|
US Intelligence Community A-Space
The United States Intelligence Community A-Space, or Analytic Space, is a project started in 2007 from the Office of the Director of National Intelligence's (ODNI) Office of Analytic Transformation and Technology to develop a common collaborative workspace for all analysts from the United States Intelligence Community, USIC. It is accessible from common workstations and provides unprecedented access to interagency databases, a capability to search classified and unclassified sources simultaneously, web-based messaging, and collaboration tools. The Defense Intelligence Agency (DIA) is the executive agent for building the first phase of A-Space. Initial operational capability was scheduled for December 2007. A-Space went live on the government's classified Joint Worldwide Intelligence Communications System 22 September 2008. A-Space is built on Jive Software's Clearspace application (which has been superseded by Jive's Social Business Software). Analytic transformation The Directo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Clearance
A security clearance is a status granted to individuals allowing them access to classified information (state or organizational secrets) or to restricted areas, after completion of a thorough background check. The term "security clearance" is also sometimes used in private organizations that have a formal process to vet employees for access to sensitive information. A clearance by itself is normally not sufficient to gain access; the organization must also determine that the cleared individual needs to know specific information. No individual is supposed to be granted automatic access to classified information solely because of rank, position, or a security clearance. Canada Background Government classified information is governed by the Treasury Board Standard on Security Screening, the ''Security of Information Act'' and '' Privacy Act''. Only those that are deemed to be loyal and reliable, and have been cleared are allowed to access sensitive information. The policy w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Counter-intelligence
Counterintelligence is an activity aimed at protecting an agency's intelligence program from an opposition's intelligence service. It includes gathering information and conducting activities to prevent espionage, sabotage, assassinations or other intelligence activities conducted by, for, or on behalf of foreign powers, organizations or persons. Many countries will have multiple organisations focusing on a different aspect of counterintelligence, such as domestic, international, and counter-terrorism. Some states will formalise it as part of the police structure, such as the United States' Federal Bureau of Investigation (FBI). Others will establish independent bodies, such as the United Kingdom's MI5, others have both intelligence and counterintelligence grouped under the same agency, like the Canadian Security Intelligence Service (CSIS). History Modern tactics of espionage and dedicated government intelligence agencies developed over the course of the late-19th century. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
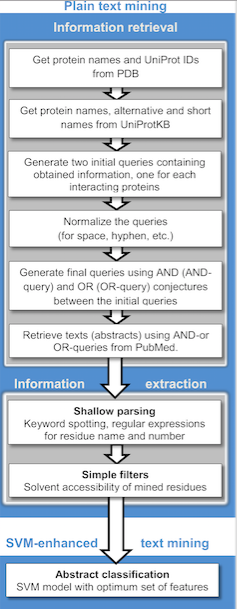
Text Mining
Text mining, also referred to as ''text data mining'', similar to text analytics, is the process of deriving high-quality information from text. It involves "the discovery by computer of new, previously unknown information, by automatically extracting information from different written resources." Written resources may include websites, books, emails, reviews, and articles. High-quality information is typically obtained by devising patterns and trends by means such as statistical pattern learning. According to Hotho et al. (2005) we can distinguish between three different perspectives of text mining: information extraction, data mining, and a KDD (Knowledge Discovery in Databases) process. Text mining usually involves the process of structuring the input text (usually parsing, along with the addition of some derived linguistic features and the removal of others, and subsequent insertion into a database), deriving patterns within the structured data, and finally evaluation and inte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bureau Of Intelligence And Research
The Bureau of Intelligence and Research (INR) is an intelligence agency in the United States Department of State. Its central mission is to provide all-source intelligence and analysis in support of U.S. diplomacy and foreign policy. INR is the oldest civilian element of the U.S. Intelligence Community and among the smallest, with roughly 300 personnel. Though lacking the resources and technology of other U.S. intelligence agencies, it is "one of the most highly regarded" for the quality of its work. INR is descended from the Research and Analysis Branch (R&A) of the World War II-era Office of Strategic Services (OSS), which was tasked with identifying the strengths and weaknesses of the Axis powers. Widely recognized as the most valuable component of the OSS, upon its dissolution in 1945, R&A assets and personnel were transferred to the State Department, forming the Office of Intelligence Research. INR was reorganized into its current form in 1957. In addition to supportin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dale Meyerrose
Dr. Dale W. Meyerrose, Major General (Retired) was the first President-appointed, Senate-confirmed Associate Director of National Intelligence/Intelligence Community Chief Information Officer (CIO) and Information Sharing Executive for the Director of National Intelligence (DNI). Dr. Meyerrose is president of the MeyerRose Group, LLC, a company that consults with a wide range of business, government, and academic organizations on strategy, business planning, technology, education, and executive development issues. He is a visiting associate professor at the School of Information Studies, Syracuse University. He is an adjunct professor at Carnegie Mellon University's School of Computer of Science with the Institute for Software Research and director for the Cybersecurity Leadership (CSL) certificate program. Additionally, Dr. Meyerrose is a Trustee and Treasurer for the U.S. Air Force Academy Falcon Foundation. He was formerly the president and chairman of the board for the A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |