|
802.1X
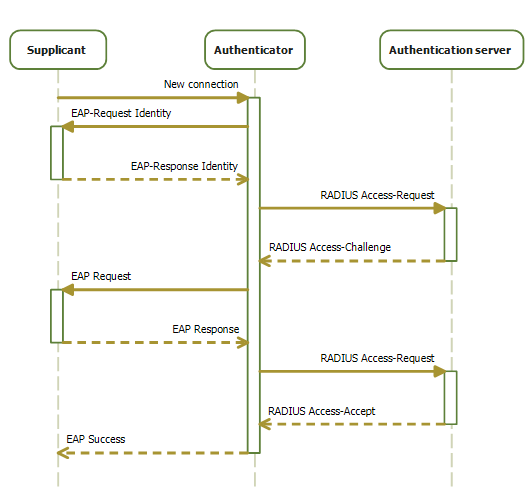
IEEE 802.1X is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN. IEEE 802.1X defines the encapsulation of the Extensible Authentication Protocol (EAP) over wired IEEE 802 networksand over 802.11 wireless networks, which is known as "EAP over LAN" or EAPOL. EAPOL was originally specified for IEEE 802.3 Ethernet, IEEE 802.5 Token Ring, and FDDI (ANSI X3T9.5/X3T12 and ISO 9314) in 802.1X-2001, but was extended to suit other IEEE 802 LAN technologies such as IEEE 802.11 wireless in 802.1X-2004. The EAPOL was also modified for use with IEEE 802.1AE ("MACsec") and IEEE 802.1AR (Secure Device Identity, DevID) in 802.1X-2010IEEE 802.1X-2010, page ivIEEE 802.1X-2010, § 5 to support service identification and optional point to point encryption over the internal LAN segment. Overview 802.1X authentication involves three pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Extensible Authentication Protocol
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by . EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods. There are many methods defined by RFCs, and a number of vendor-specific methods and new proposals exist. EAP is not a wire protocol; instead it only defines the information from the interface and the formats. Each protocol that uses EAP defines a way to encapsulate by the user EAP messages within that protocol's messages. EAP is in wide use. For example, in IEEE 802.11 (WiFi) the WPA and WPA2 standards have adopted IEEE 802.1X (with various EAP types) as the canonical authentication mechanism. Methods EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. Ther ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Supplicant (computer)
In computer networking, a supplicant is an entity at one end of a point-to-point LAN segment that seeks to be authenticated by an authenticator attached to the other end of that link. The IEEE 802.1X standard uses the term "supplicant" to refer either to hardware or to software. In practice, a supplicant is a software application installed on an end-user's computer. The user invokes the supplicant and submits credentials to connect the computer to a secure network. If the authentication succeeds, the authenticator typically allows the computer to connect to the network. A supplicant, in some contexts, refers to a user or to a client in a network environment seeking to access network resources secured by the IEEE 802.1X authentication mechanism. But saying "user" or "client" over-generalizes; in reality, the interaction takes place through a personal computer, an Internet protocol (IP) phone, or similar network device. Each of these must run supplicant software that initiates o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Access Control
Network access control (NAC) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host intrusion prevention, and vulnerability assessment), user or system authentication and network security enforcement. Description Network access control is a computer networking solution that uses a set of protocols to define and implement a policy that describes how to secure access to network nodes by devices when they initially attempt to access the network. NAC might integrate the automatic remediation process (fixing non-compliant nodes before allowing access) into the network systems, allowing the network infrastructure such as routers, switches and firewalls to work together with back office servers and end user computing equipment to ensure the information system is operating securely before interoperability is allowed. A basic form of NAC is the 802.1X standard. Network access control aims to do exactly what the name implies� ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Xsupplicant
Xsupplicant is a supplicant that allows a workstation to authenticate with a RADIUS server using 802.1X and the Extensible Authentication Protocol (EAP). It can be used for computers with wired or wireless LAN connections to complete a strong authentication before joining the network and supports the dynamic assignment of WEP keys. Overview Xsupplicant up to version 1.2.8 was designed to run on Linux clients as a command line utility. Version 1.3.X and greater are designed to run on Windows XP and are currently being ported to Linux/BSD systems, and include a robust graphical user interface, and also includes Network Access Control (NAC) functionality from Trusted Computing Group's Trusted Network Connect NAC. Xsupplicant was chosen by the OpenSea Alliance, dedicated to developing, promoting, and distributing an open source 802.1X supplicant. Xsupplicant supports the following EAP types: * EAP-MD5 * LEAP * EAP-MSCHAPv2 * EAP-OTP * EAP-PEAP (v0 and v1) * EAP-SIM * EAP-TLS ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authenticator
An authenticator is a means used to confirm a user's identity, that is, to perform digital authentication. A person authenticates to a computer system or application by demonstrating that he or she has possession and control of an authenticator. In the simplest case, the authenticator is a common password. Using the terminology of the NIST Digital Identity Guidelines, the party to be authenticated is called the ''claimant'' while the party verifying the identity of the claimant is called the ''verifier''. When the claimant successfully demonstrates possession and control of one or more authenticators to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity. Classification Authenticators may be characterized in terms of secrets, factors, and physical forms. Authenticator secrets Every authenticator is associated with at least one secret that the claimant uses to demonstrate possession and control of the authenticator. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EtherType
EtherType is a two-octet field in an Ethernet frame. It is used to indicate which protocol is encapsulated in the payload of the frame and is used at the receiving end by the data link layer to determine how the payload is processed. The same field is also used to indicate the size of some Ethernet frames. EtherType is also used as the basis of 802.1Q VLAN tagging, encapsulating packets from VLANs for transmission multiplexed with other VLAN traffic over an Ethernet trunk. EtherType was first defined by the Ethernet II framing standard and later adapted for the IEEE 802.3 standard. EtherType values are assigned by the IEEE Registration Authority. Overview In modern implementations of Ethernet, the field within the Ethernet frame used to describe the EtherType can also be used to represent the size of the payload of the Ethernet Frame. Historically, depending on the type of Ethernet framing that was in use on an Ethernet segment, both interpretations were simultaneous ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Switch
A network switch (also called switching hub, bridging hub, and, by the IEEE, MAC bridge) is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device. A network switch is a multiport network bridge that uses MAC addresses to forward data at the data link layer (layer 2) of the OSI model. Some switches can also forward data at the network layer (layer 3) by additionally incorporating routing functionality. Such switches are commonly known as layer-3 switches or multilayer switches. Switches for Ethernet are the most common form of network switch. The first MAC Bridge was invented in 1983 by Mark Kempf, an engineer in the Networking Advanced Development group of Digital Equipment Corporation. The first 2 port Bridge product (LANBridge 100) was introduced by that company shortly after. The company subsequently produced multi-port switches for both Ethernet and FDDI such as GigaSwitch. Digita ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wpa Supplicant
wpa_supplicant is a free software implementation of an IEEE 802.11i supplicant for Linux, FreeBSD, NetBSD, QNX, AROS, Microsoft Windows, Solaris, OS/2 (including ArcaOS and eComStation) and Haiku. In addition to being a WPA3 and WPA2 supplicant, it also implements WPA and older wireless LAN security protocols. Features Features include: * WPA-PSK and WPA2-PSK (" WPA-Personal", pre-shared key) *WPA3 * WPA with EAP (" WPA-Enterprise", for example with RADIUS authentication server) * RSN: PMKSA caching, pre-authentication * IEEE 802.11r * IEEE 802.11w * Wi-Fi Protected Setup ( WPS) Included with the supplicant are a GUI and a command-line utility for interacting with the running supplicant. From either of these interfaces it is possible to review a list of currently visible networks, select one of them, provide any additional security information needed to authenticate with the network (for example, a passphrase, or username and password) and add it to the preference lis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Protocol
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet. IP has the task of delivering packets from the source host to the destination host solely based on the IP addresses in the packet headers. For this purpose, IP defines packet structures that encapsulate the data to be delivered. It also defines addressing methods that are used to label the datagram with source and destination information. IP was the connectionless datagram service in the original Transmission Control Program introduced by Vint Cerf and Bob Kahn in 1974, which was complemented by a connection-oriented service that became the basis for the Transmission Control Protocol (TCP). The Internet protocol suite is therefore often referred to as ''TCP/IP''. The first major version of IP, Internet Protocol Version 4 (IPv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IPod Touch
The iPod Touch (stylized as iPod touch) is a discontinued line of iOS-based mobile devices designed and marketed by Apple Inc. with a touchscreen-controlled user interface. As with other iPod models, the iPod Touch can be used as a music player and a handheld gaming device, but can also be used as a digital camera, a web browser and for messaging. It is similar in design to the iPhone, but it connects to the Internet only through Wi-Fi and does not use cellular network data, so it is not a smartphone. The iPod Touch was introduced in 2007; some 100 million iPod Touch units were sold by May 2013. The final generation of iPod Touch, released on May 28, 2019, is the seventh-generation model. iPod Touch models were sold by storage space and color; all models of the same generation typically offered identical features, performance, and operating system upgrades. An exception was the fifth generation, in which the low-end (16 GB) model was initially sold without a rear ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IOS (Apple)
iOS (formerly iPhone OS) is a mobile operating system created and developed by Apple Inc. exclusively for its hardware. It is the operating system that powers many of the company's mobile devices, including the iPhone; the term also includes the system software for iPads predating iPadOS—which was introduced in 2019—as well as on the iPod Touch devices—which were discontinued in mid-2022. It is the world's second-most widely installed mobile operating system, after Android. It is the basis for three other operating systems made by Apple: iPadOS, tvOS, and watchOS. It is proprietary software, although some parts of it are open source under the Apple Public Source License and other licenses. Unveiled in 2007 for the first-generation iPhone, iOS has since been extended to support other Apple devices such as the iPod Touch (September 2007) and the iPad (introduced: January 2010; availability: April 2010.) , Apple's App Store contains more than 2.1 million iO ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |



.jpg)