|
Codebreaking
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
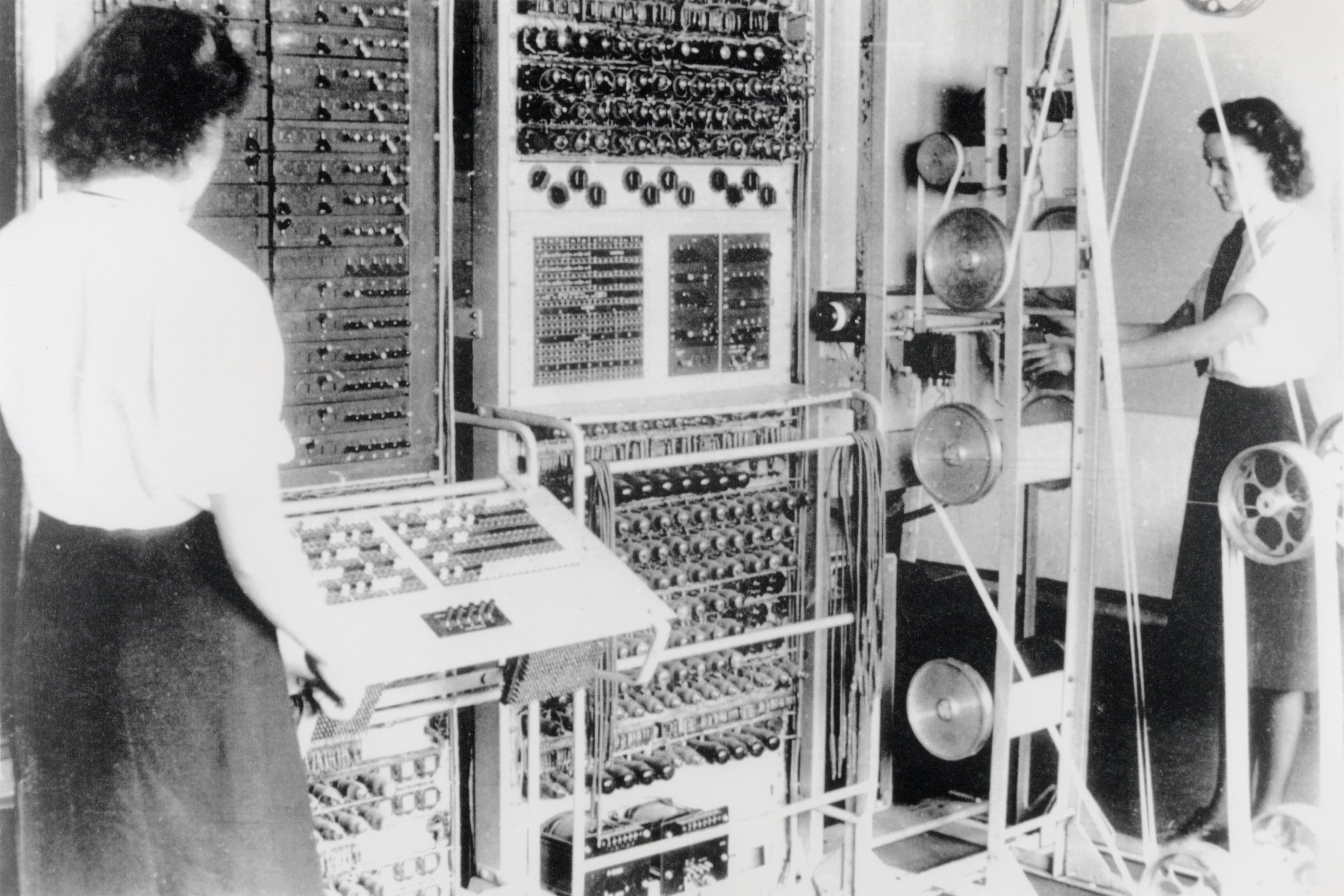
Colossus Computer
Colossus was a set of computers developed by British cryptanalysis, codebreakers in the years 1943–1945 to help in the cryptanalysis of the Lorenz cipher. Colossus used vacuum tube, thermionic valves (vacuum tubes) to perform Boolean algebra (logic), Boolean and counting operations. Colossus is thus regarded as the world's first computer programming, programmable, electronics, electronic, digital electronics, digital computer, although it was programmed by switches and plugs and not by a stored-program computer, stored program. Colossus was designed by General Post Office (GPO) research telephone engineer Tommy Flowers based on plans developed by mathematician Max Newman at the Government Code and Cypher School at Bletchley Park. Alan Turing's use of probability in cryptanalysis (see Banburismus) contributed to its design. It has sometimes been erroneously stated that Turing designed Colossus to aid the cryptanalysis of the Enigma. (Turing's machine that helped decode Enigma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
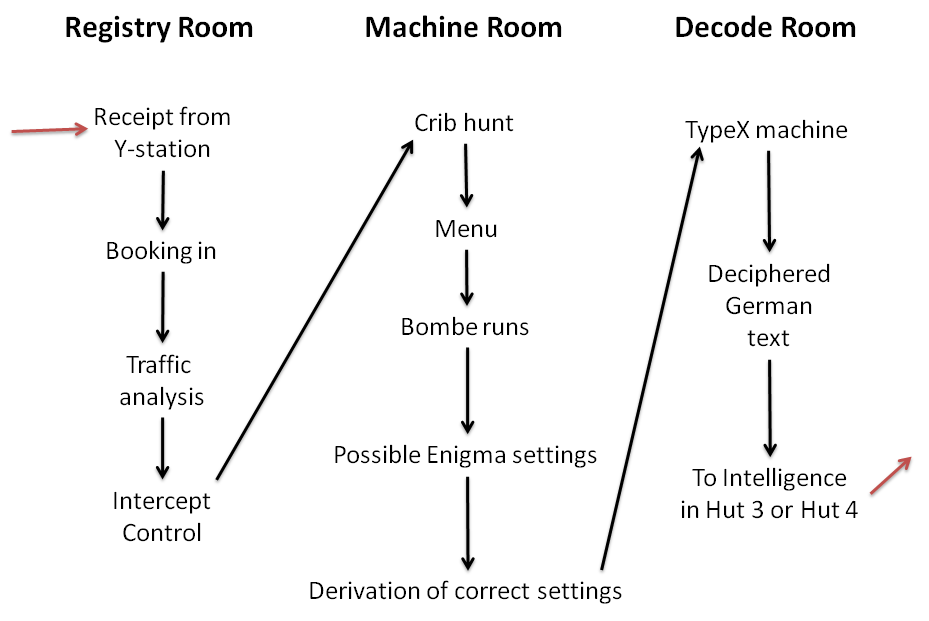
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the Second World War. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers most importantly the German Enigma machine, Enigma and Lorenz cipher, Lorenz ciphers. The GC&CS team of codebreakers included John Tiltman, Dilwyn Knox, Alan Turing, Harry Golombek, Gordon Welchman, Conel Hugh O'Donel Alexander, Hugh Alexander, Donald Michie, W. T. Tutte, Bill Tutte and Stuart Milner-Barry. The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus computer, Colossus, the world's first programmable digital electronic computer. Codebreaking operations at Bletchley Park ended in 1946 and al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lorenz Cipher
The Lorenz SZ40, SZ42a and SZ42b were German Rotor machine, rotor stream cipher machines used by the German Army (Wehrmacht), German Army during World War II. They were developed by C. Lorenz AG in Berlin. The model name ''SZ'' is derived from ''Schlüssel-Zusatz'', meaning ''cipher attachment''. The instruments implemented a Gilbert Vernam#The Vernam cipher, Vernam stream cipher. British cryptanalysts, who referred to encrypted German Electrical telegraph, teleprinter traffic as Fish (cryptography), ''Fish'', dubbed the machine and its traffic ''Tunny'' (meaning tunafish) and deduced its logical structure three years before they saw such a machine. The SZ machines were in-line attachments to standard teleprinters. An experimental link using SZ40 machines was started in June 1941. The enhanced SZ42 machines were brought into substantial use from mid-1942 onwards for high-level communications between the Oberkommando der Wehrmacht, German High Command in Wünsdorf close to Berlin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Claude Shannon
Claude Elwood Shannon (April 30, 1916 – February 24, 2001) was an American mathematician, electrical engineer, computer scientist, cryptographer and inventor known as the "father of information theory" and the man who laid the foundations of the Information Age. Shannon was the first to describe the use of Boolean algebra—essential to all digital electronic circuits—and helped found artificial intelligence (AI). Roboticist Rodney Brooks declared Shannon the 20th century engineer who contributed the most to 21st century technologies, and mathematician Solomon W. Golomb described his intellectual achievement as "one of the greatest of the twentieth century". At the University of Michigan, Shannon dual degreed, graduating with a Bachelor of Science in electrical engineering and another in mathematics, both in 1936. A 21-year-old master's degree student in electrical engineering at MIT, his thesis, "A Symbolic Analysis of Relay and Switching Circuits", demonstrated that electric ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bombe
The bombe () was an Electromechanics, electro-mechanical device used by British cryptologists to help decipher German Enigma machine, Enigma-machine-encrypted secret messages during World War II. The United States Navy, US Navy and United States Army, US Army later produced their own machines to the same functional specification, albeit engineered differently both from each other and from Polish and British bombes. The British bombe was developed from a device known as the "Bomba (cryptography), bomba" (), which had been designed in Poland at the Biuro Szyfrów (Cipher Bureau) by cryptologist Marian Rejewski, who had been breaking German Enigma machine, Enigma messages for the previous seven years, using it and earlier machines. The initial design of the British bombe was produced in 1939 at the UK Government Code and Cypher School (GC&CS) at Bletchley Park by Alan Turing, with an important refinement devised in 1940 by Gordon Welchman. The engineering design and construction ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. This process prevents the loss of sensitive information via hacking. Decryption, the inverse of encryption, is the process of turning ciphertext into readable plaintext. Ciphertext is not to be confused with codetext because the latter is a result of a code, not a cipher. Conceptual underpinnings Let m\! be the plaintext message that Alice wants to secretly transmit to Bob and let E_k\! be the encryption cipher, where _k\! is a secret key, cryptographic key. Alice must first transform the plaintext into ciphertext, c\!, in order to securely send the message to Bob, as follows: : c = E_k(m). \! In a symmetric-key system, Bob knows Alice's encryption key. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Algorithm
In mathematics and computer science, an algorithm () is a finite sequence of Rigour#Mathematics, mathematically rigorous instructions, typically used to solve a class of specific Computational problem, problems or to perform a computation. Algorithms are used as specifications for performing calculations and data processing. More advanced algorithms can use Conditional (computer programming), conditionals to divert the code execution through various routes (referred to as automated decision-making) and deduce valid inferences (referred to as automated reasoning). In contrast, a Heuristic (computer science), heuristic is an approach to solving problems without well-defined correct or optimal results.David A. Grossman, Ophir Frieder, ''Information Retrieval: Algorithms and Heuristics'', 2nd edition, 2004, For example, although social media recommender systems are commonly called "algorithms", they actually rely on heuristics as there is no truly "correct" recommendation. As an e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Betrayal
Betrayal is the breaking or violation of a presumptive contract, trust, or confidence that produces moral and psychological conflict within a relationship amongst individuals, between organizations or between individuals and organizations. Often betrayal is the act of supporting a rival group, or it is a complete break from previously decided upon or presumed norms by one party from the others. Someone who betrays others is commonly known as a traitor or betrayer. Betrayal is a commonly used story element in fiction, sometimes used as a plot twist. Definition Philosophers Judith Shklar and Peter Johnson, authors of ''The Ambiguities of Betrayal'' and ''Frames of Deceit'', respectively, contend that while no clear definition of betrayal is available, betrayal is more effectively understood through literature. Theoretical and practical needs Rodger L. Jackson explains why a clear definition is needed: Betrayal is both a "people" problem and a philosopher's problem. Philoso ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Espionage
Espionage, spying, or intelligence gathering, as a subfield of the intelligence field, is the act of obtaining secret or confidential information ( intelligence). A person who commits espionage on a mission-specific contract is called an ''espionage agent'' or ''spy''. A person who commits espionage as a fully employed officer of a government is called an intelligence officer. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kerckhoffs's Principle
Kerckhoffs's principle (also called Kerckhoffs's desideratum, assumption, axiom, doctrine or law) of cryptography was stated by the Dutch cryptographer Auguste Kerckhoffs in the 19th century. The principle holds that a cryptosystem should be secure, even if everything about the system, except the key, is public knowledge. This concept is widely embraced by cryptographers, in contrast to security through obscurity, which is not. Kerckhoffs's principle was phrased by the American mathematician Claude Shannon as "the enemy knows the system", i.e., "one ought to design systems under the assumption that the enemy will immediately gain full familiarity with them". In that form, it is called Shannon's maxim. Another formulation by American researcher and professor Steven M. Bellovin is: In other words—design your system assuming that your opponents know it in detail. (A former official at NSA's National Computer Security Center told me that the standard assumption there was that ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reverse Engineering
Reverse engineering (also known as backwards engineering or back engineering) is a process or method through which one attempts to understand through deductive reasoning how a previously made device, process, system, or piece of software accomplishes a task with very little (if any) insight into exactly how it does so. Depending on the system under consideration and the technologies employed, the knowledge gained during reverse engineering can help with repurposing obsolete objects, doing security analysis, or learning how something works. Although the process is specific to the object on which it is being performed, all reverse engineering processes consist of three basic steps: information extraction, modeling, and review. Information extraction is the practice of gathering all relevant information for performing the operation. Modeling is the practice of combining the gathered information into an abstract model, which can be used as a guide for designing the new object or syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Model
In cryptanalysis, attack models or attack types are a classification of cryptographic attacks specifying the kind of access a Cryptanalysis, cryptanalyst has to a system under attack when attempting to "break" an Encryption, encrypted message (also known as ''ciphertext'') generated by the system. The greater the access the cryptanalyst has to the system, the more useful information they can get to utilize for breaking the cypher. In cryptography, a sending party uses a cipher to encryption, encrypt (transform) a secret ''plaintext'' into a ''ciphertext'', which is sent over an insecure communication channel to the receiving party. The receiving party uses an inverse cipher to decryption, decrypt the ciphertext to obtain the plaintext. A secret knowledge is required to apply the inverse cipher to the ciphertext. This secret knowledge is usually a short number or string called a ''cryptographic key, key''. In a cryptographic attack a third party cryptanalyst analyzes the ciphertex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |