|
Authorised Engineering Organisation Certification
Authorization or authorisation (see spelling differences), in information security, computer security and IAM (Identity and Access Management), is the function of specifying rights/privileges for accessing resources, in most cases through an access policy, and then deciding whether a particular ''subject'' has privilege to access a particular ''resource''. Examples of ''subjects'' include human users, computer software and other hardware on the computer. Examples of ''resources'' include individual files or an item's data, computer programs, computer devices and functionality provided by computer applications. For example, user accounts for human resources staff are typically configured with authorization for accessing employee records. Authorization is closely related to access control, which is what enforces the authorization policy by deciding whether access requests to resources from ( authenticated) consumers shall be approved (granted) or disapproved (rejected). Autho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
American And British English Spelling Differences
Despite the various list of dialects of English, English dialects spoken from country to country and within different regions of the same country, there are only slight regional variations in English orthography, the two most notable variations being British and American spelling. Many of Comparison of American and British English, the differences between American English, American and British English, British or English in the Commonwealth of Nations, Commonwealth English date back to a time before spelling standards were developed. For instance, some spellings seen as "American" today were once commonly used in Britain, and some spellings seen as "British" were once commonly used in the United States. A "British standard" began to emerge following the 1755 publication of Samuel Johnson's ''A Dictionary of the English Language'', and an "American standard" started following the work of Noah Webster and, in particular, his ''Webster's Dictionary, An American Dictionary of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Capability-based Security
Capability-based security is a concept in the design of secure computing systems, one of the existing security models. A capability (known in some systems as a key) is a communicable, unforgeable token of authority. It refers to a value that references an object along with an associated set of access rights. A user program on a capability-based operating system must use a capability to access an object. Capability-based security refers to the principle of designing user programs such that they directly share capabilities with each other according to the principle of least privilege, and to the operating system infrastructure necessary to make such transactions efficient and secure. Capability-based security is to be contrasted with an approach that uses traditional UNIX permissions and access control lists. Although most operating systems implement a facility which resembles capabilities, they typically do not provide enough support to allow for the exchange of capabilitie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bank
A bank is a financial institution that accepts Deposit account, deposits from the public and creates a demand deposit while simultaneously making loans. Lending activities can be directly performed by the bank or indirectly through capital markets. As banks play an important role in financial stability and the economy of a country, most jurisdictions exercise a high degree of Bank regulation, regulation over banks. Most countries have institutionalized a system known as fractional-reserve banking, under which banks hold liquid assets equal to only a portion of their current liabilities. In addition to other regulations intended to ensure accounting liquidity, liquidity, banks are generally subject to minimum capital requirements based on an international set of capital standards, the Basel Accords. Banking in its modern sense evolved in the fourteenth century in the prosperous cities of Renaissance Italy but, in many ways, functioned as a continuation of ideas and concepts o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Social Control
Social control is the regulations, sanctions, mechanisms, and systems that restrict the behaviour of individuals in accordance with social norms and orders. Through both informal and formal means, individuals and groups exercise social control both internally and externally. As an area of social science, social control is studied by researchers of various fields, including anthropology, criminology, law, political science, and sociology. Social control is considered one of the foundations of social order. Sociologists identify two basic forms of social control. Informal means of control refer to the internalization of norms and values through socialization. Formal means comprise external sanctions enforced by government to prevent the establishment of chaos or anomie in society. Some theorists, such as Émile Durkheim, refer to formal control as regulation. History Social control developed together with civilization, as a rational measure against the uncontrolla ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security
Security is protection from, or resilience against, potential harm (or other unwanted coercion). Beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g., freedom from want); as the presence of an essential good (e.g., food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g., a secure telephone line); as containment (e.g., a secure room or cell); and as a state of mind (e.g., emotional security). Security is both a feeling and a state of reality. One might feel secure when one is not actually so; or might feel insecure despite being safe. This distinction is usually not very clear to express in the English language. The term is also used to refer to acts ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Policy
Policy is a deliberate system of guidelines to guide decisions and achieve rational outcomes. A policy is a statement of intent and is implemented as a procedure or protocol. Policies are generally adopted by a governance body within an organization. Policies can assist in both ''subjective'' and ''objective'' decision making. Policies used in subjective decision-making usually assist senior management with decisions that must be based on the relative merits of a number of factors, and as a result, are often hard to test objectively, e.g. work–life balance policy. Moreover, governments and other institutions have policies in the form of laws, regulations, procedures, administrative actions, incentives and voluntary practices. Frequently, resource allocations mirror policy decisions. Policies intended to assist in objective decision-making are usually operational in nature and can be objectively tested, e.g. a password policy. The term may apply to government, public se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Relationship-based Access Control
In computer systems security, Relationship-based access control (ReBAC) defines an authorization paradigm where a subject's permission to access a resource is defined by the presence of relationships between those subjects and resources. In general, authorization in ReBAC is performed by traversing the directed graph of relationships. The nodes and edges of this graph are very similar to triples in the Resource Description Framework (RDF) data format. ReBAC systems allow hierarchies of relationships, and some allow more complex definitions that include algebraic operators on relationships such as union, intersection, and difference. ReBAC gained popularity with the rise of social network web applications, where users need to control their personal information based on their relationship with the data receiver rather than the receiver’s role. Using ReBAC enabled to collectively define permissions for teams and groups, thus eliminating the need to set permissions individually for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Role-based Access Control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users, and to implementing mandatory access control (MAC) or discretionary access control, discretionary access control (DAC). Role-based access control is a policy-neutral access control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations. RBAC can be used to facilitate administration of security in large organizations with hundreds of users and thousands of permissions. Although RBAC is different from MAC and DAC access control frameworks, it can enforce these policies without any complication. Design Within an organization, role (computer science), roles are created for various job functions. The permiss ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apress
Springer Nature or the Springer Nature Group is a German-British academic publishing company created by the May 2015 merger of Springer Science+Business Media and Holtzbrinck Publishing Group's Nature Publishing Group, Palgrave Macmillan, and Macmillan Education. History The company originates from several journals and publishing houses, notably Springer-Verlag, which was founded in 1842 by Julius Springer in Berlin (the grandfather of Bernhard Springer who founded Springer Publishing in 1950 in New York), Nature Portfolio, Nature Publishing Group which has published ''Nature (journal) , Nature'' since 1869, and Macmillan Education, which goes back to Macmillan Publishers founded in 1843. Springer Nature was formed in 2015 by the merger of Nature Publishing Group, Palgrave Macmillan, and Macmillan Education (held by Holtzbrinck Publishing Group) with Springer Science+Business Media (held by BC Partners). Plans for the merger were first announced on 15 January 2015. The transactio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
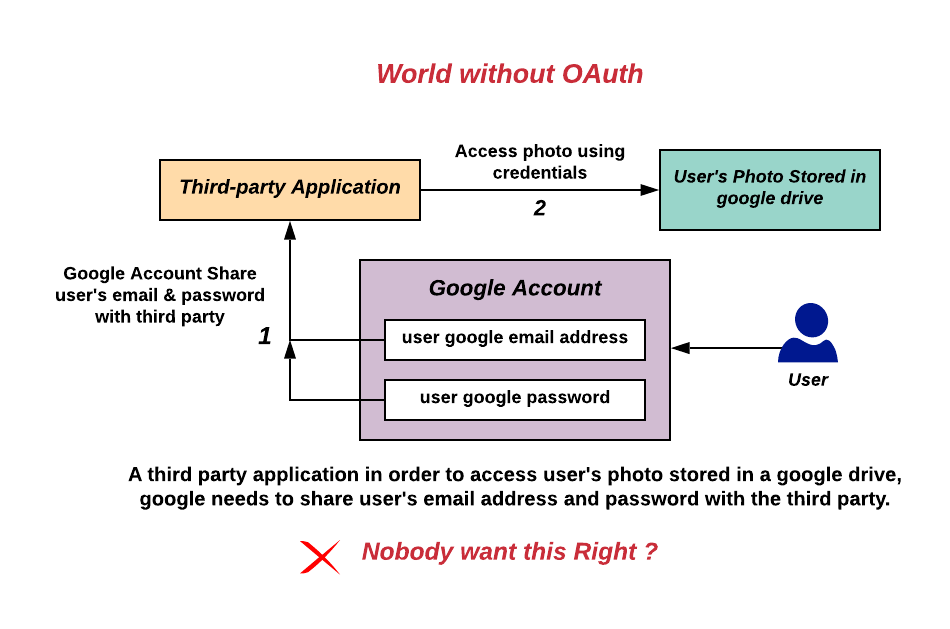
OAuth 2
OAuth (short for open authorization) is an Open standard , open standard for access Delegation (computer security), delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon (company), Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resourc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |