Purple cipher on:
[Wikipedia]
[Google]
[Amazon]
 In the
In the
 Japanese diplomatic communications at negotiations for the
Japanese diplomatic communications at negotiations for the

 In 1937, the Japanese completed the next generation "Type 97 Typewriter". The Ministry of Foreign Affairs machine was the "Type B Cipher Machine", codenamed Purple by United States cryptanalysts.
The chief designer of Purple was
In 1937, the Japanese completed the next generation "Type 97 Typewriter". The Ministry of Foreign Affairs machine was the "Type B Cipher Machine", codenamed Purple by United States cryptanalysts.
The chief designer of Purple was


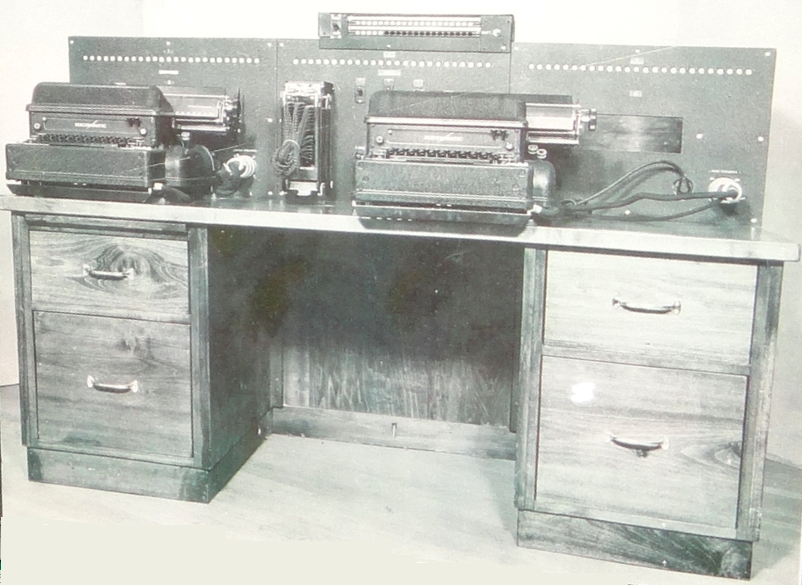
 The Type B Cipher Machine consisted of several components. As reconstructed by the US Army, there were electric typewriters at either end, similar to those used with the Type A Machine. The Type B was organized for encryption as follows:
* An input typewriter
* An input
The Type B Cipher Machine consisted of several components. As reconstructed by the US Army, there were electric typewriters at either end, similar to those used with the Type A Machine. The Type B was organized for encryption as follows:
* An input typewriter
* An input
 The SIS learned in 1938 of the forthcoming introduction of a new diplomatic cipher from decoded messages. Type B messages began to appear in February 1939.
The Type B had several weaknesses, some in its design, others in the way it was used. Frequency analysis could often make 6 of the 26 letters in the ciphertext alphabet letters stand out from the other 20 letters, which were more uniformly distributed. This suggested the Type B used a similar division of plaintext letters as used in the Type A. The weaker encryption used for the "sixes" was easier to analyze. The sixes cipher turned out to be polyalphabetic with 25 fixed permuted alphabets, each used in succession. The only difference between messages with different indicators was the starting position in the list of alphabets. The SIS team recovered the 25 permutations by 10 April 1939. The frequency analysis was complicated by the presence of
The SIS learned in 1938 of the forthcoming introduction of a new diplomatic cipher from decoded messages. Type B messages began to appear in February 1939.
The Type B had several weaknesses, some in its design, others in the way it was used. Frequency analysis could often make 6 of the 26 letters in the ciphertext alphabet letters stand out from the other 20 letters, which were more uniformly distributed. This suggested the Type B used a similar division of plaintext letters as used in the Type A. The weaker encryption used for the "sixes" was easier to analyze. The sixes cipher turned out to be polyalphabetic with 25 fixed permuted alphabets, each used in succession. The only difference between messages with different indicators was the starting position in the list of alphabets. The SIS team recovered the 25 permutations by 10 April 1939. The frequency analysis was complicated by the presence of
excerpt
of first chapter on
Red and Purple: A Story Retold
NSA analysts' modern-day attempt to duplicate solving the Red and Purple ciphers. Cryptologic Quarterly Article (NSA), Fall/Winter 1984-1985 - Vol. 3, Nos. 3-4 (last accessed: 22 August 2016).
(last accessed: 10 February 2019)
A Purple Machine simulator written in Python
A GUI Purple Machine simulator written in Java
Information and a simulator (for very old Windows). {{DEFAULTSORT:Purple (Cipher Machine) Attack on Pearl Harbor Encryption devices Japan–United States relations World War II Japanese cryptography

 In the
In the history of cryptography
Cryptography, the use of codes and ciphers to protect secrets, began thousands of years ago. Until recent decades, it has been the story of what might be called classical cryptography — that is, of methods of encryption that use pen and paper, ...
, the "System 97 Typewriter for European Characters" (九七式欧文印字機) or "Type B Cipher Machine", codenamed Purple by the United States, was an encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can de ...
machine used by the Japanese Foreign Office
The is an executive department of the Government of Japan, and is responsible for the country's foreign policy and international relations.
The ministry was established by the second term of the third article of the National Government Organi ...
from February 1939 to the end of World War II
World War II or the Second World War, often abbreviated as WWII or WW2, was a world war that lasted from 1939 to 1945. It involved the vast majority of the world's countries—including all of the great powers—forming two opposing ...
. The machine was an electromechanical device that used stepping-switches to encrypt the most sensitive diplomatic traffic. All messages were written in the 26-letter English alphabet
The alphabet for Modern English is a Latin-script alphabet consisting of 26 letters, each having an upper- and lower-case form. The word ''alphabet'' is a compound of the first two letters of the Greek alphabet, ''alpha'' and '' beta''. ...
, which was commonly used for telegraphy. Any Japanese text had to be transliterated
Transliteration is a type of conversion of a text from one script to another that involves swapping letters (thus ''trans-'' + '' liter-'') in predictable ways, such as Greek → , Cyrillic → , Greek → the digraph , Armenian → or L ...
or coded. The 26-letters were separated using a plug board into two groups, of six and twenty letters respectively. The letters in the sixes group were scrambled using a 6 × 25 substitution table, while letters in the twenties group were more thoroughly scrambled using three successive 20 × 25 substitution tables.
The cipher codenamed "Purple" replaced the Type A Red
Red is the color at the long wavelength end of the visible spectrum of light, next to orange and opposite violet. It has a dominant wavelength of approximately 625–740 nanometres. It is a primary color in the RGB color model and a secondar ...
machine previously used by the Japanese Foreign Office. The sixes and twenties division was familiar to U.S. Army Signals Intelligence Service
The Signal Intelligence Service (SIS) was the United States Army codebreaking division through World War II. It was founded in 1930 to compile codes for the Army. It was renamed the Signal Security Agency in 1943, and in September 1945, became th ...
(SIS) cryptographers from their work on the Type A cipher and it allowed them to make early progress on the sixes portion of messages. The twenties cipher proved much more difficult, but a breakthrough in September 1940 allowed the Army cryptographers to construct a machine that duplicated the behavior (was an ''analog'') of the Japanese machines, even though no one in the U.S. had any description of one.
The Japanese also used stepping-switches in systems, codenamed Coral
Corals are marine invertebrates within the class Anthozoa of the phylum Cnidaria. They typically form compact colonies of many identical individual polyps. Coral species include the important reef builders that inhabit tropical oceans and ...
and Jade, that did not divide their alphabets. American forces referred to information gained from decryptions as ''Magic
Magic or Magick most commonly refers to:
* Magic (supernatural), beliefs and actions employed to influence supernatural beings and forces
* Ceremonial magic, encompasses a wide variety of rituals of magic
* Magical thinking, the belief that unrela ...
''.
Development of Japanese cipher machines
Overview
TheImperial Japanese Navy
The Imperial Japanese Navy (IJN; Kyūjitai: Shinjitai: ' 'Navy of the Greater Japanese Empire', or ''Nippon Kaigun'', 'Japanese Navy') was the navy of the Empire of Japan from 1868 to 1945, when it was dissolved following Japan's surrend ...
did not cooperate with the Army
An army (from Old French ''armee'', itself derived from the Latin verb ''armāre'', meaning "to arm", and related to the Latin noun ''arma'', meaning "arms" or "weapons"), ground force or land force is a fighting force that fights primarily on ...
in pre-war cipher machine development, and that lack of cooperation continued into World War II. The Navy believed the Purple machine was sufficiently difficult to break that it did not attempt to revise it to improve security. This seems to have been on the advice of a mathematician, Teiji Takagi
Teiji Takagi (高木 貞治 ''Takagi Teiji'', April 21, 1875 – February 28, 1960) was a Japanese mathematician, best known for proving the Takagi existence theorem in class field theory. The Blancmange curve, the graph of a nowhere-differentiabl ...
, who lacked a background in cryptanalysis. The Ministry of Foreign Affairs was supplied Red and Purple by the Navy. No one in Japanese authority noticed the weak points in both machines.
Just before the end of the war, the Army warned the Navy of a weak point of Purple, but the Navy failed to act on this advice.
The Army developed their own cipher machines on the same principle as Enigma
Enigma may refer to:
*Riddle, someone or something that is mysterious or puzzling
Biology
*ENIGMA, a class of gene in the LIM domain
Computing and technology
* Enigma (company), a New York-based data-technology startup
* Enigma machine, a family ...
-- ''92-shiki injiki'', ''97-shiki injiki'' and ''1-shiki 1-go injiki --'' from 1932 to 1941. The Army judged that these machines had lower security than the Navy's Purple design, so the Army's two cipher machines were less used.
Prototype of Red
Washington Naval Treaty
The Washington Naval Treaty, also known as the Five-Power Treaty, was a treaty signed during 1922 among the major Allies of World War I, which agreed to prevent an arms race by limiting naval construction. It was negotiated at the Washington Nav ...
were broken by the American Black Chamber
The Black Chamber (1919–1929), also known as the Cipher Bureau, was the United States' first peacetime cryptanalytic organization, and a forerunner of the National Security Agency. The only prior codes and cypher organizations maintained by th ...
in 1922, and when this became publicly known, there was considerable pressure to improve their security. In any case, the Japanese Navy had planned to develop their first cipher machine for the following London Naval Treaty. Japanese Navy Captain Risaburo Ito, of Section 10 (cipher & code) of the Japanese Navy General Staff Office, supervised the work.
The development of the machine was the responsibility of the Japanese Navy Institute of Technology, Electric Research Department, Section 6. In 1928, the chief designer Kazuo Tanabe
Kazuo (カズオ, かずお) is a masculine Japanese given name.
Possible spellings
It has several written forms, and the meaning depends on the characters used (usually kanji, but sometimes hiragana). Common forms include:
* 一雄: first son, ...
and Navy Commander Genichiro Kakimoto developed a prototype of Red, "Roman-typewriter cipher machine".
The prototype used the same principle as the Kryha
In the history of cryptography, the Kryha machine was a device for encryption and decryption, appearing in the early 1920s and used until the 1950s. The machine was the invention of Alexander von Kryha (born 31.10.1891 in Charkow, Russian Empir ...
cipher machine, having a plug-board
A plugboard or control panel (the term used depends on the application area) is an array of jacks or sockets (often called hubs) into which patch cords can be inserted to complete an electrical circuit. Control panels are sometimes used to di ...
, and was used by the Japanese Navy and Ministry of Foreign Affairs at negotiations for the London Naval Treaty in 1930.
Red
The prototype machine was finally completed as "Type 91 Typewriter" in 1931. The year 1931 was year 2591 in the Japanese Imperial calendar. Thus it was prefixed "91-shiki" from the year it was developed. The ''91-shiki injiki'' Roman-letter model was also used by the Ministry of Foreign Affairs as "Type A Cipher Machine", codenamed "Red" by United States cryptanalysts. The Red machine was unreliable unless the contacts in its half-rotor switch were cleaned every day. It enciphered vowels (AEIOUY) and consonants separately, perhaps to reduce telegram costs, and this was a significant weak point. The Navy also used the ''91-shiki injiki''Kana
The term may refer to a number of syllabaries used to write Japanese phonological units, morae. Such syllabaries include (1) the original kana, or , which were Chinese characters (kanji) used phonetically to transcribe Japanese, the most p ...
-letter model at its bases and on its vessels.
Purple

 In 1937, the Japanese completed the next generation "Type 97 Typewriter". The Ministry of Foreign Affairs machine was the "Type B Cipher Machine", codenamed Purple by United States cryptanalysts.
The chief designer of Purple was
In 1937, the Japanese completed the next generation "Type 97 Typewriter". The Ministry of Foreign Affairs machine was the "Type B Cipher Machine", codenamed Purple by United States cryptanalysts.
The chief designer of Purple was Kazuo Tanabe
Kazuo (カズオ, かずお) is a masculine Japanese given name.
Possible spellings
It has several written forms, and the meaning depends on the characters used (usually kanji, but sometimes hiragana). Common forms include:
* 一雄: first son, ...
. His engineers were Masaji Yamamoto and Eikichi Suzuki. Eikichi Suzuki suggested the use of a stepping switch
In electrical control engineering, a stepping switch or stepping relay, also known as a uniselector, is an electromechanical device that switches an input signal path to one of several possible output paths, directed by a train of electrical puls ...
instead of the more troublesome half-rotor switch.
Clearly, the Purple machine was more secure than Red, but the Navy did not recognize that Red had already been broken. The Purple machine inherited a weakness from the Red machine that six letters of the alphabet were encrypted separately. It differed from Red in that the group of letters was changed and announced every nine days, whereas in Red they were permanently fixed as the Latin vowels 'a', 'e', 'i', 'o', 'u' and 'y'. Thus US Army SIS was able to break the cipher used for the six letters before it was able to break the one used for the 20 others.
Design


 The Type B Cipher Machine consisted of several components. As reconstructed by the US Army, there were electric typewriters at either end, similar to those used with the Type A Machine. The Type B was organized for encryption as follows:
* An input typewriter
* An input
The Type B Cipher Machine consisted of several components. As reconstructed by the US Army, there were electric typewriters at either end, similar to those used with the Type A Machine. The Type B was organized for encryption as follows:
* An input typewriter
* An input plugboard
A plugboard or control panel (the term used depends on the application area) is an array of jacks or sockets (often called hubs) into which patch cords can be inserted to complete an electrical circuit. Control panels are sometimes used to di ...
that permutes the letters from the typewriter keyboard and separates them into a group of 6 letters and a group of 20 letters
* A stepping switch
In electrical control engineering, a stepping switch or stepping relay, also known as a uniselector, is an electromechanical device that switches an input signal path to one of several possible output paths, directed by a train of electrical puls ...
with 6 layers wired to select one out of 25 permutations of the letters in the sixes group
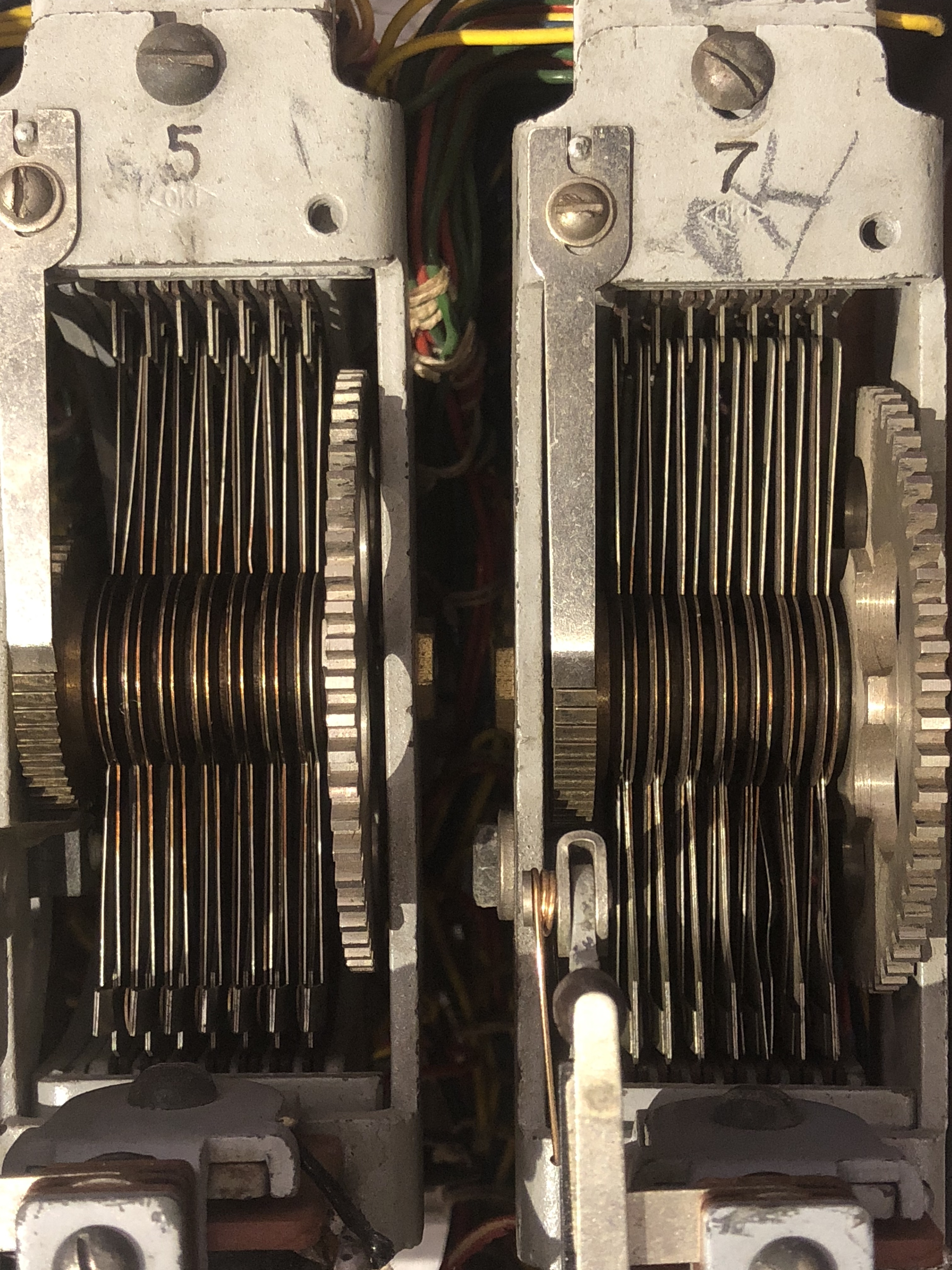
* Three stages of stepping switches (I, II, and III), connected in series. Each stage is effectively a 20 layer switch with 25 outputs on each layer. Each stage selects one out of 25 permutations of the letters in the twenties group. The Japanese used three 7-layer stepping switches geared together to build each stage (see photos). The U.S. SIS used four 6-layer switches per stage in their first analog machine.
* An output plug board that reverses the input permutation and sends the letters to the output typewriter for printing
* The output typewriter
For decryption, the data flow is reversed. The keyboard on the second typewriter becomes the input and the twenties letters pass through the stepping switch stages in the opposite order.
Stepping switches
Astepping switch
In electrical control engineering, a stepping switch or stepping relay, also known as a uniselector, is an electromechanical device that switches an input signal path to one of several possible output paths, directed by a train of electrical puls ...
is a multi-layer mechanical device that was commonly used at the time in telephone switching systems. Each layer has a set of electrical connects, 25 in the Type B, arranged in a semicircular arc. These do not move and are called the stator. A wiper arm on a rotor at the focus of the semicircle connects with one stator contact at a time. The rotors on each layer are attached to a single shaft that advances from one stator contact to the next whenever an electromagnet connected to a ratchet is pulsed. There are actually two wiper arms on each level, connected together, so that when one wiper advance past the last contact in the semicircle, the other engages the first contact. This allows the rotor connections to keeps cycling through all 25 stator contacts as the electromagnet is pulsed.
To encrypt the twenties letters, a 20-layer stepping switch was needed in each of the three stages. Both the Japanese version and the early American analog constructed each stage from several smaller stepping switches of the type used in telephone central offices. The American analog used four 6-level switches to create one 20-layer switch. The four switches in each stage were wired to step synchronously. The fragment of a Type 97 Japanese machine on display at the National Cryptologic Museum, the largest piece known in existence, has three 7-layer stepping switches (see photo). The U.S. Army developed an improved analog in 1944 that has all the layers needed for each stage on a single shaft. An additional layer was used in the improved analog to automatically set each switch bank to the initial position specified in the key.
However implemented, the 20-layer stepping switch in each stage had 20 rotor connections and 500 stator connections, one wiper and 25 stator contacts on each layer. Each stage must have exactly 20 connections on each end to connect with the adjacent stage or plugboard. On the rotor side, that is not a problem as there are 20 rotors. On the stator end of a stage, every column of stator contacts corresponding to the same rotor position on each of the 20 layers is connected to the 20 output wires (''leads'' in the diagram) in a scrambled order, creating a permutation of the 20 inputs. This is done differently for each of the rotor positions. Thus each stator output wire has 25 connections, one from each rotor position, though from different levels. The connections needed to do this created a "rats nest" of wires in the early U.S. analog. The improved analog organized the wiring more neatly with three matrices of soldering terminals visible above each stepping switch in the photograph.
Stepping order
The stages were bi-directional. Signals went through each stage in one direction for encryption and in the other direction for decryption. Unlike the system in the German Enigma machine, the order of the stages was fixed and there was no reflector. However the stepping arrangement could be changed. The sixes switches stepped one position for each character encrypted or decrypted. The motions of the switches in the twenties stages were more complex. The three stages were assigned to step fast, medium or slow. There were six possible ways to make this assignment and the choice was determined by a number included at the beginning of each message called the message indicator. The U.S. improved analog has a six-position switch for making this assignment, see photo. The message indicator also specified the initial positions of the twenties switches. The indicator was different for each message or part of a message, when multi-part messages were sent. The final part of the key, the alphabet plugboard arrangement, was changed daily. The twenties switch stepping was controlled in part by the sixes switch. Exactly one of the three switches stepped for each character. The fast switch stepped for each character except when the sixes switch was in its 25th position. Then the medium switch stepped, unless it too was in its 25th position, in which case the slow switch stepped.Weaknesses and cryptanalysis
romanized Japanese
The romanization of Japanese is the use of Latin script to write the Japanese language. This method of writing is sometimes referred to in Japanese as .
Japanese is normally written in a combination of logographic characters borrowed from Ch ...
text and the introduction in early May of a Japanese version of the Phillips Code
The Phillips Code is a brevity code (shorthand) created in 1879 by Walter P. Phillips (then of the Associated Press) for the rapid transmission of press reports by telegraph. It defined hundreds of abbreviations and initialisms for commonly use ...
.
Knowing the plaintext of 6 out of 26 letters scattered throughout the message sometimes enabled parts of the rest of the message to be guessed, especially when the writing was highly stylized. Some diplomatic messages included the text of letters from the U.S. government to the Japanese government. The English text of such messages could usually be obtained. Some diplomatic stations did not have the Type B, especially early in its introduction, and sometimes the same message was sent in Type B and in the Type A Red cipher, which the SIS had broken. All these provided cribs for attacking the twenties cipher.
William F. Friedman
William Frederick Friedman (September 24, 1891 – November 12, 1969) was a US Army cryptographer who ran the research division of the Army's Signal Intelligence Service (SIS) in the 1930s, and parts of its follow-on services into the 1950s. ...
was assigned to lead the group of cryptographers attacking the B system in August 1939. Even with the cribs, progress was difficult. The permutations used in the twenties cipher were "brilliantly" chosen, according to Friedman, and it became clear that periodicities would be unlikely to be discovered by waiting for enough traffic encrypted on a single indicator, since the plugboard alphabets changed daily. The cryptographers developed a way to transform messages sent on different days with the same indicator into homologous messages that would appear to have been sent on the same day. This provided enough traffic based on the identical settings (6 messages with indicator 59173) to have a chance of finding some periodicity that would reveal the inner workings of the twenties cipher.
On 20 September 1940 at about 2 pm Genevieve Grotjan, carrying a set of work sheets walked up to a group of men engrossed in conversation and politely attempted to get Frank Rowlett
Frank Byron Rowlett (May 2, 1908 – June 29, 1998) was an American cryptologist.
Life and career
Rowlett was born in Rose Hill, Lee County, Virginia and attended Emory & Henry College in Emory, Virginia. In 1929 he received a bachelor's d ...
's attention. She had found evidence of cycles in the twenties cipher. Celebration ensued at this first break in the 20s cipher and it soon enabled a replica machine to be built. A pair of other messages using indicator 59173 were decrypted by 27 September, coincidentally the date that the Tripartite Agreement between Nazi Germany, Fascist Italy, and Imperial Japan was announced. There was still a lot of work to do to recover the meaning of the other 119 possible indicators. As of October 1940, one third of the indicator settings had been recovered. From time to time the Japanese instituted new operating procedures to strengthen the Type B system, but these were often described in messages to diplomatic outputs in the older system, giving the Americans warning.
Reconstruction of the Purple machine was based on ideas of Larry Clark. Advances into the understanding of Purple keying procedures were made by Lt Francis A. Raven, USN. After the initial break, Raven discovered that the Japanese had divided the month into three 10-days periods, and, within each period, they used the keys of the first day, with small, predictable changes.
The Japanese believed Type B to be unbreakable throughout the war, and even for some time after the war, even though they had been informed otherwise by the Germans. In April 1941, Hans Thomsen, a diplomat at the German embassy in Washington, D.C., sent a message to Joachim von Ribbentrop, the German foreign minister, informing him that "an absolutely reliable source" had told Thomsen that the Americans had broken the Japanese diplomatic cipher (that is, Purple). That source apparently was Konstantin Umansky
Konstantin Aleksandrovich Umansky (russian: Kонстантин Aлександрович Уманский; 14 May 1902 – 25 January 1945) was a Soviet diplomat, editor, journalist and artist.
Biography and career
Umansky, who was Jewish, w ...
, the Soviet ambassador to the US, who had deduced the leak based upon communications from U.S. Undersecretary of State Sumner Welles. The message was duly forwarded to the Japanese; but use of the code continued. Text froexcerpt
of first chapter on
WNYC
WNYC is the trademark and a set of call letters shared by WNYC (AM) and WNYC-FM, a pair of nonprofit, noncommercial, public radio stations located in New York City. WNYC is owned by New York Public Radio (NYPR), a nonprofit organization that ...
website
American analogs
The SIS built its first machine that could decrypt Purple messages in late 1940. A second Purple analog was built by the SIS for the US Navy. A third was sent to England in January 1941 onHMS King George V
Two ships of the Royal Navy have been named HMS ''King George V'', after George V, King of the United Kingdom, whilst another was planned:
* HMS ''King George V'' was to have been an . She was renamed in 1910, prior to her launch in 1911. Captain ...
, which had brought Ambassador Halifax to the U.S. That Purple analog was accompanied by a team of four American cryptologists, two Army, two Navy, who received information on British successes against German ciphers in exchange. This machine was subsequently sent to Singapore, and after Japanese moves south through Malaya, on to India. A fourth Purple analog was sent to the Philippines and a fifth was kept by the SIS. A sixth, originally intended for Hawaii, was sent to England for use there. The Purple intercepts proved important in the European theater due to the detailed reports on German plans sent in that cipher by the Japanese ambassador in Berlin.
Fragmentary recovery of Japanese machines
The United States obtained portions of a Purple machine from the Japanese Embassy in Germany following Germany's defeat in 1945 (see image above) and discovered that the Japanese had used a stepping switch almost identical in its construction to the oneLeo Rosen
Leo Rosen was a U.S. cryptanalyst who worked with Frank Rowlett at Signals Intelligence Service (S.I.S.) before the start of World War II on Japanese ciphers. Rowlett found a method to read the messages enciphered on the Japanese PURPLE machine ...
of SIS had chosen when building a duplicate (or Purple analog machine) in Washington in 1939 and 1940. The stepping switch was a uniselector
In electrical control engineering, a stepping switch or stepping relay, also known as a uniselector, is an electromechanical device that switches an input signal path to one of several possible output paths, directed by a train of electrical pulse ...
; a standard component used in large quantities in automatic telephone exchanges in countries like America, Britain, Canada, Germany and Japan, with extensive dial-telephone systems. The U.S. used four 6-level switches in each stage of its Purple analogs, the Japanese used three 7-level switches. Both represented the 20s cipher identically. Note however that these were not two-motion or Strowger switch
The Strowger switch is the first commercially successful electromechanical stepping switch telephone exchange system. It was developed by the Strowger Automatic Telephone Exchange Company founded in 1891 by Almon Brown Strowger. Because of it ...
es as sometimes claimed: ''twenty-five Strolger-type (sic) stepper switches'' ...
Apparently, all other Purple machines at Japanese embassies and consulates around the world (e.g. in Axis countries, Washington, London, Moscow, and in neutral countries) and in Japan itself, were destroyed and ground into small particles by the Japanese. American occupation troops in Japan in 1945−52 searched for any remaining units. A complete Jade cipher machine, built on similar principles but without the sixes and twenties separation, was captured and is on display at NSA's National Cryptologic Museum
The National Cryptologic Museum (NCM) is an American museum of cryptologic history that is affiliated with the National Security Agency (NSA). The first public museum in the U.S. Intelligence Community, NCM is located in the former Colony Sev ...
.
Impact of Allied decryption
The Purple machine itself was first used by Japan in June 1938, but American and British cryptanalysts had broken some of its messages well before theattack on Pearl Harbor
The attack on Pearl HarborAlso known as the Battle of Pearl Harbor was a surprise military strike by the Imperial Japanese Navy Air Service upon the United States against the naval base at Pearl Harbor in Honolulu, Territory of Hawaii ...
. US cryptanalysts decrypted and translated Japan's 14-part message to its Washington embassy to break off negotiations with the United States at 1 p.m., Washington time, on 7 December 1941, before the Japanese Embassy in Washington had done so. Decryption and typing difficulties at the embassy, coupled with ignorance of the importance of it being on time, were major reasons for the " Nomura Note" to be delivered late.
During World War II, the Japanese ambassador to Nazi Germany
Nazi Germany (lit. "National Socialist State"), ' (lit. "Nazi State") for short; also ' (lit. "National Socialist Germany") (officially known as the German Reich from 1933 until 1943, and the Greater German Reich from 1943 to 1945) was ...
, General Hiroshi Oshima
is a common masculine Japanese given name. It can also be transliterated as Hirosi.
Possible writings
Hiroshi can be written using different kanji characters and can mean:
*浩, "meaning"
*汎
*弘,
*宏,
*寛,
*洋,
*博,
*博一,
*博司,
...
, was well-informed on German military affairs. His reports went to Tokyo in Purple-enciphered radio messages. One had a comment that Hitler told him on 3 June 1941 that "in every probability war with Russia cannot be avoided." In July and August 1942, he toured the Eastern Front, and in 1944, he toured the Atlantic Wall fortifications against invasion along the coasts of France and Belgium. On 4 September, Hitler told him that Germany would strike in the West, probably in November.
Since those messages were being read by the Allies, they provided valuable intelligence about German military preparations against the forthcoming invasion of Western Europe. He was described by General George Marshall
George Catlett Marshall Jr. (December 31, 1880 – October 16, 1959) was an American army officer and statesman. He rose through the United States Army to become Chief of Staff of the United States Army, Chief of Staff of the US Army under Pre ...
as "our main basis of information regarding Hitler's intentions in Europe."
The decrypted Purple traffic and Japanese messages generally were the subject of acrimonious hearings in Congress after World War II in connection with an attempt to decide who, if anyone, had allowed the attack at Pearl Harbor to happen and so should be blamed. It was during those hearings that the Japanese for the first time learned that the Purple cipher machine had indeed been broken. (See the Pearl Harbor advance-knowledge conspiracy theory
Various conspiracy theories allege that U.S. government officials had advance knowledge of Japan's December 7, 1941, attack on Pearl Harbor. Ever since the Japanese attack, there has been debate as to why and how the United States had been caugh ...
article for additional detail on the controversy and the investigations.)
The Soviets also succeeded in breaking the Purple system in late 1941, and together with reports from Richard Sorge
Richard Sorge (russian: Рихард Густавович Зорге, Rikhard Gustavovich Zorge; 4 October 1895 – 7 November 1944) was a German-Azerbaijani journalist and Soviet military intelligence officer who was active before and during Wo ...
, learned that Japan was not going to attack the Soviet Union
The Soviet Union,. officially the Union of Soviet Socialist Republics. (USSR),. was a List of former transcontinental countries#Since 1700, transcontinental country that spanned much of Eurasia from 1922 to 1991. A flagship communist state, ...
. Instead, its targets were southward, toward Southeast Asia and American and British interests there. That allowed Stalin to move considerable forces from the Far East to Moscow in time to help stop the German push to Moscow in December.
References
Further reading
*''Big Machines'', by Stephen J. Kelley (Aegean Park Press, Walnut Creek, 2001, ) – Contains a lengthy, technically detailed description of the history of the creation of the PURPLE machine, along with its breaking by the US SIS, and an analysis of its cryptographic security and flaws * - Appendix C: Cryptanalysis of the Purple Machine * Clark, Ronald W. "The Man Who Broke Purple: the Life of Colonel William F. Friedman, Who Deciphered the Japanese Code in World War II", September 1977, Little Brown & Co, . * *''Combined Fleet Decoded'' by J. Prados *''The Story of Magic: Memoirs of an American Cryptologic Pioneer'', by Frank B. Rowlett (Aegean Park Press, Laguna Hills, 1998, ) – A first-hand memoir from a lead team member of the team which 'broke' both Red and Purple, it contains detailed descriptions of both 'breaks' * * *External links
* The Japanese Wikipedia article on the Type B machine has much technical information including the substitution tables, detailed stepping algorithm, punctuation codes and a sample decryption. It also has reactions from Japanese sources to the American decryption. Entering the website link https://ja.wikipedia.org/wiki/パープル暗号 into Google Translate and clicking "Translate this page" will provide a serviceable English translation.Red and Purple: A Story Retold
NSA analysts' modern-day attempt to duplicate solving the Red and Purple ciphers. Cryptologic Quarterly Article (NSA), Fall/Winter 1984-1985 - Vol. 3, Nos. 3-4 (last accessed: 22 August 2016).
(last accessed: 10 February 2019)
A Purple Machine simulator written in Python
A GUI Purple Machine simulator written in Java
Information and a simulator (for very old Windows). {{DEFAULTSORT:Purple (Cipher Machine) Attack on Pearl Harbor Encryption devices Japan–United States relations World War II Japanese cryptography