Computer security compromised by hardware failure on:
[Wikipedia]
[Google]
[Amazon]
Computer security compromised by hardware failure is a branch of


 A very simple statistical techniques suffice to reveal sensitive information such as the length of users’ passwords or even root passwords. By using advanced statistical techniques on timing information collected from the network, the eavesdropper can learn significant information about what users type in SSH sessions.ong1p1> Song, 2001, p.1 Because the time it takes the operating system to send out the packet after the keypress is in general negligible comparing to the interkeystroke timing, this also enables an eavesdropper to learn the precise interkeystroke timings of users’ typing from the arrival times of packets.ong1p2> Song, 2001, p.2
A very simple statistical techniques suffice to reveal sensitive information such as the length of users’ passwords or even root passwords. By using advanced statistical techniques on timing information collected from the network, the eavesdropper can learn significant information about what users type in SSH sessions.ong1p1> Song, 2001, p.1 Because the time it takes the operating system to send out the packet after the keypress is in general negligible comparing to the interkeystroke timing, this also enables an eavesdropper to learn the precise interkeystroke timings of users’ typing from the arrival times of packets.ong1p2> Song, 2001, p.2
 One example which exhibits void formation (in this case severe enough to have led to complete failure) is shown in this figure:
One example which exhibits void formation (in this case severe enough to have led to complete failure) is shown in this figure:

 When the data is not where the processor is looking for, it is called a cache-miss. Below, pictures show how the processor fetch data when there are two cache levels.
Unfortunately caches contain only a small portion of the application data and can introduce additional latency to the memory transaction in the case of a miss. This involves also additional power consumption which is due to the activation of memory devices down in the memory hierarchy. The miss penalty has been already used to attack symmetric encryption algorithms, like DES. Bertoni, 2005, p.1 The basic idea proposed in this paper is to force a cache miss while the processor is executing the AES encryption algorithm on a known plain text. Bertoni, 2005, p.3 The attacks allow an unprivileged process to attack other process running in parallel on the same processor, despite partitioning methods such as memory protection, sandboxing and virtualization. Shamir, 2005, p.1
When the data is not where the processor is looking for, it is called a cache-miss. Below, pictures show how the processor fetch data when there are two cache levels.
Unfortunately caches contain only a small portion of the application data and can introduce additional latency to the memory transaction in the case of a miss. This involves also additional power consumption which is due to the activation of memory devices down in the memory hierarchy. The miss penalty has been already used to attack symmetric encryption algorithms, like DES. Bertoni, 2005, p.1 The basic idea proposed in this paper is to force a cache miss while the processor is executing the AES encryption algorithm on a known plain text. Bertoni, 2005, p.3 The attacks allow an unprivileged process to attack other process running in parallel on the same processor, despite partitioning methods such as memory protection, sandboxing and virtualization. Shamir, 2005, p.1
computer security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, n ...
applied to hardware.
The objective of computer security includes protection of information and property from theft, corruption, or natural disaster
A natural disaster is the very harmful impact on a society or community brought by natural phenomenon or Hazard#Natural hazard, hazard. Some examples of natural hazards include avalanches, droughts, earthquakes, floods, heat waves, landslides ...
, while allowing the information and property to remain accessible and productive to its intended users.Computer security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, n ...
Such secret information could be retrieved by different ways. This article focus on the retrieval of data thanks to misused hardware or hardware failure. Hardware could be misused or exploited to get secret data. This article collects main types of attack that can lead to data theft.
Computer security can be comprised by devices, such as keyboards, monitors or printers (thanks to electromagnetic or acoustic emanation for example) or by components of the computer, such as the memory, the network card or the processor (thanks to time or temperature analysis for example).
Devices
Monitor
The monitor is the main device used to access data on a computer. It has been shown that monitors radiate or reflect data on their environment, potentially giving attackers access to information displayed on the monitor.Electromagnetic emanations
Video display units radiate: * narrowband harmonics of the digital clock signals; * broadband harmonics of the various 'random' digital signals such as the video signal. Eck, 1985, p.2 Known as compromising emanations or TEMPEST radiation, a code word for a U.S. government programme aimed at attacking the problem, the electromagnetic broadcast of data has been a significant concern in sensitive computer applications. Eavesdroppers can reconstruct video screen content from radio frequency emanations. Kuhn,1998, p.1 Each (radiated) harmonic of the video signal shows a remarkable resemblance to a broadcast TV signal. It is therefore possible to reconstruct the picture displayed on the video display unit from the radiated emission by means of a normal television receiver. If no preventive measures are taken, eavesdropping on a video display unit is possible at distances up to several hundreds of meters, using only a normal black-and-white TV receiver, a directional antenna and an antenna amplifier. It is even possible to pick up information from some types of video display units at a distance of over 1 kilometer. If more sophisticated receiving and decoding equipment is used, the maximum distance can be much greater. Eck, 1985, p.3Compromising reflections
What is displayed by the monitor is reflected on the environment. The time-varying diffuse reflections of the light emitted by a CRT monitor can be exploited to recover the original monitor image.ack1> Backes, 2010, p.4 This is an eavesdropping technique for spying at a distance on data that is displayed on an arbitrary computer screen, including the currently prevalent LCD monitors. The technique exploits reflections of the screen's optical emanations in various objects that one commonly finds close to the screen and uses those reflections to recover the original screen content. Such objects include eyeglasses, tea pots, spoons, plastic bottles, and even the eye of the user. This attack can be successfully mounted to spy on even small fonts using inexpensive, off-the-shelf equipment (less than 1500 dollars) from a distance of up to 10 meters. Relying on more expensive equipment allowed to conduct this attack from over 30 meters away, demonstrating that similar attacks are feasible from the other side of the street or from a close by building.ack3> Backes, 2008, p.1 Many objects that may be found at a usual workplace can be exploited to retrieve information on a computer's display by an outsider.ack4> Backes, 2008, p.4 Particularly good results were obtained from reflections in a user's eyeglasses or a tea pot located on the desk next to the screen. Reflections that stem from the eye of the user also provide good results. However, eyes are harder to spy on at a distance because they are fast-moving objects and require high exposure times. Using more expensive equipment with lower exposure times helps to remedy this problem.ack5> Backes, 2008, p.11 The reflections gathered from curved surfaces on close by objects indeed pose a substantial threat to the confidentiality of data displayed on the screen. Fully invalidating this threat without at the same time hiding the screen from the legitimate user seems difficult, without using curtains on the windows or similar forms of strong optical shielding. Most users, however, will not be aware of this risk and may not be willing to close the curtains on a nice day.ack2> Backes, 2008, p.2 The reflection of an object, a computer display, in a curved mirror creates a virtual image that is located behind the reflecting surface. For a flat mirror this virtual image has the same size and is located behind the mirror at the same distance as the original object. For curved mirrors, however, the situation is more complex.ack6> Backes, 2008, p.3Keyboard
Electromagnetic emanations
Computer keyboards are often used to transmit confidential data such as passwords. Since they contain electronic components, keyboards emit electromagnetic waves. These emanations could reveal sensitive information such as keystrokes. Vuagnoux, 2009, p.1 Electromagnetic emanations have turned out to constitute a security threat to computer equipment.ack2/> The figure below presents how a keystroke is retrieved and what material is necessary. The approach is to acquire the raw signal directly from the antenna and to process the entire captured electromagnetic spectrum. Thanks to this method, four different kinds of compromising electromagnetic emanations have been detected, generated by wired and wireless keyboards. These emissions lead to a full or a partial recovery of the keystrokes. The best practical attack fully recovered 95% of the keystrokes of a PS/2 keyboard at a distance up to 20 meters, even through walls. Because each keyboard has a specific fingerprint based on the clock frequency inconsistencies, it can determine the source keyboard of a compromising emanation, even if multiple keyboards from the same model are used at the same time. Vuagnoux, 2009, p.2 The four different kinds way of compromising electromagnetic emanations are described below.= The Falling Edge Transition Technique
= When a key is pressed, released or held down, the keyboard sends a packet of information known as a scan code to the computer. Vuagnoux, 2009, p.5 The protocol used to transmit these scan codes is a bidirectional serial communication, based on four wires: Vcc (5 volts), ground, data and clock. Clock and data signals are identically generated. Hence, the compromising emanation detected is the combination of both signals. However, the edges of the data and the clock lines are not superposed. Thus, they can be easily separated to obtain independent signals. Vuagnoux, 2009, p.6= The Generalized Transition Technique
= The Falling Edge Transition attack is limited to a partial recovery of the keystrokes. This is a significant limitation. Vuagnoux, 2009, p.7 The GTT is a falling edge transition attack improved, which recover almost all keystrokes. Indeed, between two traces, there is exactly one data rising edge. If attackers are able to detect this transition, they can fully recover the keystrokes.= The Modulation Technique
= Harmonics compromising electromagnetic emissions come from unintentional emanations such as radiations emitted by the clock, non-linear elements, crosstalk, ground pollution, etc. Determining theoretically the reasons of these compromising radiations is a very complex task. Vuagnoux, 2009, p.8 These harmonics correspond to a carrier of approximately 4 MHz which is very likely the internal clock of the micro-controller inside the keyboard. These harmonics are correlated with both clock and data signals, which describe modulated signals (in amplitude and frequency) and the full state of both clock and data signals. This means that the scan code can be completely recovered from these harmonics.= The Matrix Scan Technique
= Keyboard manufacturers arrange the keys in a matrix. The keyboard controller, often an 8-bit processor, parses columns one-by-one and recovers the state of 8 keys at once. This matrix scan process can be described as 192 keys (some keys may not be used, for instance modern keyboards use 104/105 keys) arranged in 24 columns and 8 rows. Vuagnoux, 2009, p.9 These columns are continuously pulsed one-by-one for at least 3μs. Thus, these leads may act as an antenna and generate electromagnetic emanations. If an attacker is able to capture these emanations, he can easily recover the column of the pressed key. Even if this signal does not fully describe the pressed key, it still gives partial information on the transmitted scan code, i.e. the column number. Note that the matrix scan routine loops continuously. When no key is pressed, we still have a signal composed of multiple equidistant peaks. These emanations may be used to remotely detect the presence of powered computers. Concerning wireless keyboards, the wireless data burst transmission can be used as an electromagnetic trigger to detect exactly when a key is pressed, while the matrix scan emanations are used to determine the column it belongs to.= Summary
= Some techniques can only target some keyboards. This table sums up which technique could be used to find keystroke for different kind of keyboard. In their paper called "Compromising Electromagnetic Emanations of Wired and Wireless Keyboards", Martin Vuagnoux and Sylvain Pasini tested 12 different keyboard models, with PS/2, USB connectors and wireless communication in different setups: a semi-anechoic chamber, a small office, an adjacent office and a flat in a building. The table below presents their results.Acoustic emanations
Attacks against emanations caused by human typing have attracted interest in recent years. In particular, works showed that keyboard acoustic emanations do leak information that can be exploited to reconstruct the typed text.er1> Berger, 2006, p.1 PC keyboards, notebook keyboards are vulnerable to attacks based on differentiating the sound emanated by different keys.so1> Asonov, 2004, p.1 This attack takes as input an audio signal containing a recording of a single word typed by a single person on a keyboard, and a dictionary of words. It is assumed that the typed word is present in the dictionary. The aim of the attack is to reconstruct the original word from the signal.er2> Berger, 2006, p.2 This attack, taking as input a 10-minute sound recording of a user typing English text using a keyboard, and then recovering up to 96% of typed characters.hu1> Zhuang, 2005, p.1 This attack is inexpensive because the other hardware required is a parabolic microphone and non-invasive because it does not require physical intrusion into the system. The attack employs a neural network to recognize the key being pressed.so1/> It combines signal processing and efficient data structures and algorithms, to successfully reconstruct single words of 7-13 characters from a recording of the clicks made when typing them on a keyboard.er1/> The sound of clicks can differ slightly from key to key, because the keys are positioned at different positions on the keyboard plate, although the clicks of different keys sound similar to the human ear.so1/> On average, there were only 0.5 incorrect recognitions per 20 clicks, which shows the exposure of keyboard to the eavesdropping using this attack.so2> Asonov, 2004, p.4 The attack is very efficient, taking under 20 seconds per word on a standard PC. A 90% or better success rate of finding the correct word for words of 10 or more characters, and a success rate of 73% over all the words tested.er1/> In practice, a human attacker can typically determine if text is random. An attacker can also identify occasions when the user types user names and passwords.hu2> Zhuang, 2005, p.4 Short audio signals containing a single word, with seven or more characters long was considered. This means that the signal is only a few seconds long. Such short words are often chosen as a password.er1/> The dominant factors affecting the attack's success are the word length, and more importantly, the number of repeated characters within the word.er1/> This is a procedure that makes it possible to efficiently uncover a word out of audio recordings of keyboard click sounds.er3> Berger, 2006, p.8 More recently, extracting information out of another type of emanations was demonstrated: acoustic emanations from mechanical devices such as dot-matrix printers.er1/>Video Eavesdropping on Keyboard
While extracting private information by watching somebody typing on a keyboard might seem to be an easy task, it becomes extremely challenging if it has to be automated. However, an automated tool is needed in the case of long-lasting surveillance procedures or long user activity, as a human being is able to reconstruct only a few characters per minute. The paper "ClearShot: Eavesdropping on Keyboard Input from Video" presents a novel approach to automatically recovering the text being typed on a keyboard, based solely on a video of the user typing. Balzarotti, 2008, p.1 Automatically recognizing the keys being pressed by a user is a hard problem that requires sophisticated motion analysis. Experiments show that, for a human, reconstructing a few sentences requires lengthy hours of slow-motion analysis of the video. Balzarotti, 2008, p.2 The attacker might install a surveillance device in the room of the victim, might take control of an existing camera by exploiting a vulnerability in the camera's control software, or might simply point a mobile phone with an integrated camera at the laptop's keyboard when the victim is working in a public space. Balzarotti's analysis is divided into two main phases (figure below). The first phase analyzes the video recorded by the camera using computer vision techniques. For each frame of the video, the computer vision analysis computes the set of keys that were likely pressed, the set of keys that were certainly not pressed, and the position of space characters. Because the results of this phase of the analysis are noisy, a second phase, called the text analysis, is required. The goal of this phase is to remove errors using both language and context-sensitive techniques. The result of this phase is the reconstructed text, where each word is represented by a list of possible candidates, ranked by likelihood.
Printer
Acoustic emanations
With acoustic emanations, an attack that recovers what a dot-matrix printer processing English text is printing is possible. It is based on a record of the sound the printer makes, if the microphone is close enough to it. This attack recovers up to 72% of printed words, and up to 95% if knowledge about the text are done, with a microphone at a distance of 10 cm from the printer.ack10> Backes, 2010, p.1 After an upfront training phase ("a" in the picture below), the attack ("b" in the picture below) is fully automated and uses a combination of machine learning, audio processing, and speech recognition techniques, including spectrum features, Hidden Markov Models and linear classification.ack1/> The fundamental reason why the reconstruction of the printed text works is that, the emitted sound becomes louder if more needles strike the paper at a given time.ack2/> There is a correlation between the number of needles and the intensity of the acoustic emanation.ack2/> A training phase was conducted where words from a dictionary are printed and characteristic sound features of these words are extracted and stored in a database. The trained characteristic features was used to recognize the printed English text.ack2/> But, this task is not trivial. Major challenges include : # Identifying and extracting sound features that suitably capture the acoustic emanation of dot-matrix printers; # Compensating for the blurred and overlapping features that are induced by the substantial decay time of the emanations; # Identifying and eliminating wrongly recognized words to increase the overall percentage of correctly identified words (recognition rate).ack2/>
Computer components
Network Interface Card
Timing attack
Timing attacks enable an attacker to extract secrets maintained in a security system by observing the time it takes the system to respond to various queries.rum1p1> Brumley, 2003, p.1SSH
The Secure Shell Protocol (SSH Protocol) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution.
SSH was designed for Un ...
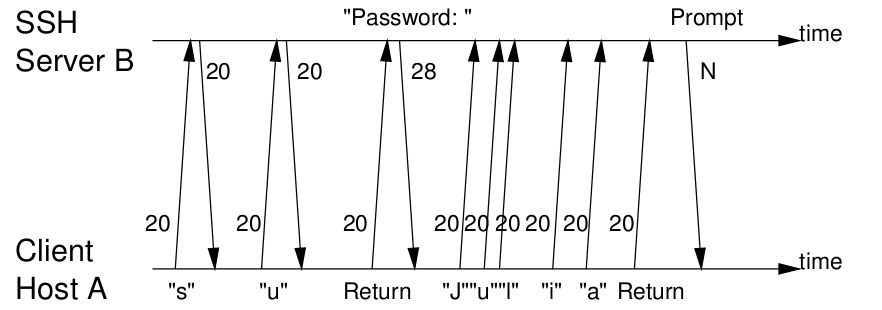
is designed to provide a secure channel between two hosts. Despite the encryption and authentication mechanisms it uses, SSH has weaknesses. In interactive mode, every individual keystroke that a user types is sent to the remote machine in a separate IP packet immediately after the key is pressed, which leaks the inter-keystroke timing information of users’ typing. Below, the picture represents the command ''su'' processed through a SSH connection.
 A very simple statistical techniques suffice to reveal sensitive information such as the length of users’ passwords or even root passwords. By using advanced statistical techniques on timing information collected from the network, the eavesdropper can learn significant information about what users type in SSH sessions.ong1p1> Song, 2001, p.1 Because the time it takes the operating system to send out the packet after the keypress is in general negligible comparing to the interkeystroke timing, this also enables an eavesdropper to learn the precise interkeystroke timings of users’ typing from the arrival times of packets.ong1p2> Song, 2001, p.2
A very simple statistical techniques suffice to reveal sensitive information such as the length of users’ passwords or even root passwords. By using advanced statistical techniques on timing information collected from the network, the eavesdropper can learn significant information about what users type in SSH sessions.ong1p1> Song, 2001, p.1 Because the time it takes the operating system to send out the packet after the keypress is in general negligible comparing to the interkeystroke timing, this also enables an eavesdropper to learn the precise interkeystroke timings of users’ typing from the arrival times of packets.ong1p2> Song, 2001, p.2
Memory
Physical chemistry
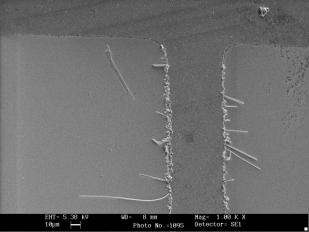
Data remanence problems not only affect obvious areas such as RAM and non-volatile memory cells but can also occur in other areas of the device through hot-carrier effects (which change the characteristics of the semiconductors in the device) and various other effects which are examined alongside the more obvious memory-cell remanence problems. Gutmann, 2001, p. 1 It is possible to analyse and recover data from these cells and from semiconductor devices in general long after it should (in theory) have vanished. Gutmann, 2001, p. 4 Electromigration, which means to physically move the atom to new locations (to physically alter the device itself) is another type of attack. It involves the relocation of metal atoms due to high current densities, a phenomenon in which atoms are carried along by an "electron wind" in the opposite direction to the conventional current, producing voids at the negative electrode and hillocks and whiskers at the positive electrode. Void formation leads to a local increase in current density and Joule heating (the interaction of electrons and metal ions to produce thermal energy), producing further electromigration effects. When the external stress is removed, the disturbed system tends to relax back to its original equilibrium state, resulting in a backflow which heals some of the electromigration damage. In the long term though, this can cause device failure, but in less extreme cases it simply serves to alter a device's operating characteristics in noticeable ways. For example, the excavations of voids leads to increased wiring resistance and the growth of whiskers leads to contact formation and current leakage. Gutmann, 2001, p.5 An example of a conductor which exhibits whisker growth due to electromigration is shown in the figure below: One example which exhibits void formation (in this case severe enough to have led to complete failure) is shown in this figure:
One example which exhibits void formation (in this case severe enough to have led to complete failure) is shown in this figure:

Temperature
Contrary to popular assumption, DRAMs used in most modern computers retain their contents for several seconds after power is lost, even at room temperature and even if removed from a motherboard. Halderman, 2008, p1 Many products do cryptographic and other security-related computations using secret keys or other variables that the equipment's operator must not be able to read out or alter. The usual solution is for the secret data to be kept in volatile memory inside a tamper-sensing enclosure. Security processors typically store secret key material in static RAM, from which power is removed if the device is tampered with. At temperatures below −20 °C, the contents of SRAM can be ‘frozen’. It is interesting to know the period of time for which a static RAM device will retain data once the power has been removed. Low temperatures can increase the data retention time of SRAM to many seconds or even minutes. Skorobogatov, 2002, p.3Read/Write exploits thanks to FireWire
Maximillian Dornseif presented a technique in these slides, which let him take the control of an Apple computer thanks to an iPod. The attacks needed a first generic phase where the iPod software was modified so that it behaves as master on the FireWire bus. Then the iPod had full read/write access on the Apple Computer when the iPod was plugged into a FireWire port. Dornseif, 2004 FireWire is used by : audio devices, printers, scanners, cameras, gps, etc. Generally, a device connected by FireWire has full access (read/write). Indeed, OHCI Standard (FireWire standard) reads : So, any device connected by FireWire can read and write data on the computer memory. For example, a device can : * Grab the screen contents; * Just search the memory for strings such as login, passwords; * Scan for possible key material; * Search cryptographic keys stored in RAM; * Parse the whole physical memory to understand logical memory layout. or * Mess up the memory; * Change screen content; * Change UID/GID of a certain process; * Inject code into a process; * Inject an additional process.Processor
Cache attack
To increase the computational power, processors are generally equipped with acache memory
In computing, a cache ( ) is a hardware or software component that stores data so that future requests for that data can be served faster; the data stored in a cache might be the result of an earlier computation or a copy of data stored elsew ...
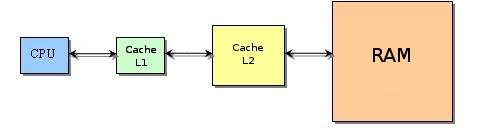
which decreases the memory access latency. Below, the figure shows the hierarchy between the processor and the memory. First the processor looks for data in the cache L1, then L2, then in the memory.
 When the data is not where the processor is looking for, it is called a cache-miss. Below, pictures show how the processor fetch data when there are two cache levels.
Unfortunately caches contain only a small portion of the application data and can introduce additional latency to the memory transaction in the case of a miss. This involves also additional power consumption which is due to the activation of memory devices down in the memory hierarchy. The miss penalty has been already used to attack symmetric encryption algorithms, like DES. Bertoni, 2005, p.1 The basic idea proposed in this paper is to force a cache miss while the processor is executing the AES encryption algorithm on a known plain text. Bertoni, 2005, p.3 The attacks allow an unprivileged process to attack other process running in parallel on the same processor, despite partitioning methods such as memory protection, sandboxing and virtualization. Shamir, 2005, p.1
When the data is not where the processor is looking for, it is called a cache-miss. Below, pictures show how the processor fetch data when there are two cache levels.
Unfortunately caches contain only a small portion of the application data and can introduce additional latency to the memory transaction in the case of a miss. This involves also additional power consumption which is due to the activation of memory devices down in the memory hierarchy. The miss penalty has been already used to attack symmetric encryption algorithms, like DES. Bertoni, 2005, p.1 The basic idea proposed in this paper is to force a cache miss while the processor is executing the AES encryption algorithm on a known plain text. Bertoni, 2005, p.3 The attacks allow an unprivileged process to attack other process running in parallel on the same processor, despite partitioning methods such as memory protection, sandboxing and virtualization. Shamir, 2005, p.1
Timing attack
By carefully measuring the amount of time required to perform private key operations, attackers may be able to find fixed Diffie-Hellman exponents, factor RSA keys, and break other cryptosystems. Against a vulnerable system, the attack is computationally inexpensive and often requires only known ciphertext.och1p1> Kocher, 1996, p.1 The attack can be treated as a signal detection problem. The signal consists of the timing variation due to the target exponent bit, and noise results from measurement inaccuracies and timing variations due to unknown exponent bits. The properties of the signal and noise determine the number of timing measurements required to for the attack. Timing attacks can potentially be used against other cryptosystems, including symmetric functions.och1p9> Kocher, 1996, p.9Privilege escalation
A simple and generic processor backdoor can be used by attackers as a means to privilege escalation to get to privileges equivalent to those of any given running operating system. Duflot, 2008, p.1 Also, a non-privileged process of one of the non-privileged invited domain running on top of a virtual machine monitor can get to privileges equivalent to those of the virtual machine monitor. Loïc Duflot studied Intel processors in the paper " CPU bugs, CPU backdoors and consequences on security"; he explains that the processor defines four different privilege rings numbered from 0 (most privileged) to 3 (least privileged). Kernel code is usually running in ring 0, whereas user-space code is generally running in ring 3. The use of some security-critical assembly language instructions is restricted to ring 0 code. In order to escalate privilege through the backdoor, the attacker must : Duflot, 2008, p.5 # activate the backdoor by placing the CPU in the desired state; # inject code and run it in ring 0; # get back to ring 3 in order to return the system to a stable state. Indeed, when code is running in ring 0, system calls do not work : Leaving the system in ring 0 and running a random system call (exit() typically) is likely to crash the system. The backdoors Loïc Duflot presents are simple as they only modify the behavior of three assembly language instructions and have very simple and specific activation conditions, so that they are very unlikely to be accidentally activated. Recent inventions have begun to target these types of processor-based escalation attacks.References
Bibliography
Acoustic
* * * *Cache attack
* * *Chemical
*Electromagnetic
* * * * *FireWire
* *Processor bug and backdoors
* * *Temperature
* *Timing attacks
* * *Other
* * {{Computer science Computer security Risk analysis