|
Authorship Obfuscation
Adversarial stylometry is the practice of altering writing style to reduce the potential for stylometry to discover the author's identity or their characteristics. This task is also known as authorship obfuscation or authorship anonymisation. Stylometry poses a significant privacy challenge in its ability to unmask anonymity, anonymous authors or to link pseudonyms to an author's other identities, which, for example, creates difficulties for whistleblowers, activists, and hoaxers and fraudsters. The privacy risk is expected to grow as machine learning techniques and text corpora develop. All adversarial stylometry shares the core idea of faithfully paraphrasing (computational linguistics), paraphrasing the source text so that the meaning is unchanged but the stylistic signals are obscured. Such a faithful paraphrase is an adversarial example for a stylometric classifier. Several broad approaches to this exist, with some overlap: ''imitation'', substituting the author's own style ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stylometry
Stylometry is the application of the study of linguistic style, usually to written language. Argamon, Shlomo, Kevin Burns, and Shlomo Dubnov, eds. The structure of style: algorithmic approaches to understanding manner and meaning. Springer Science & Business Media, 2010. It has also been applied successfully to music, paintings, and chess. Stylometry is often used to attribute authorship to anonymous or disputed documents. It has legal as well as academic and literary applications, ranging from the question of the authorship of Shakespeare's works to forensic linguistics and has methodological similarities with the analysis of text readability. Stylometry may be used to unmask pseudonymous or anonymous authors, or to reveal some information about the author short of a full identification. Authors may use adversarial stylometry to resist this identification by eliminating their own stylistic characteristics without changing the meaningful content of their communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymity Set
Anonymity describes situations where the acting person's identity is unknown. Anonymity may be created unintentionally through the loss of identifying information due to the passage of time or a destructive event, or intentionally if a person chooses to withhold their identity. There are various situations in which a person might choose to remain anonymous. Acts of charity have been performed anonymously when benefactors do not wish to be acknowledged. A person who feels threatened might attempt to mitigate that threat through anonymity. A witness to a crime might seek to avoid retribution, for example, by anonymously calling a crime tipline. In many other situations (like conversation between strangers, or buying some product or service in a shop), anonymity is traditionally accepted as natural. Some writers have argued that the term "namelessness", though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
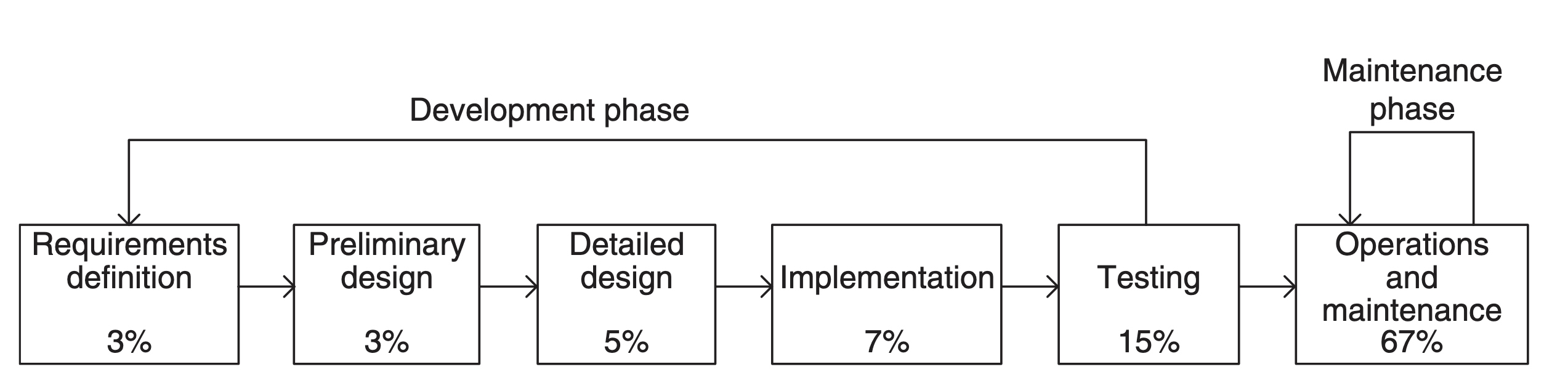
Scalability
Scalability is the property of a system to handle a growing amount of work. One definition for software systems specifies that this may be done by adding resources to the system. In an economic context, a scalable business model implies that a company can increase sales given increased resources. For example, a package delivery system is scalable because more packages can be delivered by adding more delivery vehicles. However, if all packages had to first pass through a single warehouse for sorting, the system would not be as scalable, because one warehouse can handle only a limited number of packages. In computing, scalability is a characteristic of computers, networks, algorithms, networking protocols, programs and applications. An example is a search engine, which must support increasing numbers of users, and the number of topics it indexes. Webscale is a computer architectural approach that brings the capabilities of large-scale cloud computing companies into enterprise ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Maintenance
Software maintenance is the modification of software after delivery. Software maintenance is often considered lower skilled and less rewarding than new development. As such, it is a common target for outsourcing or offshoring. Usually, the team developing the software is different from those who will be maintaining it. The developers lack an incentive to write the code to be easily maintained. Software is often delivered incomplete and almost always contains some bugs that the maintenance team must fix. Software maintenance often initially includes the development of new functionality, but as the product nears the end of its lifespan, maintenance is reduced to the bare minimum and then cut off entirely before the product is withdrawn. Each maintenance cycle begins with a change request typically originating from an end user. That request is evaluated and if it is decided to implement it, the programmer studies the existing code to understand how it works before implementing the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Search Problem
In computational complexity theory and computability theory, a search problem is a computational problem of finding an ''admissible'' answer for a given input value, provided that such an answer exists. In fact, a search problem is specified by a binary relation where if and only if "'' is an admissible answer given ''". Search problems frequently occur in graph theory and combinatorial optimization, e.g. searching for matchings, optional cliques, and stable sets in a given undirected graph. An algorithm is said to solve a search problem if, for every input value , it returns an admissible answer for when such an answer exists; otherwise, it returns any appropriate output, e.g. "not found" for with no such answer. Definition PlanetMath defines the problem as follows: If R is a binary relation such that \operatorname(R)\subseteq\Gamma^ and T is a Turing machine, then T calculates f if: * If x is such that there is some y such that R(x,y) then T accepts x with output z suc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Heuristic (computer Science)
A heuristic or heuristic technique (''problem solving'', ''Heuristic (psychology), mental shortcut'', ''rule of thumb'') is any approach to problem solving that employs a Pragmatism, pragmatic method that is not fully Mathematical optimisation, optimized, perfected, or Rationality, rationalized, but is nevertheless "good enough" as an approximation or attribute substitution. Where finding an optimal solution is impossible or impractical, heuristic methods can be used to speed up the process of finding a satisfactory solution. Heuristics can be mental shortcuts that ease the cognitive load of Decision-making, making a decision. Context Gigerenzer & Gaissmaier (2011) state that Set (mathematics), sub-sets of ''strategy'' include heuristics, regression analysis, and Bayesian inference. Heuristics are strategies based on rules to generate optimal decisions, like the anchoring effect and utility maximization problem. These strategies depend on using readily accessible, thoug ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rule-based System
In computer science, a rule-based system is a computer system in which domain-specific knowledge is represented in the form of rules and general-purpose reasoning is used to solve problems in the domain. Two different kinds of rule-based systems emerged within the field of artificial intelligence in the 1970s: * Production systems, which use ''if-then rules'' to derive ''actions'' from ''conditions''. * Logic programming systems, which use ''conclusion if conditions rules'' to derive ''conclusions'' from ''conditions''. The differences and relationships between these two kinds of rule-based system has been a major source of misunderstanding and confusion. Both kinds of rule-based systems use either forward or backward chaining, in contrast with imperative programs, which execute commands listed sequentially. However, logic programming systems have a logical interpretation, whereas production systems do not. Production system rules A classic example of a production rule-b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Letter Frequency
Letter frequency is the number of times letters of the alphabet appear on average in written language. Letter frequency analysis dates back to the Arab mathematician Al-Kindi (c. AD 801–873), who formally developed the method to break ciphers. Letter frequency analysis gained importance in Europe with the development of movable type in AD 1450, wherein one must estimate the amount of type required for each letterform. Linguists use letter frequency analysis as a rudimentary technique for language identification, where it is particularly effective as an indication of whether an unknown writing system is alphabetic, syllabic, or ideographic. The use of letter frequencies and frequency analysis plays a fundamental role in cryptograms and several word puzzle games, including hangman, ''Scrabble'', '' Wordle'' and the television game show '' Wheel of Fortune''. One of the earliest descriptions in classical literature of applying the knowledge of English letter frequency to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google Translate
Google Translate is a multilingualism, multilingual neural machine translation, neural machine translation service developed by Google to translation, translate text, documents and websites from one language into another. It offers a web application, website interface, a mobile app for Android (operating system), Android and iOS, as well as an API that helps developers build browser extensions and application software, software applications. As of , Google Translate supports languages and language varieties at various levels. It served over 200 million people daily in May 2013, and over 500 million total users , with more than 100 billion words translated daily. Launched in April 2006 as a statistical machine translation service, it originally used United Nations and European Parliament documents and transcripts to gather linguistic data. Rather than translating languages directly, it first translated text to English and then pivoted to the target language in most of the langu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Round-trip Translation
Round-trip translation (RTT), also known as back-and-forth translation, recursive translation and bi-directional translation, is the process of translating a word, phrase or text into another language (forward translation), then translating the result back into the original language ( back translation), using machine translation (MT) software. It is often used by laypeople to evaluate a machine translation system,van Zaanen, Menno & Zwarts, Simon (2006). "Unsupervised measurement of translation quality using multi-engine, bidirectional translation". AI 2006. Springer-Verlag: 1208-1214 or to test whether a text is suitable for MTGaspari, Federico (2006). "Look who's translating. Impersonation, Chinese whispers and fun with machine translation on the Internet. EAMT-2006: 149-158 via Mt- Archive.Shigenobu, Tomohiro (2007). "Evaluation and Usability of Back Translation for Intercultural Communication". In Aykin N. ''Usability and Internationalization, Part II. Berlin'': Springer-Verla ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Text Generation
Natural language generation (NLG) is a software process that produces natural language output. A widely cited survey of NLG methods describes NLG as "the subfield of artificial intelligence and computational linguistics that is concerned with the construction of computer systems that can produce understandable texts in English or other human languages from some underlying non-linguistic representation of information". While it is widely agreed that the output of any NLG process is text, there is some disagreement about whether the inputs of an NLG system need to be non-linguistic. Common applications of NLG methods include the production of various reports, for example weather and patient reports; image captions; and chatbots like ChatGPT. Automated NLG can be compared to the process humans use when they turn ideas into writing or speech. Psycholinguists prefer the term language production for this process, which can also be described in mathematical terms, or modeled in a comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |