RFID Tag on:
[Wikipedia]
[Google]
[Amazon]
Radio-frequency identification (RFID) uses
 Signaling between the reader and the tag is done in several different incompatible ways, depending on the frequency band used by the tag. Tags operating on LF and HF bands are, in terms of radio wavelength, very close to the reader antenna because they are only a small percentage of a wavelength away. In this near field region, the tag is closely coupled electrically with the transmitter in the reader. The tag can modulate the field produced by the reader by changing the electrical loading the tag represents. By switching between lower and higher relative loads, the tag produces a change that the reader can detect. At UHF and higher frequencies, the tag is more than one radio wavelength away from the reader, requiring a different approach. The tag can
Signaling between the reader and the tag is done in several different incompatible ways, depending on the frequency band used by the tag. Tags operating on LF and HF bands are, in terms of radio wavelength, very close to the reader antenna because they are only a small percentage of a wavelength away. In this near field region, the tag is closely coupled electrically with the transmitter in the reader. The tag can modulate the field produced by the reader by changing the electrical loading the tag represents. By switching between lower and higher relative loads, the tag produces a change that the reader can detect. At UHF and higher frequencies, the tag is more than one radio wavelength away from the reader, requiring a different approach. The tag can 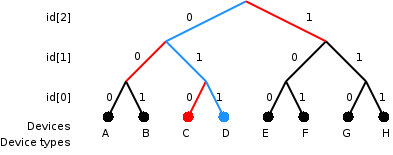 Both methods have drawbacks when used with many tags or with multiple overlapping readers.
Both methods have drawbacks when used with many tags or with multiple overlapping readers.
 * Access management
* Tracking of goods
* Tracking of persons and animals
* Toll collection and
* Access management
* Tracking of goods
* Tracking of persons and animals
* Toll collection and
 RFID tags are widely used in identification badges, replacing earlier
RFID tags are widely used in identification badges, replacing earlier
Some countries are using RFID for vehicle registration and enforcement. RFID can help detect and retrieve stolen cars. RFID is used in intelligent transportation systems. In
RFID is used in intelligent transportation systems. In
Canadian Cattle Identification Agency
began using RFID tags as a replacement for barcode tags. Currently CCIA tags are used in
 RFID for timing races began in the early 1990s with pigeon racing, introduced by the company Deister Electronics in Germany. RFID can provide race start and end timings for individuals in large races where it is impossible to get accurate stopwatch readings for every entrant.
In races utilizing RFID, racers wear tags that are read by antennas placed alongside the track or on mats across the track. UHF tags provide accurate readings with specially designed antennas. Rush error, lap count errors and accidents at race start are avoided, as anyone can start and finish at any time without being in a batch mode.
RFID for timing races began in the early 1990s with pigeon racing, introduced by the company Deister Electronics in Germany. RFID can provide race start and end timings for individuals in large races where it is impossible to get accurate stopwatch readings for every entrant.
In races utilizing RFID, racers wear tags that are read by antennas placed alongside the track or on mats across the track. UHF tags provide accurate readings with specially designed antennas. Rush error, lap count errors and accidents at race start are avoided, as anyone can start and finish at any time without being in a batch mode.
 The design of the chip and of the antenna controls the range from which it can be read. Short range compact chips are twist tied to the shoe, or strapped to the ankle with . The chips must be about 400 mm from the mat, therefore giving very good temporal resolution. Alternatively, a chip plus a very large (125mm square) antenna can be incorporated into the bib number worn on the athlete's chest at a height of about 1.25 m (4.10 ft).
Passive and active RFID systems are used in off-road events such as
The design of the chip and of the antenna controls the range from which it can be read. Short range compact chips are twist tied to the shoe, or strapped to the ankle with . The chips must be about 400 mm from the mat, therefore giving very good temporal resolution. Alternatively, a chip plus a very large (125mm square) antenna can be incorporated into the bib number worn on the athlete's chest at a height of about 1.25 m (4.10 ft).
Passive and active RFID systems are used in off-road events such as
An open source RFID library used as door opener
What is RFID? Educational video by The RFID Network
* *
What is RFID? – animated explanation
*
IEEE Council on RFID
{{Authority control Automatic identification and data capture Privacy Ubiquitous computing Wireless Radio frequency interfaces
electromagnetic field
An electromagnetic field (also EM field or EMF) is a classical (i.e. non-quantum) field produced by (stationary or moving) electric charges. It is the field described by classical electrodynamics (a classical field theory) and is the classical c ...
s to automatically identify and track
Track or Tracks may refer to:
Routes or imprints
* Ancient trackway, any track or trail whose origin is lost in antiquity
* Animal track, imprints left on surfaces that an animal walks across
* Desire path, a line worn by people taking the shorte ...
tags attached to objects. An RFID system consists of a tiny radio transponder
In telecommunications, a transponder is a device that, upon receiving a signal, emits a different signal in response. The term is a blend word, blend of ''transmitter'' and ''responder''.
In air navigation or radio frequency identification, a T ...
, a radio receiver
In radio communications, a radio receiver, also known as a receiver, a wireless, or simply a radio, is an electronic device that receives radio waves and converts the information carried by them to a usable form. It is used with an antenna. Th ...
and transmitter
In electronics and telecommunications, a radio transmitter or just transmitter is an electronic device which produces radio waves with an antenna (radio), antenna. The transmitter itself generates a radio frequency alternating current, which i ...
. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory
Inventory (American English) or stock (British English) refers to the goods and materials that a business holds for the ultimate goal of resale, production or utilisation.
Inventory management is a discipline primarily about specifying the shap ...
goods.
Passive tags are powered by energy from the RFID reader's interrogating radio wave
Radio waves are a type of electromagnetic radiation with the longest wavelengths in the electromagnetic spectrum, typically with frequencies of 300 gigahertz (GHz) and below. At 300 GHz, the corresponding wavelength is 1 mm (short ...
s. Active tags are powered by a battery and thus can be read at a greater range from the RFID reader, up to hundreds of meters.
Unlike a barcode
A barcode or bar code is a method of representing data in a visual, machine-readable form. Initially, barcodes represented data by varying the widths, spacings and sizes of parallel lines. These barcodes, now commonly referred to as linear or o ...
, the tag does not need to be within the line of sight
The line of sight, also known as visual axis or sightline (also sight line), is an imaginary line between a viewer/observer/spectator's eye(s) and a subject of interest, or their relative direction. The subject may be any definable object taken ...
of the reader, so it may be embedded in the tracked object. RFID is one method of automatic identification and data capture
Automatic identification and data capture (AIDC) refers to the methods of automatically identifying objects, collecting data about them, and entering them directly into computer systems, without human involvement. Technologies typically considere ...
(AIDC).
RFID tags are used in many industries. For example, an RFID tag attached to an automobile during production can be used to track its progress through the assembly line
An assembly line is a manufacturing process (often called a ''progressive assembly'') in which parts (usually interchangeable parts) are added as the semi-finished assembly moves from workstation to workstation where the parts are added in seq ...
, RFID-tagged pharmaceuticals can be tracked through warehouses, and implanting RFID microchips in livestock and pets enables positive identification of animals. Tags can also be used in shops to expedite checkout, and to prevent theft by customers and employees.
Since RFID tags can be attached to physical money, clothing, and possessions, or implanted in animals and people, the possibility of reading personally-linked information without consent
Consent occurs when one person voluntarily agrees to the proposal or desires of another. It is a term of common speech, with specific definitions as used in such fields as the law, medicine, research, and sexual relationships. Consent as und ...
has raised serious privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
The domain of privacy partially overlaps with security, which can include the concepts of a ...
concerns. These concerns resulted in standard specifications development addressing privacy and security issues.
In 2014, the world RFID market was worth US$8.89 billion, up from US$7.77 billion in 2013 and US$6.96 billion in 2012. This figure includes tags, readers, and software/services for RFID cards, labels, fobs, and all other form factors. The market value is expected to rise from US$12.08 billion in 2020 to US$16.23 billion by 2029.
History
In 1945,Léon Theremin
Leon Theremin (born Lev Sergeyevich Termen rus, Лев Сергеевич Термéн, p=ˈlʲef sʲɪrˈɡʲejɪvʲɪtɕ tɨrˈmʲen; – 3 November 1993) was a Russian and Soviet inventor, most famous for his invention of the theremin, one o ...
invented the "Thing", a listening device for the Soviet Union
The Soviet Union,. officially the Union of Soviet Socialist Republics. (USSR),. was a transcontinental country that spanned much of Eurasia from 1922 to 1991. A flagship communist state, it was nominally a federal union of fifteen national ...
which retransmitted incident radio waves with the added audio information. Sound waves vibrated a diaphragm which slightly altered the shape of the resonator
A resonator is a device or system that exhibits resonance or resonant behavior. That is, it naturally oscillates with greater amplitude at some frequencies, called resonant frequencies, than at other frequencies. The oscillations in a resonator ...
, which modulated the reflected radio frequency. Even though this device was a covert listening device
A covert listening device, more commonly known as a bug or a wire, is usually a combination of a miniature radio transmitter with a microphone. The use of bugs, called bugging, or wiretapping is a common technique in surveillance, espionage and ...
, rather than an identification tag, it is considered to be a predecessor of RFID because it was passive, being energised and activated by waves from an outside source.
Similar technology, such as the Identification friend or foe
Identification, friend or foe (IFF) is an identification system designed for command and control. It uses a transponder that listens for an ''interrogation'' signal and then sends a ''response'' that identifies the broadcaster. IFF systems usual ...
transponder
In telecommunications, a transponder is a device that, upon receiving a signal, emits a different signal in response. The term is a blend word, blend of ''transmitter'' and ''responder''.
In air navigation or radio frequency identification, a T ...
, was routinely used by the Allies and Germany in World War II
World War II or the Second World War, often abbreviated as WWII or WW2, was a world war that lasted from 1939 to 1945. It involved the vast majority of the world's countries—including all of the great powers—forming two opposin ...
to identify aircraft as friendly or hostile. Transponders
In telecommunications, a transponder is a device that, upon receiving a signal, emits a different signal in response. The term is a blend of ''transmitter'' and ''responder''.
In air navigation or radio frequency identification, a flight trans ...
are still used by most powered aircraft. An early work exploring RFID is the landmark 1948 paper by Harry Stockman, who predicted that "Considerable research and development work has to be done before the remaining basic problems in reflected-power communication are solved, and before the field of useful applications is explored."
Mario Cardullo
Mario Cardullo is an American inventor who received the first patent for a passive, read-write Radio-frequency identification. He is a 1957 graduate of the Polytechnic Institute of Brooklyn, now known as the New York University Tandon School of En ...
's device, patented on January 23, 1973, was the first true ancestor of modern RFID, as it was a passive radio transponder with memory. The initial device was passive, powered by the interrogating signal, and was demonstrated in 1971 to the New York Port Authority and other potential users. It consisted of a transponder with 16 bit
The bit is the most basic unit of information in computing and digital communications. The name is a portmanteau of binary digit. The bit represents a logical state with one of two possible values. These values are most commonly represente ...
memory for use as a toll device. The basic Cardullo patent covers the use of radio frequency (RF), sound and light as transmission carriers. The original business plan presented to investors in 1969 showed uses in transportation (automotive vehicle identification, automatic toll system, electronic license plate
An electronic license plate (also referred to as a digital display license plate) is a vehicle-mounted identification device that emits a radio signal for tracking and digital monitoring purposes. Various patents including advanced features hav ...
, electronic manifest, vehicle routing, vehicle performance monitoring), banking (electronic chequebook, electronic credit card), security (personnel identification, automatic gates, surveillance) and medical (identification, patient history).
In 1973, an early demonstration of ''reflected power'' (modulated backscatter) RFID tags, both passive and semi-passive, was performed by Steven Depp, Alfred Koelle and Robert Frayman at the Los Alamos National Laboratory
Los Alamos National Laboratory (often shortened as Los Alamos and LANL) is one of the sixteen research and development laboratories of the United States Department of Energy (DOE), located a short distance northwest of Santa Fe, New Mexico, ...
. The portable system operated at 915 MHz and used 12-bit tags. This technique is used by the majority of today's UHFID and microwave RFID tags.
In 1983, the first patent to be associated with the abbreviation RFID was granted to Charles Walton.
In 1996, the first patent for a batteryless RFID passive tag with limited interference was granted to David Everett, John Frech, Theodore Wright, and Kelly Rodriguez.
Design
A radio-frequency identification system uses ''tags'', or ''labels'' attached to the objects to be identified. Two-way radio transmitter-receivers called ''interrogators'' or ''readers'' send a signal to the tag and read its response.Tags
RFID tags are made out of three pieces: * a micro chip (anintegrated circuit
An integrated circuit or monolithic integrated circuit (also referred to as an IC, a chip, or a microchip) is a set of electronic circuits on one small flat piece (or "chip") of semiconductor material, usually silicon. Large numbers of tiny ...
which stores and processes information and modulates and demodulates radio-frequency
Radio frequency (RF) is the oscillation rate of an alternating electric current or voltage or of a magnetic, electric or electromagnetic field or mechanical system in the frequency range from around to around . This is roughly between the upp ...
(RF) signals)
* an antenna
Antenna ( antennas or antennae) may refer to:
Science and engineering
* Antenna (radio), also known as an aerial, a transducer designed to transmit or receive electromagnetic (e.g., TV or radio) waves
* Antennae Galaxies, the name of two collid ...
for receiving and transmitting the signal
* a substrate.
The tag information is stored in a non-volatile memory. The RFID tag includes either fixed or programmable logic for processing the transmission and sensor data, respectively.
RFID tags can be either passive, active or battery-assisted passive. An active tag has an on-board battery and periodically transmits its ID signal. A battery-assisted passive tag has a small battery on board and is activated when in the presence of an RFID reader. A passive tag is cheaper and smaller because it has no battery; instead, the tag uses the radio energy transmitted by the reader. However, to operate a passive tag, it must be illuminated with a power level roughly a thousand times stronger than an active tag for signal transmission. This makes a difference in interference and in exposure to radiation.
Tags may either be read-only, having a factory-assigned serial number that is used as a key into a database, or may be read/write, where object-specific data can be written into the tag by the system user. Field programmable tags may be write-once, read-multiple; "blank" tags may be written with an electronic product code by the user.
The RFID tag receives the message and then responds with its identification and other information. This may be only a unique tag serial number, or may be product-related information such as a stock number, lot or batch number, production date, or other specific information. Since tags have individual serial numbers, the RFID system design can discriminate among several tags that might be within the range of the RFID reader and read them simultaneously.
Readers
RFID systems can be classified by the type of tag and reader. There are 3 types: * A Passive Reader Active Tag (PRAT) system has a passive reader which only receives radio signals from active tags (battery operated, transmit only). The reception range of a PRAT system reader can be adjusted from , allowing flexibility in applications such as asset protection and supervision. * An Active Reader Passive Tag (ARPT) system has an active reader, which transmits interrogator signals and also receives authentication replies from passive tags. * An Active Reader Active Tag (ARAT) system uses active tags activated with an interrogator signal from the active reader. A variation of this system could also use a Battery-Assisted Passive (BAP) tag which acts like a passive tag but has a small battery to power the tag's return reporting signal. Fixed readers are set up to create a specific interrogation zone which can be tightly controlled. This allows a highly defined reading area for when tags go in and out of the interrogation zone. Mobile readers may be handheld or mounted on carts or vehicles.Frequencies
Signaling
 Signaling between the reader and the tag is done in several different incompatible ways, depending on the frequency band used by the tag. Tags operating on LF and HF bands are, in terms of radio wavelength, very close to the reader antenna because they are only a small percentage of a wavelength away. In this near field region, the tag is closely coupled electrically with the transmitter in the reader. The tag can modulate the field produced by the reader by changing the electrical loading the tag represents. By switching between lower and higher relative loads, the tag produces a change that the reader can detect. At UHF and higher frequencies, the tag is more than one radio wavelength away from the reader, requiring a different approach. The tag can
Signaling between the reader and the tag is done in several different incompatible ways, depending on the frequency band used by the tag. Tags operating on LF and HF bands are, in terms of radio wavelength, very close to the reader antenna because they are only a small percentage of a wavelength away. In this near field region, the tag is closely coupled electrically with the transmitter in the reader. The tag can modulate the field produced by the reader by changing the electrical loading the tag represents. By switching between lower and higher relative loads, the tag produces a change that the reader can detect. At UHF and higher frequencies, the tag is more than one radio wavelength away from the reader, requiring a different approach. The tag can backscatter
In physics, backscatter (or backscattering) is the reflection of waves, particles, or signals back to the direction from which they came. It is usually a diffuse reflection due to scattering, as opposed to specular reflection as from a mirror, a ...
a signal. Active tags may contain functionally separated transmitters and receivers, and the tag need not respond on a frequency related to the reader's interrogation signal.Daniel M. Dobkin, ''The RF in RFID: Passive UHF RFID In Practice'', Newnes 2008 , chapter 8
An Electronic Product Code
The Electronic Product Code (EPC) is designed as a universal identifier (using a idiosyncratic numerical code for each different commodity) that provides a unique identity for every physical object anywhere in the world, for all time. The EPC stru ...
(EPC) is one common type of data stored in a tag. When written into the tag by an RFID printer, the tag contains a 96-bit string of data. The first eight bits are a header which identifies the version of the protocol. The next 28 bits identify the organization that manages the data for this tag; the organization number is assigned by the EPCGlobal consortium. The next 24 bits are an object class, identifying the kind of product. The last 36 bits are a unique serial number for a particular tag. These last two fields are set by the organization that issued the tag. Rather like a URL, the total electronic product code number can be used as a key into a global database to uniquely identify a particular product.
Often more than one tag will respond to a tag reader, for example, many individual products with tags may be shipped in a common box or on a common pallet. Collision detection is important to allow reading of data. Two different types of protocols are used to "singulate" a particular tag, allowing its data to be read in the midst of many similar tags. In a slotted Aloha
ALOHAnet, also known as the ALOHA System, or simply ALOHA, was a pioneering computer networking system developed at the University of Hawaii. ALOHAnet became operational in June 1971, providing the first public demonstration of a Packet radio, w ...
system, the reader broadcasts an initialization command and a parameter that the tags individually use to pseudo-randomly delay their responses. When using an "adaptive binary tree" protocol, the reader sends an initialization symbol and then transmits one bit of ID data at a time; only tags with matching bits respond, and eventually only one tag matches the complete ID string.
 Both methods have drawbacks when used with many tags or with multiple overlapping readers.
Both methods have drawbacks when used with many tags or with multiple overlapping readers.
Bulk reading
"Bulk reading" is a strategy for interrogating multiple tags at the same time, but lacks sufficient precision for inventory control. A group of objects, all of them RFID tagged, are read completely from one single reader position at one time. However, as tags respond strictly sequentially, the time needed for bulk reading grows linearly with the number of labels to be read. This means it takes at least twice as long to read twice as many labels. Due to collision effects, the time required is greater. A group of tags has to be illuminated by the interrogating signal just like a single tag. This is not a challenge concerning energy, but with respect to visibility; if any of the tags are shielded by other tags, they might not be sufficiently illuminated to return a sufficient response. The response conditions for inductively coupled HF RFID tags and coil antennas in magnetic fields appear better than for UHF or SHF dipole fields, but then distance limits apply and may prevent success. Under operational conditions, bulk reading is not reliable. Bulk reading can be a rough guide for logistics decisions, but due to a high proportion of reading failures, it is not (yet) suitable for inventory management. However, when a single RFID tag might be seen as not guaranteeing a proper read, multiple RFID tags, where at least one will respond, may be a safer approach for detecting a known grouping of objects. In this respect, bulk reading is afuzzy
Fuzzy or Fuzzies may refer to:
Music
* Fuzzy (band), a 1990s Boston indie pop band
* Fuzzy (composer) (born 1939), Danish composer Jens Vilhelm Pedersen
* ''Fuzzy'' (album), 1993 debut album by the Los Angeles rock group Grant Lee Buffalo
* "Fuz ...
method for process support. From the perspective of cost and effect, bulk reading is not reported as an economical approach to secure process control in logistics.
Miniaturization
RFID tags are easy to conceal or incorporate in other items. For example, in 2009 researchers atBristol University
, mottoeng = earningpromotes one's innate power (from Horace, ''Ode 4.4'')
, established = 1595 – Merchant Venturers School1876 – University College, Bristol1909 – received royal charter
, type ...
successfully glued RFID micro-transponders to live ant
Ants are eusocial insects of the family Formicidae and, along with the related wasps and bees, belong to the order Hymenoptera. Ants evolved from vespoid wasp ancestors in the Cretaceous period. More than 13,800 of an estimated total of 22 ...
s in order to study their behavior. This trend towards increasingly miniaturized RFIDs is likely to continue as technology advances.
Hitachi holds the record for the smallest RFID chip, at 0.05 mm × 0.05 mm. This is 1/64th the size of the previous record holder, the mu-chip. Manufacture is enabled by using the silicon-on-insulator
In semiconductor manufacturing, silicon on insulator (SOI) technology is fabrication of silicon semiconductor devices in a layered silicon–insulator–silicon substrate, to reduce parasitic capacitance within the device, thereby improving perfo ...
(SOI) process. These dust-sized chips can store 38-digit numbers using 128-bit Read Only Memory
Read-only memory (ROM) is a type of non-volatile memory used in computers and other electronic devices. Data stored in ROM cannot be electronically modified after the manufacture of the memory device. Read-only memory is useful for storing sof ...
(ROM). A major challenge is the attachment of antennas, thus limiting read range to only millimeters.
TFID (Terahertz Frequency Identification)
In early 2020, MIT researchers demonstrated a terahertz frequency identification (TFID) tag that is barely 1 square millimeter in size. The devices are essentially a piece of silicon that are inexpensive, small, and function like larger RFID tags. Because of the small size, manufacturers could tag any product and track logistics information for minimal cost.Uses
An RFID tag can be affixed to an object and used to track tools, equipment, inventory, assets, people, or other objects. RFID offers advantages over manual systems or use ofbarcode
A barcode or bar code is a method of representing data in a visual, machine-readable form. Initially, barcodes represented data by varying the widths, spacings and sizes of parallel lines. These barcodes, now commonly referred to as linear or o ...
s. The tag can be read if passed near a reader, even if it is covered by the object or not visible. The tag can be read inside a case, carton, box or other container, and unlike barcodes, RFID tags can be read hundreds at a time; barcodes can only be read one at a time using current devices. Some RFID tags, such as battery-assisted passive tags, are also able to monitor temperature and humidity.
In 2011, the cost of passive tags started at US$0.09 each; special tags, meant to be mounted on metal or withstand gamma sterilization, could cost up to US$5. Active tags for tracking containers, medical assets, or monitoring environmental conditions in data centers started at US$50 and could be over US$100 each. Battery-Assisted Passive (BAP) tags were in the US$3–10 range.
RFID can be used in a variety of applications, such as:
 * Access management
* Tracking of goods
* Tracking of persons and animals
* Toll collection and
* Access management
* Tracking of goods
* Tracking of persons and animals
* Toll collection and contactless payment
Contactless payment systems are credit cards and debit cards, key fobs, smart cards, or other devices, including smartphones and other mobile devices, that use radio-frequency identification (RFID) or near-field communication (NFC, e.g. Samsun ...
* Machine readable travel documents
* Smartdust
Smartdust is a system of many tiny microelectromechanical systems (MEMS) such as sensors, robots, or other devices, that can detect, for example, light, temperature, vibration, magnetism, or chemicals. They are usually operated on a computer netwo ...
(for massively distributed sensor
A sensor is a device that produces an output signal for the purpose of sensing a physical phenomenon.
In the broadest definition, a sensor is a device, module, machine, or subsystem that detects events or changes in its environment and sends ...
networks)
* Locating lost airport baggage
* Timing sporting events
* Tracking and billing processes
* Monitoring the physical state of perishable goods
In 2010, three factors drove a significant increase in RFID usage: decreased cost of equipment and tags, increased performance to a reliability of 99.9%, and a stable international standard around HF and UHF passive RFID. The adoption of these standards were driven by EPCglobal, a joint venture between GS1 and GS1 US, which were responsible for driving global adoption of the barcode in the 1970s and 1980s. The EPCglobal Network was developed by the Auto-ID Center.
Commerce
RFID provides a way for organizations to identify and manage stock, tools and equipment (asset tracking
Asset tracking refers to the method of tracking physical assets, either by scanning barcode labels attached to the assets or by using tags using GPS, BLE, LoRa, or RFID which broadcast their location. These technologies can also be used for indo ...
), etc. without manual data entry. Manufactured products such as automobiles or garments can be tracked through the factory and through shipping to the customer. Automatic identification with RFID can be used for inventory systems. Many organisations require that their vendors place RFID tags on all shipments to improve supply chain management
In commerce, supply chain management (SCM) is the management of the flow of goods and services including all processes that transform raw materials into final products between businesses and locations. This can include the movement and stor ...
. Warehouse Management System incorporate this technology to speed up the receiving and delivery of the products and reduce the cost of labor needed in their warehouses.
Retail
RFID is used for item level tagging in retail stores. In addition to inventory control, this provides both protection against theft by customers (shoplifting) and employees ("shrinkage") by usingelectronic article surveillance
Electronic article surveillance is a technological method for preventing shoplifting from retail stores, pilferage of books from libraries or removal of properties from office buildings. Special tags are fixed to merchandise; these tags are remove ...
(EAS), and a self checkout
Self-checkouts (SCOs), also known as assisted checkouts (ACOs) or self-service checkouts, are machines that provide a mechanism for customers to complete their own transaction from a retailer without needing a traditional staffed checkout. When ...
process for customers. Tags of different types can be physically removed with a special tool or deactivated electronically once items have been paid for. On leaving the shop, customers have to pass near an RFID detector; if they have items with active RFID tags, an alarm sounds, both indicating an unpaid-for item, and identifying what it is.
Casinos can use RFID to authenticate poker chip
Casino tokens (also known as casino or gaming chips, checks, cheques or poker chips) are small discs used in terms of currency in casinos. Colored metal, injection-molded plastic or compression molded clay tokens of various denominations are us ...
s, and can selectively invalidate any chips known to be stolen.
Access control
 RFID tags are widely used in identification badges, replacing earlier
RFID tags are widely used in identification badges, replacing earlier magnetic stripe
The term digital card can refer to a physical item, such as a memory card on a camera, or, increasingly since 2017, to the digital content hosted
as a virtual card or cloud card, as a digital virtual representation of a physical card. They share ...
cards. These badges need only be held within a certain distance of the reader to authenticate the holder. Tags can also be placed on vehicles, which can be read at a distance, to allow entrance to controlled areas without having to stop the vehicle and present a card or enter an access code.
Advertising
In 2010 Vail Resorts began using UHF Passive RFID tags in ski passes. Facebook is using RFID cards at most of their live events to allow guests to automatically capture and post photos. Automotive brands have adopted RFID for social media product placement more quickly than other industries. Mercedes was an early adopter in 2011 at the PGA Golf Championships, and by the 2013 Geneva Motor Show many of the larger brands were using RFID for social media marketing.Promotion tracking
To prevent retailers diverting products, manufacturers are exploring the use of RFID tags on promoted merchandise so that they can track exactly which product has sold through the supply chain at fully discounted prices.Transportation and logistics
Yard management, shipping and freight and distribution centers use RFID tracking. In therailroad
Rail transport (also known as train transport) is a means of transport that transfers passengers and goods on wheeled vehicles running on rails, which are incorporated in tracks. In contrast to road transport, where the vehicles run on a pre ...
industry, RFID tags mounted on locomotives and rolling stock identify the owner, identification number and type of equipment and its characteristics. This can be used with a database to identify the type, origin, destination, etc. of the commodities being carried.
In commercial aviation, RFID is used to support maintenance on commercial aircraft. RFID tags are used to identify baggage and cargo at several airports and airlines.Some countries are using RFID for vehicle registration and enforcement. RFID can help detect and retrieve stolen cars.
 RFID is used in intelligent transportation systems. In
RFID is used in intelligent transportation systems. In New York City
New York, often called New York City or NYC, is the List of United States cities by population, most populous city in the United States. With a 2020 population of 8,804,190 distributed over , New York City is also the L ...
, RFID readers are deployed at intersections to track E-ZPass
E-ZPass is an electronic toll collection system used on toll roads, toll bridges, and toll tunnels in the Eastern United States, Midwestern United States, and Southern United States. The E-ZPass Interagency Group (IAG) consists of member agencie ...
tags as a means for monitoring the traffic flow. The data is fed through the broadband wireless infrastructure to the traffic management center to be used in adaptive traffic control
Adaptive traffic control system (ATCS) is a traffic management strategy in which traffic signal timing changes, or adapts, based on actual traffic demand. This is accomplished using an adaptive traffic control system consisting of both hardware a ...
of the traffic lights.
Where ship, rail, or highway tanks are being loaded, a fixed RFID antenna contained in a transfer hose can read an RFID tag affixed to the tank, positively identifying it.
Infrastructure management and protection
At least one company has introduced RFID to identify and locate underground infrastructure assets such asgas
Gas is one of the four fundamental states of matter (the others being solid, liquid, and plasma).
A pure gas may be made up of individual atoms (e.g. a noble gas like neon), elemental molecules made from one type of atom (e.g. oxygen), or ...
pipeline
Pipeline may refer to:
Electronics, computers and computing
* Pipeline (computing), a chain of data-processing stages or a CPU optimization found on
** Instruction pipelining, a technique for implementing instruction-level parallelism within a s ...
s, sewer lines, electrical cables, communication cables, etc.
Passports
The first RFID passports ("E-passport
A biometric passport (also known as an e-passport or a digital passport) is a traditional passport that has an embedded electronic microprocessor chip which contains biometric information that can be used to authenticate the identity of the p ...
") were issued by Malaysia
Malaysia ( ; ) is a country in Southeast Asia. The federation, federal constitutional monarchy consists of States and federal territories of Malaysia, thirteen states and three federal territories, separated by the South China Sea into two r ...
in 1998. In addition to information also contained on the visual data page of the passport, Malaysian e-passports record the travel history (time, date, and place) of entry into and exit out of the country.
Other countries that insert RFID in passports include Norway (2005), Japan (March 1, 2006), most EU countries (around 2006), Australia, Hong Kong, the United States (2007), the United Kingdom and Northern Ireland (2006), India (June 2008), Serbia (July 2008), Republic of Korea (August 2008), Taiwan (December 2008), Albania (January 2009), The Philippines (August 2009), Republic of Macedonia (2010), Argentina (2012), Canada (2013), Uruguay (2015) and Israel (2017).
Standards for RFID passports are determined by the International Civil Aviation Organization
The International Civil Aviation Organization (ICAO, ) is a specialized agency of the United Nations that coordinates the principles and techniques of international air navigation, and fosters the planning and development of international sc ...
(ICAO), and are contained in ICAO Document 9303, Part 1, Volumes 1 and 2 (6th edition, 2006). ICAO refers to the ISO/IEC 14443
ISO/IEC 14443 ''Identification cards -- Contactless integrated circuit cards -- Proximity cards'' is an international standard that defines proximity cards used for identification, and the transmission protocols for communicating with it.
Standa ...
RFID chips in e-passports as "contactless integrated circuits". ICAO standards provide for e-passports to be identifiable by a standard e-passport logo on the front cover.
Since 2006, RFID tags included in new United States passport
United States passports are passports issued to citizens and nationals of the United States of America. They are issued exclusively by the U.S. Department of State. Besides passports (in booklet form), limited-use passport cards are issued by ...
s will store the same information that is printed within the passport, and include a digital picture of the owner. The United States Department of State initially stated the chips could only be read from a distance of , but after widespread criticism and a clear demonstration that special equipment can read the test passports from away, the passports were designed to incorporate a thin metal lining to make it more difficult for unauthorized readers to skim information when the passport is closed. The department will also implement Basic Access Control (BAC), which functions as a personal identification number
A personal identification number (PIN), or sometimes redundantly a PIN number or PIN code, is a numeric (sometimes alpha-numeric) passcode used in the process of authenticating a user accessing a system.
The PIN has been the key to facilitat ...
(PIN) in the form of characters printed on the passport data page. Before a passport's tag can be read, this PIN must be entered into an RFID reader. The BAC also enables the encryption of any communication between the chip and interrogator.
Transportation payments
In many countries, RFID tags can be used to pay for mass transit fares on bus, trains, or subways, or to collect tolls on highways. Some bike lockers are operated with RFID cards assigned to individual users. A prepaid card is required to open or enter a facility or locker and is used to track and charge based on how long the bike is parked. TheZipcar
Zipcar is an American car-sharing company and a subsidiary of Avis Budget Group. Zipcar provides vehicle reservations to its members, billable by the minute, hour or day; members may have to pay a monthly or annual membership fee in addition to ...
car-sharing service uses RFID cards for locking and unlocking cars and for member identification.
In Singapore, RFID replaces paper Season Parking Ticket (SPT).
Animal identification
RFID tags for animals represent one of the oldest uses of RFID. Originally meant for large ranches and rough terrain, since the outbreak of mad-cow disease, RFID has become crucial inanimal identification
Animal identification using a means of marking is a process done to identify and track specific animals. It is done for a variety of reasons including verification of ownership, biosecurity control, and tracking for research or agricultural purpose ...
management. An implantable RFID tag or transponder
In telecommunications, a transponder is a device that, upon receiving a signal, emits a different signal in response. The term is a blend word, blend of ''transmitter'' and ''responder''.
In air navigation or radio frequency identification, a T ...
can also be used for animal identification. The transponders are better known as PIT (Passive Integrated Transponder) tags, passive RFID, or "chips
''CHiPs'' is an American crime drama television series created by Rick Rosner and originally aired on NBC from September 15, 1977, to May 1, 1983. It follows the lives of two motorcycle officers of the California Highway Patrol (CHP). The serie ...
" on animals. ThCanadian Cattle Identification Agency
began using RFID tags as a replacement for barcode tags. Currently CCIA tags are used in
Wisconsin
Wisconsin () is a state in the upper Midwestern United States. Wisconsin is the 25th-largest state by total area and the 20th-most populous. It is bordered by Minnesota to the west, Iowa to the southwest, Illinois to the south, Lake M ...
and by United States farmers on a voluntary basis. The USDA
The United States Department of Agriculture (USDA) is the federal executive department responsible for developing and executing federal laws related to farming, forestry, rural economic development, and food. It aims to meet the needs of com ...
is currently developing its own program.
RFID tags are required for all cattle sold in Australia and in some states, sheep and goats as well.
Human implantation
Biocompatible
Biocompatibility is related to the behavior of biomaterials in various contexts. The term refers to the ability of a material to perform with an appropriate host response in a specific situation. The ambiguity of the term reflects the ongoing de ...
microchip implants that use RFID technology are being routinely implanted in humans. The first-ever human to receive an RFID microchip implant was American artist Eduardo Kac
Eduardo Kac �dwardoʊ kæts; ĕd·wâr′·dō kăts(1962) is a contemporary artist of dual nationality (American and Brazilian) whose artworks span a wide range of practices, including performance art, poetry, holography, interactive art, digital ...
in 1997. Kac implanted the microchip live on television (and also live on the Internet) in the context of his artwork ''Time Capsule''.
A year later, British professor of cybernetics
Cybernetics is a wide-ranging field concerned with circular causality, such as feedback, in regulatory and purposive systems. Cybernetics is named after an example of circular causal feedback, that of steering a ship, where the helmsperson m ...
Kevin Warwick
Kevin Warwick (born 9 February 1954) is an English engineer and Deputy Vice-Chancellor (Research) at Coventry University. He is known for his studies on direct interfaces between computer systems and the human nervous system, and has also done ...
had an RFID chip implanted in his arm by his general practitioner, George Boulos. In 2004 the ' Baja Beach Clubs' operated by Conrad Chase
Conrad Keven Chase (born June 9, 1965 in Portland, Maine) is an actor, singer/songwriter and public speaker.
History
Conrad participated in Spain's '' Gran Hermano'' (Big Brother). He was also a member of a Dutch boy band known as the Baja Boy ...
in Barcelona
Barcelona ( , , ) is a city on the coast of northeastern Spain. It is the capital and largest city of the autonomous community of Catalonia, as well as the second most populous municipality of Spain. With a population of 1.6 million within ci ...
and Rotterdam
Rotterdam ( , , , lit. ''The Dam on the River Rotte'') is the second largest city and municipality in the Netherlands. It is in the province of South Holland, part of the North Sea mouth of the Rhine–Meuse–Scheldt delta, via the ''"N ...
offered implanted chips to identify their VIP customers, who could in turn use it to pay for service. In 2009 British scientist Mark Gasson
Mark N. Gasson is a British scientist and visiting research fellow at the Cybernetics Research Group, University of Reading, UK. He pioneered developments in direct neural interfaces between computer systems and the human nervous system, has devel ...
had an advanced glass capsule RFID device surgically implanted into his left hand and subsequently demonstrated how a computer virus could wirelessly infect his implant and then be transmitted on to other systems.
The Food and Drug Administration
The United States Food and Drug Administration (FDA or US FDA) is a List of United States federal agencies, federal agency of the United States Department of Health and Human Services, Department of Health and Human Services. The FDA is respon ...
in the United States approved the use of RFID chips in humans in 2004.
There is controversy regarding human applications of implantable RFID technology including concerns that individuals could potentially be tracked by carrying an identifier unique to them. Privacy advocates have protested against implantable RFID chips, warning of potential abuse. Some are concerned this could lead to abuse by an authoritarian government, to removal of freedoms, and to the emergence of an "ultimate panopticon
The panopticon is a type of institutional building and a system of control designed by the English philosopher and social theorist Jeremy Bentham in the 18th century. The concept of the design is to allow all prisoners of an institution to be o ...
", a society where all citizens behave in a socially accepted manner because others might be watching.
On July 22, 2006, Reuters reported that two hackers, Newitz and Westhues, at a conference in New York City demonstrated that they could clone the RFID signal from a human implanted RFID chip, indicating that the device was not as secure as was previously claimed.
Institutions
Hospitals and healthcare
Adoption of RFID in the medical industry has been widespread and very effective. Hospitals are among the first users to combine both active and passive RFID. Active tags track high-value, or frequently moved items, and passive tags track smaller, lower cost items that only need room-level identification. Medical facility rooms can collect data from transmissions of RFID badges worn by patients and employees, as well as from tags assigned to items such as mobile medical devices. The U.S. Department of Veterans Affairs (VA) recently announced plans to deploy RFID in hospitals across America to improve care and reduce costs. Since 2004 a number of U.S. hospitals have begun implanting patients with RFID tags and using RFID systems, usually for workflow and inventory management. The use of RFID to prevent mix-ups betweensperm
Sperm is the male reproductive cell, or gamete, in anisogamous forms of sexual reproduction (forms in which there is a larger, female reproductive cell and a smaller, male one). Animals produce motile sperm with a tail known as a flagellum, whi ...
and ova
, abbreviated as OVA and sometimes as OAV (original animation video), are Japanese animated films and series made specially for release in home video formats without prior showings on television or in theaters, though the first part of an OVA s ...
in IVF
In vitro fertilisation (IVF) is a process of fertilisation where an egg is combined with sperm in vitro ("in glass"). The process involves monitoring and stimulating an individual's ovulatory process, removing an ovum or ova (egg or eggs) f ...
clinics is also being considered.
In October 2004, the FDA approved the USA's first RFID chips that can be implanted in humans. The 134 kHz RFID chips, from VeriChip Corp. can incorporate personal medical information and could save lives and limit injuries from errors in medical treatments, according to the company. Anti-RFID activists Katherine Albrecht
Katherine Albrecht is a consumer privacy advocate , Vice President (VP) of Startpage.com and spokesperson against radio-frequency identification (RFID). Albrecht devised the term " spy chips" to describe RFID tags such as those embedded in passpo ...
and Liz McIntyre discovered an FDA Warning Letter An FDA warning letter is an official message from the United States Food and Drug Administration (FDA) to a manufacturer or other organization that has violated some rule in a federally regulated activity.
The FDA defines an FDA warning letter as: ...
that spelled out health risks. According to the FDA, these include "adverse tissue reaction", "migration of the implanted transponder", "failure of implanted transponder", "electrical hazards" and "magnetic resonance imaging RIincompatibility."
Libraries
Libraries have used RFID to replace the barcodes on library items. The tag can contain identifying information or may just be a key into a database. An RFID system may replace or supplement bar codes and may offer another method of inventory management and self-service checkout by patrons. It can also act as asecurity
Security is protection from, or resilience against, potential harm (or other unwanted coercive change) caused by others, by restraining the freedom of others to act. Beneficiaries (technically referents) of security may be of persons and social ...
device, taking the place of the more traditional electromagnetic security strip.
It is estimated that over 30 million library items worldwide now contain RFID tags, including some in the Vatican Library
The Vatican Apostolic Library ( la, Bibliotheca Apostolica Vaticana, it, Biblioteca Apostolica Vaticana), more commonly known as the Vatican Library or informally as the Vat, is the library of the Holy See, located in Vatican City. Formally es ...
in Rome
, established_title = Founded
, established_date = 753 BC
, founder = King Romulus (legendary)
, image_map = Map of comune of Rome (metropolitan city of Capital Rome, region Lazio, Italy).svg
, map_caption ...
.
Since RFID tags can be read through an item, there is no need to open a book cover or DVD case to scan an item, and a stack of books can be read simultaneously. Book tags can be read while books are in motion on a conveyor belt
A conveyor belt is the carrying medium of a belt conveyor system (often shortened to belt conveyor). A belt conveyor system is one of many types of conveyor systems. A belt conveyor system consists of two or more pulleys (sometimes referred to ...
, which reduces staff time. This can all be done by the borrowers themselves, reducing the need for library staff assistance. With portable readers, inventories could be done on a whole shelf of materials within seconds.
However, as of 2008 this technology remained too costly for many smaller libraries, and the conversion period has been estimated at 11 months for an average-size library. A 2004 Dutch estimate was that a library which lends 100,000 books per year should plan on a cost of €50,000 (borrow- and return-stations: 12,500 each, detection porches 10,000 each; tags 0.36 each). RFID taking a large burden off staff could also mean that fewer staff will be needed, resulting in some of them getting laid off, but that has so far not happened in North America where recent surveys have not returned a single library that cut staff because of adding RFID. In fact, library budgets are being reduced for personnel and increased for infrastructure, making it necessary for libraries to add automation to compensate for the reduced staff size. Also, the tasks that RFID takes over are largely not the primary tasks of librarians. A finding in the Netherlands is that borrowers are pleased with the fact that staff are now more available for answering questions.
Privacy concerns have been raised surrounding library use of RFID. Because some RFID tags can be read up to away, there is some concern over whether sensitive information could be collected from an unwilling source. However, library RFID tags do not contain any patron information, and the tags used in the majority of libraries use a frequency only readable from approximately . Another concern is that a non-library agency could potentially record the RFID tags of every person leaving the library without the library administrator's knowledge or consent. One simple option is to let the book transmit a code that has meaning only in conjunction with the library's database. Another possible enhancement would be to give each book a new code every time it is returned. In future, should readers become ubiquitous (and possibly networked), then stolen books could be traced even outside the library. Tag removal could be made difficult if the tags are so small that they fit invisibly inside a (random) page, possibly put there by the publisher.
Museums
RFID technologies are now also implemented in end-user applications in museums. An example was the custom-designed temporary research application, "eXspot", at theExploratorium
The Exploratorium is a museum of science, technology, and arts in San Francisco, California. Characterized as "a mad scientist's penny arcade, a scientific funhouse, and an experimental laboratory all rolled into one", the participatory natur ...
, a science museum in San Francisco, California
San Francisco (; Spanish for " Saint Francis"), officially the City and County of San Francisco, is the commercial, financial, and cultural center of Northern California. The city proper is the fourth most populous in California and 17th ...
. A visitor entering the museum received an RF tag that could be carried as a card. The eXspot system enabled the visitor to receive information about specific exhibits. Aside from the exhibit information, the visitor could take photographs of themselves at the exhibit. It was also intended to allow the visitor to take data for later analysis. The collected information could be retrieved at home from a "personalized" website keyed to the RFID tag.
Schools and universities
In 2004, school authorities in the Japanese city ofOsaka
is a designated city in the Kansai region of Honshu in Japan. It is the capital of and most populous city in Osaka Prefecture, and the third most populous city in Japan, following Special wards of Tokyo and Yokohama. With a population of 2. ...
made a decision to start chipping children's clothing, backpacks, and student IDs in a primary school. Later, in 2007, a school in Doncaster
Doncaster (, ) is a city in South Yorkshire, England. Named after the River Don, it is the administrative centre of the larger City of Doncaster. It is the second largest settlement in South Yorkshire after Sheffield. Doncaster is situated in ...
, England, is piloting a monitoring system designed to keep tabs on pupils by tracking radio chips in their uniforms. St Charles Sixth Form College in west London
London is the capital and largest city of England and the United Kingdom, with a population of just under 9 million. It stands on the River Thames in south-east England at the head of a estuary down to the North Sea, and has been a majo ...
, England, started in 2008, uses an RFID card system to check in and out of the main gate, to both track attendance and prevent unauthorized entrance. Similarly, Whitcliffe Mount School in Cleckheaton
Cleckheaton is a town in the Metropolitan borough of Kirklees, in West Yorkshire, England. Historically part of the West Riding of Yorkshire, it is situated south of Bradford, east of Brighouse, west of Batley and south-west of Leeds. It is a ...
, England, uses RFID to track pupils and staff in and out of the building via a specially designed card. In the Philippines, during 2012, some schools already use RFID in IDs for borrowing books. Gates in those particular schools also have RFID scanners for buying items at school shops and canteens. RFID is also used in school libraries, and to sign in and out for student and teacher attendance.
Sports
 RFID for timing races began in the early 1990s with pigeon racing, introduced by the company Deister Electronics in Germany. RFID can provide race start and end timings for individuals in large races where it is impossible to get accurate stopwatch readings for every entrant.
In races utilizing RFID, racers wear tags that are read by antennas placed alongside the track or on mats across the track. UHF tags provide accurate readings with specially designed antennas. Rush error, lap count errors and accidents at race start are avoided, as anyone can start and finish at any time without being in a batch mode.
RFID for timing races began in the early 1990s with pigeon racing, introduced by the company Deister Electronics in Germany. RFID can provide race start and end timings for individuals in large races where it is impossible to get accurate stopwatch readings for every entrant.
In races utilizing RFID, racers wear tags that are read by antennas placed alongside the track or on mats across the track. UHF tags provide accurate readings with specially designed antennas. Rush error, lap count errors and accidents at race start are avoided, as anyone can start and finish at any time without being in a batch mode.
Orienteering
Orienteering is a group of sports that require navigational skills using a map and compass to navigate from point to point in diverse and usually unfamiliar terrain whilst moving at speed. Participants are given a topographical map, usually a s ...
, Enduro
Enduro is a form of motorcycle sport run on extended cross-country, off-road courses. Enduro consists of many different obstacles and challenges. The main type of enduro event, and the format to which the World Enduro Championship is run, is a ...
and Hare and Hounds racing. Riders have a transponder on their person, normally on their arm. When they complete a lap they swipe or touch the receiver which is connected to a computer and log their lap time.
RFID is being adapted by many recruitment agencies which have a PET (physical endurance test) as their qualifying procedure, especially in cases where the candidate volumes may run into millions (Indian Railway recruitment cells, police and power sector).
A number of ski resort
A ski resort is a resort developed for skiing, snowboarding, and other winter sports. In Europe, most ski resorts are towns or villages in or adjacent to a ski area – a mountainous area with pistes (ski trails) and a ski lift system. In North ...
s have adopted RFID tags to provide skiers hands-free access to ski lift
A ski lift is a mechanism for transporting skiers up a hill. Ski lifts are typically a paid service at ski resorts. The first ski lift was built in 1908 by German Robert Winterhalder in Schollach/Eisenbach, Hochschwarzwald.
Types
* Aerial l ...
s. Skiers do not have to take their passes out of their pockets. Ski jackets have a left pocket into which the chip+card fits. This nearly contacts the sensor unit on the left of the turnstile as the skier pushes through to the lift. These systems were based on high frequency (HF) at 13.56 megahertz. The bulk of ski areas in Europe, from Verbier to Chamonix, use these systems.
The NFL in the United States equips players with RFID chips that measures speed, distance and direction traveled by each player in real-time. Currently cameras stay focused on the quarterback
The quarterback (commonly abbreviated "QB"), colloquially known as the "signal caller", is a position in gridiron football. Quarterbacks are members of the offensive platoon and mostly line up directly behind the offensive line. In modern Ame ...
; however, numerous plays are happening simultaneously on the field. The RFID chip will provide new insight into these simultaneous plays. The chip triangulates the player's position within six inches and will be used to digitally broadcast
Broadcasting is the distribution of audio or video content to a dispersed audience via any electronic mass communications medium, but typically one using the electromagnetic spectrum ( radio waves), in a one-to-many model. Broadcasting began ...
replays. The RFID chip will make individual player information accessible to the public. The data will be available via the NFL 2015 app. The RFID chips are manufactured by Zebra Technologies
Zebra Technologies Corporation is an American mobile computing company specializing in technology used to sense, analyze, and act in real time. The company manufactures and sells marking, tracking, and computer printing technologies. Its product ...
. Zebra Technologies tested the RFID chip in 18 stadiums last year to track vector data.
Complement to barcode
RFID tags are often a complement, but not a substitute, forUniversal Product Code
The Universal Product Code (UPC or UPC code) is a barcode symbology that is widely used worldwide for tracking trade items in stores.
UPC (technically refers to UPC-A) consists of 12 digits that are uniquely assigned to each trade item. Along w ...
(UPC) or European Article Number
The International Article Number (also known as European Article Number or EAN) is a standard describing a barcode symbology and numbering system used in global trade to identify a specific retail product type, in a specific packaging configurat ...
(EAN) barcodes. They may never completely replace barcodes, due in part to their higher cost and the advantage of multiple data sources on the same object. Also, unlike RFID labels, barcodes can be generated and distributed electronically by e-mail or mobile phone, for printing or display by the recipient. An example is airline boarding passes. The new EPC, along with several other schemes, is widely available at reasonable cost.
The storage of data associated with tracking items will require many terabyte
The byte is a units of information, unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character (computing), character of text in a computer and for this ...
s. Filtering and categorizing RFID data is needed to create useful information. It is likely that goods will be tracked by the pallet using RFID tags, and at package level with UPC or EAN from unique barcodes.
The unique identity is a mandatory requirement for RFID tags, despite special choice of the numbering scheme. RFID tag data capacity is large enough that each individual tag will have a unique code, while current barcodes are limited to a single type code for a particular product. The uniqueness of RFID tags means that a product may be tracked as it moves from location to location while being delivered to a person. This may help to combat theft and other forms of product loss. The tracing of products is an important feature that is well supported with RFID tags containing a unique identity of the tag and the serial number of the object. This may help companies cope with quality deficiencies and resulting recall campaigns, but also contributes to concern about tracking and profiling of persons after the sale.
Waste management
Since around 2007 there been increasing development in the use of RFID in thewaste management
Waste management or waste disposal includes the processes and actions required to manage waste from its inception to its final disposal.
This includes the collection, transport, treatment and disposal of waste, together with monitoring ...
industry. RFID tags are installed on waste collection carts, linking carts to the owner's account for easy billing and service verification. The tag is embedded into a garbage and recycle container, and the RFID reader is affixed to the garbage and recycle trucks. RFID also measures a customer's set-out rate and provides insight as to the number of carts serviced by each waste collection vehicle. This RFID process replaces traditional "pay as you throw
Pay as you throw (PAYT) (also called trash metering, unit pricing, variable rate pricing, or user-pay) is a usage-pricing model for disposing of municipal solid waste. Users are charged a rate based on how much waste they present for collection to ...
" (PAYT) municipal solid waste
Municipal solid waste (MSW), commonly known as trash or garbage in the United States and rubbish in Britain, is a waste type consisting of everyday items that are discarded by the public. "Garbage" can also refer specifically to food waste, ...
usage-pricing models.
Telemetry
Active RFID tags have the potential to function as low-cost remote sensors that broadcasttelemetry
Telemetry is the in situ data collection, collection of measurements or other data at remote points and their automatic data transmission, transmission to receiving equipment (telecommunication) for monitoring. The word is derived from the Gr ...
back to a base station. Applications of tagometry data could include sensing of road conditions by implanted beacons
A beacon is an intentionally conspicuous device designed to attract attention to a specific location. A common example is the lighthouse, which draws attention to a fixed point that can be used to navigate around obstacles or into port. More mod ...
, weather reports, and noise level monitoring.
Passive RFID tags can also report sensor data. For example, the Wireless Identification and Sensing Platform is a passive tag that reports temperature, acceleration and capacitance to commercial Gen2 RFID readers.
It is possible that active or battery-assisted passive (BAP) RFID tags could broadcast a signal to an in-store receiver to determine whether the RFID tag – and by extension, the product it is attached to – is in the store.
Regulation and standardization
To avoid injuries to humans and animals, RF transmission needs to be controlled. A number of organizations have set standards for RFID, including theInternational Organization for Standardization
The International Organization for Standardization (ISO ) is an international standard development organization composed of representatives from the national standards organizations of member countries. Membership requirements are given in Ar ...
(ISO), the International Electrotechnical Commission
The International Electrotechnical Commission (IEC; in French: ''Commission électrotechnique internationale'') is an international standards organization that prepares and publishes international standards for all electrical, electronic and r ...
(IEC), ASTM International
ASTM International, formerly known as American Society for Testing and Materials, is an international standards organization that develops and publishes voluntary consensus technical standards for a wide range of materials, products, systems, an ...
, the DASH7
DASH7 Alliance Protocol (D7A) is an open-source wireless sensor and actuator network protocol, which operates in the 433 MHz, 868 MHz and 915 MHz unlicensed ISM band/SRD band. DASH7 provides multi-year battery life, range of up to ...
Alliance and EPCglobal
The Electronic Product Code (EPC) is designed as a universal identifier (using a idiosyncratic numerical code for each different commodity) that provides a unique identity for every physical object anywhere in the world, for all time. The EPC stru ...
.
Several specific industries have also set guidelines, including the Financial Services Technology Consortium (FSTC) for tracking IT Assets with RFID, the Computer Technology Industry Association CompTIA
The Computing Technology Industry Association (CompTIA) is an American non-profit trade association that issues professional certifications for the information technology (IT) industry. It is considered one of the IT industry's top trade associ ...
for certifying RFID engineers, and the International Air Transport Association
The International Air Transport Association (IATA ) is a trade association of the world's airlines founded in 1945. IATA has been described as a cartel since, in addition to setting technical standards for airlines, IATA also organized tariff ...
(IATA) for luggage in airports.
Every country can set its own rules for frequency allocation
Frequency allocation (or spectrum allocation or spectrum management) is the allocation and regulation of the electromagnetic spectrum into radio frequency bands, normally done by governments in most countries. Because radio propagation does no ...
for RFID tags, and not all radio bands are available in all countries. These frequencies are known as the ISM band
The ISM radio bands are portions of the radio spectrum reserved internationally for industrial, scientific and medical (ISM) purposes, excluding applications in telecommunications.
Examples of applications for the use of radio frequency (RF) ener ...
s (Industrial Scientific and Medical bands). The return signal of the tag may still cause interference
Interference is the act of interfering, invading, or poaching. Interference may also refer to:
Communications
* Interference (communication), anything which alters, modifies, or disrupts a message
* Adjacent-channel interference, caused by extr ...
for other radio users.
* Low-frequency (LF: 125–134.2 kHz and 140–148.5 kHz) (LowFID) tags and high-frequency (HF: 13.56 MHz) (HighFID) tags can be used globally without a license.
* Ultra-high-frequency (UHF: 865–928 MHz) (Ultra-HighFID or UHFID) tags cannot be used globally as there is no single global standard, and regulations differ from country to country.
In North America, UHF can be used unlicensed for 902–928 MHz (±13 MHz from the 915 MHz center frequency), but restrictions exist for transmission power. In Europe, RFID and other low-power radio applications are regulated by ETSI
The European Telecommunications Standards Institute (ETSI) is an independent, not-for-profit, standardization organization in the field of information and communications. ETSI supports the development and testing of global technical standard ...
recommendations EN 300 220
En or EN may refer to:
Businesses
* Bouygues (stock symbol EN)
* Esquimalt and Nanaimo Railway (reporting mark EN, but now known as Southern Railway of Vancouver Island)
* Euronews, a news television and internet channel
Language and writing
* ...
and EN 302 208
En or EN may refer to:
Businesses
* Bouygues (stock symbol EN)
* Esquimalt and Nanaimo Railway (reporting mark EN, but now known as Southern Railway of Vancouver Island)
* Euronews, a news television and internet channel
Language and writing
* ...
, and ERO
''Ero'' is a genus of pirate spiders first described in 1836. They resemble comb-footed spiders due to their globular abdomen, which is higher than it is long.
Description
The upper side of their abdomen bears one or two pairs of conical tu ...
recommendation 70 03, allowing RFID operation with somewhat complex band restrictions from 865–868 MHz. Readers are required to monitor a channel before transmitting ("Listen Before Talk"); this requirement has led to some restrictions on performance, the resolution of which is a subject of current research. The North American UHF standard is not accepted in France as it interferes with its military bands. On July 25, 2012, Japan changed its UHF band to 920 MHz, more closely matching the United States' 915 MHz band, establishing an international standard environment for RFID.
In some countries, a site license is needed, which needs to be applied for at the local authorities, and can be revoked.
As of 31 October 2014, regulations are in place in 78 countries representing approximately 96.5% of the world's GDP, and work on regulations was in progress in three countries representing approximately 1% of the world's GDP.
Standards Standard may refer to:
Symbols
* Colours, standards and guidons, kinds of military signs
* Standard (emblem), a type of a large symbol or emblem used for identification
Norms, conventions or requirements
* Standard (metrology), an object th ...
that have been made regarding RFID include:
* ISO 11784/11785 – Animal identification. Uses 134.2 kHz.
* ISO 14223 ISO 14223 '' identification of animals — Advanced transponders'' is an international standard that specifies the structure of the radio frequency (RF) code for advanced transponders for animals. The technical concept of advanced transponders ...
– Radiofrequency identification of animals – Advanced transponders
* ISO/IEC 14443
ISO/IEC 14443 ''Identification cards -- Contactless integrated circuit cards -- Proximity cards'' is an international standard that defines proximity cards used for identification, and the transmission protocols for communicating with it.
Standa ...
: This standard is a popular HF (13.56 MHz) standard for HighFIDs which is being used as the basis of RFID-enabled passports under ICAO 9303. The Near Field Communication
Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of 4 cm (1 in) or less. NFC offers a low-speed connection through a simple setup that can be u ...
standard that lets mobile devices act as RFID readers/transponders is also based on ISO/IEC 14443.
* ISO/IEC 15693
ISO/IEC 15693, is an ISO/ IEC standard for ''vicinity cards'', i.e. cards which can be read from a greater distance as compared with proximity cards. Such cards can normally be read out by a reader without being powered themselves, as the reader ...
: This is also a popular HF (13.56 MHz) standard for HighFIDs widely used for non-contact smart payment
Smart or SMART may refer to:
Arts and entertainment
* Smart (Hey! Say! JUMP album), ''Smart'' (Hey! Say! JUMP album), 2014
* Smart (Hotels.com), former mascot of Hotels.com
* Smart (Sleeper album), ''Smart'' (Sleeper album), 1995 debut album b ...
and credit cards.
* ISO/IEC 18000
This is a list of publishedThis list generally excludes draft versions. International Organization for Standardization (ISO) standards and other deliverables.
: Information technology—Radio frequency identification for item management:
* ISO/IEC 18092 Information technology—Telecommunications and information exchange between systems—Near Field Communication—Interface and Protocol (NFCIP-1)
* ISO 18185
ISO is the most common abbreviation for the International Organization for Standardization.
ISO or Iso may also refer to: Business and finance
* Iso (supermarket), a chain of Danish supermarkets incorporated into the SuperBest chain in 2007
* Iso ...
: This is the industry standard for electronic seals or "e-seals" for tracking cargo containers using the 433 MHz and 2.4 GHz frequencies.
* ISO/IEC 21481 Information technology—Telecommunications and information exchange between systems—Near Field Communication Interface and Protocol −2 (NFCIP-2)
* ASTM
ASTM International, formerly known as American Society for Testing and Materials, is an international standards organization that develops and publishes voluntary consensus technical standards for a wide range of materials, products, systems, an ...
D7434, Standard Test Method for Determining the Performance of Passive Radio Frequency Identification (RFID) Transponders on Palletized or Unitized Loads
* ASTM
ASTM International, formerly known as American Society for Testing and Materials, is an international standards organization that develops and publishes voluntary consensus technical standards for a wide range of materials, products, systems, an ...
D7435, Standard Test Method for Determining the Performance of Passive Radio Frequency Identification (RFID) Transponders on Loaded Containers
* ASTM
ASTM International, formerly known as American Society for Testing and Materials, is an international standards organization that develops and publishes voluntary consensus technical standards for a wide range of materials, products, systems, an ...
D7580, Standard Test Method for Rotary Stretch Wrapper Method for Determining the Readability of Passive RFID Transponders on Homogenous Palletized or Unitized Loads
* ISO 28560-2— specifies encoding standards and data model to be used within libraries.
In order to ensure global interoperability of products, several organizations have set up additional standards for RFID testing. These standards include conformance, performance and interoperability tests.
EPC Gen2
EPC Gen2 is short for ''EPCglobal UHF Class 1 Generation 2''.EPCglobal
The Electronic Product Code (EPC) is designed as a universal identifier (using a idiosyncratic numerical code for each different commodity) that provides a unique identity for every physical object anywhere in the world, for all time. The EPC stru ...
, a joint venture between GS1 and GS1 US, is working on international standards for the use of mostly passive RFID and the Electronic Product Code
The Electronic Product Code (EPC) is designed as a universal identifier (using a idiosyncratic numerical code for each different commodity) that provides a unique identity for every physical object anywhere in the world, for all time. The EPC stru ...
(EPC) in the identification of many items in the supply chain
In commerce, a supply chain is a network of facilities that procure raw materials, transform them into intermediate goods and then final products to customers through a distribution system. It refers to the network of organizations, people, acti ...
for companies worldwide.
One of the missions of EPCglobal was to simplify the Babel of protocols prevalent in the RFID world in the 1990s. Two tag air interfaces (the protocol for exchanging information between a tag and a reader) were defined (but not ratified) by EPCglobal prior to 2003. These protocols, commonly known as Class 0 and Class 1, saw significant commercial implementation in 2002–2005.
In 2004, the Hardware Action Group created a new protocol, the Class 1 Generation 2 interface, which addressed a number of problems that had been experienced with Class 0 and Class 1 tags. The EPC Gen2 standard was approved in December 2004. This was approved after a contention from Intermec
Intermec is a manufacturer and supplier of automated identification and data capture equipment, including barcode scanners, barcode printers, mobile computers, RFID systems, voice recognition systems, and life cycle services.
Intermec holds pate ...
that the standard may infringe a number of their RFID-related patents. It was decided that the standard itself does not infringe their patents, making the standard royalty free. The EPC Gen2 standard was adopted with minor modifications as ISO 18000-6C in 2006.
In 2007, the lowest cost of Gen2 EPC inlay was offered by the now-defunct company SmartCode, at a price of $0.05 apiece in volumes of 100 million or more.
Problems and concerns
Data flooding
Not every successful reading of a tag (an observation) is useful for business purposes. A large amount of data may be generated that is not useful for managing inventory or other applications. For example, a customer moving a product from one shelf to another, or a pallet load of articles that passes several readers while being moved in a warehouse, are events that do not produce data that are meaningful to an inventory control system. Event filtering is required to reduce this data inflow to a meaningful depiction of moving goods passing a threshold. Various concepts have been designed, mainly offered as ''middleware
Middleware is a type of computer software that provides services to software applications beyond those available from the operating system. It can be described as "software glue".
Middleware makes it easier for software developers to implement co ...
'' performing the filtering from noisy and redundant raw data to significant processed data.
Global standardization
The frequencies used for UHF RFID in the USA are as of 2007 incompatible with those of Europe or Japan. Furthermore, no emerging standard has yet become as universal as thebarcode
A barcode or bar code is a method of representing data in a visual, machine-readable form. Initially, barcodes represented data by varying the widths, spacings and sizes of parallel lines. These barcodes, now commonly referred to as linear or o ...
. To address international trade concerns, it is necessary to use a tag that is operational within all of the international frequency domains.
Security concerns
A primary RFID security concern is the illicit tracking of RFID tags. Tags, which are world-readable, pose a risk to both personal location privacy and corporate/military security. Such concerns have been raised with respect to theUnited States Department of Defense
The United States Department of Defense (DoD, USDOD or DOD) is an executive branch department of the federal government charged with coordinating and supervising all agencies and functions of the government directly related to national secu ...
's recent adoption of RFID tags for supply chain management
In commerce, supply chain management (SCM) is the management of the flow of goods and services including all processes that transform raw materials into final products between businesses and locations. This can include the movement and stor ...
. More generally, privacy organizations have expressed concerns in the context of ongoing efforts to embed electronic product code (EPC) RFID tags in general-use products. This is mostly as a result of the fact that RFID tags can be read, and legitimate transactions with readers can be eavesdropped on, from non-trivial distances. RFID used in access control, payment and eID (e-passport) systems operate at a shorter range than EPC RFID systems but are also vulnerable to skimming and eavesdropping, albeit at shorter distances.
A second method of prevention is by using cryptography. Rolling code
A rolling code (or sometimes called a hopping code) is used in keyless entry systems to prevent replay attacks, where an eavesdropper records the transmission and replays it at a later time to cause the receiver to 'unlock'. Such systems are typic ...
s and challenge–response authentication
In computer security, challenge–response authentication is a family of protocols in which one party presents a question ("challenge") and another party must provide a valid answer ("response") to be authenticated.
The simplest example of a ch ...
(CRA) are commonly used to foil monitor-repetition of the messages between the tag and reader, as any messages that have been recorded would prove to be unsuccessful on repeat transmission. Rolling codes rely upon the tag's ID being changed after each interrogation, while CRA uses software to ask for a cryptographic
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or '' -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adve ...
ally coded response from the tag. The protocols used during CRA can be symmetric
Symmetry (from grc, συμμετρία "agreement in dimensions, due proportion, arrangement") in everyday language refers to a sense of harmonious and beautiful proportion and balance. In mathematics, "symmetry" has a more precise definiti ...
, or may use public key cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic alg ...
.
While a variety of secure protocols have been suggested for RFID tags,
in order to support long read range at low cost, many RFID tags have barely enough power available
to support very low-power and therefore simple security protocols such as cover-coding.
Unauthorized reading of RFID tags presents a risk to privacy and to business secrecy. Unauthorized readers can potentially use RFID information to identify or track packages, persons, carriers, or the contents of a package. Several prototype systems are being developed to combat unauthorized reading, including RFID signal interruption, as well as the possibility of legislation, and 700 scientific papers have been published on this matter since 2002. There are also concerns that the database structure of Object Naming Service
Object may refer to:
General meanings
* Object (philosophy), a thing, being, or concept
** Object (abstract), an object which does not exist at any particular time or place
** Physical object, an identifiable collection of matter
* Goal, an ai ...
may be susceptible to infiltration, similar to denial-of-service attack
In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connect ...
s, after the EPCglobal Network ONS root servers were shown to be vulnerable.
Health
Microchip–induced tumours have been noted during animal trials.Shielding
In an effort to prevent the passive " skimming" of RFID-enabled cards or passports, the U.S.General Services Administration
The General Services Administration (GSA) is an independent agency of the United States government established in 1949 to help manage and support the basic functioning of federal agencies. GSA supplies products and communications for U.S. gover ...
(GSA) issued a set of test procedures for evaluating electromagnetically opaque sleeves. For shielding products to be in compliance with FIPS-201 guidelines, they must meet or exceed this published standard; compliant products are listed on the website of the U.S. CIO's FIPS-201 Evaluation Program. The United States government requires that when new ID cards are issued, they must be delivered with an approved shielding sleeve or holder. Although many wallets and passport holders are advertised to protect personal information, there is little evidence that RFID skimming is a serious threat; data encryption and use of EMV
EMV is a payment method based on a technical standard for smart payment cards and for payment terminals and automated teller machines which can accept them. EMV stands for " Europay, Mastercard, and Visa", the three companies that created th ...
chips rather than RFID makes this sort of theft rare.
There are contradictory opinions as to whether aluminum can prevent reading of RFID chips. Some people claim that aluminum shielding, essentially creating a Faraday cage
A Faraday cage or Faraday shield is an enclosure used to block electromagnetic fields. A Faraday shield may be formed by a continuous covering of conductive material, or in the case of a Faraday cage, by a mesh of such materials. Faraday cage ...
, does work. Others claim that simply wrapping an RFID card in aluminum foil only makes transmission more difficult and is not completely effective at preventing it.
Shielding effectiveness depends on the frequency being used. Low-frequency LowFID tags, like those used in implantable devices for humans and pets, are relatively resistant to shielding, although thick metal foil will prevent most reads. High frequency
High frequency (HF) is the ITU designation for the range of radio frequency electromagnetic waves (radio waves) between 3 and 30 megahertz (MHz). It is also known as the decameter band or decameter wave as its wavelengths range from one to ten ...
HighFID tags (13.56 MHz—smart card
A smart card, chip card, or integrated circuit card (ICC or IC card) is a physical electronic authentication device, used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) c ...
s and access badges) are sensitive to shielding and are difficult to read when within a few centimetres of a metal surface. UHF Ultra-HighFID tags (pallets and cartons) are difficult to read when placed within a few millimetres of a metal surface, although their read range is actually increased when they are spaced 2–4 cm from a metal surface due to positive reinforcement of the reflected wave and the incident wave at the tag.
Controversies
Privacy
The use of RFID has engendered considerable controversy and someconsumer privacy
Consumer privacy is information privacy as it relates to the consumers of products and services.
A variety of social, legal and political issues arise from the interaction of the public's potential expectation of privacy and the collection and di ...
advocates have initiated product boycott
A boycott is an act of nonviolent, voluntary abstention from a product, person, organization, or country as an expression of protest. It is usually for moral, social, political, or environmental reasons. The purpose of a boycott is to inflict som ...
s. Consumer privacy experts Katherine Albrecht
Katherine Albrecht is a consumer privacy advocate , Vice President (VP) of Startpage.com and spokesperson against radio-frequency identification (RFID). Albrecht devised the term " spy chips" to describe RFID tags such as those embedded in passpo ...
and Liz McIntyre are two prominent critics of the "spychip" technology. The two main privacy concerns regarding RFID are as follows:
* As the owner of an item may not necessarily be aware of the presence of an RFID tag and the tag can be read at a distance without the knowledge of the individual, sensitive data may be acquired without consent.
* If a tagged item is paid for by credit card or in conjunction with use of a loyalty card
A loyalty program is a marketing strategy designed to encourage customers to continue to shop at or use the services of a business associated with the program. Today, such programs cover most types of commerce, each having varying features and ...
, then it would be possible to indirectly deduce the identity of the purchaser by reading the globally unique ID of that item contained in the RFID tag. This is a possibility if the person watching also had access to the loyalty card and credit card data, and the person with the equipment knows where the purchaser is going to be.
Most concerns revolve around the fact that RFID tags affixed to products remain functional even after the products have been purchased and taken home and thus can be used for surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as c ...
and other purposes unrelated to their supply chain inventory functions.
The RFID Network responded to these fears in the first episode of their syndicated cable TV series, saying that they are unfounded, and let RF engineers demonstrate how RFID works. They provided images of RF engineers driving an RFID-enabled van around a building and trying to take an inventory of items inside. They also discussed satellite tracking of a passive RFID tag.
The concerns raised may be addressed in part by use of the Clipped Tag. The Clipped Tag is an RFID tag designed to increase privacy for the purchaser of an item. The Clipped Tag has been suggested by IBM researchers Paul Moskowitz and Guenter Karjoth. After the point of sale, a person may tear off a portion of the tag. This allows the transformation of a long-range tag into a proximity tag that still may be read, but only at short range – less than a few inches or centimeters. The modification of the tag may be confirmed visually. The tag may still be used later for returns, recalls, or recycling.
However, read range is a function of both the reader and the tag itself. Improvements in technology may increase read ranges for tags. Tags may be read at longer ranges than they are designed for by increasing reader power. The limit on read distance then becomes the signal-to-noise ratio of the signal reflected from the tag back to the reader. Researchers at two security conferences have demonstrated that passive Ultra-HighFID tags normally read at ranges of up to 30 feet can be read at ranges of 50 to 69 feet using suitable equipment.
In January 2004 privacy advocates from CASPIAN and the German privacy group FoeBuD were invited to the METRO Future Store in Germany, where an RFID pilot project was implemented. It was uncovered by accident that METRO "Payback" customer loyalty card
A loyalty program is a marketing strategy designed to encourage customers to continue to shop at or use the services of a business associated with the program. Today, such programs cover most types of commerce, each having varying features and ...
s contained RFID tags with customer IDs, a fact that was disclosed neither to customers receiving the cards, nor to this group of privacy advocates. This happened despite assurances by METRO that no customer identification data was tracked and all RFID usage was clearly disclosed.
During the UN World Summit on the Information Society
The World Summit on the Information Society (WSIS) was a two-phase United Nations-sponsored summit on information, communication and, in broad terms, the information society that took place in 2003 in Geneva and in 2005 in Tunis. WSIS Forums have ...
(WSIS) in November 2005, Richard Stallman
Richard Matthew Stallman (; born March 16, 1953), also known by his initials, rms, is an American free software movement activist and programmer. He campaigns for software to be distributed in such a manner that its users have the freedom to ...
, the founder of the free software movement
The free software movement is a social movement with the goal of obtaining and guaranteeing certain freedoms for software users, namely the freedoms to run the software, to study the software, to modify the software, and to share copies of the s ...
, protested the use of RFID security cards by covering his card with aluminum foil.
In 2004–2005 the Federal Trade Commission
The Federal Trade Commission (FTC) is an independent agency of the United States government whose principal mission is the enforcement of civil (non-criminal) antitrust law and the promotion of consumer protection. The FTC shares jurisdiction ov ...
staff conducted a workshop and review of RFID privacy concerns and issued a report recommending best practices.
RFID was one of the main topics of the 2006 Chaos Communication Congress
The Chaos Communication Congress is an annual conference organized by the Chaos Computer Club. The congress features a variety of lectures and workshops on technical and political issues related to security, cryptography, privacy and online ...
(organized by the Chaos Computer Club
The Chaos Computer Club (CCC) is Europe's largest association of hackers with 7,700 registered members. Founded in 1981, the association is incorporated as an ''eingetragener Verein'' in Germany, with local chapters (called ''Erfa-Kreise'') in ...
in Berlin
Berlin ( , ) is the capital and largest city of Germany by both area and population. Its 3.7 million inhabitants make it the European Union's most populous city, according to population within city limits. One of Germany's sixteen constitue ...
) and triggered a large press debate. Topics included electronic passports, Mifare cryptography and the tickets for the FIFA World Cup 2006. Talks showed how the first real-world mass application of RFID at the 2006 FIFA Football World Cup worked. The group monochrom
Monochrom (stylised as monochrom) is an international art-technology-philosophy group, publishing house and film production company. It was founded in 1993, and defines itself as "an unpeculiar mixture of proto-aesthetic fringe work, pop att ...
staged a "Hack RFID" song.
Government control
Some individuals have grown to fear the loss of rights due to RFID human implantation. By early 2007, Chris Paget of San Francisco, California, showed that RFID information could be pulled from aUS passport card
The United States passport card is an optional national identity card and a travel document issued by the U.S. federal government in the size of a credit card. Like a U.S. passport book, the passport card is only issued to U.S. nationals exclu ...
by using only $250 worth of equipment. This suggests that with the information captured, it would be possible to clone such cards.
According to ZDNet, critics believe that RFID will lead to tracking individuals' every movement and will be an invasion of privacy. In the book ''SpyChips: How Major Corporations and Government Plan to Track Your Every Move'' by Katherine Albrecht
Katherine Albrecht is a consumer privacy advocate , Vice President (VP) of Startpage.com and spokesperson against radio-frequency identification (RFID). Albrecht devised the term " spy chips" to describe RFID tags such as those embedded in passpo ...
and Liz McIntyre, one is encouraged to "imagine a world of no privacy. Where your every purchase is monitored and recorded in a database and your every belonging is numbered. Where someone many states away or perhaps in another country has a record of everything you have ever bought. What's more, they can be tracked and monitored remotely".
Deliberate destruction in clothing and other items
According to an RSA laboratories FAQ, RFID tags can be destroyed by a standard microwave oven; however, some types of RFID tags, particularly those constructed to radiate using large metallic antennas (in particular RF tags and EPC tags), may catch fire if subjected to this process for too long (as would any metallic item inside a microwave oven). This simple method cannot safely be used to deactivate RFID features in electronic devices, or those implanted in living tissue, because of the risk of damage to the "host". However the time required is extremely short (a second or two of radiation) and the method works in many other non-electronic and inanimate items, long before heat or fire become of concern. Some RFID tags implement a "kill command" mechanism to permanently and irreversibly disable them. This mechanism can be applied if the chip itself is trusted or the mechanism is known by the person that wants to "kill" the tag. UHF RFID tags that comply with the EPC2 Gen 2 Class 1 standard usually support this mechanism, while protecting the chip from being killed with a password. Guessing or cracking this needed 32-bit password for killing a tag would not be difficult for a determined attacker.See also
* AS5678 *Balise
A balise is an electronic beacon or transponder placed between the rails of a railway as part of an automatic train protection (ATP) system. The French word ''balise'' is used to distinguish these beacons from other kinds of beacons.
Balises a ...
* Bin bug
The term "bin bug" was coined in August 2006 by the British media to refer to the use of Radio Frequency Identification (RFID) chips by some local councils to monitor the amount of domestic waste created by each household. The system works by havi ...
* Campus card
A campus credential, more commonly known as a campus card or a campus ID card is an identification document certifying the status of students, faculty, staff or other constituents as members of the institutional community and eligible for access ...
* Chipless RFID Chipless RFID tags are RFID tags that do not require a microchip in the transponder.
RFIDs offer longer range and ability to be automated, unlike barcodes that require a human operator for interrogation. The main challenge to their adoption is the ...
* Internet of Things
The Internet of things (IoT) describes physical objects (or groups of such objects) with sensors, processing ability, software and other technologies that connect and exchange data with other devices and systems over the Internet or other comm ...
* Mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizati ...
* Microchip implant (human)
A human microchip implant is any electronic device implanted subcutaneously (subdermally) usually via an injection. Examples include an identifying integrated circuit RFID device encased in silicate glass which is implanted in the body of a human b ...
* Mobile RFID Mobile RFID (M-RFID) are services that provide information on objects equipped with an RFID tag over a telecommunication network. The reader or interrogator can be installed in a mobile device such as a mobile phone or PDA.
Unlike ordinary fixed R ...
* Near Field Communication
Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of 4 cm (1 in) or less. NFC offers a low-speed connection through a simple setup that can be u ...
(NFC)
* PositiveID
* Privacy by design
Privacy by design is an approach to systems engineering initially developed by Ann Cavoukian and formalized in a joint report on privacy-enhancing technologies by a joint team of the Information and Privacy Commissioner of Ontario (Canada), the ...
* Proximity card
A proximity card or prox card also known as a key card or keycard is a contactless smart card which can be read without inserting it into a reader device, as required by earlier magnetic stripe cards such as credit cards and contact type sma ...
* Resonant inductive coupling
Resonant inductive coupling or magnetic phase synchronous coupling is a phenomenon with inductive coupling where the coupling becomes stronger when the "secondary" (load-bearing) side of the loosely coupled coil resonates. A resonant transfo ...
* RFdump
RFdump is a software created by Lukas Grunwald and Christian Bottger for security auditing RFID tags. It is periodically updated to support emerging RFID standards such as e-passport and Mifare encryption that are currently found on many pay as y ...
* RFID in schools
* RFID Journal
RFID Journal is an independent media company devoted solely to radio frequency identification (RFID) and its business applications. A bi-monthly print publication and online news and information source, the journal offers news, features that addre ...
* RFID on metal RFID on metal (abbreviated to ROM) are radio-frequency identification (RFID) tags which perform a specific function when attached to metal objects. The ROM tags overcome some of the problems traditional RFID tags suffer when near metal, such as detu ...
* RSA blocker tag An RSA blocker tag (or RSA tag) is a RFID tag that responds positively to all unauthorized requests, thus blocking some scanners from reading any RFID tags placed nearby. The tags are designed to protect privacy, and are supposedly unable to be us ...
* Smart label
Smart Label, also called Smart Tag, is an extremely flat configured transponder under a conventional print-coded label, which includes chip, antenna and bonding wires as a so-called inlay. The labels, made of paper, fabric or plastics, are prepared ...
* Speedpass
Speedpass was a keychain radio-frequency identification (RFID) device introduced in 1997 by Mobil (which later merged with Exxon to become ExxonMobil in 1999) for electronic payment. It was originally developed by Verifone. By 2004, more than ...
* TecTile
TecTiles are a near field communication (NFC) application, developed by Samsung, for use with mobile smartphone devices.
Each TecTile is a low-cost self-adhesive sticker with an embedded NFC Tag. They are programmed before use, which can be don ...
* Tracking system
A tracking system, also known as a locating system, is used for the observing of persons or objects on the move and supplying a timely ordered sequence of location data for further processing. It is important to be aware of human tracking, fur ...
References
External links
An open source RFID library used as door opener
What is RFID? Educational video by The RFID Network
* *
What is RFID? – animated explanation
*
IEEE Council on RFID
{{Authority control Automatic identification and data capture Privacy Ubiquitous computing Wireless Radio frequency interfaces