|
Computer Network Programming
Computer network programming involves writing computer programs that enable processes to communicate with each other across a computer network. Connection-oriented and connectionless communications Very generally, most of communications can be divided into connection-oriented, and connectionless. Whether a communication is connection-oriented or connectionless, is defined by the communication protocol A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any variation of a physical quantity. The protocol defines the rules, syntax, semantics (computer science), sem ..., and not by . Examples of the connection-oriented protocols include and , and examples of connectionless protocols include , "raw IP", and . Clients and servers For connection-oriented communications, communication parties usually have different roles. One party is usually waiting for incoming connections; this party is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Programs
A computer program is a sequence or set of instructions in a programming language for a computer to Execution (computing), execute. It is one component of software, which also includes software documentation, documentation and other intangible components. A ''computer program'' in its human-readable form is called source code. Source code needs another computer program to Execution (computing), execute because computers can only execute their native machine instructions. Therefore, source code may be Translator (computing), translated to machine instructions using a compiler written for the language. (Assembly language programs are translated using an Assembler (computing), assembler.) The resulting file is called an executable. Alternatively, source code may execute within an interpreter (computing), interpreter written for the language. If the executable is requested for execution, then the operating system Loader (computing), loads it into Random-access memory, memory and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Protocol
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet. IP has the task of delivering Packet (information technology), packets from the source Host (network), host to the destination host solely based on the IP addresses in the packet Header (computing), headers. For this purpose, IP defines packet structures that encapsulation (networking), encapsulate the data to be delivered. It also defines addressing methods that are used to label the datagram with source and destination information. IP was the connectionless datagram service in the original ''Transmission Control Program'' introduced by Vint Cerf and Bob Kahn in 1974, which was complemented by a connection-oriented service that became the basis for the Transmission Control Protocol (TCP). The Internet protocol suite is therefore often referre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networks Engineering
A computer is a machine that can be Computer programming, programmed to automatically Execution (computing), carry out sequences of arithmetic or logical operations (''computation''). Modern digital electronic computers can perform generic sets of operations known as Computer program, ''programs'', which enable computers to perform a wide range of tasks. The term computer system may refer to a nominally complete computer that includes the Computer hardware, hardware, operating system, software, and peripheral equipment needed and used for full operation; or to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of Programmable logic controller, industrial and Consumer electronics, consumer products use computers as control systems, including simple special-purpose devices like microwave ovens and remote controls, and factory devices like industrial robots. Computers are at the core of general-purpose devices ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
UNIX Network Programming
Unix Network Programming is a book written by W. Richard Stevens. It was published in 1990 by Prentice Hall and covers many topics regarding UNIX networking and Computer network programming. The book focuses on the design and development of network software under UNIX. The book provides descriptions of how and why a given solution works and includes 15,000 lines of C code. The book's summary describes it as "for programmers seeking an in depth tutorial on sockets, transport level interface (TLI), interprocess communications (IPC) facilities under System V and BSD UNIX." The book has been translated into several languages, including Chinese, Italian, German, Japanese and others. Later editions have expanded into two volumes, Volume 1: The Sockets Networking API and Volume 2: Interprocess Communications. In the movie ''Wayne's World 2 ''Wayne's World 2'' is a 1993 American comedy film directed by Stephen Surjik and starring Mike Myers and Dana Carvey as hosts of a public-ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DevOps
DevOps is the integration and automation of the software development and information technology operations. DevOps encompasses necessary tasks of software development and can lead to shortening development time and improving the development life cycle. According to Neal Ford, DevOps, particularly through continuous delivery, employs the "Bring the pain forward" principle, tackling tough tasks early, fostering automation and swift issue detection. Software programmers and architects should use fitness functions to keep their software in check. Although debated, DevOps is characterized by key principles: shared ownership, workflow automation, and rapid feedback. From an academic perspective, Len Bass, Ingo Weber, and Liming Zhu—three computer science researchers from the CSIRO and the Software Engineering Institute—suggested defining DevOps as "a set of practices intended to reduce the time between committing a change to a system and the change being placed into normal produ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
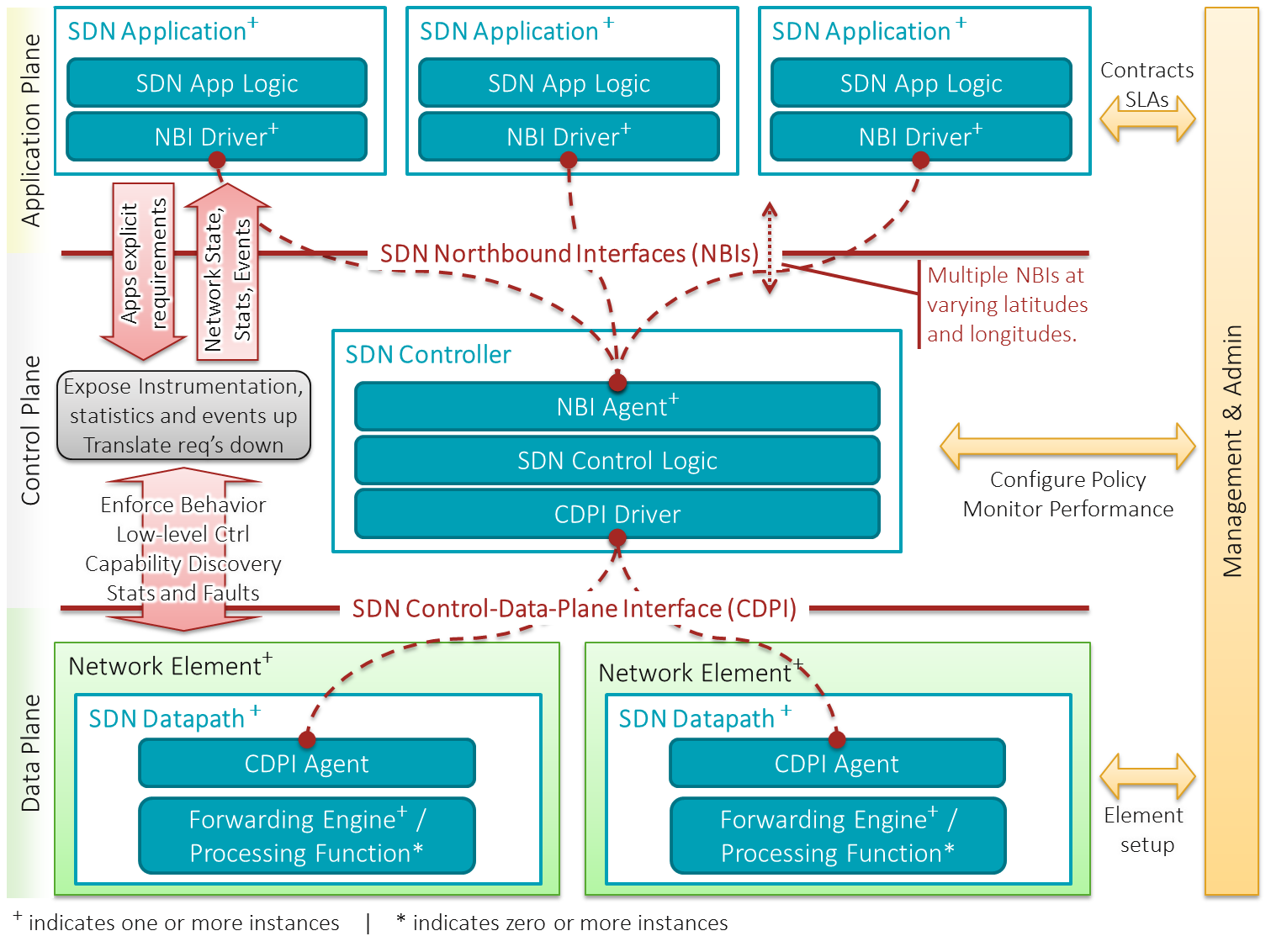
Software-defined Networking
Software-defined networking (SDN) is an approach to network management that uses abstraction to enable dynamic and programmatically efficient network configuration to create grouping and segmentation while improving network performance and monitoring in a manner more akin to cloud computing than to traditional network management. SDN is meant to improve the static architecture of traditional networks and may be employed to centralize network intelligence in one network component by disassociating the forwarding process of network packets ( data plane) from the routing process ( control plane). The control plane consists of one or more controllers, which are considered the brains of the SDN network, where the whole intelligence is incorporated. However, centralization has certain drawbacks related to security, scalability and elasticity. SDN was commonly associated with the OpenFlow protocol for remote communication with network plane elements to determine the path of network pac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTP
HTTP (Hypertext Transfer Protocol) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, where hypertext documents include hyperlinks to other resources that the user can easily access, for example by a Computer mouse, mouse click or by tapping the screen in a web browser. Development of HTTP was initiated by Tim Berners-Lee at CERN in 1989 and summarized in a simple document describing the behavior of a client and a server using the first HTTP version, named 0.9. That version was subsequently developed, eventually becoming the public 1.0. Development of early HTTP Requests for Comments (RFCs) started a few years later in a coordinated effort by the Internet Engineering Task Force (IETF) and the World Wide Web Consortium (W3C), with work later moving to the IETF. HTTP/1 was finalized and fully documented (as version 1.0) in 1996 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenSSL
OpenSSL is a software library for applications that provide secure communications over computer networks against eavesdropping, and identify the party at the other end. It is widely used by Internet servers, including the majority of HTTPS websites. OpenSSL contains an open-source implementation of the SSL and TLS protocols. The core library, written in the C programming language, implements basic cryptographic functions and provides various utility functions. Wrappers allowing the use of the OpenSSL library in a variety of computer languages are available. The OpenSSL Software Foundation (OSF) represents the OpenSSL project in most legal capacities including contributor license agreements, managing donations, and so on. OpenSSL Software Services (OSS) also represents the OpenSSL project for support contracts. OpenSSL is available for most Unix-like operating systems (including Linux, macOS, and BSD), Microsoft Windows and OpenVMS. Project history The OpenSSL project wa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network, such as the Internet. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol that provides security to datagram-based applications. In technical writing, references to "(D)TLS" are often seen when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, fir ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Berkeley Sockets
A Berkeley ( BSD) socket is an application programming interface (API) for Internet domain sockets and Unix domain sockets, used for inter-process communication (IPC). It is commonly implemented as a library of linkable modules. It originated with the 4.2BSD Unix operating system, which was released in 1983. A socket is an abstract representation (handle) for the local endpoint of a network communication path. The Berkeley sockets API represents it as a file descriptor in the Unix philosophy that provides a common interface for input and output to streams of data. Berkeley sockets evolved with little modification from a ''de facto'' standard into a component of the POSIX specification. The term POSIX sockets is essentially synonymous with ''Berkeley sockets'', but they are also known as BSD sockets, acknowledging the first implementation in the Berkeley Software Distribution. History and implementations Berkeley sockets originated with the 4.2BSD Unix operating system, relea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |