Zeus Malware on:
[Wikipedia]
[Google]
[Amazon]
Zeus, ZeuS, or Zbot is a
 In October 2010 the US
In October 2010 the US
"Measuring the in-the-wild effectiveness of Antivirus against Zeus"
Study by Internet security firm Trusteer.
"A summary of the ZeuS Bot"
A summary of ZeuS as a Trojan and Botnet, plus vector of attacks.
"The Kneber BotNet" by Alex Cox
NetWitness Whitepaper on the Kneber botnet.
"België legt fraude met onlinebankieren bloot"
Dutch news article about a banking trojan
Files and registry keys created by different versions of Zeus Trojan.
Zeus, le dieu des virus contre les banques
Zeus source code at GitHub
Botnet Bust - SpyEye Malware Mastermind Pleads Guilty
Trojan horse
The Trojan Horse was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's ''Iliad'', with the poem ending before the war is concluded, ...
malware
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, depri ...
package that runs on versions of Microsoft Windows
Windows is a group of several proprietary graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for serv ...
. While it can be used to carry out many malicious and criminal tasks, it is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. It is also used to install the CryptoLocker
The CryptoLocker ransomware attack was a cyberattack using the ''CryptoLocker'' ransomware that occurred from 5 September 2013 to late May 2014. The attack utilized a trojan that targeted computers running Microsoft Windows, and was believed ...
ransomware
Ransomware is a type of malware from cryptovirology that threatens to publish the victim's personal data or permanently block access to it unless a ransom is paid off. While some simple ransomware may lock the system without damaging any files, ...
. Zeus is spread mainly through drive-by download
Drive-by download is of two types, each concerning the unintended download of computer software from the Internet:
# Authorized drive-by downloads are downloads which a person has authorized but without understanding the consequences (e.g. down ...
s and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation
The United States Department of Transportation (USDOT or DOT) is one of the executive departments of the U.S. federal government. It is headed by the secretary of transportation, who reports directly to the President of the United States and ...
, it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 FTP
The File Transfer Protocol (FTP) is a standard communication protocol used for the transfer of computer files from a server to a client on a computer network. FTP is built on a client–server model architecture using separate control and data ...
accounts on websites of such companies as the Bank of America
The Bank of America Corporation (often abbreviated BofA or BoA) is an American multinational investment bank and financial services holding company headquartered at the Bank of America Corporate Center in Charlotte, North Carolina. The bank w ...
, NASA
The National Aeronautics and Space Administration (NASA ) is an independent agency of the US federal government responsible for the civil space program, aeronautics research, and space research.
NASA was established in 1958, succeeding t ...
, Monster.com
Monster.com is a global employment website owned and operated by Monster Worldwide, Inc. It was created in 1999 through the merger of The Monster Board (TMB) and Online Career Centre (OCC). It is a subsidiary of Randstad Holding, a Dutch mult ...
, ABC
ABC are the first three letters of the Latin script known as the alphabet.
ABC or abc may also refer to:
Arts, entertainment, and media Broadcasting
* American Broadcasting Company, a commercial U.S. TV broadcaster
** Disney–ABC Television ...
, Oracle
An oracle is a person or agency considered to provide wise and insightful counsel or prophetic predictions, most notably including precognition of the future, inspired by deities. As such, it is a form of divination.
Description
The word '' ...
, Play.com, Cisco
Cisco Systems, Inc., commonly known as Cisco, is an American-based multinational digital communications technology conglomerate corporation headquartered in San Jose, California. Cisco develops, manufactures, and sells networking hardware, ...
, Amazon
Amazon most often refers to:
* Amazons, a tribe of female warriors in Greek mythology
* Amazon rainforest, a rainforest covering most of the Amazon basin
* Amazon River, in South America
* Amazon (company), an American multinational technology c ...
, and '' BusinessWeek''. Similarly to Koobface
Koobface is a network worm that attacks Microsoft Windows, Mac OS X, and Linux platforms. This worm originally targeted users of networking websites like Facebook, Skype, Yahoo Messenger, and email websites such as GMail, Yahoo Mail, and AOL Ma ...
, Zeus has also been used to trick victims of technical support scams into giving the scam artists money through pop-up messages that claim the user has a virus
A virus is a submicroscopic infectious agent that replicates only inside the living cells of an organism. Viruses infect all life forms, from animals and plants to microorganisms, including bacteria and archaea.
Since Dmitri Ivanovsky's 1 ...
, when in reality they might have no viruses at all. The scammers may use programs such as Command prompt
Command Prompt, also known as cmd.exe or cmd, is the default command-line interpreter for the OS/2, eComStation, ArcaOS, Microsoft Windows (Windows NT family and Windows CE family), and ReactOS operating systems. On Windows CE .NET 4.2, Wind ...
or Event viewer
Event Viewer is a component of Microsoft's Windows NT operating system that lets administrators and users view the event logs on a local or remote machine. Applications and operating-system components can use this centralized log service to repo ...
to make the user believe that their computer is infected.
Detection
Zeus is very difficult to detect even with up-to-date antivirus and other security software as it hides itself using stealth techniques. It is considered that this is the primary reason why the Zeus malware has become the largest botnet on the Internet:Damballa
Damballa, also spelled Damballah, Dambala, Dambalah, among other variations ( ht, Danbala), is one of the most important of all loa, spirits in Haitian Voodoo and other African diaspora religious traditions such as Obeah. He is traditionally po ...
estimated that the malware infected 3.6 million PCs
A personal computer (PC) is a multi-purpose microcomputer whose size, capabilities, and price make it feasible for individual use. Personal computers are intended to be operated directly by an end user, rather than by a computer expert or techn ...
in the U.S. in 2009. Security experts are advising that businesses continue to offer training to users to teach them to not to click on hostile or suspicious links in emails or Web sites, and to keep antivirus protection up to date. Antivirus software does not claim to reliably prevent infection; for example Symantec's Browser Protection says that it can prevent "some infection attempts".
FBI crackdown
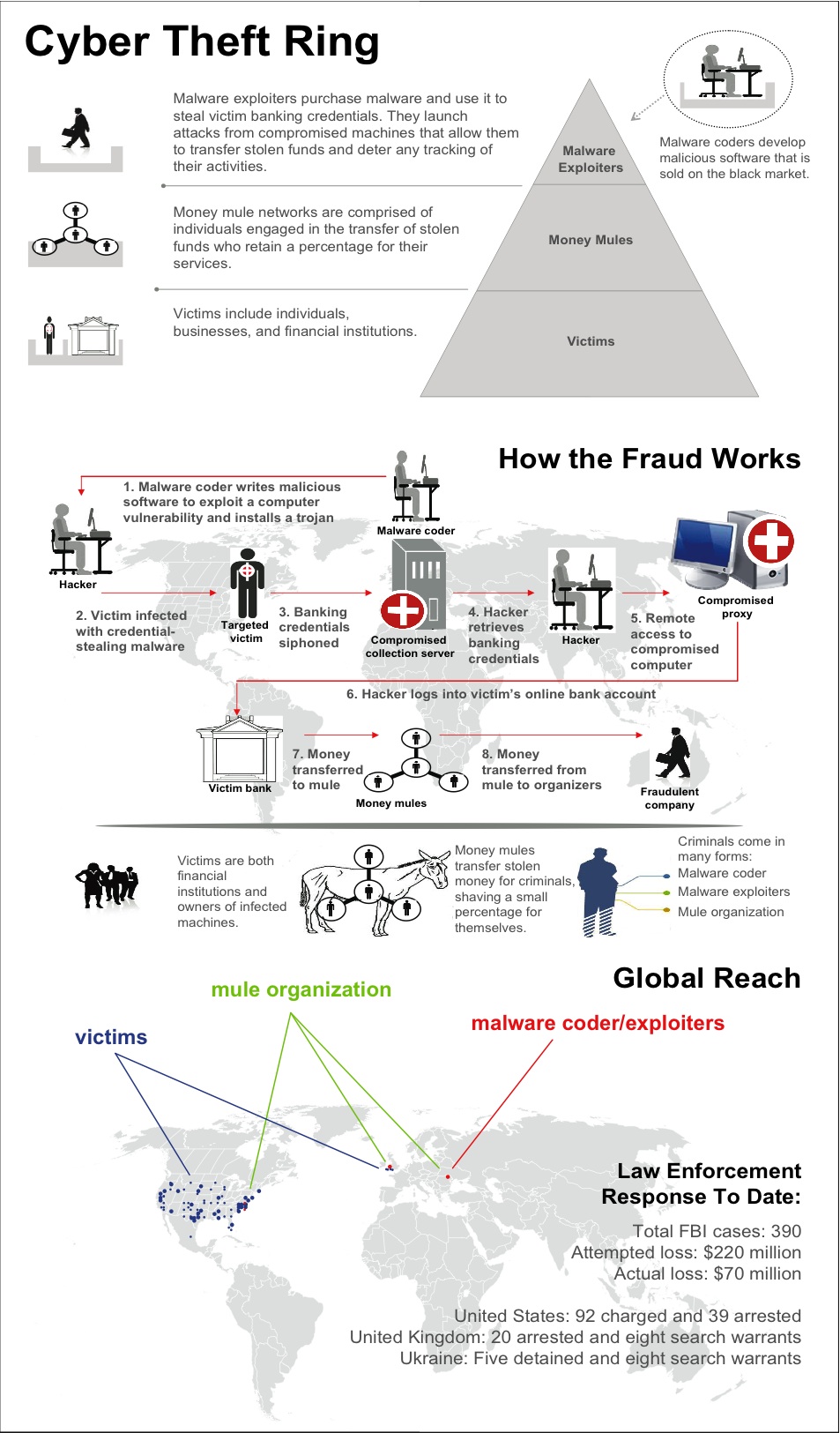
 In October 2010 the US
In October 2010 the US FBI
The Federal Bureau of Investigation (FBI) is the domestic Intelligence agency, intelligence and Security agency, security service of the United States and its principal Federal law enforcement in the United States, federal law enforcement age ...
announced that hackers in Eastern Europe
Eastern Europe is a subregion of the Europe, European continent. As a largely ambiguous term, it has a wide range of geopolitical, geographical, ethnic, cultural, and socio-economic connotations. The vast majority of the region is covered by Russ ...
had managed to infect computers around the world using Zeus. The virus was distributed in an e-mail, and when targeted individuals at businesses and municipalities opened the e-mail, the trojan software installed itself on the victimized computer, secretly capturing passwords, account numbers, and other data used to log into online banking accounts.
The hackers then used this information to take over the victims’ bank accounts and make unauthorized transfers of thousands of dollars at a time, often routing the funds to other accounts controlled by a network of money mules, paid a commission. Many of the U.S. money mules were recruited from overseas. They created bank accounts using fake documents and false names. Once the money was in the accounts, the mules would either wire it back to their bosses in Eastern Europe, or withdraw it in cash and smuggle it out of the country.
More than 100 people were arrested on charges of conspiracy to commit bank fraud
Bank fraud is the use of potentially illegal means to obtain money, assets, or other property owned or held by a financial institution, or to obtain money from depositors by fraudulently posing as a bank or other financial institution. In many ins ...
and money laundering
Money laundering is the process of concealing the origin of money, obtained from illicit activities such as drug trafficking, corruption, embezzlement or gambling, by converting it into a legitimate source. It is a crime in many jurisdictions ...
, over 90 in the US, and the others in the UK and Ukraine
Ukraine ( uk, Україна, Ukraïna, ) is a country in Eastern Europe. It is the second-largest European country after Russia, which it borders to the east and northeast. Ukraine covers approximately . Prior to the ongoing Russian inv ...
. Members of the ring had stolen $70 million.
In 2013 Hamza Bendelladj Hamza Bendelladj ( ar, حمزة بن دلاج, Ḥamza bin Dalāj , th, แฮมซา เบ็นดิลลาดจ์, Haemsa Bendinlat), born either in 1988 or in 1989 in Tizi Ouzou, is an Algerian cyber-criminal and a carder who goes by th ...
, known as Bx1 online, was arrested in Thailand and deported to Atlanta, Georgia
Atlanta ( ) is the capital and most populous city of the U.S. state of Georgia. It is the seat of Fulton County, the most populous county in Georgia, but its territory falls in both Fulton and DeKalb counties. With a population of 498,715 ...
, USA. Early reports said that he was the mastermind behind ZeuS. He was accused of operating SpyEye
SpyEye is a malware program that attacks users running Google Chrome, Opera, Firefox and Internet Explorer on Microsoft Windows operating systems. This malware uses keystroke logging and form grabbing to steal user credentials for malicious use. ...
(a bot functionally similar to ZeuS) botnets, and suspected of also operating ZeuS botnets. He was charged with several counts of wire fraud and computer fraud and abuse. Court papers allege that from 2009 to 2011 Bendelladj and others "developed, marketed, and sold various versions of the SpyEye virus and component parts on the Internet and allowed cybercriminals to customize their purchases to include tailor-made methods of obtaining victims’ personal and financial information". It was also alleged that Bendelladj advertised SpyEye on Internet forums devoted to cyber- and other crimes and operated Command and Control servers. The charges in Georgia relate only to SpyEye, as a SpyEye botnet control server was based in Atlanta.
Possible retirement of creator
In late 2010, a number of Internet security vendors including McAfee andInternet Identity
IID, previously Internet Identity, was a privately held Internet security company based in Tacoma, Washington, United States. IID was acquired in an all-cash transaction by Infoblox on February 8, 2016. It primarily provides cyberthreat data, a p ...
claimed that the creator of Zeus had said that he was retiring and had given the source code
In computing, source code, or simply code, is any collection of code, with or without comments, written using a human-readable programming language, usually as plain text. The source code of a program is specially designed to facilitate the wo ...
and rights to sell Zeus to his biggest competitor, the creator of the SpyEye trojan. However, those same experts warned the retirement was a ruse and expect the developer to return with new tricks.
See also
*Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows OS software and dictionary attacks on administrator passw ...
* Command and control (malware)
* Gameover ZeuS
GameOverZeus is a peer-to-peer botnet based on components from the earlier ZeuS trojan. The malware was created by Russian hacker Evgeniy Mikhailovich Bogachev. It is believed to have been spread through use of the Cutwail botnet.
Unlike its pr ...
, the successor to ZeuS
* Operation Tovar
Operation Tovar is an international collaborative operation carried out by law enforcement agencies from multiple countries against the Gameover ZeuS botnet, which is believed by the investigators to have been used in bank fraud and the distributi ...
* Timeline of computer viruses and worms
A timeline is a display of a list of events in chronological order. It is typically a graphic design showing a long bar labelled with dates paralleling it, and usually contemporaneous events.
Timelines can use any suitable scale representin ...
* Tiny Banker Trojan
Tiny Banker Trojan, also called Tinba, is a malware program that targets financial institution websites. It is a modified form of an older form of viruses known as Banker Trojans, yet it is much smaller in size and more powerful. It works by estab ...
* Torpig
Torpig, also known as Anserin or Sinowal is a type of botnet spread through systems compromised by the Mebroot rootkit by a variety of trojan horses for the purpose of collecting sensitive personal and corporate data such as bank account and credit ...
* Zombie (computer science)
In computing, a zombie is a computer connected to the Internet that has been compromised by a hacker via a computer virus, computer worm, or trojan horse program and can be used to perform malicious tasks under the remote direction of the hac ...
References
External links
"Measuring the in-the-wild effectiveness of Antivirus against Zeus"
Study by Internet security firm Trusteer.
"A summary of the ZeuS Bot"
A summary of ZeuS as a Trojan and Botnet, plus vector of attacks.
"The Kneber BotNet" by Alex Cox
NetWitness Whitepaper on the Kneber botnet.
"België legt fraude met onlinebankieren bloot"
Dutch news article about a banking trojan
Files and registry keys created by different versions of Zeus Trojan.
Zeus, le dieu des virus contre les banques
Zeus source code at GitHub
Botnet Bust - SpyEye Malware Mastermind Pleads Guilty
FBI
The Federal Bureau of Investigation (FBI) is the domestic Intelligence agency, intelligence and Security agency, security service of the United States and its principal Federal law enforcement in the United States, federal law enforcement age ...
{{DEFAULTSORT:Zeus (malware)
Botnets
Rootkits
Windows trojans
Malware toolkits
Cyberattacks on banking industry
Hacking in the 2000s
Hacking in the 2010s
2007 in computing
2008 in computing
2009 in computing
2010 in computing