The reflected binary code (RBC), also known as reflected binary (RB) or Gray code after
Frank Gray, is an ordering of the
binary numeral system
A binary number is a number expressed in the base-2 numeral system or binary numeral system, a method of mathematical expression which uses only two symbols: typically "0" (zero) and "1" ( one).
The base-2 numeral system is a positional notatio ...
such that two successive values differ in only one
bit (binary digit).
For example, the representation of the decimal value "1" in binary would normally be "" and "2" would be "". In Gray code, these values are represented as "" and "". That way, incrementing a value from 1 to 2 requires only one bit to change, instead of two.
Gray codes are widely used to prevent spurious output from
electromechanical switches and to facilitate
error correction
In information theory and coding theory with applications in computer science and telecommunication, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communica ...
in digital communications such as
digital terrestrial television and some
cable TV
Cable television is a system of delivering television programming to consumers via radio frequency (RF) signals transmitted through coaxial cables, or in more recent systems, light pulses through fibre-optic cables. This contrasts with broadc ...
systems.
Motivation and name
Many devices indicate position by closing and opening switches. If that device uses
natural binary code
A binary number is a number expressed in the base-2 numeral system or binary numeral system, a method of mathematical expression which uses only two symbols: typically "0" (zero) and "1" ( one).
The base-2 numeral system is a positional notatio ...
s, positions 3 and 4 are next to each other but all three bits of the binary representation differ:
:
The problem with natural binary codes is that physical switches are not ideal: it is very unlikely that physical switches will change states exactly in synchrony. In the transition between the two states shown above, all three switches change state. In the brief period while all are changing, the switches will read some spurious position. Even without
keybounce, the transition might look like — — — . When the switches appear to be in position , the observer cannot tell if that is the "real" position 1, or a transitional state between two other positions. If the output feeds into a
sequential system, possibly via
combinational logic, then the sequential system may store a false value.
This problem can be solved by changing only one switch at a time, so there is never any ambiguity of position, resulting in codes assigning to each of a contiguous set of
integers, or to each member of a circular list, a word of symbols such that no two code words are identical and each two adjacent code words differ by exactly one symbol. These codes are also known as ''unit-distance'',
''single-distance'', ''single-step'', ''monostrophic''
or ''syncopic codes'',
in reference to the
Hamming distance of 1 between adjacent codes.

In principle, there can be more than one such code for a given word length, but the term Gray code was first applied to a particular
binary code for non-negative integers, the ''binary-reflected Gray code'', or BRGC.
Bell Labs researcher
George R. Stibitz
George Robert Stibitz (April 30, 1904 – January 31, 1995) was a Bell Labs researcher internationally recognized as one of the fathers of the modern digital computer. He was known for his work in the 1930s and 1940s on the realization of Boolea ...
described such a code in a 1941 patent application, granted in 1943.
introduced the term ''reflected binary code'' in his 1947 patent application, remarking that the code had "as yet no recognized name".
He derived the name from the fact that it "may be built up from the conventional binary code by a sort of reflection process".
In the standard encoding the least significant bit follows a repetitive pattern of 2 on, 2 off the next digit a pattern of 4 on, 4 off; the ''n''th least significant bit a pattern of 2
''n'' on 2
''n'' off. The four-bit version of this is shown below:


:
For decimal 15 the code rolls over to decimal 0 with only one switch change. This is called the cyclic or adjacency property of the code.
In modern
digital communications, Gray codes play an important role in
error correction
In information theory and coding theory with applications in computer science and telecommunication, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communica ...
. For example, in a
digital modulation scheme such as
QAM where data is typically transmitted in
symbols
A symbol is a mark, sign, or word that indicates, signifies, or is understood as representing an idea, object, or relationship. Symbols allow people to go beyond what is known or seen by creating linkages between otherwise very different conc ...
of 4 bits or more, the signal's
constellation diagram is arranged so that the bit patterns conveyed by adjacent constellation points differ by only one bit. By combining this with
forward error correction
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is ...
capable of correcting single-bit errors, it is possible for a receiver to correct any transmission errors that cause a constellation point to deviate into the area of an adjacent point. This makes the transmission system less susceptible to
noise.
Despite the fact that Stibitz described this code
before Gray, the reflected binary code was later named after Gray by others who used it. Two different 1953 patent applications use "Gray code" as an alternative name for the "reflected binary code";
one of those also lists "minimum error code" and "cyclic permutation code" among the names.
A 1954 patent application refers to "the Bell Telephone Gray code".
Other names include "cyclic binary code",
"cyclic progression code",
"cyclic permuting binary"
or "cyclic permuted binary" (CPB).
The Gray code was sometimes attributed, incorrectly,
to
Elisha Gray
Elisha Gray (August 2, 1835 – January 21, 1901) was an American electrical engineer who co-founded the Western Electric Manufacturing Company. Gray is best known for his development of a telephone prototype in 1876 in Highland Park, Illinois. ...
.
History and practical application
Mathematical puzzles
Reflected binary codes were applied to mathematical puzzles before they became known to engineers.
The binary-reflected Gray code represents the underlying scheme of the classical
Chinese rings puzzle, a sequential mechanical puzzle mechanism described by the French Louis Gros in 1872.
It can serve as a solution guide for the
Towers of Hanoi problem, based on a game by the French
Édouard Lucas in 1883.
Similarly, the so-called Towers of Bucharest and Towers of Klagenfurt game configurations yield
ternary and pentary Gray codes.
wrote a popular account of the Gray code in his August 1972
Mathematical Games column in
Scientific American.
The code also forms a
Hamiltonian cycle on a
hypercube
In geometry, a hypercube is an ''n''-dimensional analogue of a square () and a cube (). It is a closed, compact, convex figure whose 1- skeleton consists of groups of opposite parallel line segments aligned in each of the space's dimensions, ...
, where each bit is seen as one dimension.
Telegraphy codes
When the French engineer
Émile Baudot changed from using a 6-unit (6-bit) code to 5-unit code for his
printing telegraph system, in 1875
or 1876,
he ordered the alphabetic characters on his print wheel using a reflected binary code, and assigned the codes using only three of the bits to vowels. With vowels and consonants sorted in their alphabetical order,
and other symbols appropriately placed, the 5-bit character code has been recognized as a reflected binary code.
This code became known as
Baudot code and, with minor changes, was eventually adopted as
International Telegraph Alphabet No. 1 (ITA1, CCITT-1) in 1932.
About the same time, the German-Austrian
demonstrated another printing telegraph in Vienna using a 5-bit reflected binary code for the same purpose, in 1874.
Analog-to-digital signal conversion
Frank Gray, who became famous for inventing the signaling method that came to be used for compatible color television, invented a method to convert analog signals to reflected binary code groups using
vacuum tube-based apparatus. Filed in 1947, the method and apparatus were granted a patent in 1953,
and the name of Gray stuck to the codes. The "
PCM tube" apparatus that Gray patented was made by Raymond W. Sears of Bell Labs, working with Gray and William M. Goodall, who credited Gray for the idea of the reflected binary code.
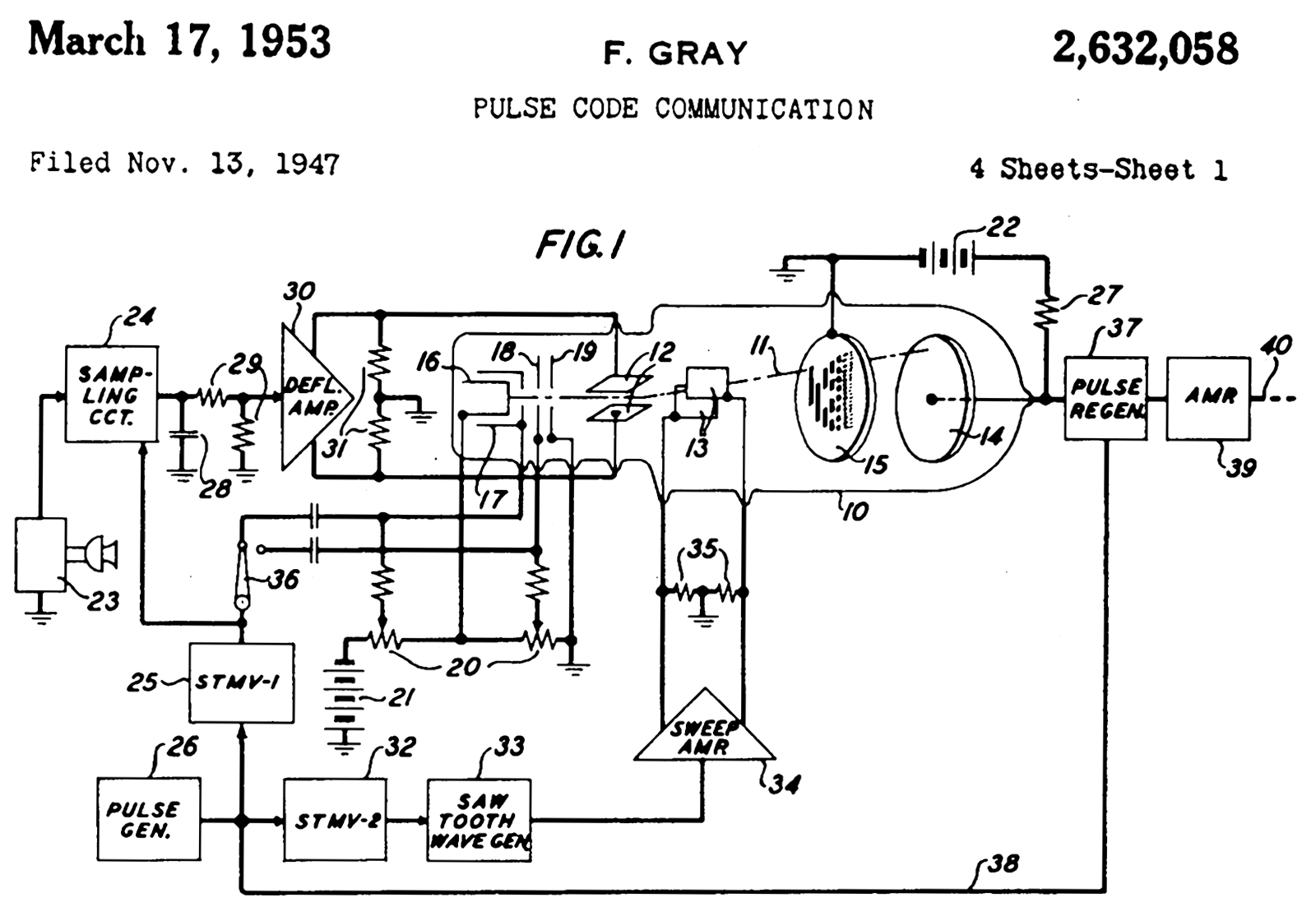
Gray was most interested in using the codes to minimize errors in converting analog signals to digital; his codes are still used today for this purpose.
Position encoders


Gray codes are used in linear and rotary position encoders (
absolute encoders and
quadrature encoders) in preference to weighted binary encoding. This avoids the possibility that, when multiple bits change in the binary representation of a position, a misread will result from some of the bits changing before others.
For example, some rotary encoders provide a disk which has an electrically conductive Gray code pattern on concentric rings (tracks). Each track has a stationary metal spring contact that provides electrical contact to the conductive code pattern. Together, these contacts produce output signals in the form of a Gray code. Other encoders employ non-contact mechanisms based on optical or magnetic sensors to produce the Gray code output signals.
Regardless of the mechanism or precision of a moving encoder, position measurement error can occur at specific positions (at code boundaries) because the code may be changing at the exact moment it is read (sampled). A binary output code could cause significant position measurement errors because it is impossible to make all bits change at exactly the same time. If, at the moment the position is sampled, some bits have changed and others have not, the sampled position will be incorrect. In the case of absolute encoders, the indicated position may be far away from the actual position and, in the case of incremental encoders, this can corrupt position tracking.
In contrast, the Gray code used by position encoders ensures that the codes for any two consecutive positions will differ by only one bit and, consequently, only one bit can change at a time. In this case, the maximum position error will be small, indicating a position adjacent to the actual position.
Genetic algorithms
Due to the
Hamming distance properties of Gray codes, they are sometimes used in
genetic algorithm
In computer science and operations research, a genetic algorithm (GA) is a metaheuristic inspired by the process of natural selection that belongs to the larger class of evolutionary algorithms (EA). Genetic algorithms are commonly used to gene ...
s.
They are very useful in this field, since mutations in the code allow for mostly incremental changes, but occasionally a single bit-change can cause a big leap and lead to new properties.
Boolean circuit minimization
Gray codes are also used in labelling the axes of
Karnaugh maps since 1953
as well as in
Händler circle graph
Logic optimization is a process of finding an equivalent representation of the specified logic circuit under one or more specified constraints. This process is a part of a logic synthesis applied in digital electronics and integrated circuit de ...
s since 1958,
both graphical methods for
logic circuit minimization
Logic optimization is a process of finding an equivalent representation of the specified logic circuit under one or more specified constraints. This process is a part of a logic synthesis applied in digital electronics and integrated circuit de ...
.
Error correction
In modern
digital communications, Gray codes play an important role in
error correction
In information theory and coding theory with applications in computer science and telecommunication, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communica ...
. For example, in a
digital modulation scheme such as
QAM where data is typically transmitted in
symbols
A symbol is a mark, sign, or word that indicates, signifies, or is understood as representing an idea, object, or relationship. Symbols allow people to go beyond what is known or seen by creating linkages between otherwise very different conc ...
of 4 bits or more, the signal's
constellation diagram is arranged so that the bit patterns conveyed by adjacent constellation points differ by only one bit. By combining this with
forward error correction
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is ...
capable of correcting single-bit errors, it is possible for a
receiver to correct any transmission errors that cause a constellation point to deviate into the area of an adjacent point. This makes the transmission system less susceptible to
noise.
Communication between clock domains
Digital logic designers use Gray codes extensively for passing multi-bit count information between synchronous logic that operates at different clock frequencies. The logic is considered operating in different "clock domains". It is fundamental to the design of large chips that operate with many different clocking frequencies.
Cycling through states with minimal effort
If a system has to cycle through all possible combinations of on-off states of some set of controls, and the changes of the controls require non-trivial expense (e.g. time, wear, human work), a Gray code minimizes the number of setting changes to just one change for each combination of states. An example would be testing a piping system for all combinations of settings of its manually operated valves.
A
balanced Gray code
The reflected binary code (RBC), also known as reflected binary (RB) or Gray code after Frank Gray (researcher), Frank Gray, is an ordering of the binary numeral system such that two successive values differ in only one bit (binary digit).
For ...
can be constructed,
that flips every bit equally often. Since bit-flips are evenly distributed, this is optimal in the following way: balanced Gray codes minimize the maximal count of bit-flips for each digit.
Gray code counters and arithmetic
George R. Stibitz
George Robert Stibitz (April 30, 1904 – January 31, 1995) was a Bell Labs researcher internationally recognized as one of the fathers of the modern digital computer. He was known for his work in the 1930s and 1940s on the realization of Boolea ...
utilized a reflected binary code in a binary pulse counting device in 1941 already.
A typical use of Gray code counters is building a
FIFO (first-in, first-out) data buffer that has read and write ports that exist in different clock domains. The input and output counters inside such a dual-port FIFO are often stored using Gray code to prevent invalid transient states from being captured when the count crosses clock domains.
The updated read and write pointers need to be passed between clock domains when they change, to be able to track FIFO empty and full status in each domain. Each bit of the pointers is sampled non-deterministically for this clock domain transfer. So for each bit, either the old value or the new value is propagated. Therefore, if more than one bit in the multi-bit pointer is changing at the sampling point, a "wrong" binary value (neither new nor old) can be propagated. By guaranteeing only one bit can be changing, Gray codes guarantee that the only possible sampled values are the new or old multi-bit value. Typically Gray codes of power-of-two length are used.
Sometimes digital buses in electronic systems are used to convey quantities that can only increase or decrease by one at a time, for example the output of an event counter which is being passed between clock domains or to a digital-to-analog converter. The advantage of Gray codes in these applications is that differences in the propagation delays of the many wires that represent the bits of the code cannot cause the received value to go through states that are out of the Gray code sequence. This is similar to the advantage of Gray codes in the construction of mechanical encoders, however the source of the Gray code is an electronic counter in this case. The counter itself must count in Gray code, or if the counter runs in binary then the output value from the counter must be reclocked after it has been converted to Gray code, because when a value is converted from binary to Gray code,
it is possible that differences in the arrival times of the binary data bits into the binary-to-Gray conversion circuit will mean that the code could go briefly through states that are wildly out of sequence. Adding a clocked register after the circuit that converts the count value to Gray code may introduce a clock cycle of latency, so counting directly in Gray code may be advantageous.
To produce the next count value in a Gray-code counter, it is necessary to have some combinational logic that will increment the current count value that is stored. One way to increment a Gray code number is to convert it into ordinary binary code,
add one to it with a standard binary adder, and then convert the result back to Gray code.
Other methods of counting in Gray code are discussed in a report by
Robert W. Doran
Robert William Doran HFNZCS (5 November 1944 – 13 October 2018) was a New Zealand-based computer scientist and historian of computing. He was Professor Emeritus of Computer Science at the University of Auckland, New Zealand.
Robert W. Do ...
, including taking the output from the first latches of the master-slave flip flops in a binary ripple counter.
Gray code addressing
As the execution of
program code typically causes an instruction memory access pattern of locally consecutive addresses,
bus encodings using Gray code addressing instead of binary addressing can reduce the number of state changes of the address bits significantly, thereby reducing the
CPU power consumption Processor power dissipation or processing unit power dissipation is the process in which computer processors consume electrical energy, and dissipate this energy in the form of heat due to the resistance in the electronic circuits.
Power managem ...
in some low-power designs.
Constructing an ''n''-bit Gray code


The binary-reflected Gray code list for ''n'' bits can be generated
recursively from the list for ''n'' − 1 bits by reflecting the list (i.e. listing the entries in reverse order), prefixing the entries in the original list with a binary , prefixing the entries in the reflected list with a binary , and then concatenating the original list with the reversed list.
For example, generating the ''n'' = 3 list from the ''n'' = 2 list:
The one-bit Gray code is ''G''
1 = (). This can be thought of as built recursively as above from a zero-bit Gray code ''G''
0 = (
Λ ) consisting of a single entry of zero length. This iterative process of generating ''G''
''n''+1 from ''G''
''n'' makes the following properties of the standard reflecting code clear:
* ''G''
''n'' is a
permutation
In mathematics, a permutation of a set is, loosely speaking, an arrangement of its members into a sequence or linear order, or if the set is already ordered, a rearrangement of its elements. The word "permutation" also refers to the act or proc ...
of the numbers 0, ..., 2
''n'' − 1. (Each number appears exactly once in the list.)
* ''G''
''n'' is embedded as the first half of ''G''
''n''+1.
* Therefore, the coding is ''stable'', in the sense that once a binary number appears in ''G''
''n'' it appears in the same position in all longer lists; so it makes sense to talk about ''the'' reflective Gray code value of a number: ''G''(''m'') = the ''m''th reflecting Gray code, counting from 0.
* Each entry in ''G''
''n'' differs by only one bit from the previous entry. (The Hamming distance is 1.)
* The last entry in ''G''
''n'' differs by only one bit from the first entry. (The code is cyclic.)
These characteristics suggest a simple and fast method of translating a binary value into the corresponding Gray code. Each bit is inverted if the next higher bit of the input value is set to one. This can be performed in parallel by a bit-shift and exclusive-or operation if they are available: the ''n''th Gray code is obtained by computing
. Prepending a bit leaves the order of the code words unchanged, prepending a bit reverses the order of the code words. If the bits at position
of codewords are inverted, the order of neighbouring blocks of
codewords is reversed. For example, if bit 0 is inverted in a 3 bit codeword sequence, the order of two neighbouring codewords is reversed
: → (invert bit 0)
If bit 1 is inverted, blocks of 2 codewords change order:
: → (invert bit 1)
If bit 2 is inverted, blocks of 4 codewords reverse order:
: → (invert bit 2)
Thus, performing an
exclusive or on a bit
at position
with the bit
at position
leaves the order of codewords intact if
, and reverses the order of blocks of
codewords if
. Now, this is exactly the same operation as the reflect-and-prefix method to generate the Gray code.
A similar method can be used to perform the reverse translation, but the computation of each bit depends on the computed value of the next higher bit so it cannot be performed in parallel. Assuming
is the
th Gray-coded bit (
being the most significant bit), and
is the
th binary-coded bit (
being the most-significant bit), the reverse translation can be given recursively:
, and
. Alternatively, decoding a Gray code into a binary number can be described as a
prefix sum of the bits in the Gray code, where each individual summation operation in the prefix sum is performed modulo two.
To construct the binary-reflected Gray code iteratively, at step 0 start with the
, and at step
find the bit position of the least significant in the binary representation of
and flip the bit at that position in the previous code
to get the next code
. The bit positions start 0, 1, 0, 2, 0, 1, 0, 3, ....
See
find first set for efficient algorithms to compute these values.
Converting to and from Gray code
The following functions in
C convert between binary numbers and their associated Gray codes. While it may seem that Gray-to-binary conversion requires each bit to be handled one at a time, faster algorithms exist.
On newer processors, the number of ALU instructions in the decoding step can be reduced by taking advantage of the
CLMUL instruction set. If MASK is the constant binary string of ones ended with a single zero digit, then carryless multiplication of MASK with the grey encoding of x will always give either x or its bitwise negation.
Special types of Gray codes
In practice, "Gray code" almost always refers to a binary-reflected Gray code (BRGC).
However, mathematicians have discovered other kinds of Gray codes.
Like BRGCs, each consists of a list of words, where each word differs from the next in only one digit (each word has a
Hamming distance of 1 from the next word).
Gray codes with ''n'' bits and of length less than
It is possible to construct binary Gray codes with ''n'' bits with a length of less than , if the length is even. One possibility is to start with a balanced Gray code and remove pairs of values at either the beginning and the end, or in the middle.
OEIS sequence A290772 gives the number of possible Gray sequences of length which include zero and use the minimum number of bits.
''n''-ary Gray code
There are many specialized types of Gray codes other than the binary-reflected Gray code. One such type of Gray code is the ''n''-ary Gray code, also known as a non-Boolean Gray code. As the name implies, this type of Gray code uses non-
Boolean
Any kind of logic, function, expression, or theory based on the work of George Boole is considered Boolean.
Related to this, "Boolean" may refer to:
* Boolean data type, a form of data with only two possible values (usually "true" and "false" ...
values in its encodings.
For example, a 3-ary (
ternary) Gray code would use the values .
The (''n'', ''k'')-''Gray code'' is the ''n''-ary Gray code with ''k'' digits.
The sequence of elements in the (3, 2)-Gray code is: . The (''n'', ''k'')-Gray code may be constructed recursively, as the BRGC, or may be constructed
iteratively. An
algorithm to iteratively generate the (''N'', ''k'')-Gray code is presented (in
C):
// inputs: base, digits, value
// output: Gray
// Convert a value to a Gray code with the given base and digits.
// Iterating through a sequence of values would result in a sequence
// of Gray codes in which only one digit changes at a time.
void toGray(unsigned base, unsigned digits, unsigned value, unsigned gray igits
// EXAMPLES
// input: value = 1899, base = 10, digits = 4
// output: baseN[] = [9,9,8,1], gray[] = [0,1,7,1]
// input: value = 1900, base = 10, digits = 4
// output: baseN[] = [0,0,9,1], gray[] = [0,1,8,1]
There are other Gray code algorithms for (''n'',''k'')-Gray codes. The (''n'',''k'')-Gray code produced by the above algorithm is always cyclical; some algorithms, such as that by Guan,
lack this property when k is odd. On the other hand, while only one digit at a time changes with this method, it can change by wrapping (looping from ''n'' − 1 to 0). In Guan's algorithm, the count alternately rises and falls, so that the numeric difference between two Gray code digits is always one.
Gray codes are not uniquely defined, because a permutation of the columns of such a code is a Gray code too. The above procedure produces a code in which the lower the significance of a digit, the more often it changes, making it similar to normal counting methods.
See also
Skew binary number system, a variant ternary number system where at most two digits change on each increment, as each increment can be done with at most one digit
carry operation.
Balanced Gray code
Although the binary reflected Gray code is useful in many scenarios, it is not optimal in certain cases because of a lack of "uniformity".
In balanced Gray codes, the number of changes in different coordinate positions are as close as possible. To make this more precise, let ''G'' be an ''R''-ary complete Gray cycle having transition sequence
; the ''transition counts'' (''spectrum'') of ''G'' are the collection of integers defined by
:
A Gray code is ''uniform'' or ''uniformly balanced'' if its transition counts are all equal, in which case we have
for all ''k''. Clearly, when
, such codes exist only if ''n'' is a power of 2. If ''n'' is not a power of 2, it is possible to construct ''well-balanced'' binary codes where the difference between two transition counts is at most 2; so that (combining both cases) every transition count is either
or
.
Gray codes can also be ''exponentially balanced'' if all of their transition counts are adjacent powers of two, and such codes exist for every power of two.
For example, a balanced 4-bit Gray code has 16 transitions, which can be evenly distributed among all four positions (four transitions per position), making it uniformly balanced:
:
:
:
:
whereas a balanced 5-bit Gray code has a total of 32 transitions, which cannot be evenly distributed among the positions. In this example, four positions have six transitions each, and one has eight:
:
:
:
:
:
We will now show a construction
and implementation
for well-balanced binary Gray codes which allows us to generate an ''n''-digit balanced Gray code for every ''n''. The main principle is to inductively construct an (''n'' + 2)-digit Gray code
given an ''n''-digit Gray code ''G'' in such a way that the balanced property is preserved. To do this, we consider partitions of
into an even number ''L'' of non-empty blocks of the form
:
where
,
, and
). This partition induces an
-digit Gray code given by
:
:
:
:
If we define the ''transition multiplicities''
:
to be the number of times the digit in position ''i'' changes between consecutive blocks in a partition, then for the (''n'' + 2)-digit Gray code induced by this partition the transition spectrum
is
:
The delicate part of this construction is to find an adequate partitioning of a balanced ''n''-digit Gray code such that the code induced by it remains balanced, but for this only the transition multiplicities matter; joining two consecutive blocks over a digit
transition and splitting another block at another digit
transition produces a different Gray code with exactly the same transition spectrum
, so one may for example
designate the first
transitions at digit
as those that fall between two blocks. Uniform codes can be found when
and
, and this construction can be extended to the ''R''-ary case as well.
Long run Gray codes
Long run (or ''maximum gap'') Gray codes maximize the distance between consecutive changes of digits in the same position. That is, the minimum run-length of any bit remains unchanged for as long as possible.
Monotonic Gray codes
Monotonic codes are useful in the theory of interconnection networks, especially for minimizing dilation for linear arrays of processors.
If we define the ''weight'' of a binary string to be the number of 1s in the string, then although we clearly cannot have a Gray code with strictly increasing weight, we may want to approximate this by having the code run through two adjacent weights before reaching the next one.
We can formalize the concept of monotone Gray codes as follows: consider the partition of the hypercube
into ''levels'' of vertices that have equal weight, i.e.
:
for
. These levels satisfy
. Let
be the subgraph of
induced by
, and let
be the edges in
. A monotonic Gray code is then a Hamiltonian path in
such that whenever
comes before
in the path, then
.
An elegant construction of monotonic ''n''-digit Gray codes for any ''n'' is based on the idea of recursively building subpaths
of length
having edges in
.
We define
,
whenever
or
, and
:
otherwise. Here,
is a suitably defined permutation and
refers to the path ''P'' with its coordinates permuted by
. These paths give rise to two monotonic ''n''-digit Gray codes
and
given by
:
The choice of
which ensures that these codes are indeed Gray codes turns out to be
. The first few values of
are shown in the table below.
These monotonic Gray codes can be efficiently implemented in such a way that each subsequent element can be generated in ''O''(''n'') time. The algorithm is most easily described using
coroutines.
Monotonic codes have an interesting connection to the
Lovász conjecture In graph theory, the Lovász conjecture (1969) is a classical problem on Hamiltonian paths in graphs. It says:
: Every finite connected vertex-transitive graph contains a Hamiltonian path.
Originally László Lovász stated the problem in the opposi ...
, which states that every connected
vertex-transitive graph contains a Hamiltonian path. The "middle-level" subgraph
is
vertex-transitive (that is, its automorphism group is transitive, so that each vertex has the same "local environment" and cannot be differentiated from the others, since we can relabel the coordinates as well as the binary digits to obtain an
automorphism
In mathematics, an automorphism is an isomorphism from a mathematical object to itself. It is, in some sense, a symmetry of the object, and a way of mapping the object to itself while preserving all of its structure. The set of all automorphisms ...
) and the problem of finding a Hamiltonian path in this subgraph is called the "middle-levels problem", which can provide insights into the more general conjecture. The question has been answered affirmatively for
, and the preceding construction for monotonic codes ensures a Hamiltonian path of length at least 0.839''N'' where ''N'' is the number of vertices in the middle-level subgraph.
Beckett–Gray code
Another type of Gray code, the Beckett–Gray code, is named for Irish playwright
Samuel Beckett
Samuel Barclay Beckett (; 13 April 1906 – 22 December 1989) was an Irish novelist, dramatist, short story writer, theatre director, poet, and literary translator. His literary and theatrical work features bleak, impersonal and tragicomic expe ...
, who was interested in
symmetry
Symmetry (from grc, συμμετρία "agreement in dimensions, due proportion, arrangement") in everyday language refers to a sense of harmonious and beautiful proportion and balance. In mathematics, "symmetry" has a more precise definit ...
. His play "
Quad
Quad as a word or prefix usually means 'four'. It may refer to:
Government
* Quadrilateral Security Dialogue, a strategic security dialogue between Australia, India, Japan, and the United States
* Quadrilateral group, an informal group which inc ...
" features four actors and is divided into sixteen time periods. Each period ends with one of the four actors entering or leaving the stage. The play begins and ends with an empty stage, and Beckett wanted each subset of actors to appear on stage exactly once.
Clearly the set of actors currently on stage can be represented by a 4-bit binary Gray code. Beckett, however, placed an additional restriction on the script: he wished the actors to enter and exit so that the actor who had been on stage the longest would always be the one to exit. The actors could then be represented by a
first in, first out queue, so that (of the actors onstage) the actor being dequeued is always the one who was enqueued first.
Beckett was unable to find a Beckett–Gray code for his play, and indeed, an exhaustive listing of all possible sequences reveals that no such code exists for ''n'' = 4. It is known today that such codes do exist for ''n'' = 2, 5, 6, 7, and 8, and do not exist for ''n'' = 3 or 4. An example of an 8-bit Beckett–Gray code can be found in
Donald Knuth's ''Art of Computer Programming''.
According to Sawada and Wong, the search space for ''n'' = 6 can be explored in 15 hours, and more than 9,500 solutions for the case ''n'' = 7 have been found.
Snake-in-the-box codes
Snake-in-the-box codes, or ''snakes'', are the sequences of nodes of
induced path
In the mathematical area of graph theory, an induced path in an undirected graph is a path that is an induced subgraph of . That is, it is a sequence of vertices in such that each two adjacent vertices in the sequence are connected by an edge ...
s in an ''n''-dimensional
hypercube graph, and coil-in-the-box codes,
or ''coils'', are the sequences of nodes of induced
cycles in a hypercube. Viewed as Gray codes, these sequences have the property of being able to detect any single-bit coding error. Codes of this type were first described by
William H. Kautz In signal processing, the Kautz filter, named after William H. Kautz, is a fixed-Pole (complex analysis), pole traversal filter (signal processing), filter, published in 1954.
Like Laguerre filters, Kautz filters can be implemented using a cascade ...
in the late 1950s;
since then, there has been much research on finding the code with the largest possible number of codewords for a given hypercube dimension.
Single-track Gray code
Yet another kind of Gray code is the single-track Gray code (STGC) developed by Norman B. Spedding
and refined by Hiltgen, Paterson and Brandestini in "Single-track Gray codes" (1996).
The STGC is a cyclical list of ''P'' unique binary encodings of length n such that two consecutive words differ in exactly one position, and when the list is examined as a ''P'' × ''n''
matrix
Matrix most commonly refers to:
* ''The Matrix'' (franchise), an American media franchise
** '' The Matrix'', a 1999 science-fiction action film
** "The Matrix", a fictional setting, a virtual reality environment, within ''The Matrix'' (franchi ...
, each column is a cyclic shift of the first column.


The name comes from their use with
rotary encoders, where a number of tracks are being sensed by contacts, resulting for each in an output of or . To reduce noise due to different contacts not switching at exactly the same moment in time, one preferably sets up the tracks so that the data output by the contacts are in Gray code. To get high angular accuracy, one needs lots of contacts; in order to achieve at least 1° accuracy, one needs at least 360 distinct positions per revolution, which requires a minimum of 9 bits of data, and thus the same number of contacts.
If all contacts are placed at the same angular position, then 9 tracks are needed to get a standard BRGC with at least 1° accuracy. However, if the manufacturer moves a contact to a different angular position (but at the same distance from the center shaft), then the corresponding "ring pattern" needs to be rotated the same angle to give the same output. If the most significant bit (the inner ring in Figure 1) is rotated enough, it exactly matches the next ring out. Since both rings are then identical, the inner ring can be cut out, and the sensor for that ring moved to the remaining, identical ring (but offset at that angle from the other sensor on that ring). Those two sensors on a single ring make a quadrature encoder. That reduces the number of tracks for a "1° resolution" angular encoder to 8 tracks. Reducing the number of tracks still further cannot be done with BRGC.
For many years, Torsten Sillke
and other mathematicians believed that it was impossible to encode position on a single track such that consecutive positions differed at only a single sensor, except for the 2-sensor, 1-track quadrature encoder. So for applications where 8 tracks were too bulky, people used single-track incremental encoders (quadrature encoders) or 2-track "quadrature encoder + reference notch" encoders.
Norman B. Spedding, however, registered a patent in 1994 with several examples showing that it was possible.
Although it is not possible to distinguish 2
''n'' positions with ''n'' sensors on a single track, it ''is'' possible to distinguish close to that many. Etzion and Paterson conjecture that when ''n'' is itself a power of 2, ''n'' sensors can distinguish at most 2
''n'' − 2''n'' positions and that for prime ''n'' the limit is 2
''n'' − 2 positions.
The authors went on to generate a 504-position single track code of length 9 which they believe is optimal. Since this number is larger than 2
8 = 256, more than 8 sensors are required by any code, although a BRGC could distinguish 512 positions with 9 sensors.
An STGC for ''P'' = 30 and ''n'' = 5 is reproduced here:
:
Each column is a cyclic shift of the first column, and from any row to the next row only one bit changes.
The single-track nature (like a code chain) is useful in the fabrication of these wheels (compared to BRGC), as only one track is needed, thus reducing their cost and size.
The Gray code nature is useful (compared to
chain codes, also called
De Bruijn sequences), as only one sensor will change at any one time, so the uncertainty during a transition between two discrete states will only be plus or minus one unit of angular measurement the device is capable of resolving.
Two-dimensional Gray code

Two-dimensional Gray codes are used in communication to minimize the number of bit errors in
quadrature amplitude modulation (QAM) adjacent points in the
constellation
A constellation is an area on the celestial sphere in which a group of visible stars forms Asterism (astronomy), a perceived pattern or outline, typically representing an animal, mythological subject, or inanimate object.
The origins of the e ...
. In a typical encoding the horizontal and vertical adjacent constellation points differ by a single bit, and diagonal adjacent points differ by 2 bits.
Two-dimensional Gray codes also have uses in
location identification
A location identifier is a symbolic representation for the name and the location of an airport, navigation aid, or weather station, and is used for staffed air traffic control facilities in air traffic control, telecommunications, computer programm ...
s schemes, where the code would be applied to area maps such as a
Mercator projection
The Mercator projection () is a cylindrical map projection presented by Flemish geographer and cartographer Gerardus Mercator in 1569. It became the standard map projection for navigation because it is unique in representing north as up and sou ...
of the earth's surface and an appropriate cyclic two-dimensional distance function such as the
Mannheim metric In coding theory, the Lee distance is a distance between two strings x_1 x_2 \dots x_n and y_1 y_2 \dots y_n of equal length ''n'' over the ''q''-ary alphabet of size . It is a metric defined as
\sum_^n \min(, x_i - y_i, ,\, q - , x_i - y_i, ).
I ...
be used to calculate the distance between two encoded locations, thereby combining the characteristics of the
Hamming distance with the cyclic continuation of a Mercator projection.
Excess-Gray-Code
If a subsection of a specific codevalue is extracted from that value, for example the last 3 bits of a 4-bit gray-code, the resulting code will be an "excess gray code". This code shows the property of counting backwards in those extracted bits if the original value is further increased. Reason for this is that gray-encoded values do not show the behaviour of overflow, known from classic binary encoding, when increasing past the "highest" value.
Example: The highest 3-bit gray code, 7, is encoded as (0)100. Adding 1 results in number 8, encoded in gray as 1100. The last 3 bits do not overflow and count backwards if you further increase the original 4 bit code.
When working with sensors that output multiple, gray-encoded values in a serial fashion, one should therefore pay attention whether the sensor produces those multiple values encoded in 1 single gray-code or as separate ones, as otherwise the values might appear to be counting backwards when an "overflow" is expected.
Gray isometry
The bijective mapping establishes an
isometry between the
metric space over the
finite field with the metric given by the
Hamming distance and the metric space over the
finite ring (the usual
modular arithmetic) with the metric given by the
Lee distance. The mapping is suitably extended to an isometry of the
Hamming spaces
and
. Its importance lies in establishing a correspondence between various "good" but not necessarily
linear codes as Gray-map images in
of
ring-linear codes from
.
Related codes
There are a number of binary codes similar to Gray codes, including:
* Datex codes aka Giannini codes (1954), as described by Carl P. Spaulding,
use a variant of
O'Brien code II.
* Codes used by Varec (ca. 1954),
use a variant of
O'Brien code I
The reflected binary code (RBC), also known as reflected binary (RB) or Gray code after Frank Gray, is an ordering of the binary numeral system such that two successive values differ in only one bit (binary digit).
For example, the representa ...
as well as base-12 and base-16 Gray code variants.
* Lucal code (1959)
aka modified reflected binary code (MRB)
*
Gillham code (1961/1962),
uses a variant of
Datex code and
O'Brien code II.
* Leslie and Russell code (1964)
* Royal Radar Establishment code
* Hoklas code (1988)
The following
binary-coded decimal
In computing and electronic systems, binary-coded decimal (BCD) is a class of binary encodings of decimal numbers where each digit is represented by a fixed number of bits, usually four or eight. Sometimes, special bit patterns are used for ...
(BCD) codes are Gray code variants as well:
* Petherick code (1953),
also known as
Royal Aircraft Establishment
The Royal Aircraft Establishment (RAE) was a British research establishment, known by several different names during its history, that eventually came under the aegis of the Ministry of Defence (United Kingdom), UK Ministry of Defence (MoD), bef ...
(RAE) code.
* O'Brien codes I and II (1955)
(An O'Brien type-I code
was already described by Frederic A. Foss of
IBM and used by
Varec in 1954. Later, it was also known as Watts code or Watts reflected decimal (WRD) code and is sometimes ambiguously referred to as reflected binary modified Gray code.
An O'Brien type-II code was already used by
Datex in 1954.
)
* Excess-3 Gray code (1956)
(aka Gray
excess-3 code,
Gray 3-excess code, reflex excess-3 code, excess Gray code,
Gray excess code, 10-excess-3 Gray code or Gray–Stibitz code), described by Frank P. Turvey Jr. of
ITT
ITT may refer to:
Communication
* Infantry-Tank Telephone, a device allowing infantrymen to speak to the occupants of armoured vehicles.
Mathematics
*Intuitionistic type theory, other name of Martin-Löf Type Theory
*Intensional type theory
B ...
.
* Tompkins codes I and II (1956)
* Glixon code (1957), sometimes ambiguously also called modified Gray code
See also
*
Linear-feedback shift register
*
De Bruijn sequence
*
Steinhaus–Johnson–Trotter algorithm – an algorithm that generates Gray codes for the
factorial number system
*
Minimum distance code
*
Prouhet–Thue–Morse sequence – related to inverse Gray code
*
Ryser formula
In linear algebra, the computation of the Permanent (mathematics), permanent of a matrix (mathematics), matrix is a problem that is thought to be more difficult than the computation of the determinant of a matrix despite the apparent similarity of ...
*
Hilbert curve
Notes
References
Further reading
*
*
*
*
*
*
*
*
Part 2https://web.archive.org/web/20171030140323/https://www.eetimes.com/document.asp?doc_id=1278853 --> Part 3
* (7 pages)
* (5 pages)
* (2 pages)
*
External links
"Gray Code" demonstration
by Michael Schreiber, Wolfram Demonstrations Project (with Mathematica implementation). 2007.
NIST Dictionary of Algorithms and Data Structures: Gray code
including C code to convert between binary and BRGC.
* Dragos A. Harabor use
Gray codes in a 3D digitizer
* Single-track gray codes, binary chain codes
Lancaster 1994
, and linear-feedback shift registers are all useful in finding one's absolute position on a single-track rotary encoder (or other position sensor).
AMS Column: Gray codes
ProtoTalk.net – Understanding Quadrature Encoding
– Covers quadrature encoding in more detail with a focus on robotic applications
{{DEFAULTSORT:Gray Code
Data transmission
Numeral systems
Binary arithmetic
Non-standard positional numeral systems
Articles with example C code
 In principle, there can be more than one such code for a given word length, but the term Gray code was first applied to a particular binary code for non-negative integers, the ''binary-reflected Gray code'', or BRGC. Bell Labs researcher
In principle, there can be more than one such code for a given word length, but the term Gray code was first applied to a particular binary code for non-negative integers, the ''binary-reflected Gray code'', or BRGC. Bell Labs researcher
 :
For decimal 15 the code rolls over to decimal 0 with only one switch change. This is called the cyclic or adjacency property of the code.
In modern digital communications, Gray codes play an important role in
:
For decimal 15 the code rolls over to decimal 0 with only one switch change. This is called the cyclic or adjacency property of the code.
In modern digital communications, Gray codes play an important role in  Gray was most interested in using the codes to minimize errors in converting analog signals to digital; his codes are still used today for this purpose.
Gray was most interested in using the codes to minimize errors in converting analog signals to digital; his codes are still used today for this purpose.
 Gray codes are used in linear and rotary position encoders ( absolute encoders and quadrature encoders) in preference to weighted binary encoding. This avoids the possibility that, when multiple bits change in the binary representation of a position, a misread will result from some of the bits changing before others.
For example, some rotary encoders provide a disk which has an electrically conductive Gray code pattern on concentric rings (tracks). Each track has a stationary metal spring contact that provides electrical contact to the conductive code pattern. Together, these contacts produce output signals in the form of a Gray code. Other encoders employ non-contact mechanisms based on optical or magnetic sensors to produce the Gray code output signals.
Regardless of the mechanism or precision of a moving encoder, position measurement error can occur at specific positions (at code boundaries) because the code may be changing at the exact moment it is read (sampled). A binary output code could cause significant position measurement errors because it is impossible to make all bits change at exactly the same time. If, at the moment the position is sampled, some bits have changed and others have not, the sampled position will be incorrect. In the case of absolute encoders, the indicated position may be far away from the actual position and, in the case of incremental encoders, this can corrupt position tracking.
In contrast, the Gray code used by position encoders ensures that the codes for any two consecutive positions will differ by only one bit and, consequently, only one bit can change at a time. In this case, the maximum position error will be small, indicating a position adjacent to the actual position.
Gray codes are used in linear and rotary position encoders ( absolute encoders and quadrature encoders) in preference to weighted binary encoding. This avoids the possibility that, when multiple bits change in the binary representation of a position, a misread will result from some of the bits changing before others.
For example, some rotary encoders provide a disk which has an electrically conductive Gray code pattern on concentric rings (tracks). Each track has a stationary metal spring contact that provides electrical contact to the conductive code pattern. Together, these contacts produce output signals in the form of a Gray code. Other encoders employ non-contact mechanisms based on optical or magnetic sensors to produce the Gray code output signals.
Regardless of the mechanism or precision of a moving encoder, position measurement error can occur at specific positions (at code boundaries) because the code may be changing at the exact moment it is read (sampled). A binary output code could cause significant position measurement errors because it is impossible to make all bits change at exactly the same time. If, at the moment the position is sampled, some bits have changed and others have not, the sampled position will be incorrect. In the case of absolute encoders, the indicated position may be far away from the actual position and, in the case of incremental encoders, this can corrupt position tracking.
In contrast, the Gray code used by position encoders ensures that the codes for any two consecutive positions will differ by only one bit and, consequently, only one bit can change at a time. In this case, the maximum position error will be small, indicating a position adjacent to the actual position.
 The name comes from their use with rotary encoders, where a number of tracks are being sensed by contacts, resulting for each in an output of or . To reduce noise due to different contacts not switching at exactly the same moment in time, one preferably sets up the tracks so that the data output by the contacts are in Gray code. To get high angular accuracy, one needs lots of contacts; in order to achieve at least 1° accuracy, one needs at least 360 distinct positions per revolution, which requires a minimum of 9 bits of data, and thus the same number of contacts.
If all contacts are placed at the same angular position, then 9 tracks are needed to get a standard BRGC with at least 1° accuracy. However, if the manufacturer moves a contact to a different angular position (but at the same distance from the center shaft), then the corresponding "ring pattern" needs to be rotated the same angle to give the same output. If the most significant bit (the inner ring in Figure 1) is rotated enough, it exactly matches the next ring out. Since both rings are then identical, the inner ring can be cut out, and the sensor for that ring moved to the remaining, identical ring (but offset at that angle from the other sensor on that ring). Those two sensors on a single ring make a quadrature encoder. That reduces the number of tracks for a "1° resolution" angular encoder to 8 tracks. Reducing the number of tracks still further cannot be done with BRGC.
For many years, Torsten Sillke and other mathematicians believed that it was impossible to encode position on a single track such that consecutive positions differed at only a single sensor, except for the 2-sensor, 1-track quadrature encoder. So for applications where 8 tracks were too bulky, people used single-track incremental encoders (quadrature encoders) or 2-track "quadrature encoder + reference notch" encoders.
Norman B. Spedding, however, registered a patent in 1994 with several examples showing that it was possible. Although it is not possible to distinguish 2''n'' positions with ''n'' sensors on a single track, it ''is'' possible to distinguish close to that many. Etzion and Paterson conjecture that when ''n'' is itself a power of 2, ''n'' sensors can distinguish at most 2''n'' − 2''n'' positions and that for prime ''n'' the limit is 2''n'' − 2 positions. The authors went on to generate a 504-position single track code of length 9 which they believe is optimal. Since this number is larger than 28 = 256, more than 8 sensors are required by any code, although a BRGC could distinguish 512 positions with 9 sensors.
An STGC for ''P'' = 30 and ''n'' = 5 is reproduced here:
:
Each column is a cyclic shift of the first column, and from any row to the next row only one bit changes.
The single-track nature (like a code chain) is useful in the fabrication of these wheels (compared to BRGC), as only one track is needed, thus reducing their cost and size.
The Gray code nature is useful (compared to chain codes, also called De Bruijn sequences), as only one sensor will change at any one time, so the uncertainty during a transition between two discrete states will only be plus or minus one unit of angular measurement the device is capable of resolving.
The name comes from their use with rotary encoders, where a number of tracks are being sensed by contacts, resulting for each in an output of or . To reduce noise due to different contacts not switching at exactly the same moment in time, one preferably sets up the tracks so that the data output by the contacts are in Gray code. To get high angular accuracy, one needs lots of contacts; in order to achieve at least 1° accuracy, one needs at least 360 distinct positions per revolution, which requires a minimum of 9 bits of data, and thus the same number of contacts.
If all contacts are placed at the same angular position, then 9 tracks are needed to get a standard BRGC with at least 1° accuracy. However, if the manufacturer moves a contact to a different angular position (but at the same distance from the center shaft), then the corresponding "ring pattern" needs to be rotated the same angle to give the same output. If the most significant bit (the inner ring in Figure 1) is rotated enough, it exactly matches the next ring out. Since both rings are then identical, the inner ring can be cut out, and the sensor for that ring moved to the remaining, identical ring (but offset at that angle from the other sensor on that ring). Those two sensors on a single ring make a quadrature encoder. That reduces the number of tracks for a "1° resolution" angular encoder to 8 tracks. Reducing the number of tracks still further cannot be done with BRGC.
For many years, Torsten Sillke and other mathematicians believed that it was impossible to encode position on a single track such that consecutive positions differed at only a single sensor, except for the 2-sensor, 1-track quadrature encoder. So for applications where 8 tracks were too bulky, people used single-track incremental encoders (quadrature encoders) or 2-track "quadrature encoder + reference notch" encoders.
Norman B. Spedding, however, registered a patent in 1994 with several examples showing that it was possible. Although it is not possible to distinguish 2''n'' positions with ''n'' sensors on a single track, it ''is'' possible to distinguish close to that many. Etzion and Paterson conjecture that when ''n'' is itself a power of 2, ''n'' sensors can distinguish at most 2''n'' − 2''n'' positions and that for prime ''n'' the limit is 2''n'' − 2 positions. The authors went on to generate a 504-position single track code of length 9 which they believe is optimal. Since this number is larger than 28 = 256, more than 8 sensors are required by any code, although a BRGC could distinguish 512 positions with 9 sensors.
An STGC for ''P'' = 30 and ''n'' = 5 is reproduced here:
:
Each column is a cyclic shift of the first column, and from any row to the next row only one bit changes.
The single-track nature (like a code chain) is useful in the fabrication of these wheels (compared to BRGC), as only one track is needed, thus reducing their cost and size.
The Gray code nature is useful (compared to chain codes, also called De Bruijn sequences), as only one sensor will change at any one time, so the uncertainty during a transition between two discrete states will only be plus or minus one unit of angular measurement the device is capable of resolving.