Intelligence analysis management on:
[Wikipedia]
[Google]
[Amazon]
Intelligence Analysis Management is the process of managing and organizing the analytical processing of raw intelligence information. The terms "analysis", "production", and "processing" denote the organization and evaluation of raw information used in a phase informally called " connecting the dots", thus creating an " intelligence mosaic". The information may result in multiple analytic products, each with different security classifications, time scales, and levels of detail. Intelligence analysis goes back to the beginning of history. Sherman Kent is often considered the father of modern intelligence analysis. His writings include a 1947 book, ''Strategic Intelligence for American World Policy''.
During his career in the Office of Strategic Services and the
 Some intelligence disciplines, especially technical ones, will analyze the same raw data in different ways for complementary purposes. For example, a signals intelligence collection platform will record all the electromagnetic signals it received from an antenna pointed to a particular target at a particular time. Assuming the target was radar, the
Some intelligence disciplines, especially technical ones, will analyze the same raw data in different ways for complementary purposes. For example, a signals intelligence collection platform will record all the electromagnetic signals it received from an antenna pointed to a particular target at a particular time. Assuming the target was radar, the
Central Intelligence Agency
The Central Intelligence Agency (CIA ), known informally as the Agency and historically as the Company, is a civilian foreign intelligence service of the federal government of the United States, officially tasked with gathering, processing, ...
(CIA), Kent defined many of the parameters of modern analysis and its use. Kent disagreed with the philosophy that analysts never recommend policy, but only advise policymakers. He considered it a partnership in which the analyst did not push a personal point of view.
Recent scholarship drawing upon theories of the sociology of knowledge has criticized Kent's work for being over-positivist and for failing to recognize the role the identity and culture of the analytic unit play in formulating, accepting, and rejecting the hypotheses used to collect and analyze intelligence.
Preprocessing
 Some intelligence disciplines, especially technical ones, will analyze the same raw data in different ways for complementary purposes. For example, a signals intelligence collection platform will record all the electromagnetic signals it received from an antenna pointed to a particular target at a particular time. Assuming the target was radar, the
Some intelligence disciplines, especially technical ones, will analyze the same raw data in different ways for complementary purposes. For example, a signals intelligence collection platform will record all the electromagnetic signals it received from an antenna pointed to a particular target at a particular time. Assuming the target was radar, the ELINT
Signals intelligence (SIGINT) is intelligence-gathering by interception of '' signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly used in communication ...
analysts would be focused on the purpose and coverage of the radar. The MASINT analysts, however, would be looking for patterns not in the intentional signals of the radar or side frequencies that were inadvertently generated. In the same manner, if the target was a voice communication, the COMINT
Signals intelligence (SIGINT) is intelligence-gathering by interception of '' signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly used in communication ...
specialists would concentrate on the content of the message, but acoustic MASINT technicians might "voice print" the spoken words to validate that it was really from the supposed source. While Morse code telegraphy is largely obsolete, each operator has a distinct rhythm known as a "fist". Experienced telegraph intercept operators can recognize radio deception when the fist failed to match the purported operator identity.
A very basic preprocessing step is translating the collected material into the native language of the analysts unless, as is desirable, the analysts are fluent in the language of the information.
Basic intelligence and reference library services
Librarians at the CIA receive large numbers of documents, not counting special source materials, cables, newspapers, press summaries, periodicals, books, and maps. Since these reports come from scores of different major sources, the daily volume fluctuates and shows a lack of uniformity in format, in reproduction media, in length and quality of presentation, and in security classification. As they come in they must be read with an eye to identifying material of interest to some 150 different customer offices or individuals. The reference office manages several registers (in effect special libraries) for special source materials, biographic data on scientists and technicians, films and ground photographs, and data on industrial installations. Demands made on the document collection stem from three types of requests: :*Requests for a specific document to which the analyst has a reference or citation; :*Requests for a specific bit of information in answer to a specific question; :* Requests for all information relevant to a subject which may or may not be well defined. The last, which requires literature search, is the most difficult. Where central reference services have been organized independent of research offices, it soon becomes evident that the functional line of demarcation between them and the research units is not clear. This becomes important when it results in duplication of effort or, in non-use of reference materials by the researcher laboring under the misimpression that they have all relevant documents in their possession. Increasing use of collaborative technologies can help this misimpression. Then there is the question of whether a reference service should be active or passive, dynamic or static? A passive approach to reference service would mean that reference personnel would merely keep the stacks of the library in order, leaving it to research analysts to exploit the collection. Under the active approach, on the other hand, reference analysts would discuss the researcher's problem with them and then proceed, as appropriate, to prepare a bibliography, gather apparently pertinent documents, screen them, check with colleagues in other departments for supplementary materials, make abstracts, have retention copies made of popular items in short supply, initiate a requirement for supplementary field service, or prepare reference aids. Once a separate facility has been set up to provide reference services it is not long before it publishes. This comes about for several reasons, the least controversial of which is that a customer has made a specific request. This type of publication is called a research or reference aid. Some are quite specific; others are more general, being prepared in response to a need generally expressed. A number of different customers may, for example, make known that it would be very helpful to have a periodic compilation of all finished intelligence reports and estimates for ready reference. Reference officers have the responsibility to make known the availability of services and information the existence of which may be unknown to the analyst; and, given a task, to make the preliminary selection of materials to meet the particular need of a particular user. To the analyst must be left the determination of its significance for the present; to the consumer its significance for the future; and to the policy-maker the indicated course of action. Intelligence personnel, as well as end consumers, need their equivalent of reference books and encyclopedias. The US term for this is "basic intelligence", while the WEU calls it "documentary intelligence". Much of this information may itself be unclassified, but their indexing and cross-referencing, especially if that cross-referencing includes classified sources, the index itself, and bibliographies drawn from it, may be properly classified. One means of organizing basic intelligence is with the acronym BEST MAPS : :* B--biographic intelligence :* E--economic intelligence :* S--sociological intelligence :* T--transportation and telecommunications intelligence :* M--military geographical intelligence :* A--armed forces intelligence :* P--political intelligence :* S--scientific and technical intelligence This is not a complete list, as the basic intelligence library also includes: :*Maps, including "base maps" over which overlays can be placed :*Biographical data, extensively cross-referenced; the UK term is "registry" :*Graphics data :*Targeting data, which may be considered basic data only by military units As a practical matter, these may be collected into: :*Country handbooks, at various levels of classification (e.g., the unclassifiedWorld Factbook
''The World Factbook'', also known as the ''CIA World Factbook'', is a reference resource produced by the Central Intelligence Agency (CIA) with almanac-style information about the countries of the world. The official print version is available ...
)
:*Topical handbooks (e.g., international terrorist groups), again at varying level of classifications.
With modern technology, these collections may be web documents rather than hard copies.
Country handbooks
Unclassified examples of a country reference, in much shorter form than the internal handbooks, is the '' CIA World Factbook'', the "Countries and Regions" data sheets from the UK Foreign and Commonwealth Office , and the US Department of State ''Background Notes''. Closer to the internal reference books of the intelligence communities are the ''Foreign Area Handbooks'', originally prepared under contract to the US Army by American University, and later by theFederal Research Division
The Federal Research Division (FRD) is the research and analysis unit of the United States Library of Congress.
The Federal Research Division provides directed research and analysis on domestic and international subjects to agencies of the Unit ...
of the Library of Congress
The Library of Congress (LOC) is the research library that officially serves the United States Congress and is the ''de facto'' national library of the United States. It is the oldest federal cultural institution in the country. The library ...
. The Country Studies-Area Handbook Program was "sponsored by the U.S. Department of the Army. Because the original intent of the series' sponsor was to focus primarily on lesser-known areas of the world or regions in which US forces might be deployed, the series is not all-inclusive." At the time of original publication, there was a main unclassified handbook and a secret supplement, the latter dealing principally with biographical information. Area Handbooks had less restrictive distribution than the CIA ''National Intelligence Summaries''.
Biographical references
Comprehensive indexing is the real value of a biographical registry. The names themselves are a challenge, with phonetic variations and aliases. Soundex is one technique for indexing names such that phonetic equivalents, with variations in transliterations into the local language, can be retrieved. While there is no truly general solution, there has been considerable work in both intransliteration
Transliteration is a type of conversion of a text from one script to another that involves swapping letters (thus ''trans-'' + '' liter-'') in predictable ways, such as Greek → , Cyrillic → , Greek → the digraph , Armenian → or L ...
nonroman character sets. Soundex and related systems help search biographical databases by phonetics, but transliterated character sets allow people not fully fluent in the written language to search for names.
Relationships among the people in the biographical index are essential and constantly updated. One term of art used for relationships indices are "wiring diagrams".
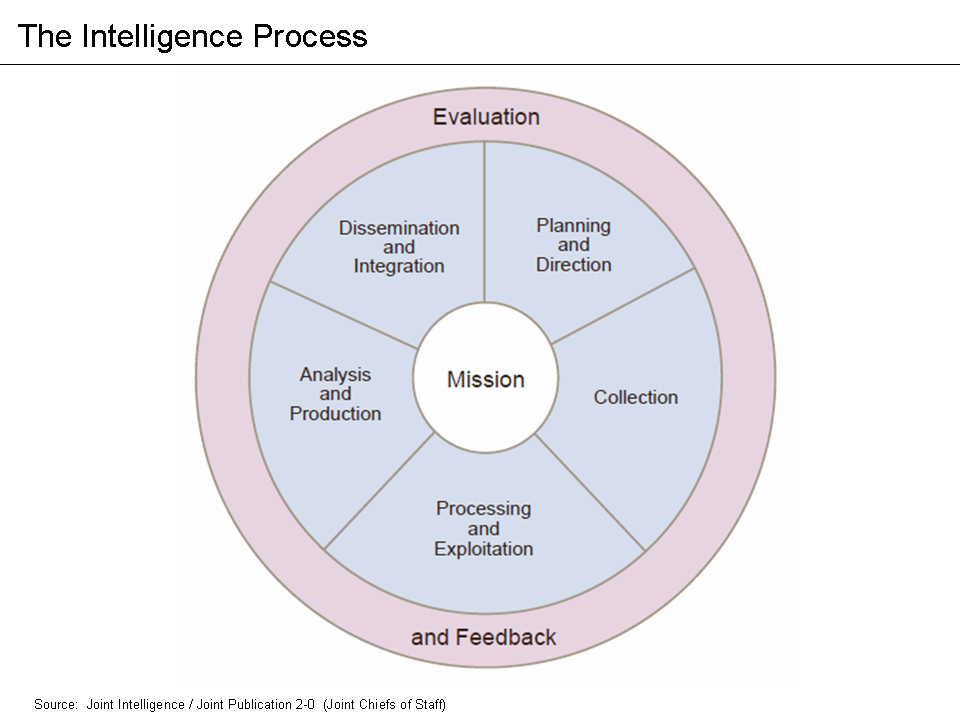
The cycle of organizational activity for intelligence purposes extends from the collection of selected information to its direct use in reports prepared for policy makers. Between these beginning and end activities there lie a number of functions which can be grouped under the term information processing. These functions include the identification, recording, organization, retrieval, conversion into more useful forms, synthesis and dissemination of the intellectual content of the information collected. The ever-mounting volume of information produced and promptly wanted and the high cost of performing these manifold operations are forcing a critical review of current practices in the processing field.
Geophysical basic intelligence
Maps are obvious products, but in infinite variety, including simple outlines onto which specific information can be overlaid, and divisions by political jurisdiction, ethnicities and languages, terrain, etc. The line between maps and actual imagery grows increasingly blurry. Online resources such as Google Earth are increasingly useful for other than the most detailed technical analysis. One challenge remains the indexing of maps ingeographical information systems
A geographic information system (GIS) is a type of database containing geographic data (that is, descriptions of phenomena for which location is relevant), combined with software tools for managing, analyzing, and visualizing those data. In a b ...
, since multiple projections and coordinate systems are used both in maps and in imagery.
Order of battle intelligence
Principally a military term, order of battle refers to the composition of an adversary's organization, including units, key personnel, equipment, and strength. In general, this is a form of basic intelligence, but is so important, and often so rapidly changing, that it may be assigned to a specific branch of an intelligence unit. The term is also used for the organizational details of other aspects of opposition. For example, electronic order of battle is an inventory of the equipment, location, and operating signal characteristics of enemy transmitters, antennas, and other electronic equipment.Current intelligence
A spectrum of activities falls under the term "current intelligence". At a minimum, a current intelligence facility receives raw or minimally processed reports, integrates them with information it has, and, depending on its mission, may support: :*Tactical warning (especially military facilities that combine operations and intelligence), such as theNorth American Air Defense Command
North American Aerospace Defense Command (NORAD ), known until March 1981 as the North American Air Defense Command, is a combined organization of the United States and Canada that provides aerospace warning, air sovereignty, and protection ...
(NORAD) command post
:*Mobile military and policymaker command centers, such as naval Combat Information Center
A combat information center (CIC) or action information centre (AIC) is a room in a warship or AWACS aircraft that functions as a tactical center and provides processed information for command and control of the near battlespace or area of op ...
s or Airborne Warning and Control Systems (AWACS)
:*Strategic warning and coordination (e.g., US Department of State Operations Center)
:*Situational awareness of continuing items of interest, for operational use (e.g., World War II UK Submarine Tracking Room)
:*Situational awareness of continuing items of interest, for policymaker information and more systematic presentations (e.g., US White House Situation Room
The Situation Room, officially known as the John F. Kennedy Conference Room, is a conference room and intelligence management center in the basement of the West Wing of the White House. It is run by the National Security Council staff for the ...
).
One function of watch centers, at least those in agencies and commands with collection and surveillance capabilities, is to monitor the availability of sensors, scheduled patrols, etc. Part of the tactical surprise at the Battle of Pearl Harbor was that patrol aircraft were supposed to be aloft and the early radar station operating, but no watch center verified this—senior officers assumed it was being done.
Intermediate in timeliness between tactical warning and situation awareness are 24/7/365 facilities that stay active on current matters. Perhaps the first modern watch center was the British submarine tracking center under Rodger Winn. This was the predecessor of the modern "all-source" center, where tactical reports, cryptanalysis, direction finding, and other functions came together to locate German submarines threatening Allied convoys.
Modern current intelligence facilities often use teleconferencing or videoconferencing to share information, such as the NOIWON ( National Operational Intelligence Watch Officer's Network) that links the (US) National Military Command Center, National Military Joint Intelligence Center, State Department Operations Center, CIA Operations Center, State Department Bureau of Intelligence and Research, NSA Operations Center and White House Situation Room. Other units may join conferences when appropriate, such as the Federal Bureau of Investigation
The Federal Bureau of Investigation (FBI) is the domestic intelligence and security service of the United States and its principal federal law enforcement agency. Operating under the jurisdiction of the United States Department of Justice, ...
(FBI) Strategic Information and Operations Center (SIOC).
Other countries have similar networks, or sometimes a physical installation to which all affected agencies send representatives, such as the UK Cabinet Office Briefing Rooms "COBRA".
When a crisis is not necessarily of international significance, a subset may be all that is needed, such as the SIOC for multiple simultaneous prison riots. In the case of an aircraft hijacking without terrorist implications, the Federal Aviation Administration
The Federal Aviation Administration (FAA) is the largest transportation agency of the U.S. government and regulates all aspects of civil aviation in the country as well as over surrounding international waters. Its powers include air traffic ...
operations center may work with the SIOC, or with specific service components such as Coast Guard headquarters. The Coast Guard, other Department of Homeland Security offices such as Federal Emergency Management Agency
The Federal Emergency Management Agency (FEMA) is an agency of the United States Department of Homeland Security (DHS), initially created under President Jimmy Carter by Presidential Reorganization Plan No. 3 of 1978 and implemented by two Ex ...
, and technical specialists such as the United States Environmental Protection Agency
The Environmental Protection Agency (EPA) is an independent executive agency of the United States federal government tasked with environmental protection matters. President Richard Nixon proposed the establishment of EPA on July 9, 1970; it ...
or National Weather Service
The National Weather Service (NWS) is an agency of the United States federal government that is tasked with providing weather forecasts, warnings of hazardous weather, and other weather-related products to organizations and the public for the ...
may join ad hoc operations.
While some of these contingencies may not immediately seem related to national security, the reality is different, in that a major natural disaster, such as Hurricane Katrina, will need significant military support. In North America, the Incident Command System
The Incident Command System (ICS) is a standardized approach to the command, control, and coordination of emergency response providing a common hierarchy within which responders from multiple agencies can be effective.
ICS was initially develo ...
, with variants all the way from local to the National Incident Management System
The National Incident Management System (NIMS) is a standardized approach to incident management developed by the United States Department of Homeland Security. The program was established in March 2004, in response to Homeland Security Presidentia ...
, are common to emergency service organizations.
Major military commands often have operations centers, into which subordinate headquarters feed information, and higher commands are kept aware of the situation but not its details. They, in turn, feed information to their national levels. The US and Russia have exchanged liaison teams in their aerospace warning centers, and there are "hotline" communications between countries that may need to resolve crises, such the HAMMER RICK system between the US and Israel.
Indications and warning checklists
Indications and warnings are collated into "indications check lists" specific to particular countries and systems. For example, it might be routine for one country flying a given aircraft to launch formations on short notice, as part of its regular training. A different country might, due to shortages of fuel or maintenance personnel, rarely do formation takeoffs, and that would be indicative of an intended action. Some actions in one's own country or by one's own forces may trigger national-level alerts, such as an accident involving nuclear weapons, a major national disaster, etc.Situation intelligence
Situation intelligence lies between the immediate and the moderate term. It draws on reference material, current intelligence, and raw information that is not directly relevant to a tactical goal. It gives policymakers an overview and context. TheCanadian Security Intelligence Service
The Canadian Security Intelligence Service (CSIS, ; french: Service canadien du renseignement de sécurité, ''SCRS'') is Canada's primary national intelligence agency. It is responsible for collecting, analysing, reporting and disseminating int ...
(CSIS) is especially good on publishing materials. An example of a situation study would be ''Commentary No. 70, The Threat from Transnational Crime: An Intelligence Perspective''. The ''Currently Listed errorist' entities data base is another publication.
Technnically not public but widely available, are the reports of the US Congressional Research Service
The Congressional Research Service (CRS) is a public policy research institute of the United States Congress. Operating within the Library of Congress, it works primarily and directly for members of Congress and their committees and staff on a ...
. The Federation of American Scientists maintains one data base at https://fas.org/sgp/crs/index.html.
Information technology
During 2001-2002, a Scholar-in-Residence at the Sherman Kent Center for Intelligence Analysis, the “think tank” attached to the CIA’s training center for analysts, was tasked with something new: using an outside scholar to study the process of analysis itself, especially how Information Technology (IT) was, and could be, used. His "approach was to watch as many DI analysts as practical and ask them how they performed their work. We discussed what kinds of tasks were hard to do and what technologies or procedures seemed to work smoothly. We also talked about their own ideas about how they might use IT more effectively. For the sake of comparison, I also met with researchers at organizations that perform functions similar to those of the DI (e.g., other intelligence organizations; the Congressional Research Service; The Washington Post; and business risk assessment services). Finally, I drew on my own experience in business and non-government research institutions. I was able to watch the DI respond to the terrorist attacks of 11 September 2001 and ramp-up for the war on terrorism. "I came away from this experience impressed by the quality of DI analysts, but also concerned about their lack of awareness of and access to new information technology and services that could be of critical value to their work. The DI has used automated databases since the 1970s and has gradually improved its capabilities. With the existing system, analysts can perform most searches for source documents from CIA archives at their desks and retrieve the documents electronically." It is sadly worth noting, however, that CIA analysts still do much better than their FBI counterparts, who have difficulty accessing any external secure networks, or sharing the most sensitive data within their agency. NSA, however, seems to be much more comfortable with using IT as a daily tool. Agency internal databases continue to improve over earlier generations, but, in many respects, are inferior to commercial search engines. It should be remembered, however, that ease of use is not an absolute requirement. Some search engine human interfaces are "expert friendly" rather than "user friendly", allowing analysts with solid backgrounds in complex search strategies to be at their most efficient. One indicator of some system shortcomings is simply the fact that an important part of a DI analyst’s tradecraft is building an informal source network. A good analyst either knows someone, or “knows someone who knows someone,” at another office or organization who can get the information they need. A good analyst will use these contacts to develop more leads in the process. In the commercial world, these contacts are managed with CRM, ERM, or social networking software. Agency policies and practices create five kinds of constraints that prevent the DI from acquiring new IT and using it effectively. In 2008, the US intelligence community A-Space may have broken through some of these constraints, or will break through in time.Security and IT
Security is probably the single most important factor that prevents the DI from applying information technology more effectively. Security is essential for intelligence, of course. The problem is that, when it comes to IT, approach is not “risk management,” but “risk exclusion.” Until recently, personal digital assistants were forbidden in high-security facilities. There are some very specialized electronic security threats that could apply, so it may be that a secure PDA needs to be developed and provided. Even in government agencies with sensitive but unclassified information (e.g., personal health information covered byHIPAA
The Health Insurance Portability and Accountability Act of 1996 (HIPAA or the Kennedy– Kassebaum Act) is a United States Act of Congress enacted by the 104th United States Congress and signed into law by President Bill Clinton on August 21, 1 ...
), there has been a serious concern over information bypassing safeguards on tiny solid state disk equivalents, which can fit into pens. Other agencies, however, are addressing this problem by requiring the devices to store information in encrypted form, and using biometric identification.
Such exclusionary rules also send an implicit message to DI analysts that information technology is dangerous and not essential for analysis. Analysts are, by the nature of their work, especially aware of security threats. So when they are told that a technology is potentially dangerous, their instinct is to avoid it unless absolutely necessary.
A laptop can be secured, but the security both has to be built-in, and maintained. Files need strong encryption. Multiple layers of security risk detection tools are needed. Biometric authentication will identify only legitimate users.
Security staffs must develop a better understanding of how analysts work. Rather than simply excluding technologies, their goal should be to develop methods of applying IT that are so user-friendly that DI analysts can operate securely with as few hindrances as possible.
See also
* Basic intelligence *Technical intelligence
Technical Intelligence (TECHINT) is intelligence about weapons and equipment used by the armed forces of foreign nations. The related term, scientific and technical intelligence, addresses information collected or analyzed about the broad range ...
*All-source intelligence All-source intelligence is a term used to describe intelligence organizations, intelligence analysts, or intelligence products that are based on all available sources of intelligence collection information.
History
The definition of all-source inte ...
* Geospatial intelligence
References
{{DEFAULTSORT:Analysis ManagementManagement
Management (or managing) is the administration of an organization, whether it is a business, a nonprofit organization, or a Government agency, government body. It is the art and science of managing resources of the business.
Management includ ...
Military intelligence