|
Computer Fraud And Abuse Act
The Computer Fraud and Abuse Act of 1986 (CFAA) is a United States cybersecurity bill that was enacted in 1986 as an amendment to existing computer fraud law (), which had been included in the Comprehensive Crime Control Act of 1984. Prior to computer-specific criminal laws, computer crimes were prosecuted as mail and wire fraud, but the applying law was often insufficient. The original 1984 bill was enacted in response to concern that computer-related crimes might go unpunished. The House Committee Report to the original computer crime bill included a statement by a representative of GTE-owned Telenet that characterized the 1983 techno-thriller film '' WarGames''—in which a young teenager (played by Matthew Broderick) from Seattle breaks into a U.S. military supercomputer programmed to predict possible outcomes of nuclear war and unwittingly almost starts World War III—as "a realistic representation of the automatic dialing and access capabilities of the personal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intangible Property
Intangible property, also known as incorporeal property, is something that a person or corporation can have ownership of and can transfer ownership to another person or corporation, but has no physical substance, for example brand identity or knowledge/intellectual property. Description Intangible property generally refers to statutory creations, such as copyright, trademarks, or patents. It excludes tangible property like real property (land, buildings, and fixtures) and personal property (ships, automobiles, tools, etc.). In some jurisdictions, intangible property are referred to as ''choses in action''. Intangible property is used in distinction to tangible property. It is useful to note that there are two forms of intangible property: legal intangible property (which is discussed here) and competitive intangible property (which is the source from which legal intangible property is created but cannot be owned, extinguished, or transferred). Competitive intangible ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DEF CON
DEF CON (also written as DEFCON, Defcon, or DC) is a Computer security conference, hacker convention held annually in Las Vegas Valley, Las Vegas, Nevada. The first DEF CON took place in June 1993 and today many attendees at DEF CON include computer security professionals, journalists, lawyers, federal government employees, security researchers, students, and Hacker (computer security), hackers with a general interest in source code, software, computer architecture, hardware modification, conference badges, and anything else that can be "hacked". The event consists of several tracks of speakers about computer and hacking-related subjects, as well as cyber-security challenges and competitions (known as hacking Wargame (hacking), wargames). Contests held during the event are extremely varied and can range from creating the longest Wi-Fi connection to finding the most effective way to cool a beer in the Nevada heat. Other contests, past and present, include lockpicking, Defcon Robot ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Whitehouse
Whitehouse may refer to: People * Charles S. Whitehouse (1921–2001), American diplomat * Cornelius Whitehouse (1796–1883), English engineer and inventor * E. Sheldon Whitehouse (1883–1965), American diplomat * Elliott Whitehouse (born 1993), English footballer * Eula Whitehouse (1892–1974), American botanist * Frederick William Whitehouse (1900–1973), Australian geologist * Jimmy Whitehouse (footballer, born 1924) (1924–2005), English footballer * Mary Whitehouse (1910–2001), British Christian morality campaigner * Morris H. Whitehouse (1878–1944), American architect * Paul Whitehouse (born 1958), Welsh comedian and actor * Paul Whitehouse (police officer) (born 1944) * Sheldon Whitehouse (born 1955), American politician from the state of Rhode Island * Wildman Whitehouse (1816–1890), English surgeon and chief electrician for the transatlantic telegraph cable Places ;in the United Kingdom * Whitehouse, Aberdeenshire, location of the Whitehouse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NARA
The National Archives and Records Administration (NARA) is an independent agency of the United States government within the executive branch, charged with the preservation and documentation of government and historical records. It is also tasked with increasing public access to those documents that make up the National Archives. NARA is officially responsible for maintaining and publishing the legally authentic and authoritative copies of acts of Congress, presidential directives, and federal regulations. NARA also transmits votes of the Electoral College to Congress. It also examines Electoral College and constitutional amendment ratification documents for prima facie legal sufficiency and an authenticating signature. The National Archives, and its publicly exhibited Charters of Freedom, which include the original United States Declaration of Independence, Constitution of the United States, United States Bill of Rights, Emancipation Proclamation (starting in 2026), and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RICO Act
The Racketeer Influenced and Corrupt Organizations (RICO) Act is a United States federal law that provides for extended criminal penalties and a civil cause of action for acts performed as part of an ongoing criminal organization. RICO was enacted by Title IX of the Organized Crime Control Act of 1970 (), and is codified at as . This article primarily covers the federal criminal statute, but since 1972, 33 U.S. states and territories have adopted state RICO laws, which although similar, cover additional state crimes and may differ from the federal law and each other in several respects. History G. Robert Blakey, an adviser to the United States Senate Government Operations Committee, drafted the law under the close supervision of Senator John L. McClellan, the Chairman of the Criminal Law and Procedures Subcommittee of the Senate Judiciary Committee. It was signed into law by US President Richard Nixon. Prosecutors in the 1970s used it to prosecute the Mafia as well ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
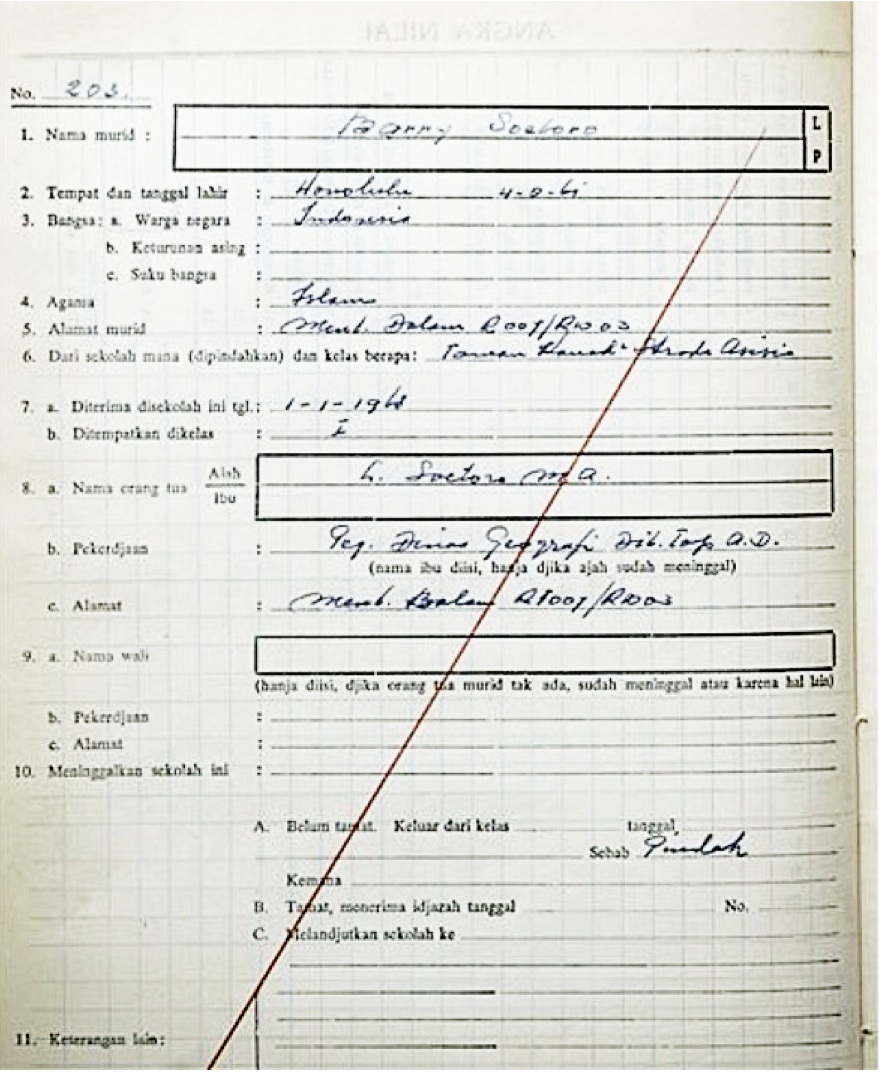
Barack Obama
Barack Hussein Obama II (born August 4, 1961) is an American politician who was the 44th president of the United States from 2009 to 2017. A member of the Democratic Party, he was the first African American president in American history. Obama previously served as a U.S. senator representing Illinois from 2005 to 2008 and as an Illinois state senator from 1997 to 2004. Born in Honolulu, Hawaii, Obama graduated from Columbia University in 1983 with a Bachelor of Arts degree in political science and later worked as a community organizer in Chicago. In 1988, Obama enrolled in Harvard Law School, where he was the first black president of the ''Harvard Law Review''. He became a civil rights attorney and an academic, teaching constitutional law at the University of Chicago Law School from 1992 to 2004. In 1996, Obama was elected to represent the 13th district in the Illinois Senate, a position he held until 2004, when he successfully ran for the U.S. Senate. In the 2008 pre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Passwords
A password, sometimes called a passcode, is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services that a typical individual accesses can make memorization of unique passwords for each service impractical. Using the terminology of the NIST Digital Identity Guidelines, the secret is held by a party called the ''claimant'' while the party verifying the identity of the claimant is called the ''verifier''. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity. In general, a password is an arbitrary string of characters including letters, digits, or other symbols. If the permissible characters are constrained to be numeric, the corresponding secret is sometimes called a personal identification number (PIN). ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Denial-of-service Attack
In computing, a denial-of-service attack (DoS attack) is a cyberattack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. The range of attacks varies widely, spanning from inundating a server with millions of requests to slow its performance, overwhelming a server with a substantial amount of invalid data, to submitting requests with an illegitimate IP address. In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources. More sophisticated strategies are required to mitigate this type of attack; simply attempting to block a single source is insuffic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to cause disruption to a computer, server (computing), server, Client (computing), client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types (i.e. computer viruses, Computer worm, worms, Trojan horse (computing), Trojan horses, logic bombs, ransomware, spyware, adware, rogue software, Wiper (malware), wipers and keyloggers). Malware poses serious problems to individuals and businesses on the Internet. According to NortonLifeLock, Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 66 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Contract Law
A contract is an agreement that specifies certain legally enforceable rights and obligations pertaining to two or more Party (law), parties. A contract typically involves consent to transfer of goods, Service (economics), services, money, or promise to transfer any of those at a future date. The activities and intentions of the parties entering into a contract may be referred to as contracting. In the event of a breach of contract, the injured party may seek legal remedy, judicial remedies such as damages or equitable remedies such as specific performance or Rescission (contract law), rescission. A binding agreement between actors in international law is known as a treaty. Contract law, the field of the law of obligations concerned with contracts, is based on the principle that pacta sunt servanda, agreements must be honoured. Like other areas of private law, contract law varies between jurisdictions. In general, contract law is exercised and governed either under common law jur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |