Oauth Logo on:
[Wikipedia]
[Google]
[Amazon]
 OAuth (short for "Open Authorization") is an open standard for access
OAuth (short for "Open Authorization") is an open standard for access
 OAuth began in November 2006 when
OAuth began in November 2006 when RFC 5849 , an informational RFC 6749 and the Bearer Token Usage as RFC 6750 , both standards track Requests for Comments, in October 2012.
The OAuth 2.1 Authorization Framework is in draft stage and consolidates the functionality in the RFCs OAuth 2.0, OAuth 2.0 for Native Apps, Proof Key for Code Exchange, OAuth 2.0 for Browser-Based Apps, OAuth Security Best Current and Bearer Token Usage.

oauth.com
oauth.net
{{Authentication APIs Cloud standards Internet protocols Computer-related introductions in 2007 Computer access control Computer access control protocols
delegation
Delegation is the assignment of authority to another person (normally from a manager to a subordinate) to carry out specific activities. It is the process of distributing and entrusting work to another person,Schermerhorn, J., Davidson, P., Poole ...
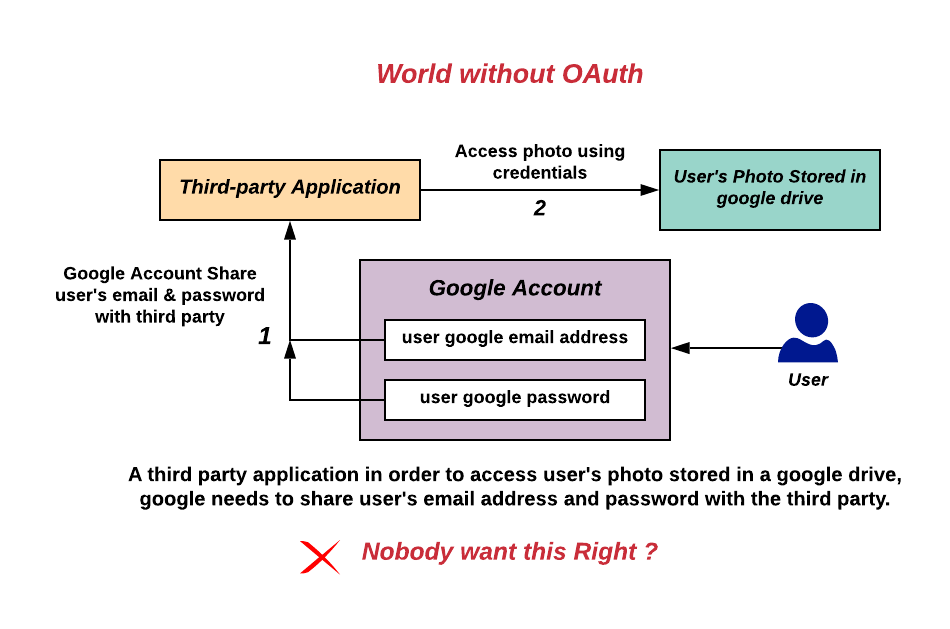
, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon
Amazon most often refers to:
* Amazons, a tribe of female warriors in Greek mythology
* Amazon rainforest, a rainforest covering most of the Amazon basin
* Amazon River, in South America
* Amazon (company), an American multinational technology c ...
, Google
Google LLC () is an American multinational technology company focusing on search engine technology, online advertising, cloud computing, computer software, quantum computing, e-commerce, artificial intelligence, and consumer electronics. ...
, Facebook
Facebook is an online social media and social networking service owned by American company Meta Platforms. Founded in 2004 by Mark Zuckerberg with fellow Harvard College students and roommates Eduardo Saverin, Andrew McCollum, Dustin M ...
, Microsoft
Microsoft Corporation is an American multinational technology corporation producing computer software, consumer electronics, personal computers, and related services headquartered at the Microsoft Redmond campus located in Redmond, Washing ...
, and Twitter
Twitter is an online social media and social networking service owned and operated by American company Twitter, Inc., on which users post and interact with 280-character-long messages known as "tweets". Registered users can post, like, and ...
to permit the users to share information about their accounts with third-party applications or websites.
Generally, OAuth provides clients a "secure delegated access" to server resources on behalf of a resource owner. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol
The Hypertext Transfer Protocol (HTTP) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, ...
(HTTP), OAuth essentially allows access token
In computer systems, an access token contains the security credentials for a login session and identifies the user, the user's groups, the user's privileges, and, in some cases, a particular application. In some instances, one may be asked to ente ...
s to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access the protected resources hosted by the resource server. In particular, OAuth 2.0 provides specific authorization flows for web applications, desktop applications, mobile phones, and smart device
A smart device is an electronic device, generally connected to other devices or networks via different wireless protocols (such as Bluetooth, Zigbee, near-field communication, Wi-Fi, LiFi, or 5G) that can operate to some extent interactively and ...
s.
History
 OAuth began in November 2006 when
OAuth began in November 2006 when Blaine Cook
Blaine "Zippy" Cook is the former lead singer of the early 1980s Seattle political punk band the Fartz. After they disbanded, he went on to front the thrash oriented the Accüsed. Cook currently fronts Toe Tag
A toe tag is a piece of cardbo ...
was developing the Twitter
Twitter is an online social media and social networking service owned and operated by American company Twitter, Inc., on which users post and interact with 280-character-long messages known as "tweets". Registered users can post, like, and ...
OpenID
OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party identity provider ...
implementation. Meanwhile, Ma.gnolia needed a solution to allow its members with OpenIDs to authorize Dashboard Widgets to access their service. Cook, Chris Messina
Christopher Messina (born August 11, 1974)Hochberg, Mina.Chris Messina stars in 'Ruby Sparks'��. ''Newsday'' (Long Island, New York). August 8, 2012: “...the actor, who turns 38 Saturday ugust 11, 2012 After graduating from Northport ew Yor ...
and Larry Halff from Magnolia met with David Recordon
David Recordon (born September 4, 1986) is an American technologist with an open standards and open source background. He is currently the Chief Technology Officer at Rebellion Defense. From January 2021 to September 2022, he served as the Di ...
to discuss using OpenID with the Twitter and Magnolia API
An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software Interface (computing), interface, offering a service to other pieces of software. A document or standa ...
s to delegate authentication. They concluded that there were no open standards for API access delegation.
The OAuth discussion group A discussion group is a group of individuals, typically who share a similar interest, who gather either formally or informally to discuss ideas, solve problems, or make comments. Common methods of conversing including meeting in person, conducting c ...
was created in April 2007, for a small group of implementers to write the draft proposal for an open protocol. DeWitt Clinton from Google
Google LLC () is an American multinational technology company focusing on search engine technology, online advertising, cloud computing, computer software, quantum computing, e-commerce, artificial intelligence, and consumer electronics. ...
learned of the OAuth project, and expressed his interest in supporting the effort. In July 2007, the team drafted an initial specification. Eran Hammer joined and coordinated the many OAuth contributions creating a more formal specification. On 4 December 2007, the OAuth Core 1.0 final draft was released.
At the 73rd Internet Engineering Task Force
The Internet Engineering Task Force (IETF) is a standards organization for the Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and a ...
(IETF) meeting in Minneapolis
Minneapolis () is the largest city in Minnesota, United States, and the county seat of Hennepin County. The city is abundant in water, with thirteen lakes, wetlands, the Mississippi River, creeks and waterfalls. Minneapolis has its origins ...
in November 2008, an OAuth BoF was held to discuss bringing the protocol into the IETF for further standardization work. The event was well attended and there was wide support for formally chartering an OAuth working group within the IETF.
The OAuth 1.0 protocol was published as Request for Comments
A Request for Comments (RFC) is a publication in a series from the principal technical development and standards-setting bodies for the Internet, most prominently the Internet Engineering Task Force (IETF). An RFC is authored by individuals or g ...
, in April 2010. Since 31 August 2010, all third party Twitter applications have been required to use OAuth.
The OAuth 2.0 framework was published considering additional use cases and extensibility requirements gathered from the wider IETF community. Albeit being built on the OAuth 1.0 deployment experience, OAuth 2.0 is not backwards compatible with OAuth 1.0. OAuth 2.0 was published as Security issues
OAuth 1.0
On 23 April 2009, asession fixation
In computer network security, session fixation attacks attempt to exploit the vulnerability of a system that allows one person to fixate (find or set) another person's session identifier. Most session fixation attacks are web based, and most rel ...
security flaw in the 1.0 protocol was announced. It affects the OAuth authorization flow (also known as "3-legged OAuth") in OAuth Core 1.0 Section 6.
Version 1.0a of the OAuth Core protocol was issued to address this issue.
OAuth 2.0
In January 2013, the Internet Engineering Task Force published a threat model for OAuth 2.0. fc:6819 OAuth 2.0 Threat Model and Security Considerations Internet Engineering Task Force. Accessed January 2015. Among the threats outlined is one called "Open Redirector"; in early 2014, a variant of this was described under the name "Covert Redirect" by Wang Jing. OAuth 2.0 has been analyzed using formal web protocol analysis. This analysis revealed that in setups with multiple authorization servers, one of which is behaving maliciously, clients can become confused about the authorization server to use and may forward secrets to the malicious authorization server (AS Mix-Up Attack). This prompted the creation of a newbest current practice
A Best Current Practice (BCP) is a ''de facto'' level of performance in engineering and information technology. It is more flexible than a standard, since techniques and tools are continually evolving.
The Internet Engineering Task Force publishe ...
internet draft that sets out to define a new security standard for OAuth 2.0. Assuming a fix against the AS Mix-Up Attack in place, the security of OAuth 2.0 has been proven under strong attacker models using formal analysis.
One implementation of OAuth 2.0 with numerous security flaws has been exposed.
In April and May 2017, about one million users of Gmail
Gmail is a free email service provided by Google. As of 2019, it had 1.5 billion active users worldwide. A user typically accesses Gmail in a web browser or the official mobile app. Google also supports the use of email clients via the POP an ...
(less than 0.1% of users as of May 2017) were targeted by an OAuth-based phishing attack, receiving an email purporting to be from a colleague, employer or friend wanting to share a document on Google Docs. Those who clicked on the link within the email were directed to sign in and allow a potentially malicious third-party program called "Google Apps" to access their "email account, contacts and online documents". Within "approximately one hour", the phishing attack was stopped by Google, who advised those who had given "Google Apps" access to their email to revoke such access and change their passwords.
In the draft of OAuth 2.1 the use of the PKCE extension for native apps has been recommended to all kinds of OAuth clients, including web applications and other confidential clients in order to avoid malicious browser extensions to perform OAuth 2.0 code injection attack.
Uses
Facebook
Facebook is an online social media and social networking service owned by American company Meta Platforms. Founded in 2004 by Mark Zuckerberg with fellow Harvard College students and roommates Eduardo Saverin, Andrew McCollum, Dustin M ...
's Graph API
The social graph is a graph that represents social relations between entities. In short, it is a model or representation of a social network, where the word graph has been taken from graph theory. The social graph has been referred to as "the ...
only supports OAuth 2.0. Google
Google LLC () is an American multinational technology company focusing on search engine technology, online advertising, cloud computing, computer software, quantum computing, e-commerce, artificial intelligence, and consumer electronics. ...
supports OAuth 2.0 as the recommended authorization mechanism for all of its API
An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software Interface (computing), interface, offering a service to other pieces of software. A document or standa ...
s. Microsoft
Microsoft Corporation is an American multinational technology corporation producing computer software, consumer electronics, personal computers, and related services headquartered at the Microsoft Redmond campus located in Redmond, Washing ...
also supports OAuth 2.0 for various APIs and its Azure Active Directory service, which is used to secure many Microsoft and third party APIs.
OAuth can be used as an authorizing mechanism to access secured RSS
RSS ( RDF Site Summary or Really Simple Syndication) is a web feed that allows users and applications to access updates to websites in a standardized, computer-readable format. Subscribing to RSS feeds can allow a user to keep track of many di ...
/Atom
Every atom is composed of a nucleus and one or more electrons bound to the nucleus. The nucleus is made of one or more protons and a number of neutrons. Only the most common variety of hydrogen has no neutrons.
Every solid, liquid, gas, and ...
feeds. Access to RSS/ATOM feeds that require authentication has always been an issue. For example, an RSS feed from a secured Google Site could not have been accessed using Google Reader
Google Reader was an RSS/Atom feed aggregator operated by Google. It was created in early 2005 by Google engineer Chris Wetherell and launched on October 7, 2005, through Google Labs. Google Reader grew in popularity to support a number of progra ...
. Instead, three-legged OAuth would have been used to authorize that RSS client to access the feed from the Google Site.
OAuth and other standards
OAuth is a service that is complementary to and distinct fromOpenID
OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party identity provider ...
. OAuth is unrelated to OATH
Traditionally an oath (from Anglo-Saxon ', also called plight) is either a statement of fact or a promise taken by a sacrality as a sign of verity. A common legal substitute for those who conscientiously object to making sacred oaths is to ...
, which is a reference architecture for authentication, not a standard for authorization. However, OAuth is directly related to OpenID Connect
OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party identity provider ...
(OIDC), since OIDC is an authentication layer built on top of OAuth 2.0. OAuth is also unrelated to XACML
XACML stands for "eXtensible Access Control Markup Language". The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests a ...
, which is an authorization policy standard. OAuth can be used in conjunction with XACML, where OAuth is used for ownership consent and access delegation whereas XACML is used to define the authorization policies (e.g., managers can view documents in their region).
OpenID vis-à-vis pseudo-authentication using OAuth
OAuth is an ''authorization'' protocol, rather than an ''authentication'' protocol. Using OAuth on its own as an authentication method may be referred to as pseudo-authentication. The following diagrams highlight the differences between using OpenID (specifically designed as an authentication protocol) and OAuth for authorization. The communication flow in both processes is similar: # (Not pictured) The user requests a resource or site login from the application. # The site sees that the user is not authenticated. It formulates a request for the identity provider, encodes it, and sends it to the user as part of a redirect URL. # The user's browser makes a request to the redirect URL for the identity provider, including the application's request # If necessary, the identity provider authenticates the user (perhaps by asking them for their username and password) # Once the identity provider is satisfied that the user is sufficiently authenticated, it processes the application's request, formulates a response, and sends that back to the user along with a redirect URL back to the application. # The user's browser requests the redirect URL that goes back to the application, including the identity provider's response # The application decodes the identity provider's response, and carries on accordingly. # (OAuth only) The response includes an access token which the application can use to gain direct access to the identity provider's services on the user's behalf. The crucial difference is that in the OpenID ''authentication'' use case, the response from the identity provider is an assertion of identity; while in the OAuth ''authorization'' use case, the identity provider is also anAPI
An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software Interface (computing), interface, offering a service to other pieces of software. A document or standa ...
provider, and the response from the identity provider is an access token that may grant the application ongoing access to some of the identity provider's APIs, on the user's behalf. The access token acts as a kind of "valet key" that the application can include with its requests to the identity provider, which prove that it has permission from the user to access those APIs.
Because the identity provider typically (but not always) authenticates the user as part of the process of granting an OAuth access token, it is tempting to view a successful OAuth access token request as an authentication method itself. However, because OAuth was not designed with this use case in mind, making this assumption can lead to major security flaws.
OAuth and XACML
XACML
XACML stands for "eXtensible Access Control Markup Language". The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests a ...
is a policy-based, attribute-based access control Attribute-based access control (ABAC), also known as policy-based access control for IAM, defines an access control paradigm whereby a subject's authorization to perform a set of operations is determined by evaluating attributes associated with the ...
authorization framework. It provides:
* An access control architecture.
* A policy language with which to express a wide range of access control policies including policies that can use consents handled / defined via OAuth.
* A request / response scheme to send and receive authorization requests.
XACML and OAuth can be combined to deliver a more comprehensive approach to authorization. OAuth does not provide a policy language with which to define access control policies. XACML can be used for its policy language.
Where OAuth focuses on delegated access (I, the user, grant Twitter access to my Facebook wall), and identity-centric authorization, XACML takes an attribute-based approach which can consider attributes of the user, the action, the resource, and the context (who, what, where, when, how). With XACML it is possible to define policies such as
* Managers can view documents in their department
* Managers can edit documents they own in draft mode
XACML provides more fine-grained access control than OAuth does. OAuth is limited in granularity to the coarse functionality (the scopes) exposed by the target service. As a result, it often makes sense to combine OAuth and XACML together where OAuth will provide the delegated access use case and consent management and XACML will provide the authorization policies that work on the applications, processes, and data.
Lastly, XACML can work transparently across multiple stacks ( APIs, web SSO, ESBs, home-grown apps, databases...). OAuth focuses exclusively on HTTP-based apps.
Controversy
Eran Hammer resigned from his role of lead author for the OAuth 2.0 project, withdrew from theIETF working group
The Internet Engineering Task Force (IETF) is a standards organization for the Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and a ...
, and removed his name from the specification in July 2012. Hammer cited a conflict between web and enterprise cultures as his reason for leaving, noting that IETF is a community that is "all about enterprise use cases" and "not capable of simple". "What is now offered is a blueprint for an authorization protocol", he noted, "that is the enterprise way", providing a "whole new frontier to sell consulting services and integration solutions". In comparing OAuth 2.0 with OAuth 1.0, Hammer points out that it has become "more complex, less interoperable, less useful, more incomplete, and most importantly, less secure". He explains how architectural changes for 2.0 unbound tokens from clients, removed all signatures and cryptography at a protocol level and added expiring tokens (because tokens could not be revoked) while complicating the processing of authorization. Numerous items were left unspecified or unlimited in the specification because "as has been the nature of this working group, no issue is too small to get stuck on or leave open for each implementation to decide."
David Recordon
David Recordon (born September 4, 1986) is an American technologist with an open standards and open source background. He is currently the Chief Technology Officer at Rebellion Defense. From January 2021 to September 2022, he served as the Di ...
later also removed his name from the specifications for unspecified reasons. Dick Hardt
Dick Clarence Hardt (born May 28, 1963) is the founder of ''SignIn.Org'' and is an advocate of Identity 2.0.
Hardt has spoken at tech events such as Web 2.0, Supernova, Digital ID World, ETech, OSCON, PICNIC, International World Wide Web Confer ...
took over the editor role, and the framework was published in October 2012.
David Harris, author of the email client Pegasus Mail
Pegasus Mail is a proprietary email client developed by David Harris (who also develops the Mercury Mail Transport System). It was originally released in 1990 for internal and external mail on NetWare networks with MS-DOS and later Apple Macint ...
, has criticised OAuth 2.0 as "an absolute dog's breakfast", requiring developers to write custom modules specific to each service (Gmail, Microsoft Mail services, etc.), and to register specifically with them.
See also
* List of OAuth providers *Data portability Data portability is a concept to protect users from having their data stored in "silos" or "walled gardens" that are incompatible with one another, i.e. closed platforms, thus subjecting them to vendor lock-in and making the creation of data backups ...
* IndieAuth
IndieAuth is an open standard decentralized authentication protocol that uses OAuth 2.0 and enables services to verify the identity of a user represented by a URL as well as to obtain an access token that can be used to access resources under the c ...
* Mozilla Persona
Mozilla Persona was a decentralized authentication system for the web, based on the open BrowserID protocol prototyped by Mozilla and standardized by IETF. It was launched in July 2011, but after failing to achieve traction, Mozilla announced in ...
* SAML
Security Assertion Markup Language (SAML, pronounced ''SAM-el'', ) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based m ...
* User-Managed Access
User-Managed Access (UMA) is an OAuth-based access management protocol standard. Version 1.0 of the standard was approved by the Kantara Initiative on March 23, 2015.
As described by the charter of the group that developed UMA, the purpose of the ...
References
External links
oauth.com
oauth.net
{{Authentication APIs Cloud standards Internet protocols Computer-related introductions in 2007 Computer access control Computer access control protocols