|
FreeSWITCH
FreeSWITCH is free and open-source server software for real-time communication applications, including WebRTC, video, and voice over Internet Protocol (VoIP). It runs on Linux, Windows, macOS, and FreeBSD. FreeSWITCH is used to build private branch exchange (PBX) telecommunication systems, IVR services, videoconferencing with chat and screen sharing, wholesale least-cost routing, Session Border Controller (SBC) and embedded communication appliances. It has support for encryption, ZRTP, DTLS, and Session Initiation Protocol (SIP). It is implemented as a core library, libfreeswitch, which can be embedded into other projects. It is distributed under the Mozilla Public License (MPL), a free software license. History The FreeSWITCH project was announced in January 2006 at O'Reilly Media's ETEL Conference. In June 2007, FreeSWITCH was selected by Truphone for use, and in August 2007, Gaboogie announced that it selected FreeSWITCH as its conferencing platform. The official rel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ZRTP
ZRTP (composed of Z and Real-time Transport Protocol) is a cryptographic key-agreement protocol to negotiate the keys for encryption between two end points in a Voice over IP (VoIP) phone telephony call based on the Real-time Transport Protocol. It uses Diffie–Hellman key exchange and the Secure Real-time Transport Protocol (SRTP) for encryption. ZRTP was developed by Phil Zimmermann, with help from Bryce Wilcox-O'Hearn, Colin Plumb, Jon Callas and Alan Johnston and was submitted to the Internet Engineering Task Force (IETF) by Zimmermann, Callas and Johnston on March 5, 2006 and published on April 11, 2011 as . Overview ZRTP ("Z" is a reference to its inventor, Zimmermann; "RTP" stands for Real-time Transport Protocol) is described in the Internet Draft as a ''"key agreement protocol which performs Diffie–Hellman key exchange during call setup in-band in the Real-time Transport Protocol (RTP) media stream which has been established using some other signaling protocol suc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cross-platform
In computing, cross-platform software (also called multi-platform software, platform-agnostic software, or platform-independent software) is computer software that is designed to work in several computing platforms. Some cross-platform software requires a separate build for each platform, but some can be directly run on any platform without special preparation, being written in an interpreted language or compiled to portable bytecode for which the interpreters or run-time packages are common or standard components of all supported platforms. For example, a cross-platform application may run on Microsoft Windows, Linux, and macOS. Cross-platform software may run on many platforms, or as few as two. Some frameworks for cross-platform development are Codename One, Kivy, Qt, Flutter, NativeScript, Xamarin, Phonegap, Ionic, and React Native. Platforms ''Platform'' can refer to the type of processor (CPU) or other hardware on which an operating system (OS) or application runs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Voice Over Internet Protocol
Voice over Internet Protocol (VoIP), also called IP telephony, is a method and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. The terms Internet telephony, broadband telephony, and broadband phone service specifically refer to the provisioning of communications services (voice, fax, SMS, voice-messaging) over the Internet, rather than via the public switched telephone network (PSTN), also known as plain old telephone service (POTS). Overview The steps and principles involved in originating VoIP telephone calls are similar to traditional digital telephony and involve signaling, channel setup, digitization of the analog voice signals, and encoding. Instead of being transmitted over a circuit-switched network, the digital information is packetized and transmission occurs as IP packets over a packet-switched network. They transport media streams using special media delivery protocols ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DTLS
Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications by allowing them to communicate in a way designed to prevent eavesdropping, tampering, or message forgery. The DTLS protocol is based on the stream-oriented Transport Layer Security (TLS) protocol and is intended to provide similar security guarantees. The DTLS protocol datagram preserves the semantics of the underlying transport—the application does not suffer from the delays associated with stream protocols, but because it uses UDP or SCTP, the application has to deal with packet reordering, loss of datagram and data larger than the size of a datagram network packet. Because DTLS uses UDP or SCTP rather than TCP, it avoids the "TCP meltdown problem", when being used to create a VPN tunnel. Definition The following documents define DTLS: * for use with User Datagram Protocol (UDP), * for use with Datagram Congestion Control Protocol (DCCP), * for use wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in mil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Appliance
A computer appliance is a home appliance with software or firmware that is specifically designed to provide a specific computing resource. Such devices became known as ''appliances'' because of the similarity in role or management to a home appliance, which are generally ''closed and sealed'', and are not serviceable by the user or owner. The hardware and software are delivered as an integrated product and may even be pre-configured before delivery to a customer, to provide a turn-key solution for a particular application. Unlike general purpose computers, appliances are generally not designed to allow the customers to change the software and the underlying operating system, or to flexibly reconfigure the hardware. Another form of appliance is the virtual appliance, which has similar functionality to a dedicated hardware appliance, but is distributed as a software virtual machine image for a hypervisor-equipped device. Overview Traditionally, software applications run on top ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Embedded System
An embedded system is a computer system—a combination of a computer processor, computer memory, and input/output peripheral devices—that has a dedicated function within a larger mechanical or electronic system. It is ''embedded'' as part of a complete device often including electrical or electronic hardware and mechanical parts. Because an embedded system typically controls physical operations of the machine that it is embedded within, it often has real-time computing constraints. Embedded systems control many devices in common use today. , it was estimated that ninety-eight percent of all microprocessors manufactured were used in embedded systems. Modern embedded systems are often based on microcontrollers (i.e. microprocessors with integrated memory and peripheral interfaces), but ordinary microprocessors (using external chips for memory and peripheral interface circuits) are also common, especially in more complex systems. In either case, the processor(s) us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Session Border Controller
A session border controller (SBC) is a network element deployed to protect SIP based voice over Internet Protocol (VoIP) networks. Early deployments of SBCs were focused on the borders between two service provider networks in a peering environment. This role has now expanded to include significant deployments between a service provider's access network and a backbone network to provide service to residential and/or enterprise customers. The term "session" refers to a communication between two or more parties – in the context of telephony, this would be a call. Each call consists of one or more call signaling message exchanges that control the call, and one or more call media streams which carry the call's audio, video, or other data along with information of call statistics and quality. Together, these streams make up a session. It is the job of a session border controller to exert influence over the data flows of sessions. The term "border" refers to a point of demarcation b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Least-cost Routing
In voice telecommunications, least-cost routing (LCR) is the process of selecting the path of outbound communications traffic based on cost. Within a telecoms carrier, an LCR team might periodically (monthly, weekly or even daily) choose between routes from several or even hundreds of carriers for destinations across the world. This function might also be automated by a device or software program known as a least-cost router. Telecoms carriers as suppliers and customers Telecoms carriers often buy and sell call termination services with other carriers. A carrier such as Telewest or France Telecom will be interconnected with other telecoms carriers and might have a number of routing options of different price, quality and capacity to a given country. In the de-regulated EU, these will be licensed alternative operators (e.g. Cable and Wireless / Colt in the UK or Jazztel in Spain) or the ( PTT)'s of other countries, such as T-Systems (Germany), Telefónica (Spain), NTT (Japan) or Te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Screen Sharing
In computing, the term remote desktop refers to a software- or operating system feature that allows a personal computer's desktop environment to be run remotely off of one system (usually a PC, but the concept applies equally to a server or a smartphone), while being displayed on a separate client device. Remote desktop applications have varying features. Some allow attaching to an existing user's session and "remote controlling", either displaying the remote control session or blanking the screen. Taking over a desktop remotely is a form of remote administration. Overview Remote access can also be explained as the remote control of a computer by using another device connected via the internet or another network. This is widely used by many computer manufacturers and large businesses help desks for technical troubleshooting of their customer's problems. Remote desktop software captures the mouse and keyboard inputs from the local computer (client) and sends them to the rem ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
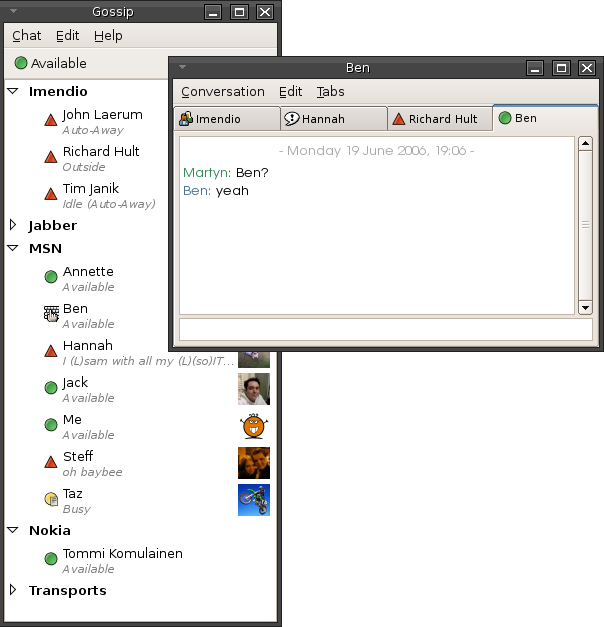
Online Chat
Online chat may refer to any kind of communication over the Internet that offers a real-time transmission of text messages from sender to receiver. Chat messages are generally short in order to enable other participants to respond quickly. Thereby, a feeling similar to a spoken conversation is created, which distinguishes chatting from other text-based online communication forms such as Internet forums and email. Online chat may address point-to-point communications as well as multicast communications from one sender to many receivers and voice and video chat, or may be a feature of a web conferencing service. Online chat in a less stringent definition may be primarily any direct text-based or video-based (webcams), one-on-one chat or one-to-many group chat (formally also known as synchronous conferencing), using tools such as instant messengers, Internet Relay Chat (IRC), talkers and possibly MUDs or other online games. The expression ''online chat'' comes from the word '' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Videoconferencing
Videotelephony, also known as videoconferencing and video teleconferencing, is the two-way or multipoint reception and transmission of audio and video signals by people in different locations for real time communication.McGraw-Hill Concise Encyclopedia of EngineeringVideotelephony McGraw-Hill, 2002. Retrieved from the FreeDictionary.com website, January 9, 2010 A videophone is a telephone with a video camera and video display, capable of simultaneous video and audio communication. Videoconferencing implies the use of this technology for a group or organizational meeting rather than for individuals, in a videoconference.Mulbach et al, 1995. pg. 291. Telepresence may refer either to a high-quality videotelephony system (where the goal is to create the illusion that remote participants are in the same room) or to meetup technology, which can go beyond video into robotics (such as moving around the room or physically manipulating objects). Videoconferencing has also been called "vis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |