|
Communications Security Board
The Committee on National Security Systems (CNSS) is a United States intergovernmental organization that sets policies for the security of the US security systems. The CIA triad ( data confidentiality, data integrity, and data availability) are the three main security goals of CNSS. History The Committee dates its establishment back to 1953, under the name of U.S. Communications Security Board (USCSB). Under the name National Security Telecommunications and Information Systems Security Committee (NSTISSC) the committee was established by the National Security Directive 42, "National Policy for the Security of National Security Telecommunications and Information Systems", dated 5 July 1990. On October 16, 2001, President George W. Bush signed Executive Order 13231, the Critical Infrastructure Protection in the Information Age, re-designating NSTISSC as the Committee on National Security Systems. Activities The CNSS holds discussions of policy issues, sets national policy, direc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fort George G
A fortification (also called a fort, fortress, fastness, or stronghold) is a military construction designed for the defense of territories in warfare, and is used to establish rule in a region during peacetime. The term is derived from Latin ("strong") and ("to make"). From very early history to modern times, defensive walls have often been necessary for cities to survive in an ever-changing world of invasion and conquest. Some settlements in the Indus Valley Civilization were the first small cities to be fortified. In ancient Greece, large cyclopean stone walls fitted without mortar had been built in Mycenaean Greece, such as the ancient site of Mycenae. A Greek '' phrourion'' was a fortified collection of buildings used as a military garrison, and is the equivalent of the Roman castellum or fortress. These constructions mainly served the purpose of a watch tower, to guard certain roads, passes, and borders. Though smaller than a real fortress, they acted as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Defense Information Systems Agency
The Defense Information Systems Agency (DISA), known as the Defense Communications Agency (DCA) until 1991, is a United States Department of Defense (DoD) combat support agency. It is composed of military, federal civilians, and contractors. DISA provides information technology (IT) and communications support to the President, Vice President, Secretary of Defense, the Department of Defense, the combatant commands, and any individual or system contributing to the defense of the United States. History 1960s: The Defense Communications Agency DCA was established May 12, 1960, with the primary mission of operational control and management of the Defense Communications System (DCS). The initial headquarters for 34 DCA members was Wake Hall, one of a complex of three buildings (which included Midway Hall and Guam Hall) on the site where the parking lot of the Robert F. Kennedy Stadium in Washington, D.C., stands today. Navy Rear Admiral William D. Irvin became the first DCA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Independent Agencies Of The United States Government
In the Federal government of the United States, United States federal government, independent agencies are List of federal agencies in the United States, agencies that exist outside the United States federal executive departments, federal executive departments (those headed by a United States Cabinet, Cabinet secretary) and the Executive Office of the President of the United States, Executive Office of the President. In a narrower sense, the term refers only to those independent agencies that, while considered part of the Executive branch of the United States, executive branch, have administrative law, regulatory or rulemaking authority and are insulated from presidential control, usually because the president's power to dismiss the agency head or a member is limited. Established through separate United States Code, statutes passed by United States Congress, Congress, each respective Organic law, statutory grant of authority defines the goals the agency must work towards, as wel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States Government Secrecy
The United States government classification system is established under Executive Order 13526, the latest in a long series of executive orders on the topic of classified information beginning in 1951. Issued by President Barack Obama in 2009, Executive Order 13526 replaced earlier executive orders on the topic and modified the regulations codified to 32 C.F.R. 2001. It lays out the system of classification, declassification, and handling of national security information generated by the U.S. government and its employees and contractors, as well as information received from other governments. The desired degree of secrecy about such information is known as its sensitivity. Sensitivity is based upon a calculation of the damage to national security that the release of the information would cause. The United States has three levels of classification: Confidential, Secret, and Top Secret. Each level of classification indicates an increasing degree of sensitivity. Thus, if one holds ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security Organizations
A computer is a machine that can be programmed to automatically carry out sequences of arithmetic or logical operations (''computation''). Modern digital electronic computers can perform generic sets of operations known as ''programs'', which enable computers to perform a wide range of tasks. The term computer system may refer to a nominally complete computer that includes the hardware, operating system, software, and peripheral equipment needed and used for full operation; or to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems, including simple special-purpose devices like microwave ovens and remote controls, and factory devices like industrial robots. Computers are at the core of general-purpose devices such as personal computers and mobile devices such as smartphones. Computers power the Internet, which links billions of compute ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
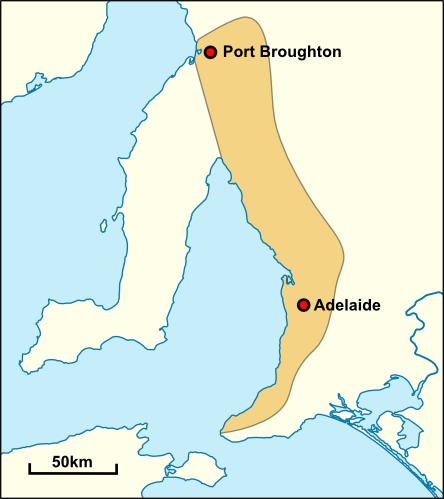
Adelaide, Australia
Adelaide ( , ; ) is the list of Australian capital cities, capital and most populous city of South Australia, as well as the list of cities in Australia by population, fifth-most populous city in Australia. The name "Adelaide" may refer to either Greater Adelaide (including the Adelaide Hills) or the Adelaide city centre; the demonym ''Adelaidean'' is used to denote the city and the residents of Adelaide. The Native title in Australia#Traditional owner, traditional owners of the Adelaide region are the Kaurna, with the name referring to the area of the city centre and surrounding Adelaide Park Lands, Park Lands, in the Kaurna language. Adelaide is situated on the Adelaide Plains north of the Fleurieu Peninsula, between the Gulf St Vincent in the west and the Mount Lofty Ranges in the east. Its metropolitan area extends from the coast to the Adelaide Hills, foothills of the Mount Lofty Ranges, and stretches from Gawler in the north to Sellicks Beach in the south. Named in ho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of South Australia
The University of South Australia is a public research university based in Adelaide, South Australia. Established in 1991, it is the successor of the former South Australian Institute of Technology. Its main campuses along North Terrace are adjacent to the Australian Space Agency in Lot Fourteen and forms part of the Adelaide BioMed City research precinct. It also has a presence in the Adelaide Technology Park in Mawson Lakes. In mid-2023, it agreed to merge with the neighbouring University of Adelaide to form Adelaide University. Its earliest antecedent institutions were both founded in the Jubilee Exhibition Building of the former Royal South Australian Society of Arts. The South Australian Institute of Technology was founded in 1889 as the School of Mines and Industries and the South Australian College of Advanced Education dates back to the School of Art in 1856. The institute later gained university status during the Dawkins Revolution following their merger in 199 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Information Assurance Certification And Accreditation Process
The National Information Assurance Certification and Accreditation Process (NIACAP) formerly was the minimum-standard process for the certification and accreditation of computer and telecommunications systems that handle U.S. national-security information. NIACAP was derived from the Department of Defense Certification and Accreditation Process (DITSCAP), and it played a key role in the National Information Assurance Partnership. The Committee on National Security Systems (CNSS) Policy (CNSSP) No. 22 dated January 2012 cancelled CNSS Policy No. 6, “National Policy on Certification and Accreditation of National Security Systems,” dated October 2005, and National Security Telecommunications and Information Systems Security Instruction (NSTISSI) 1000, “National Information Assurance Certification and Accreditation Process (NIACAP),” dated April 2000. CNSSP No. 22 also states that "The CNSS intends to adopt National Institute of Standards and Technology The National Ins ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certification
Certification is part of testing, inspection and certification and the provision by an independent body of written assurance (a certificate) that the product, service or system in question meets specific requirements. It is the formal attestation or confirmation of certain characteristics of an object, person, or organization. This confirmation is often, but not always, provided by some form of external review, education, assessment, or audit. Accreditation is a specific organization's process of certification. According to the U.S. National Council on Measurement in Education, a certification test is a credentialing test used to determine whether individuals are knowledgeable enough in a given occupational area to be labeled "competent to practice" in that area. As a rule, certificates must be renewed and periodically reviewed by a certifying regulatory body responsible for the validity of the certificate's assessment methods. The certifying body can be either a state authority ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for global intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of personnel and budget. Still, information available as of 2013 indicates that the C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Reconnaissance Office
The National Reconnaissance Office (NRO) is a member of the United States Intelligence Community and an agency of the United States Department of Defense which designs, builds, launches, and operates the reconnaissance satellites of the U.S. federal government. It provides satellite intelligence to several government agencies, particularly signals intelligence (SIGINT) to the National Security Agency (NSA), imagery intelligence (IMINT) to the National Geospatial-Intelligence Agency (NGA), and measurement and signature intelligence (MASINT) to the Defense Intelligence Agency (DIA). The NRO announced in 2023 that it plans within the following decade to quadruple the number of satellites it operates and increase the number of signals and images it delivers by a factor of ten. NRO is considered, along with the Central Intelligence Agency (CIA), NSA, DIA, and NGA, to be one of the "big five" U.S. intelligence agencies. The NRO is headquartered in Chantilly, Virginia, south of Wa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |