|
Electronic Authentication
Electronic authentication is the process of establishing confidence in user identities electronically presented to an information system. Digital authentication, or e-authentication, may be used synonymously when referring to the authentication process that confirms or certifies a person's identity and works. When used in conjunction with an electronic signature, it can provide evidence of whether data received has been tampered with after being signed by its original sender. Electronic authentication can reduce the risk of fraud and identity theft by verifying that a person is who they say they are when performing transactions online. Various e-authentication methods can be used to authenticate a user's identify ranging from a password to higher levels of security that utilize multi-factor authentication (MFA). Depending on the level of security used, the user might need to prove his or her identity through the use of security tokens, challenge questions, or being in possession of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information System
An information system (IS) is a formal, sociotechnical, organizational system designed to collect, process, Information Processing and Management, store, and information distribution, distribute information. From a sociotechnical perspective, information systems comprise four components: task, people, structure (or roles), and technology. Information systems can be defined as an integration of components for collection, storage and data processing, processing of data, comprising digital products that process data to facilitate decision making and the data being used to provide information and contribute to knowledge. A computer information system is a system, which consists of people and computers that process or interpret information. The term is also sometimes used to simply refer to a computer system with software installed. "Information systems" is also an academic field of study about systems with a specific reference to information and the complementary networks of computer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometric
Biometrics are body measurements and calculations related to human characteristics and features. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, voice, and behavioral profiling. Some researchers have coined the term behaviometrics (behavioral biom ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Advanced Electronic Signature
An advanced electronic signature (AES or AdES) is an electronic signature that has met the requirements set forth under EU Regulation No 910/2014 ( eIDAS-regulation) on electronic identification and trust services for electronic transactions in the European Single Market. Description eIDAS created standards for the use of electronic signatures so that they could be used securely when conducting business online, such as an electronic fund transfer or official business across borders with EU Member States. The advanced electronic signature is one of the standards outlined in eIDAS. For an electronic signature to be considered as advanced it must meet several requirements: # The signatory can be uniquely identified and linked to the signature # The signatory must have sole control of the signature creation data (typically a private key) that was used to create the electronic signature # The signature must be capable of identifying if its accompanying data has been tampered with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Voter ID Laws
A voter identification law is a law that requires a person to show some form of identification in order to vote. In some jurisdictions requiring photo IDs, voters who do not have photo ID often must have their identity verified by someone else (such as in Sweden) or sign Challenged Voter Affidavit(such as in New Hampshire) in order to receive a ballot to vote. Examples Argentina In Argentina, voting is compulsory for all citizens between 18 and 70 years old, non-compulsory for those older than 70 and between 16 and 18, and citizens with domiciles in foreign countries. To vote they must present a valid Documento Nacional de Identidad at the corresponding voting center. Other countries in Latin America have similar policies. Australia In Australia, voting is compulsory for all adult citizens. Failure to cast a ballot in a federal election without a valid reason may attract a fine of , and each state imposes its own fines for the same offence in state elections. No form of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Identification
An electronic identification ("eID") is a digital solution for proof of identity of citizens or organizations. They can be used to view to access benefits or services provided by government authorities, banks or other companies, for mobile payments, etc. Apart from online authentication and login, many electronic identity services also give users the option to sign electronic documents with a digital signature. One form of eID is an electronic identification card (eIC), which is a physical identity card that can be used for online and offline personal identification or authentication. The eIC is a smart card in ID-1 format of a regular bank card, with identity information printed on the surface (such as personal details and a photograph) and in an embedded RFID microchip, similar to that in biometric passports. The chip stores the information printed on the card (such as the holder's name and date of birth) and the holder's photo(s). Several photos may be taken from different ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometrics
Biometrics are body measurements and calculations related to human characteristics and features. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, voice, and behavioral profiling. Some researchers have coined the term behaviometrics (behavioral biom ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
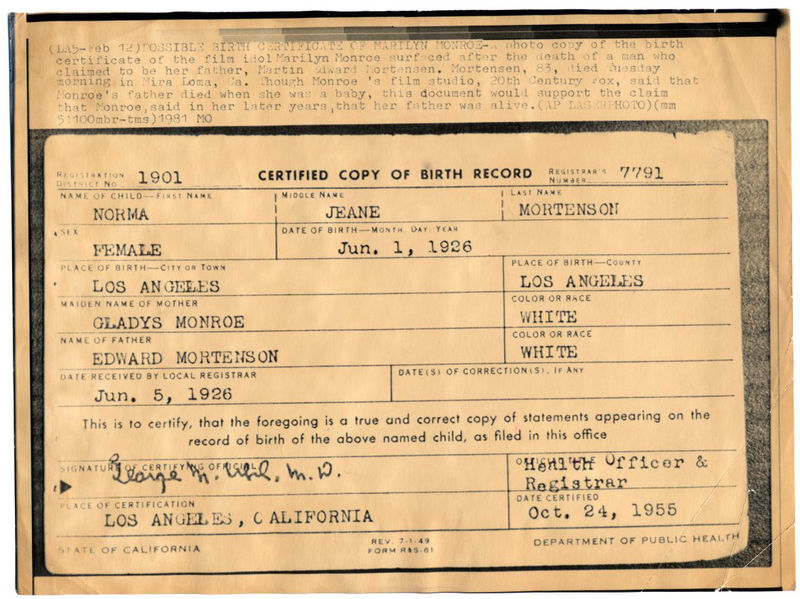
Birth Certificate
A birth certificate is a vital record that documents the Childbirth, birth of a person. The term "birth certificate" can refer to either the original document certifying the circumstances of the birth or to a certified copy of or representation of the ensuing registration of that birth. Depending on the jurisdiction, a record of birth might or might not contain verification of the event by a healthcare professional such as a midwife or doctor. The United Nations Sustainable Development Goal 17, an integral part of the Sustainable Development Goals, 2030 Agenda, has a target to increase the timely availability of data regarding age, gender, race, ethnicity, and other relevant characteristics which documents like a birth certificate have the capacity to provide. History and contemporary times The documentation of births is a practice widely held throughout human civilization. The original purpose of vital statistics was for tax purposes and for the determination of available mil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Browser Fingerprinting
A device fingerprint or machine fingerprint is information collected about the software and hardware of a remote computing device for the purpose of identification. The information is usually assimilated into a brief identifier using a fingerprinting algorithm. A browser fingerprint is information collected specifically by interaction with the web browser of the device. Device fingerprints can be used to fully or partially identify individual devices even when persistent cookies (and zombie cookies) cannot be read or stored in the browser, the client IP address is hidden, or one switches to another browser on the same device. This may allow a service provider to detect and prevent identity theft and credit card fraud, but also to compile long-term records of individuals' browsing histories (and deliver targeted advertising or targeted exploits) even when they are attempting to avoid tracking – raising a major concern for internet privacy advocates. History Basic web browser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Face Recognition
A facial recognition system is a technology potentially capable of matching a human face from a digital image or a Film frame, video frame against a database of faces. Such a system is typically employed to authenticate users through ID verification services, and works by pinpointing and measuring facial features from a given image. Development began on similar systems in the 1960s, beginning as a form of computer Application software, application. Since their inception, facial recognition systems have seen wider uses in recent times on smartphones and in other forms of technology, such as robotics. Because computerized facial recognition involves the measurement of a human's physiological characteristics, facial recognition systems are categorized as biometrics. Although the accuracy of facial recognition systems as a biometric technology is lower than iris recognition, fingerprint, fingerprint image acquisition, palm recognition or Speech recognition, voice recognition, it i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Speaker Detection
Speaker recognition is the identification of a person from characteristics of voices. It is used to answer the question "Who is speaking?" The term voice recognition can refer to ''speaker recognition'' or speech recognition. Speaker verification (also called speaker authentication) contrasts with identification, and ''speaker recognition'' differs from '' speaker diarisation'' (recognizing when the same speaker is speaking). Recognizing the speaker can simplify the task of translating speech in systems that have been trained on specific voices or it can be used to authenticate or verify the identity of a speaker as part of a security process. Speaker recognition has a history dating back some four decades as of 2019 and uses the acoustic features of speech that have been found to differ between individuals. These acoustic patterns reflect both anatomy and learned behavioral patterns. Verification versus identification There are two major applications of speaker recognition techn ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Short Message Service
Short Message Service, commonly abbreviated as SMS, is a text messaging service component of most telephone, Internet and mobile device systems. It uses standardized communication protocols that let mobile phones exchange short text messages, typically transmitted over cellular networks. Developed as part of the GSM standards, and based on the SS7 signalling protocol, SMS rolled out on digital cellular networks starting in 1993 and was originally intended for customers to receive alerts from their carrier/operator. The service allows users to send and receive text messages of up to 160 characters, originally to and from GSM phones and later also CDMA and Digital AMPS; it has since been defined and supported on newer networks, including present-day 5G ones. Using SMS gateways, messages can be transmitted over the Internet through an SMSC, allowing communication to computers, fixed landlines, and satellite. MMS was later introduced as an upgrade to SMS with "picture mess ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
US-VISIT (CBP)
United States Visitor and Immigrant Status Indicator Technology (commonly referred to as US-VISIT) is a U.S. Customs and Border Protection (CBP) management system. The system involves the collection and analysis of biometric data (such as fingerprints), which are checked against a database to track individuals deemed by the United States to be terrorists, criminals, and illegal immigrants. US-VISIT is accessed by 30,000 users from federal, state, and local government agencies. Upon Presidential approval of the 2013 Continuing resolution the US-VISIT program officially became the Office of Biometric Identity Management (OBIM), save for portions of the agency which performed overstay analysis being transferred into U.S. Immigration and Customs Enforcement and biometric Entry and Exit operations which became a part of U.S. Customs and Border Protection. Purpose and overview The U.S. government states that the purpose of US-VISIT is to advance the national security, security of both t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |