Weird Machine on:
[Wikipedia]
[Google]
[Amazon]
In
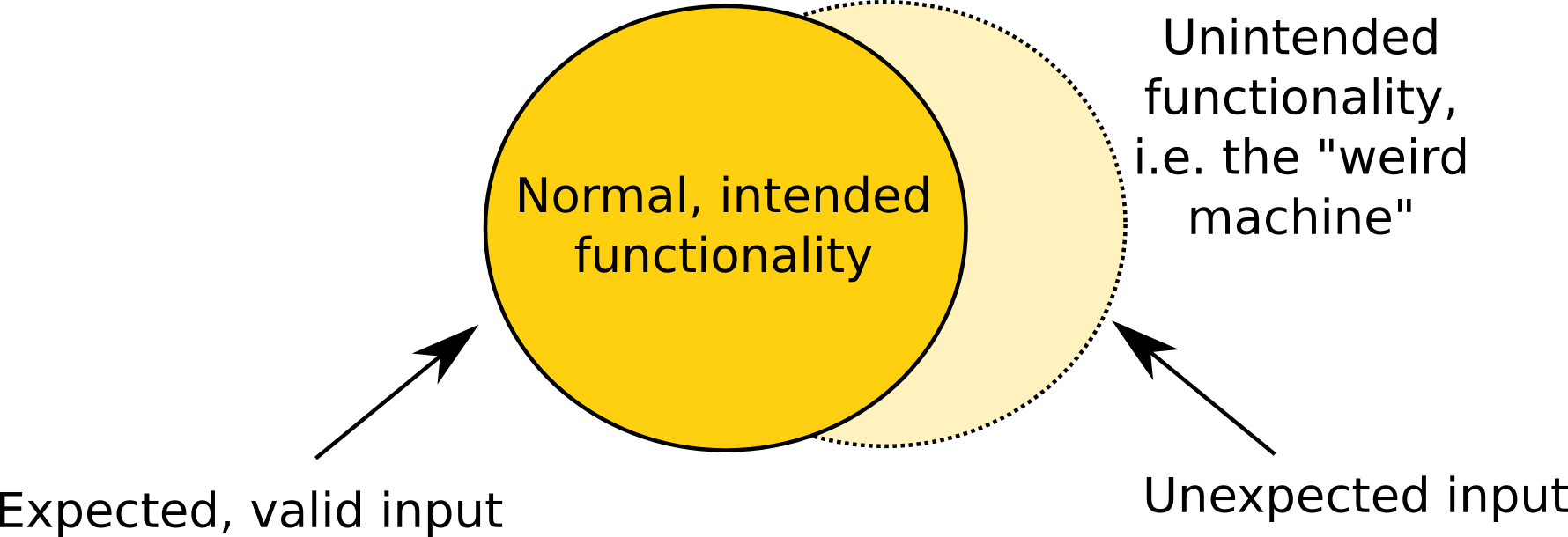 While expected, valid input activates the normal, intended functionality in a
While expected, valid input activates the normal, intended functionality in a
computer security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, t ...
, a weird machine is a computational artifact where additional code execution can happen outside the original specification of the program. It is closely related to the concept of weird instructions, which are the building blocks of an exploit
Exploit means to take advantage of something (a person, situation, etc.) for one's own end, especially unethically or unjustifiably.
Exploit can mean:
* Exploitation of natural resources
*Exploit (computer security)
* Video game exploit
*Exploita ...
based on crafted input data.
The concept of weird machine is a theoretical framework to understand the existence of exploits for security vulnerabilities. Exploits exist empirically, but were not studied from a theoretical perspective prior to the emergence of the framework of weird machines.
Theory
From a theoretical perspective, the emergence of weird machines becomes clear when one considers software as a way to ''restrict'' the number of reachable states and state transitions of a computer: The general-purpose CPU is, through software, specialized to simulate a finite-state machine (with potentially very large state space). Many states the CPU could be in are excluded, and certain state transitions are ruled out - for example those that violate the software's security requirements. When the system is somehow moved into a state that "makes no sense" when viewed from the perspective of the intended finite-state machine (through memory corruption, hardware failure, or other programming mistakes), the software will keep transforming the broken state into new broken states, triggered by further user input. A new computational device arises: The weird machine which can reach different states of the CPU than the programmer anticipated, and which does so in reaction to inputs.Applications
 While expected, valid input activates the normal, intended functionality in a
While expected, valid input activates the normal, intended functionality in a computer program
A computer program is a sequence or set of instructions in a programming language for a computer to execute. Computer programs are one component of software, which also includes documentation and other intangible components.
A computer progra ...
, input that was unexpected by the program developer may activate unintended functionality. The weird machine consists of this unintended functionality that can be programmed with selected inputs in an exploit
Exploit means to take advantage of something (a person, situation, etc.) for one's own end, especially unethically or unjustifiably.
Exploit can mean:
* Exploitation of natural resources
*Exploit (computer security)
* Video game exploit
*Exploita ...
.
In a classical attack taking advantage of a stack buffer overflow
In software, a stack buffer overflow or stack buffer overrun occurs when a program writes to a memory address on the program's call stack outside of the intended data structure, which is usually a fixed-length buffer.
Stack buffer overflow bugs ...
, the input given to a vulnerable program is crafted and delivered so that it itself becomes executed as program code
A computer language is a formal language used to communicate with a computer. Types of computer languages include:
* Construction language – all forms of communication by which a human can specify an executable problem solution to a comput ...
. However, if the data areas of the program memory have been protected so that they cannot be executed directly like this, the input may instead take the form of pointers into pieces of existing program code that then become executed in an unexpected order to generate the functionality of the exploit. These snippets of code that are used by the exploit are referred to as ''gadgets'' in the context of return-oriented programming
Return-oriented programming (ROP) is a computer security exploit technique that allows an attacker to execute code in the presence of security defenses such as executable space protection and code signing.
In this technique, an attacker gains cont ...
.
Through interpretation of data as code, weird machine functionality that is by definition outside the original program specification can be reached also by proof-carrying code Proof-carrying code (PCC) is a software mechanism that allows a host system to verify properties about an application via a formal proof that accompanies the application's executable code. The host system can quickly verify the validity of the pro ...
(PCC), which has been formally proven to function in a certain specific way. This disparity is essentially caused by a disconnect between formal abstract modelling of a computer program and its real-world instance, which can be influenced by events that are not captured in the original abstraction, such as memory errors or power outages.
Weird machine behaviors are observed even in hardware. For instance, it has been shown that one can do computation with only MOV instructions in x86.
Mitigation
Two central categories of mitigation to the problems caused by weird machine functionality include input validation within the software and protecting against problems arising from the platform on which the program runs, such as memory errors. Input validation aims to limit the scope and forms of unexpected inputs e.g. through whitelists of allowed inputs, so that the software program itself would not end up in an unexpected state by interpreting the data internally. Equally importantly, secure programming practices such as protecting againstbuffer overflow
In information security and programming, a buffer overflow, or buffer overrun, is an anomaly whereby a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory locations.
Buffers are areas of memor ...
s make it less likely that input data becomes interpreted in unintended ways by lower layers, such as the hardware on which the program is executed.
See also
*Exploit (computer security)
An exploit (from the English verb ''to exploit'', meaning "to use something to one’s own advantage") is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unant ...
* Return-oriented programming
Return-oriented programming (ROP) is a computer security exploit technique that allows an attacker to execute code in the presence of security defenses such as executable space protection and code signing.
In this technique, an attacker gains cont ...
* Speedrun
Speedrunning is the act of playing a video game, or section of a video game, with the goal of completing it as fast as possible. Speedrunning often involves following planned routes, which may incorporate sequence breaking and can exploit gli ...
* Stack buffer overflow
In software, a stack buffer overflow or stack buffer overrun occurs when a program writes to a memory address on the program's call stack outside of the intended data structure, which is usually a fixed-length buffer.
Stack buffer overflow bugs ...
References
{{reflist Computer security exploits