|
RFdump
RFdump is a software created by Lukas Grunwald and Christian Bottger for security auditing RFID tags. It is periodically updated to support emerging RFID standards such as e-passport and Mifare encryption that are currently found on many pay as you go systems. RFDump is a back-end GPL tool to directly inter-operate with any RFID reader to make the contents stored on RFID tags accessible. The tool reads an RFID tag's meta information: tag ID, tag type, manufacturer etc. The user data of a tag can be displayed and modified using either a hex or an ASCII editor. The cookie feature demonstrates how simple it is to abuse RFID technology, such as company's using it to spy on consumers. RFDump works with the ACG Multi-Tag Reader or similar card reader hardware. RFDump features (Gtk application): * Runs on Linux, Windows * Supports ACGs PCMCIA/CF Multi-Tag Readers * Decodes the tag type, tag ID and manufacturer * Displays tag memory in hex and ASCII encoding * Allows to write memory usi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RFID
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods. Passive tags are powered by energy from the RFID reader's interrogating radio waves. Active tags are powered by a battery and thus can be read at a greater range from the RFID reader, up to hundreds of meters. Unlike a barcode, the tag does not need to be within the line of sight of the reader, so it may be embedded in the tracked object. RFID is one method of automatic identification and data capture (AIDC). RFID tags are used in many industries. For example, an RFID tag attached to an automobile during production can be used to track ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometric Passport
A biometric passport (also known as an e-passport or a digital passport) is a traditional passport that has an embedded electronic microprocessor chip which contains biometric information that can be used to authenticate the identity of the passport holder. It uses contactless smart card technology, including a microprocessor chip (computer chip) and antenna (for both power to the chip and communication) embedded in the front or back cover, or centre page, of the passport. The passport's critical information is printed on the data page of the passport, repeated on the machine readable lines and stored in the chip. Public key infrastructure (PKI) is used to authenticate the data stored electronically in the passport chip, making it expensive and difficult to forge when all security mechanisms are fully and correctly implemented. Many countries are moving towards issuing biometric passports to their citizens. Malaysia was the first country to issue biometric passports in 1998. I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
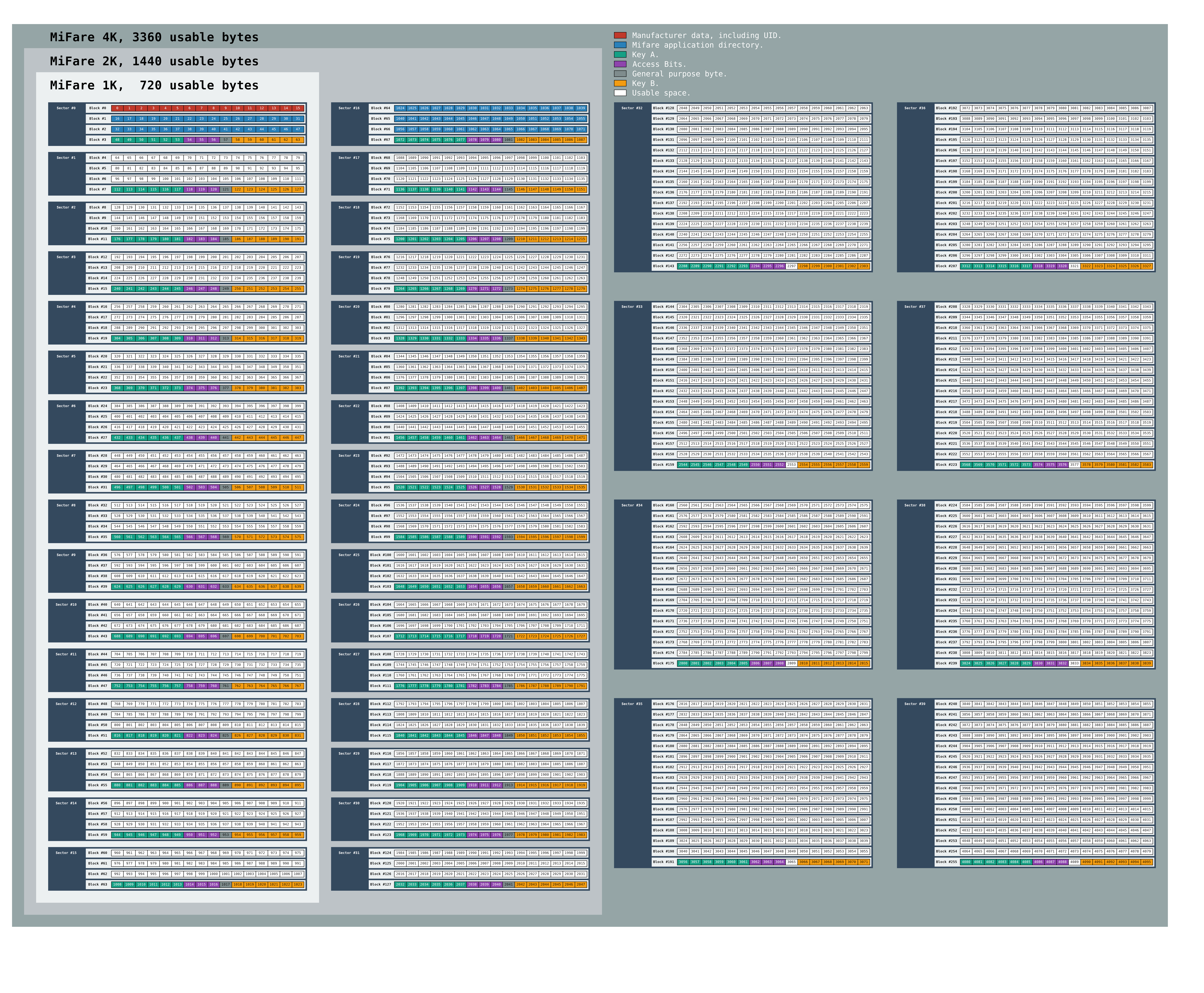
Mifare
MIFARE is the NXP Semiconductors-owned trademark of a series of integrated circuit (IC) chips used in contactless smart cards and proximity cards. The brand name covers proprietary solutions based upon various levels of the ISO/IEC 14443 Type A 13.56 MHz contactless smart card standard. It uses AES and DES/Triple-DES encryption standards, as well as an older proprietary encryption algorithm, Crypto-1. According to NXP, 10 billion of their smart card chips and over 150 million reader modules have been sold. MIFARE is owned by NXP Semiconductors, which was spun off from Philips Electronics in 2006. Variants MIFARE products are embedded in contactless and contact smart cards, smart paper tickets, wearables and phones. The MIFARE brand name (derived from the term MIKRON FARE Collection and created by the company Mikron) covers four families of contactless cards: ; MIFARE Classic: Employs a proprietary protocol compliant to parts 1–3 of ISO/IEC 14443 Type A, with an NXP ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hexadecimal
In mathematics and computing, the hexadecimal (also base-16 or simply hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. Unlike the decimal system representing numbers using 10 symbols, hexadecimal uses 16 distinct symbols, most often the symbols "0"–"9" to represent values 0 to 9, and "A"–"F" (or alternatively "a"–"f") to represent values from 10 to 15. Software developers and system designers widely use hexadecimal numbers because they provide a human-friendly representation of binary-coded values. Each hexadecimal digit represents four bits (binary digits), also known as a nibble (or nybble). For example, an 8-bit byte can have values ranging from 00000000 to 11111111 in binary form, which can be conveniently represented as 00 to FF in hexadecimal. In mathematics, a subscript is typically used to specify the base. For example, the decimal value would be expressed in hexadecimal as . In programming, a number of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ASCII
ASCII ( ), abbreviated from American Standard Code for Information Interchange, is a character encoding standard for electronic communication. ASCII codes represent text in computers, telecommunications equipment, and other devices. Because of technical limitations of computer systems at the time it was invented, ASCII has just 128 code points, of which only 95 are , which severely limited its scope. All modern computer systems instead use Unicode, which has millions of code points, but the first 128 of these are the same as the ASCII set. The Internet Assigned Numbers Authority (IANA) prefers the name US-ASCII for this character encoding. ASCII is one of the List of IEEE milestones, IEEE milestones. Overview ASCII was developed from telegraph code. Its first commercial use was as a seven-bit teleprinter code promoted by Bell data services. Work on the ASCII standard began in May 1961, with the first meeting of the American Standards Association's (ASA) (now the American Nat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTP Cookie
HTTP cookies (also called web cookies, Internet cookies, browser cookies, or simply cookies) are small blocks of data created by a web server while a user is browsing a website and placed on the user's computer or other device by the user's web browser. Cookies are placed on the device used to access a website, and more than one cookie may be placed on a user's device during a session. Cookies serve useful and sometimes essential functions on the web. They enable web servers to store stateful information (such as items added in the shopping cart in an online store) on the user's device or to track the user's browsing activity (including clicking particular buttons, logging in, or recording which pages were visited in the past). They can also be used to save for subsequent use information that the user previously entered into form fields, such as names, addresses, passwords, and payment card numbers. Authentication cookies are commonly used by web servers to authenticate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which includes the kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name "GNU/Linux" to emphasize the importance of GNU software, causing some controversy. Popular Linux distributions include Debian, Fedora Linux, and Ubuntu, the latter of which itself consists of many different distributions and modifications, including Lubuntu and Xubuntu. Commercial distributions include Red Hat Enterprise Linux and SUSE Linux Enterprise. Desktop Linux distributions include a windowing system such as X11 or Wayland, and a desktop environment such as GNOME or KDE Plasma. Distributions intended for ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Windows
Windows is a group of several proprietary graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for servers, and Windows IoT for embedded systems. Defunct Windows families include Windows 9x, Windows Mobile, and Windows Phone. The first version of Windows was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). Windows is the most popular desktop operating system in the world, with 75% market share , according to StatCounter. However, Windows is not the most used operating system when including both mobile and desktop OSes, due to Android's massive growth. , the most recent version of Windows is Windows 11 for consumer PCs and tablets, Windows 11 Enterprise for corporations, and Windows Server 2022 for servers. Genealogy By marketing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PCMCIA
The Personal Computer Memory Card International Association (PCMCIA) was a group of computer hardware manufacturers, operating under that name from 1989 to 2009. Starting with the PCMCIA card in 1990 (the name later simplified to ''PC Card''), it created various standards for peripheral interfaces designed for laptop computers. History The PCMCIA (Personal Computer Memory Card International Association) industry organization was based on the original initiative of the British mathematician and computer scientist Ian H. S. Cullimore, one of the founders of the Sunnyvale-based Poqet Computer Corporation, who was seeking to integrate some kind of memory card technology as storage medium into their early DOS-based palmtop PCs, when traditional floppy drives and harddisks were found to be too power-hungry and large to fit into their battery-powered handheld devices. When in July 1989, Poqet contacted Fujitsu for their existing but still non-standardized SRAM memory cards, and Intel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ISO/IEC 14443
ISO/IEC 14443 ''Identification cards -- Contactless integrated circuit cards -- Proximity cards'' is an international standard that defines proximity cards used for identification, and the transmission protocols for communicating with it. Standard The standard is developed by ISO/IEC JTC 1 (Joint Technical Committee 1) / SC 17 (Subcommittee 17) / WG 8 (Working Group 8). Parts * ISO/IEC 14443-1:2018 Part 1: Physical characteristics * ISO/IEC 14443-2:2016 Part 2: Radio frequency power and signal interface * ISO/IEC 14443-3:2018 Part 3: Initialization and anticollision * ISO/IEC 14443-4:2018 Part 4: Transmission protocol Types Cards may be Type A and Type B, both of which communicate via radio at 13.56 MHz (RFID HF). The main differences between these types concern modulation methods, coding schemes (Part 2) and protocol initialization procedures (Part 3). Both Type A and Type B cards use the same transmission protocol (described in Part 4). The transmission protocol sp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Brute-force Attack
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. Alternatively, the attacker can attempt to guess the key which is typically created from the password using a key derivation function. This is known as an exhaustive key search. A brute-force attack is a cryptanalytic attack that can, in theory, be used to attempt to decrypt any encrypted data (except for data encrypted in an information-theoretically secure manner). Such an attack might be used when it is not possible to take advantage of other weaknesses in an encryption system (if any exist) that would make the task easier. When password-guessing, this method is very fast when used to check all short passwords, but for longer passwords other methods such as the dictionary attack are used because a brute-force search ta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Baud
In telecommunication and electronics, baud (; symbol: Bd) is a common unit of measurement of symbol rate, which is one of the components that determine the speed of communication over a data channel. It is the unit for symbol rate or modulation rate in symbols per second or pulses per second. It is the number of distinct symbol changes (signalling events) made to the transmission medium per second in a digitally modulated signal or a bd rate line code. Baud is related to ''gross bit rate'', which can be expressed in bits per second. If there are precisely two symbols in the system (typically 0 and 1), then baud and bit per second (bit/s) are equivalent. Naming The baud unit is named after Émile Baudot, the inventor of the Baudot code for telegraphy, and is represented according to the rules for SI units. That is, the first letter of its symbol is uppercase (Bd), but when the unit is spelled out, it should be written in lowercase (baud) except when it begins a sentence. It ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)

