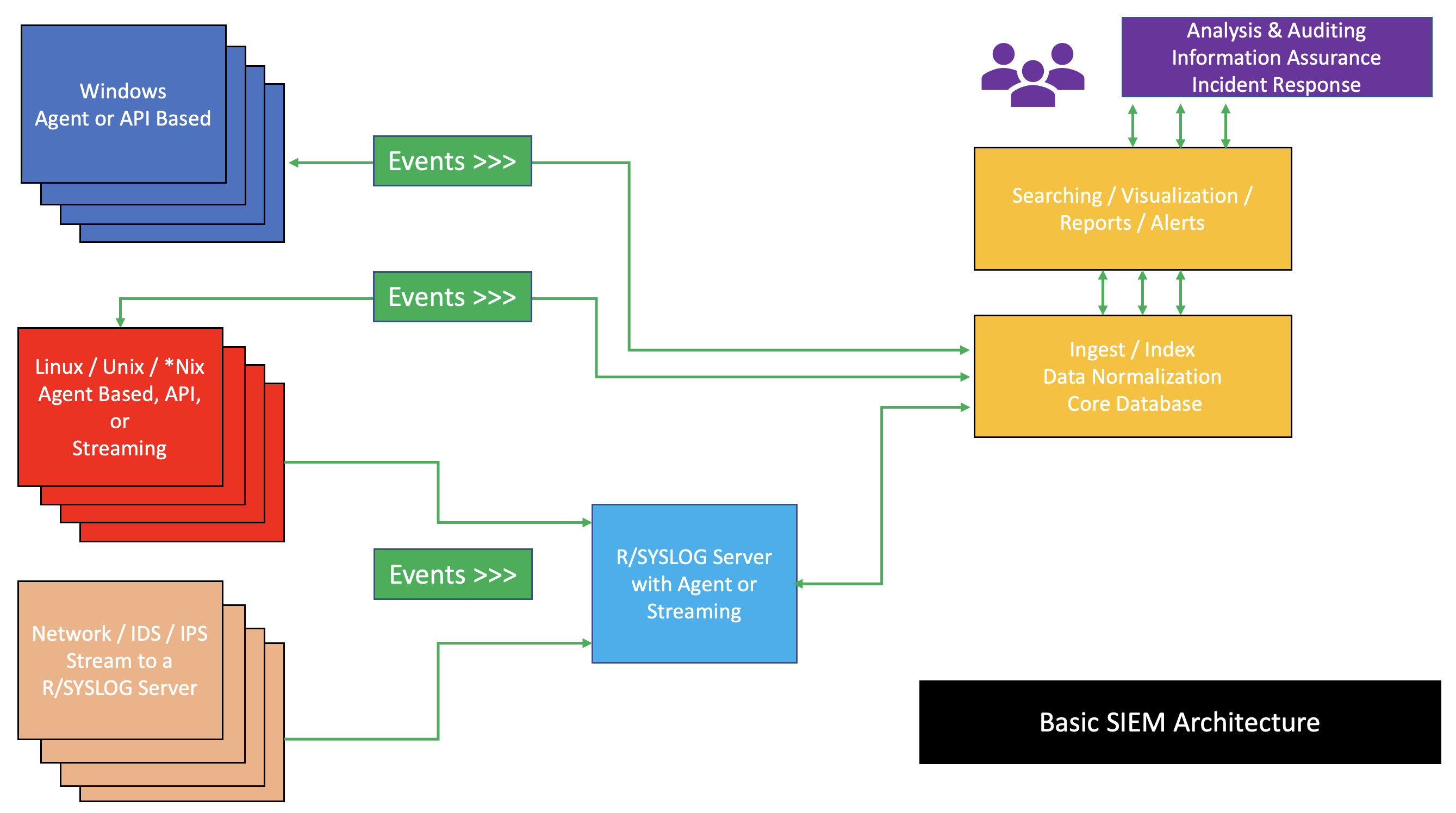
Security Information And Event Management
Security information and event management (SIEM) is a field within the field of computer security, where software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated by applications and network hardware. Vendors sell SIEM as software, as appliances, or as managed services; these products are also used to log security data and generate reports for compliance purposes. The term and the initialism SIEM was coined by Mark Nicolett and Amrit Williams of Gartner in 2005. History Monitoring system logs has grown more prevalent as complex cyber-attacks force compliance and regulatory mechanisms to mandate logging security controls within a Risk Management Framework. Logging levels of a system started with the primary function of troubleshooting system errors or debugging code compiled and run. As operating systems and networks have increased in complexity, so has the even ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Initially, Active Directory was used only for centralized domain management. However, Active Directory eventually became an umbrella title for a broad range of directory-based identity-related services. A server running the Active Directory Domain Service (AD DS) role is called a domain controller. It authenticates and authorizes all users and computers in a Windows domain type network, assigning and enforcing security policies for all computers, and installing or updating software. For example, when a user logs into a computer that is part of a Windows domain, Active Directory checks the submitted username and password and determines whether the user is a system administrator or normal user. Also, it allows management and storage of information, provides authentication and authoriza ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Role-based Access Control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users. It is an approach to implement mandatory access control (MAC) or discretionary access control (DAC). Role-based access control is a policy-neutral access-control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations. RBAC can be used to facilitate administration of security in large organizations with hundreds of users and thousands of permissions. Although RBAC is different from MAC and DAC access control frameworks, it can enforce these policies without any complication. Design Within an organization, roles are created for various job functions. The permissions to perform certain operations are ass ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Endpoint Detection And Response
Endpoint detection and response (EDR), also known as endpoint threat detection and response (ETDR), is a cybersecurity technology that continually monitors an "endpoint" (e.g. mobile phone, laptop, Internet-of-Things device) to mitigate malicious cyber threats. History In 2013, Anton Chuvakin of Gartner coined the term "endpoint threat detection and response" for "tools primarily focused on detecting and investigating suspicious activities (and traces of such) other problems on hosts/endpoints". Now, it is commonly known as "endpoint detection and response". According to the ''Endpoint Detection and Response - Global Market Outlook (2017-2026)'' report, the adoption of cloud-based and on-premises EDR solutions are going to grow 26% annually, and will be valued at $7273.26 million by 2026. According to the ''Artificial Intelligence (AI) in Cyber Security Market'' report by Zion Market Research, the role of machine learning and artificial intelligence will create a $30.9 billion ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |