safe cracker on:
[Wikipedia]
[Google]
[Amazon]
 Safe-cracking is the process of opening a
Safe-cracking is the process of opening a
 While some safes are hard to open, some are susceptible to compromise by
While some safes are hard to open, some are susceptible to compromise by
Safe-cracking history and modern safe engineering
How to Crack a Safe – Tough Method
Safe opening Secrets (German)
Locksmithing Security breaches
 Safe-cracking is the process of opening a
Safe-cracking is the process of opening a safe
A safe (also called a strongbox or coffer) is a secure lockable box used for securing valuable objects against theft or fire. A safe is usually a hollow cuboid or cylinder, with one face being removable or hinged to form a door. The body and ...
without either the combination or the key.
Physical methods
Different procedures may be used to crack a safe, depending on its construction. Different procedures are required to open different safes, so safe-crackers need to be aware of the differences.Lock manipulation
Lock manipulation is a damage-free combination recovery method and a well known surreptitious bypass technique. Manipulation only requires fingers, eyes, and proper technique, though it is a skill that takes years to develop. While manipulation of combination locks is usually performed on Group 2 locks, many Group 1 locks are susceptible to manipulation. It involves the manipulation of thelock
Lock(s) may refer to:
Common meanings
*Lock and key, a mechanical device used to secure items of importance
*Lock (water navigation), a device for boats to transit between different levels of water, as in a canal
Arts and entertainment
* ''Lock ...
in order to obtain the combination one number at a time. Manipulation procedures can vary, but they all rely on exploiting the presence of mechanical imperfections in the lock, unlocking the safe and recovering its combination, which can then be reused to open the safe lock. Similar damage-free bypass can also be completed by a brute-force attack
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct ...
from a computerized auto-dialer or manipulation robot. These auto-dialer machines may take 24 hours or more to reach the correct combination, although modern devices with enhanced advanced software may successfully do this more quickly.
Mechanical safe locks are manipulated primarily by feel and vision, with sound helping the process occasionally. To find the combination the operator uses the lock against itself by measuring internal movements with the dial numbers. More sophisticated locks use advanced mechanics to reduce any feedback a technician could use to identify a combination. These group 1
locks were developed in response to group 2 lock manipulation. Wheels made from lightweight materials will reduce valuable sensory feedback, but are mainly used for improved resistance against radiographic attacks. Manipulation is often the preferred choice in lost-combination lockouts, since it requires no repairs or damage, but can be time consuming for an operator, the specific difficulty depends on the unique wheel shapes and where the gates rest in relation to them. A novice's opening time will be governed by these random inconsistencies, while some leading champions of this art show consistency. There are also a number of tools on the market to assist safe engineers in manipulating a combination lock open in the field.
Nearly all combination locks allow some "slop" while entering a combination on the dial. On average 1% radial rotation in either direction from the center of the true combination number to allow the fence to fall despite slight deviation, so that for a given safe it may be necessary only to try a subset of the combinations. Such "slops" may allow for a margin of error of plus or minus two digits, which means that trying multiples of five would be sufficient in this case. This drastically reduces the time required to exhaust the number of meaningful combinations. A further reduction in solving time is obtained by trying all possible settings for the last wheel for a given setting of the first wheels before nudging the next-to-last wheel to its next meaningful setting, instead of zeroing the lock each time with a number of turns in one direction.
Guessing the combination
Safes may be compromised surprisingly often by simply guessing the combination. This results from the fact that manufactured safes often come with a manufacturer-set combination. These combinations (known as try-out combinations) are designed to allow owners initial access to the safes so that they may set their own new combinations. Sources exist which list manufacturers' try-out combinations. Combinations are also unwittingly compromised by the owners of the safes by having the locks set to easy-to-guess combinations such as a birthdate, street address, or driver's license number.Autodialers
A number of companies and groups have developed autodialing machines to open safes. Unlike fictional machines that can open any combination in a matter of seconds, such machines are usually specific to a particular type of lock and must cycle through thousands of combinations to open a device. A good example of such a device is a project completed by two students from theMassachusetts Institute of Technology
The Massachusetts Institute of Technology (MIT) is a private land-grant research university in Cambridge, Massachusetts. Established in 1861, MIT has played a key role in the development of modern technology and science, and is one of the ...
, Kyle Vogt and Grant Jordan. Their machine, built to open a Sargent and Greenleaf 8500 lock on a Diebold Safe, found an unknown combination in 21,000 tries. Lockmasters, Inc. markets one autodialing machine X3 Combi Autodialer (LKMCOMBI) X3 may refer to:
Arts, entertainment, and media Films
* '' X-Men: The Last Stand'', also known as ''X3'' and ''X-Men 3'', the third film in the comic book film series
* '' XXX: Return of Xander Cage'', a 2017 American film directed by D. J. Caruso ...
that works on a variety of 3 and 4 Wheel combination safe locks.
There also exist computer-aided manipulation tools such as Mas Hamilton's SoftDrill (no longer in production). These tools are similar to autodialers, except they make measurements of the internal components of the lock, and deduce the combination in a similar way to that of a human safe technician.
Weak-point drilling
 While some safes are hard to open, some are susceptible to compromise by
While some safes are hard to open, some are susceptible to compromise by drilling
Drilling is a cutting process where a drill bit is spun to cut a hole of circular cross-section in solid materials. The drill bit is usually a rotary cutting tool, often multi-point. The bit is pressed against the work-piece and rotated at ra ...
or other physical methods. Manufacturers publish drill-point diagrams for specific models of safes. These are tightly guarded by both the manufacturers and locksmithing professionals. Drilling is usually aimed at gaining access to the safe by observation or bypass of the locking mechanism. Drilling is the most common method used by locksmiths, and is commonly used in cases of burglary attempts, malfunctioning locks or damaged locks.
In observational attacks, the drill hole allows the safecracker to view the internal state of the combination lock. Drill-points are often located close to the axis of the dial on the combination lock, but observation may sometimes require drilling through the top, sides or rear of the safe. While observing the lock, the locksmith manipulates the dial to align the lock gates so that the fence falls and the bolt is disengaged.
Bypass attacks involve physical manipulation of the bolt mechanism directly, bypassing the combination lock.
All but the simplest safes are designed to protect against drilling attacks through the implementation of hardplate steel (extremely wear-resistant) or composite hardplate (a casting of metal such as cobalt-vanadium alloys with embedded tungsten carbide
Tungsten carbide (chemical formula: WC) is a chemical compound (specifically, a carbide) containing equal parts of tungsten and carbon atoms. In its most basic form, tungsten carbide is a fine gray powder, but it can be pressed and formed into ...
chips designed to shatter the cutting tips of a drill bit) within the safe, protecting the locking mechanism and other critical areas such as the locking bolts. The use of hardplate ensures that conventional drilling is not successful when used against the safe. Drilling through hardplate requires the use of special-purpose diamond or tungsten-carbide drill-bits. Even then, this can be a time-consuming and difficult process with safes equipped with modern composite hardplates.
Some high-security
Security is protection from, or resilience against, potential harm (or other unwanted coercive change) caused by others, by restraining the freedom of others to act. Beneficiaries (technically referents) of security may be of persons and social ...
safes use a glass relocker. This is a piece of tempered glass mounted between the safe door and the combination lock. It has wires attached to the edges. These wires lead to randomly located, spring-loaded bolts. If an attempt is made to penetrate the safe, the penetrating drill or torch could break the glass and release the bolts. These bolts block the retraction of the main locking bolts. To drill a safe with a glass relocker, side, top, or rear drilling may be necessary. A gas abrasive drill can sometimes be used to drill through a glass relocker without triggering it.
Many modern high-security safes also incorporate thermal relockers in conjunction with glass-based relockers (usually a fusible link as part of the relocker cabling), which also activate when the temperature of a safe exceeds a certain level as a defense against torches
A torch is a stick with combustible material at one end, which is ignited and used as a light source. Torches have been used throughout history, and are still used in processions, symbolic and religious events, and in juggling entertainment. In ...
and thermal lance
A thermal lance, thermic lance, oxygen lance, or burning bar is a tool that heats and melts steel in the presence of pressurized oxygen to create very high temperatures for cutting. It consists of a long steel tube packed with alloy steel rods, w ...
s.
Drilling is an attractive method of safecracking for locksmiths, as it is usually quicker than manipulation, and drilled safes can generally be repaired and returned to service.
Punching, peeling and using a torch are other methods of compromising a safe. The punch system is widely used by criminals for rapid entry. Punching was developed by Pavle Stanimirovic and used in New York City. Peeling is a method that involves removing the outer skin of the safe.
Plasma cutters and thermal lance
A thermal lance, thermic lance, oxygen lance, or burning bar is a tool that heats and melts steel in the presence of pressurized oxygen to create very high temperatures for cutting. It consists of a long steel tube packed with alloy steel rods, w ...
s can be as hot as , much hotter than traditional oxyacetylene torch
Principle of burn cutting
Oxy-fuel welding (commonly called oxyacetylene welding, oxy welding, or gas welding in the United States) and oxy-fuel cutting are processes that use fuel gases (or liquid fuels such as gasoline or petrol, diesel, ...
es, and can be used to burn through the metal
A metal (from Greek μέταλλον ''métallon'', "mine, quarry, metal") is a material that, when freshly prepared, polished, or fractured, shows a lustrous appearance, and conducts electricity and heat relatively well. Metals are typicall ...
on a safe.
Scoping
Scoping a safe is the process of drilling a hole and inserting aborescope
A borescope (occasionally called a boroscope, though this spelling is nonstandard) is an optical instrument designed to assist visual inspection of narrow, difficult-to-reach wikt:cavity#Noun, cavities, consisting of a rigid or flexible tube with ...
into the safe to get an intimate look into a specific part of the security
Security is protection from, or resilience against, potential harm (or other unwanted coercive change) caused by others, by restraining the freedom of others to act. Beneficiaries (technically referents) of security may be of persons and social ...
container. When manipulation proof mechanical locks and glass re-lockers are implemented as security measures, scoping is the most practical option. One common method is called "scoping the change key hole." The safecracker will drill a hole allowing him to get his scope into a position to observe the change key hole. While spinning the dial and looking through the change key hole for certain landmarks on the combination lock's wheel pack, it is possible to obtain the combination and then dial open the safe with the correct combination. This method is common for a professional safe specialist because it leaves the lock in good working order and only simple repairs are needed to bring the safe barrier back to its original condition. It is also a common way to bypass difficult hard plates and glass re-lockers since the change key hole can be scoped by drilling the top, side, or back of the container.
Brute force methods
Other methods of cracking a safe generally involve damaging the safe so that it is no longer functional. These methods may involveexplosives
An explosive (or explosive material) is a reactive substance that contains a great amount of potential energy that can produce an explosion if released suddenly, usually accompanied by the production of light, heat, sound, and pressure. An expl ...
or other devices to inflict severe force
In physics, a force is an influence that can change the motion of an object. A force can cause an object with mass to change its velocity (e.g. moving from a state of rest), i.e., to accelerate. Force can also be described intuitively as a p ...
and damage the safe so it may be opened. Examples of penetration tools include acetylene torch
Principle of burn cutting
Oxy-fuel welding (commonly called oxyacetylene welding, oxy welding, or gas welding in the United States) and oxy-fuel cutting are processes that use fuel gases (or liquid fuels such as gasoline or petrol, diesel, ...
es, drills, and thermal lance
A thermal lance, thermic lance, oxygen lance, or burning bar is a tool that heats and melts steel in the presence of pressurized oxygen to create very high temperatures for cutting. It consists of a long steel tube packed with alloy steel rods, w ...
s. This method requires care as the contents of the safe may be damaged. Safe-crackers can use what are known as jam shots to blow off the safe's doors.
Most modern safes are fitted with 'relockers' (like the one described above) which are triggered by excessive force and will then lock the safe semi-permanently (a safe whose relocker has tripped must then be forced, as the combination or key alone will no longer suffice). This is why a professional safe-technician will use manipulation rather than brute force to open a safe so they do not risk releasing the relocker.
Radiological methods
Penetrating radiation such asX-ray
An X-ray, or, much less commonly, X-radiation, is a penetrating form of high-energy electromagnetic radiation. Most X-rays have a wavelength ranging from 10 picometers to 10 nanometers, corresponding to frequencies in the range 30&nb ...
radiation can be used to reveal the internal angular relationship of the wheels gates to the flys mechanism to deduce the combination. Some modern safe locks are made of lightweight materials such as nylon to inhibit this technique, since most safe exteriors are made of much denser metals. The Chubb Manifoil Mk4 combination lock contains a lead shield surrounding part of the lock to defeat such attempts to read its wheels.
Tunneling into bank vaults
Largebank vault
A bank vault is a secure space where money, valuables, records, and documents are stored. It is intended to protect their contents from theft, unauthorized use, fire, natural disasters, and other threats, much like a safe. Unlike safes, vaults a ...
s which are often located underground have been compromised by safe-crackers who have tunneled in using digging equipment. This method of safe-cracking has been countered by building patrol-passages around the underground vaults. These patrol-passages allow early detection of any attempts to tunnel into a vault.
Safe bouncing
A number of inexpensive safes sold to households for under $100 use mechanical locking mechanisms that are vulnerable to bouncing. Many cheap safes use a magnetic locking pin to prevent lateral movement of an internal locking bolt, and use asolenoid
upright=1.20, An illustration of a solenoid
upright=1.20, Magnetic field created by a seven-loop solenoid (cross-sectional view) described using field lines
A solenoid () is a type of electromagnet formed by a helix, helical coil of wire whose ...
to move the pin when the correct code is entered. This pin can also be moved by the impact of the safe being dropped or struck while on its side, which allows the safe to be opened. One security researcher taught his three-year-old son how to open most consumer gun safes. More expensive safes use a gear mechanism that is less susceptible to mechanical attacks.
Magnet risk
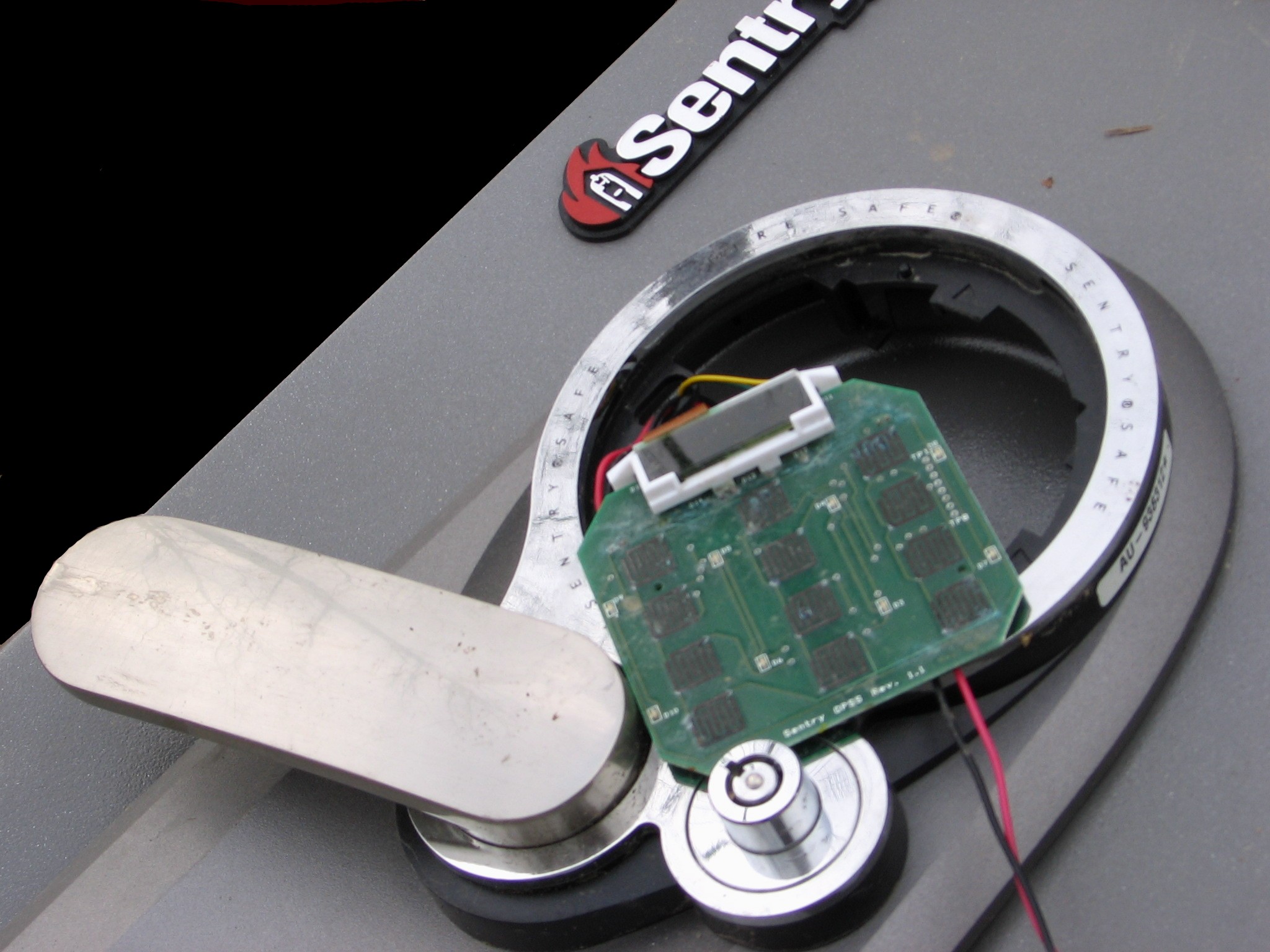
Low-end home and hotel safes often utilize a solenoid as the locking device and can often be opened using a powerful rare-earth magnet.Electronic methods
Electronic lock
An electronic lock (or electric lock) is a locking device which operates by means of electric current. Electric locks are sometimes stand-alone with an electronic control assembly mounted directly to the lock. Electric locks may be connected to ...
s are not vulnerable to traditional manipulation techniques (except for brute-force entry). These locks are often compromised through power analysis
Power analysis is a form of side channel attack in which the attacker studies the power consumption of a cryptographic hardware device. These attacks rely on basic physical properties of the device: semiconductor devices are governed by the l ...
attacks. Several tools exist that can automatically retrieve or reset the combination of an electronic lock; notably, the Little Black Box and Phoenix. Tools like these are often connected to wires in the lock that can be accessed without causing damage to the lock or container. Nearly all high-end, consumer-grade electronic locks are vulnerable to some form of electronic attack.
TEMPEST
The combinations for some electronic locks can be retrieved by examining electromagnetic emissions coming from the lock. Because of this, many safe locks used to protect critical infrastructure are tested and certified to resistTEMPEST
Tempest is a synonym for a storm.
'' The Tempest'' is a play by William Shakespeare.
Tempest or The Tempest may also refer to:
Arts and entertainment Films
* ''The Tempest'' (1908 film), a British silent film
* ''The Tempest'' (1911 film), a ...
attacks. These include the Kaba Mas X-10 and S&G 2740B, which are FF-L-2740B compliant.
Spiking the lock
Low-end electronic fire-safes, such as those used in hotels or for home use, are locked with either a small motor or a solenoid. If the wires running to the device (solenoid or motor) can be accessed, the device can be 'spiked' with a voltage from an external source - typically a 9 volt battery - to open the container.Keypad-based attacks
If an electronic lock accepts user input from akeypad
A keypad is a block or pad of buttons set with an arrangement of digits, symbols, or alphabetical letters. Pads mostly containing numbers and used with computers are numeric keypads. Keypads are found on devices which require mainly numeric in ...
, this process can be observed in order to reveal the combination. Common attacks include:
* Visually observing a user enter the combination ( shoulder surfing)
* Hiding a camera in the room which records the user pressing keys
* Examining fingerprints left on the keys
* Placing certain gels, powders, or substances on the keys that can be smudged or transferred between keys when the combination is entered, and observed at a later time.
* Placing a "skimmer" (akin to those used for credit card fraud
Credit card fraud is an inclusive term for fraud committed using a payment card, such as a credit card or debit card. The purpose may be to obtain goods or services or to make payment to another account, which is controlled by a criminal. The P ...
) behind the keypad to record the digital signals that are sent to the lock body when the combination is entered.
* Examining wear or deformity of buttons which are pressed more often than others
Many of these techniques require the attacker to tamper with the keypad, wait for the unsuspecting user to enter the combination, and return at a later time to retrieve the information. These techniques are sometimes used by members of intelligence or law enforcement agencies, as they are often effective and surreptitious.
High-security keypads
Some keypads are designed to inhibit the aforementioned attacks. This is usually accomplished by restricting the viewing angle of the keypad (either by using a mechanical shroud or special buttons), or randomizing the positions of the buttons each time a combination is entered. Some keypads use smallLED
A light-emitting diode (LED) is a semiconductor Electronics, device that Light#Light sources, emits light when Electric current, current flows through it. Electrons in the semiconductor recombine with electron holes, releasing energy i ...
or LCD
A liquid-crystal display (LCD) is a flat-panel display or other electronically modulated optical device that uses the light-modulating properties of liquid crystals combined with polarizers. Liquid crystals do not emit light directly but in ...
displays inside of the buttons to allow the number on each button to change. This allows for randomization of the button positions, which is normally performed each time the keypad is powered on. The buttons usually contain a lenticular screen in front of the display, which inhibits off-axis viewing of the numbers.
When properly implemented, these keypads make the " shoulder surfing" attack infeasible, as the combination bears no resemblance to the positions of the keys which are pressed.
While these keypads can be used on safes and vaults, this practice is uncommon.
Media depictions
Movies often depict a safe-cracker determining the combination of a safe lock using his fingers or a sensitive listening device to determine the combination of a rotary combination lock. Other films also depict an elaborate scheme of explosives and other devices to open safes. Some of the more famous works include: * ''A Retrieved Reformation
"A Retrieved Reformation" is a short story by American author O. Henry first published in '' The Cosmopolitan Magazine'', April 1903. The original title was "A Retrieved Reform". It was illustrated by A.I. Keller.
History
The story describes ...
'' (1909)
* ''The Asphalt Jungle
''The Asphalt Jungle'' is a 1950 American film noir heist film directed by John Huston. Based on the 1949 novel of the same name by W. R. Burnett, it tells the story of a jewel robbery in a Midwestern city. The film stars Sterling Hayden and Lo ...
'' (1950)
* ''Rififi
''Rififi'' (french: Du rififi chez les hommes) is a 1955 French crime film adaptation of Auguste Le Breton's novel of the same name. Directed by American Hollywood blacklist, blacklisted filmmaker Jules Dassin, the film stars Jean Servais as the ...
'' (1955)
* ''The Cracksman
''The Cracksman'' is a 1963 British comedy film directed by Peter Graham Scott.Personal letter from Delia Derbyshire to Associated British Picture Corporation, dated 25 April 1963.
Plot
Charlie Drake plays honest but naive locksmith Ernest Wr ...
'' (1963)
* '' You Only Live Twice'' (1967)
* ''Who's Minding the Mint?
''Who's Minding the Mint?'' is a 1967 American crime comedy film directed by Howard Morris and starring Jim Hutton, Dorothy Provine, Walter Brennan and Milton Berle. The screenplay, concerning a group of individuals who break into a United State ...
'' (1967)
* ''Olsen Gang
The ''Olsen Gang'' ( da, Olsen-banden, no, Olsenbanden, german: Die Olsenbande) is a Danish comedy film series created by Danish director Erik Balling and special effects expert Henning Bahs about the eponymous fictional criminal gang. The gang's ...
''
** ''Olsen-banden
The ''Olsen Gang'' ( da, Olsen-banden, no, Olsenbanden, german: Die Olsenbande) is a Danish comedy film series created by Danish director Erik Balling and special effects expert Henning Bahs about the eponymous fictional criminal gang. The gang's ...
''
*** ''Olsen-banden Junior
''Olsen-banden Junior'' is a 2001 Danish family-comedy heist film. It is a prequel to the long running Danish film series ''Olsen-banden'', and an implementation of the concept used by the Swedish ''Olsen-banden'' remakes prequels ''Lilla Jöns ...
''
** '' Olsenbanden''
*** '' Olsenbanden Jr.''
** ''Jönssonligan
''Jönssonligan'', literally the ''Jönsson Gang'', is a Swedish comedy film series, originally based on the Danish series of films about the Olsen-banden, but later with unique scripts.
The Jönsson gang consists of the leader and criminal geniu ...
''
*** ''Lilla Jönssonligan
Lilla Jönssonligan ( en, The Little Jönsson gang) is a Swedish film series that consists of four movies. The film series is a spin-off of the original ''Jönssonligan'' film series, featuring the main characters as kids instead of adults. Unli ...
''
* ''Butch Cassidy and the Sundance Kid
''Butch Cassidy and the Sundance Kid'' is a 1969 American Western buddy film directed by George Roy Hill and written by William Goldman. Based loosely on fact, the film tells the story of Wild West outlaws Robert LeRoy Parker, known as Butch C ...
'' (1969)
* ''On Her Majesty's Secret Service On Her Majesty's Secret Service may refer to:
* ''On Her Majesty's Secret Service'' (novel), a 1963 novel by Ian Fleming
* ''On Her Majesty's Secret Service'' (film), a 1969 film adaptation of the novel
** ''On Her Majesty's Secret Service'' (sou ...
'' (1969) - Auto-dialer
* ''The Burglars
''Le Casse'' (US title: ''The Burglars'') is a 1971 French-Italian neo noir crime film directed by director Henri Verneuil and starring Jean-Paul Belmondo and Omar Sharif. It is based on the 1953 novel by David Goodis and revolves around a team ...
'' (1971)
* '' Cool Breeze'' (1972)
* ''Thunderbolt and Lightfoot
''Thunderbolt and Lightfoot'' is a 1974 American crime comedy film written and directed by Michael Cimino and starring Clint Eastwood, Jeff Bridges, George Kennedy, and Geoffrey Lewis.
Plot
A young ne'er-do-well, Lightfoot steals a car. Elsewh ...
'' (1974)
* ''No Deposit, No Return
''No Deposit, No Return'' is a 1976 American crime comedy film directed by Norman Tokar and produced by Walt Disney Productions. The film was written by Arthur Alsberg and Don Nelson, and stars David Niven, Darren McGavin, Don Knotts, Herschel Be ...
'' (1976)
* ''Thief
Theft is the act of taking another person's property or services without that person's permission or consent with the intent to deprive the rightful owner of it. The word ''theft'' is also used as a synonym or informal shorthand term for some ...
'' (1981)
* ''Vabank
''Vabank'' is a 1981 Polish comedy heist film written and directed by Juliusz Machulski, set in 1934 Warsaw (although actually filmed in Łódź and Piotrków Trybunalski).
The film received several awards and nominations, among them:
* Polish Fi ...
'' (1981)
* ''Blood Simple
''Blood Simple'' is a 1984 American independent neo-noir crime film written, edited, produced, and directed by Joel and Ethan Coen, and starring John Getz, Frances McDormand, Dan Hedaya, and M. Emmet Walsh. Its plot follows a Texas bartender who ...
'' (1984)
* ''Short Circuit 2
''Short Circuit 2'' is a 1988 American science fiction comedy film, the sequel to the 1986 film ''Short Circuit''. It was directed by Kenneth Johnson and starred Fisher Stevens as Ben Jahveri, Michael McKean as Fred Ritter, Cynthia Gibb as Sandy ...
'' (1988)
* ''Die Hard
''Die Hard'' is a 1988 American action film directed by John McTiernan, with a screenplay by Jeb Stuart and Steven E. de Souza. Based on the 1979 novel '' Nothing Lasts Forever'', by Roderick Thorp, it stars Bruce Willis, Alan Rickman, Ale ...
'' (1988) - Drilling, guessing electronic passwords
* ''Disorganized Crime
''Disorganized Crime'' is a 1989 American heist comedy film. It was written and directed by Jim Kouf and released through Touchstone Pictures. The ensemble cast includes Fred Gwynne, Lou Diamond Phillips, Rubén Blades, William Russ, Corbin Ber ...
'' (1989)
* '' Breaking In'' (1989) - Drilling, hammering (a cheap safe), nitroglycerin explosives, torch-cutting (with this method the contents were destroyed), social engineering
* ''Hudson Hawk
''Hudson Hawk'' is a 1991 American action comedy film directed by Michael Lehmann. Bruce Willis stars in the title role and also co-wrote both the story and the theme song. Danny Aiello, Andie MacDowell, James Coburn, David Caruso, Lorraine To ...
'' (1991)
* ''Killing Zoe
''Killing Zoe'' is a 1993 crime film written and directed by Roger Avary and starring Eric Stoltz, Jean-Hugues Anglade and Julie Delpy. The story details a safe cracker named Zed who returns to France to aid an old friend in performing a doomed b ...
'' (1994)
* ''Heat
In thermodynamics, heat is defined as the form of energy crossing the boundary of a thermodynamic system by virtue of a temperature difference across the boundary. A thermodynamic system does not ''contain'' heat. Nevertheless, the term is al ...
'' (1995) - Drilling, physical sabotage of external security systems
* ''Safe Men
''Safe Men'' is a 1998 American criminal comedy film written and directed by John Hamburg (in his directorial debut), and stars Sam Rockwell and Steve Zahn as a pair of aspiring lounge singers who are mistaken for ace safe crackers, and get mixe ...
'' (1998)
* ''The Newton Boys
''The Newton Boys'' is a 1998 American Western crime film directed by Richard Linklater, who co-wrote the screenplay with Claude Stanush and Clark Lee Walker. It is based on Stanush's 1994 book of the same name, which tells the true story of the N ...
'' (1998)
* ''Blue Streak
Blue Streak or Bluestreak may refer to:
Entertainment
* ''Blue Streak'' (album), a 1995 album by American blues guitarist Luther Allison
* Blue Streak (comics), a secret identity used by three separate Marvel Comics supervillains
* Bluestreak (c ...
'' (1999)
* ''Sexy Beast
''Sexy Beast'' is a 2000 British crime film directed by Jonathan Glazer (in his feature film directorial debut) and written by Louis Mellis and David Scinto. It stars Ray Winstone, Ben Kingsley, and Ian McShane. It follows Gary "Gal" Dove (Winst ...
'' (2000) -- Tunnelling into a bank vault, and physical destruction of security devices by flooding
* ''Small Time Crooks
''Small Time Crooks'' is a 2000 American crime-comedy film written and directed by Woody Allen, the film's plot has some similarities to that of the 1942 comedy ''Larceny, Inc.''Robert Osborne of Turner Classic Movies on June 15, 2006 It stars Alle ...
'' (2000)
* ''Ocean's Eleven
''Ocean's Eleven'' is a 2001 American heist comedy film directed by Steven Soderbergh from a screenplay by Ted Griffin. The first installment in the ''Ocean's'' film trilogy, it is a remake of the 1960 Rat Pack film of the same name. The fil ...
'' (2001) - Social engineering Social engineering may refer to:
* Social engineering (political science), a means of influencing particular attitudes and social behaviors on a large scale
* Social engineering (security), obtaining confidential information by manipulating and/or ...
, physical sabotage of security systems
* '' The Score'' (2001) - Drilling, thermal lance, internal explosion. This method shown at the climax of the film was tested on an episode of MythBusters
''MythBusters'' is a science entertainment television program, developed by Peter Rees and produced by Australia's Beyond Television Productions. The series premiered on the Discovery Channel on January 23, 2003. It was broadcast internatio ...
(see below).
* ''Panic Room
''Panic Room'' is a 2002 American thriller film directed by David Fincher. The film stars Jodie Foster and Kristen Stewart as a mother and daughter whose new home is invaded by burglars, played by Forest Whitaker, Jared Leto, and Dwight Yoaka ...
'' (2002) - Drilling, brute force, physical destruction of electronic security systems
* ''The Italian Job
''The Italian Job'' is a 1969 British comedy caper film, written by Troy Kennedy Martin, produced by Michael Deeley, directed by Peter Collinson, and starring Michael Caine. The film's plot centres around Cockney criminal Charlie Croker, rece ...
'' (2003)
* ''Bad Santa
''Bad Santa'' is a 2003 American Christmas black comedy film directed by Terry Zwigoff and written by Glenn Ficarra and John Requa. It stars Billy Bob Thornton, with a supporting cast of Tony Cox, Lauren Graham, Brett Kelly, Lauren Tom, John ...
'' (2003)
* '' Brainiac: Science Abuse'' (2003) – The safe was eventually cracked by a high-explosive round fired using a Challenger 2 Tank
The FV4034 Challenger 2 (MOD designation "CR2") is a third generation British main battle tank (MBT) in service with the armies of the United Kingdom and Oman. It was designed and built by the British company Vickers Defence Systems (now known ...
. The contents were destroyed.
* '' The Ladykillers'' (2004)
* ''Burn Notice
''Burn Notice'' is an American espionage television series created by Matt Nix, which originally aired on the USA Network for a total of seven seasons from June 28, 2007, to September 12, 2013. The show stars Jeffrey Donovan, Gabrielle Anwar, ...
'' (2007–2013)
* ''The Bank Job
''The'' () is a grammatical article in English, denoting persons or things already mentioned, under discussion, implied or otherwise presumed familiar to listeners, readers, or speakers. It is the definite article in English. ''The'' is the m ...
'' (2008)
* '' Payday: The Heist'' (2011)
* ''Dom Hemingway
''Dom Hemingway'' is a 2013 British black comedycrime drama film directed and written by Richard Shepard, and starring Jude Law, Richard E. Grant, Demián Bichir and Emilia Clarke. It was shown at the 2013 Toronto International Film Festival ...
'' (2013)
* ''Payday 2
''Payday 2'' is a cooperative first-person shooter video game developed by Overkill Software and published by 505 Games. The game is a sequel to 2011's '' Payday: The Heist''. It was released in August 2013 for Windows, PlayStation 3 and Xbox 360 ...
'' (2013-2016)
* "Battlefield Hardline
''Battlefield Hardline'' is a first-person shooter video game developed by Visceral Games and published by Electronic Arts. It was released in March 2015 for Microsoft Windows, PlayStation 3, PlayStation 4, Xbox 360 and Xbox One. Unlike the prev ...
" (2015) - Safe-cracking robot
* ''Army of Thieves
''Army of Thieves'' is a 2021 heist comedy film directed by Matthias Schweighöfer from a screenplay by Shay Hatten, based on a story he wrote with Zack Snyder. A prequel to ''Army of the Dead'' (2021), it is the second installment in the '' ...
'' (2021)
Three safecracking methods seen in movies were also tested on the television show ''MythBusters
''MythBusters'' is a science entertainment television program, developed by Peter Rees and produced by Australia's Beyond Television Productions. The series premiered on the Discovery Channel on January 23, 2003. It was broadcast internatio ...
'', with some success. While the team was able to blow the door off of a safe by filling the safe with water and detonating an explosive inside it, the contents of the safe were destroyed and filling the safe with water required sealing it from the inside. The safe had also sprung many leaks.
See also
*Access control
In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of ''accessing'' may mean consuming ...
* Lock picking
Lock picking is the practice of unlocking a lock by manipulating the components of the lock device without the original key.
Although lock-picking can be associated with criminal intent, it is an essential skill for the legitimate professi ...
* Physical security
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physica ...
* Security engineering
Security engineering is the process of incorporating security controls into an information system so that the controls become an integral part of the system’s operational capabilities. It is similar to other systems engineering activities in tha ...
References
{{Reflist, 30emExternal links
Safe-cracking history and modern safe engineering
How to Crack a Safe – Tough Method
Safe opening Secrets (German)
Locksmithing Security breaches