STU-III Desk Set With Crypto Ignition Key on:
[Wikipedia]
[Google]
[Amazon]
 STU-III (Secure Telephone Unit - third generation) is a family of
STU-III (Secure Telephone Unit - third generation) is a family of
 * STU-III/Low Cost Terminal (LCT) designed for use in office environment by all types of users. (Motorola Sectel 1500, Lucent Technologies/GD 1100 and 1150)
* STU-III/Cellular Telephone (CT) is interoperable with all STU-III versions. Works in all continental US mobile network and in most of the foreign cellular networks.
* STU-III/Allied (A) specialized version of the STU-III/LCT that is compatible with the STU-II. It retains all basic STU-III functions and capabilities and incorporates STU-II BELLFIELD KDC, STU-II net, and STU-II multipoint modes of operation.
* STU-III/Remote Control Interface (R or RCU)
* STU-III/MultiMedia Terminal (MMT)
* STU-III/Inter Working Function (IWF)
* STU-III/Secure Data Device (SDD)
* STU-III/CipherTAC 2000 (CTAC)
* STU-III/Low Cost Terminal (LCT) designed for use in office environment by all types of users. (Motorola Sectel 1500, Lucent Technologies/GD 1100 and 1150)
* STU-III/Cellular Telephone (CT) is interoperable with all STU-III versions. Works in all continental US mobile network and in most of the foreign cellular networks.
* STU-III/Allied (A) specialized version of the STU-III/LCT that is compatible with the STU-II. It retains all basic STU-III functions and capabilities and incorporates STU-II BELLFIELD KDC, STU-II net, and STU-II multipoint modes of operation.
* STU-III/Remote Control Interface (R or RCU)
* STU-III/MultiMedia Terminal (MMT)
* STU-III/Inter Working Function (IWF)
* STU-III/Secure Data Device (SDD)
* STU-III/CipherTAC 2000 (CTAC)
 Most STU-III units were built for use with what NSA calls
Most STU-III units were built for use with what NSA calls 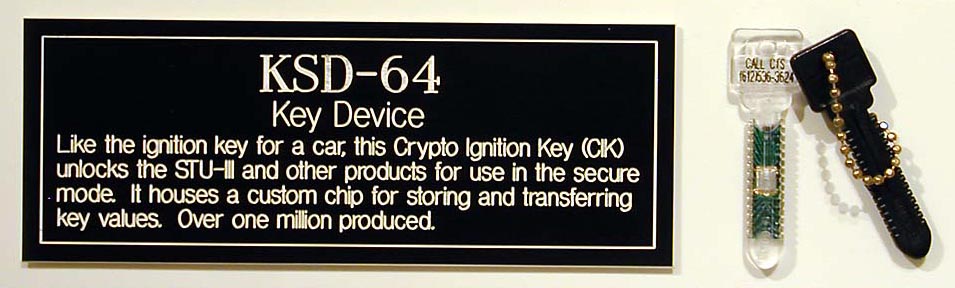 The KSD-64A contains a 64kbit
The KSD-64A contains a 64kbit
STU-III Handbook
{{National Security Agency National Security Agency encryption devices Secure telephones
 STU-III (Secure Telephone Unit - third generation) is a family of
STU-III (Secure Telephone Unit - third generation) is a family of secure telephone
A secure telephone is a telephone that provides Secure voice, voice security in the form of end-to-end encryption for the telephone call, and in some cases also the mutual authentication of the call parties, protecting them against a man-in-the-mi ...
s introduced in 1987 by the NSA
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collecti ...
for use by the United States government, its contractors, and its allies. STU-III desk units look much like typical office telephones, plug into a standard telephone wall jack and can make calls to any ordinary phone user (with such calls receiving no special protection, however). When a call is placed to another STU-III unit that is properly set up, one caller can ask the other to initiate secure transmission
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. Many secure transmission methods require a type of encryption. The most common email encryption is called ...
. They then press a button on their telephones and, after a 15-second delay, their call is encrypted to prevent eavesdropping. There are portable and militarized versions and most STU-IIIs contained an internal modem
A modulator-demodulator or modem is a computer hardware device that converts data from a digital format into a format suitable for an analog transmission medium such as telephone or radio. A modem transmits data by Modulation#Digital modulati ...
and RS-232
In telecommunications, RS-232 or Recommended Standard 232 is a standard originally introduced in 1960 for serial communication transmission of data. It formally defines signals connecting between a ''DTE'' (''data terminal equipment'') such a ...
port for data and fax
Fax (short for facsimile), sometimes called telecopying or telefax (the latter short for telefacsimile), is the telephonic transmission of scanned printed material (both text and images), normally to a telephone number connected to a printer o ...
transmission. Vendors were AT&T
AT&T Inc. is an American multinational telecommunications holding company headquartered at Whitacre Tower in Downtown Dallas, Texas. It is the world's largest telecommunications company by revenue and the third largest provider of mobile tel ...
(later transferred to Lucent Technologies
Lucent Technologies, Inc. was an American multinational telecommunications equipment company headquartered in Murray Hill, New Jersey. It was established on September 30, 1996, through the divestiture of the former AT&T Technologies business u ...
), RCA
The RCA Corporation was a major American electronics company, which was founded as the Radio Corporation of America in 1919. It was initially a patent trust owned by General Electric (GE), Westinghouse, AT&T Corporation and United Fruit Comp ...
(Now L-3 Communications
L3 Technologies, formerly L-3 Communications Holdings, was an American company that supplied command and control, communications, intelligence, surveillance and reconnaissance ( C3ISR) systems and products, avionics, ocean products, training d ...
, East) and Motorola
Motorola, Inc. () was an American Multinational corporation, multinational telecommunications company based in Schaumburg, Illinois, United States. After having lost $4.3 billion from 2007 to 2009, the company split into two independent p ...
.
STU-III are no longer in service with the U.S. Government, with the last cryptographic keys for the units expiring on December 31, 2009. It has been replaced by the STE (Secure Terminal Equipment
Secure Terminal Equipment (STE) is the U.S. government's current (), encrypted telephone communications system for wired or "landline" communications. STE is designed to use ISDN telephone lines which offer higher speeds of up to 128 kbit/s ...
) and other equipment using the more modern Secure Communications Interoperability Protocol
The Secure Communications Interoperability Protocol (SCIP) is a US standard for secure voice and data communication, foone-to-one connections, not packet-switched networks. SCIP derived from the US Government Future Narrowband Digital Terminal ( ...
(SCIP).
Versions
 * STU-III/Low Cost Terminal (LCT) designed for use in office environment by all types of users. (Motorola Sectel 1500, Lucent Technologies/GD 1100 and 1150)
* STU-III/Cellular Telephone (CT) is interoperable with all STU-III versions. Works in all continental US mobile network and in most of the foreign cellular networks.
* STU-III/Allied (A) specialized version of the STU-III/LCT that is compatible with the STU-II. It retains all basic STU-III functions and capabilities and incorporates STU-II BELLFIELD KDC, STU-II net, and STU-II multipoint modes of operation.
* STU-III/Remote Control Interface (R or RCU)
* STU-III/MultiMedia Terminal (MMT)
* STU-III/Inter Working Function (IWF)
* STU-III/Secure Data Device (SDD)
* STU-III/CipherTAC 2000 (CTAC)
* STU-III/Low Cost Terminal (LCT) designed for use in office environment by all types of users. (Motorola Sectel 1500, Lucent Technologies/GD 1100 and 1150)
* STU-III/Cellular Telephone (CT) is interoperable with all STU-III versions. Works in all continental US mobile network and in most of the foreign cellular networks.
* STU-III/Allied (A) specialized version of the STU-III/LCT that is compatible with the STU-II. It retains all basic STU-III functions and capabilities and incorporates STU-II BELLFIELD KDC, STU-II net, and STU-II multipoint modes of operation.
* STU-III/Remote Control Interface (R or RCU)
* STU-III/MultiMedia Terminal (MMT)
* STU-III/Inter Working Function (IWF)
* STU-III/Secure Data Device (SDD)
* STU-III/CipherTAC 2000 (CTAC)
Security
 Most STU-III units were built for use with what NSA calls
Most STU-III units were built for use with what NSA calls Type 1 encryption The U.S. National Security Agency (NSA) used to rank cryptographic products or algorithms by a certification called product types. Product types were defined in the National Information Assurance Glossary (CNSSI No. 4009, 2010) which used to define ...
. This allows them to protect conversations at all security classification
Classified information is material that a government body deems to be sensitive information that must be protected. Access is restricted by law or regulation to particular groups of people with the necessary security clearance and need to know, ...
levels up to Top Secret
Classified information is material that a government body deems to be sensitive information that must be protected. Access is restricted by law or regulation to particular groups of people with the necessary security clearance and need to know, ...
, with the maximum level permitted on a call being the lower clearance level of the two persons talking. At the height of the Commercial COMSEC Endorsement Program, Type 2, 3, and 4 STU-IIIs were manufactured, but they saw little commercial success.
Two major factors in the STU-III's success were the Electronic Key Management System
The Electronic Key Management System (EKMS) is a United States National Security Agency led program responsible for Communications Security ( COMSEC) key management, accounting, and distribution. Specifically, EKMS generates and distributes elect ...
(EKMS) and the use of a removable memory module in a plastic package in the shape of a house key, called a KSD-64A
The KSD-64 Crypto Ignition Key (CIK) is an NSA-developed EEPROM chip packed in a plastic case that looks like a toy key. The model number is due to its storage capacity — 64 kibibits (65,536bits, or 8KiB), enough to store multiple en ...
. The EKMS is believed to be one of the first widespread applications of asymmetric cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic alg ...
. It greatly reduced the complex logistics and bookkeeping associated with ensuring each encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decip ...
device has the right keys and that all keying material is protected and accounted for.
 The KSD-64A contains a 64kbit
The KSD-64A contains a 64kbit EEPROM
EEPROM (also called E2PROM) stands for electrically erasable programmable read-only memory and is a type of non-volatile memory used in computers, usually integrated in microcontrollers such as smart cards and remote keyless systems, or as a ...
chip that can be used to store various types of keying and other information. A new (or zeroized) STU-III must first have a "seed key" installed. This key is shipped from NSA
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collecti ...
by registered mail
Registered mail is a mail service offered by postal services in many countries which allows the sender proof of mailing via a mailing receipt and, upon request, electronic verification that an article was delivered or that a delivery attempt was ...
or Defense Courier Service. Once the STU-III has its seed key, the user calls a toll-free number at NSA to have the seed key converted into an operational key. A list of compromised keys is downloaded to the STU-III at this time. The operational key is supposed to be renewed at least once a year.
The operational key is then split into two components, one of which replaces the information on the KSD-64A, at which point it becomes a Crypto Ignition Key
The KSD-64 Crypto Ignition Key (CIK) is an NSA-developed EEPROM chip packed in a plastic case that looks like a toy key. The model number is due to its storage capacity — 64 kibibits (65,536bits, or 8KiB), enough to store multiple en ...
or CIK. When the CIK is removed from the STU-III telephone neither unit is considered classified. Only when the CIK is inserted into the STU-III on which it was created can classified information be received and sent.
When a call "goes secure", the two STU-III's create a unique key that will be used to encrypt just the call being placed. Each unit first makes sure that the other is not using a revoked key and if one has a more up-to-date key revocation list, it transmits it to the other. Presumably the revocation lists are protected by a digital signature
A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very high confidence that the message was created b ...
generated by NSA.
While there have been no reports of STU-III encryption being broken, there have been claims that foreign intelligence services can recognize the lines on which STU-IIIs are installed and that un-encrypted calls on these lines, particularly what was said while waiting for the "go secure" command to complete, have provided valuable information.
Use
Hundreds of thousands of STU-III sets were produced and many were still in use as of 2004. STU-III replaced earlier voice encryption devices, including theKY-3
The KY-3 (TSEC/KY-3) is a secure telephone system developed by the U.S. National Security Agency in the early 1960s. It was one of the first widely accepted voice voice encryption systems. The "TSEC" prefix to the model number indicates NSA's Tel ...
(1960s), the STU-I (1970) and the STU-II (1975). The STU-II had some 10,000 users. These, in turn, replaced less secure voice scrambler
In telecommunications, a scrambler is a device that transposes or inverts signals or otherwise encodes a message at the sender's side to make the message unintelligible at a receiver not equipped with an appropriately set descrambling device. Wher ...
s. Unlike earlier systems, the STU-III's encryption electronics are completely contained in the desk set. Further, the reduced bandwidth required by a STU-III permitted it to be used for encrypted voice communications even over limited conduits such as the commercial maritime communication satellites of the day.As first demonstrated by Cold War technological innovator Lieutenant Commander David Winters. OPERATION PROVIDE COMFORT, A Communications Perspective, published by the United States European Command Directorate of Command, Control, and Communications, June 4, 1993. The STU-III is no longer in use, having been replaced by the STE (Secure Terminal Equipment
Secure Terminal Equipment (STE) is the U.S. government's current (), encrypted telephone communications system for wired or "landline" communications. STE is designed to use ISDN telephone lines which offer higher speeds of up to 128 kbit/s ...
) or OMNI, more modern, all digital systems that overcome many of the STU-III's problems, including the 15 second delay.
Operational difficulties in using STU-III phones hindered coordination between the Federal Aviation Administration
The Federal Aviation Administration (FAA) is the largest transportation agency of the U.S. government and regulates all aspects of civil aviation in the country as well as over surrounding international waters. Its powers include air traffic m ...
and NORAD
North American Aerospace Defense Command (NORAD ), known until March 1981 as the North American Air Defense Command, is a combined organization of the United States and Canada that provides aerospace warning, air sovereignty, and protection ...
during the September 11, 2001 attacks on New York and Washington. ''See'' Communication during the September 11 attacks
Communication problems and successes played an important role during the September 11 attacks in 2001 and their aftermath. Systems were variously destroyed or overwhelmed by loads greater than they were designed to carry, or failed to operate a ...
.
STE succeeded STU-III in the 1990s. Similar to STU-III, an STE unit physically resembles an ordinary telephone. Besides connecting to a regular wall phone jack (Public Switched Telephone Network
The public switched telephone network (PSTN) provides Communications infrastructure, infrastructure and services for public Telecommunications, telecommunication. The PSTN is the aggregate of the world's circuit-switched telephone networks that ...
), the STE was originally designed to be connected to Integrated Services Digital Network
Integrated Services Digital Network (ISDN) is a set of communication standards for simultaneous digital transmission of voice, video, data, and other network services over the digitalised circuits of the public switched telephone network. W ...
(ISDN) lines. As a result, in addition to having secured voice conversations, users can also use an STE unit for classified data and fax transmissions. Transfer rate of an STE is also considerably higher (STU-III: up to 9 kbit/s; STE: up to 128 kbit/s). Lastly, an STE unit is backward compatible with an STU-III unit when both units are connected to the PSTN.
The heart of an STE unit is the Fortezza Plus (KOV-14
The KOV-14 Fortezza Plus is a US National Security Agency-approved PC card which provides encryption functions and key storage to the Secure Terminal Equipment and other devices. It is a tamper-resistant module based on the Mykotronx Krypton chip ...
) Crypto Card, which is a PCMCIA card
In computing, PC Card is a configuration for computer parallel communication peripheral interface, designed for laptop computers. Originally introduced as PCMCIA, the PC Card standard as well as its successors like CardBus were defined and develop ...
. It contains both the cryptographic algorithms as well as the key(s) used for encryption. Cryptographic algorithms include BATON, FIREFLY, and SDNS signature algorithm. When the Crypto Card is removed from the STE unit, neither the phone or the card is considered classified. BATON
Baton may refer to:
Stick-like objects
*Baton, a type of club
*Baton (law enforcement)
*Baston (weapon), a type of baton used in Arnis and Filipino Martial Arts
*Baton charge, a coordinated tactic for dispersing crowds of people
*Baton (conductin ...
is a block cipher developed by the NSA with a block size of 128 bits and key size of 320 bits. FIREFLY
The Lampyridae are a family of elateroid beetles with more than 2,000 described species, many of which are light-emitting. They are soft-bodied beetles commonly called fireflies, lightning bugs, or glowworms for their conspicuous production ...
, on the other hand, is a key distribution protocol developed by the NSA. The FIREFLY protocol uses public key cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic alg ...
to exchange keys between two participants of a secured call.
Both STU-III and STE are built on technologies that are proprietary, and details of the cryptographic algorithms (BATON and FIREFLY) are classified. Although the secrecy of the algorithms does not make the device less secure, it does limit the usage to within the U.S. government and its allies. Within the Department of Defense, Voice over IP
Voice over Internet Protocol (VoIP), also called IP telephony, is a method and group of technologies for the delivery of speech, voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. The terms In ...
(VoIP) has slowly emerged as an alternative solution to STU-III and STE. The high bandwidth of IP networks makes VoIP attractive because it results in voice quality superior to STU-III and STE. To secure VoIP calls, VoIP phones are connected to classified IP networks (e.g. Secret Internet Protocol Router Network – SIPRNET
The Secure Internet Protocol Router Network (SIPRNet) is "a system of interconnected computer networks used by the U.S. Department of Defense and the U.S. Department of State to transmit classified information (up to and including information cla ...
).
Both allies and adversaries of the United States are interested in STU-III, STE, and other secured voice technologies developed by the NSA. To date, there has not been any reported cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic sec ...
on the encryption algorithms used by the STU-III and STE. Any breaks in these algorithms could jeopardize national security
National security, or national defence, is the security and defence of a sovereign state, including its citizens, economy, and institutions, which is regarded as a duty of government. Originally conceived as protection against military atta ...
.
Information about STU-III is very limited despite the fact that it is out of production. Because of the sensitive nature of the subject, there are few relevant documents available. The majority of the information available originates from the manufacturers (e.g. L-3 Communications) of STU-III and STE.
See also
*SIGSALY
SIGSALY (also known as the X System, Project X, Ciphony I, and the Green Hornet) was a secure speech system used in World War II for the highest-level Allied communications. It pioneered a number of digital communications concepts, including the ...
* STU-I
* STU-II
* KG-84
The KG-84A and KG-84C are encryption devices developed by the U.S. National Security Agency (NSA) to ensure secure transmission of digital data. The KG-84C is a Dedicated Loop Encryption Device (DLED), and both devices are General-Purpose Telegrap ...
* SCIP
* Secure Terminal Equipment
Secure Terminal Equipment (STE) is the U.S. government's current (), encrypted telephone communications system for wired or "landline" communications. STE is designed to use ISDN telephone lines which offer higher speeds of up to 128 kbit/s ...
References
External links
STU-III Handbook
{{National Security Agency National Security Agency encryption devices Secure telephones