|
XACML
__NOTOC__ The eXtensible Access Control Markup Language (XACML) is an XML-based standard markup language for specifying access control policies. The standard, published by OASIS (organization), OASIS, defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies. XACML is primarily an attribute-based access control system. In XACML, attributes – information about the subject accessing a resource, the resource to be addressed, and the environment – act as inputs for the decision of whether access is granted or not. XACML can also be used to implement role-based access control.See for example In XACML, access control decisions to be taken are expressed as Rules. Each Rule comprises a series of conditions which decide whether a given request is approved or not. If a Rule is applicable to a request but the conditions within t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
XACML Architecture & Flow
__NOTOC__ The eXtensible Access Control Markup Language (XACML) is an XML-based standard markup language for specifying access control policies. The standard, published by OASIS, defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies. XACML is primarily an attribute-based access control system. In XACML, attributes – information about the subject accessing a resource, the resource to be addressed, and the environment – act as inputs for the decision of whether access is granted or not. XACML can also be used to implement role-based access control.See for example In XACML, access control decisions to be taken are expressed as Rules. Each Rule comprises a series of conditions which decide whether a given request is approved or not. If a Rule is applicable to a request but the conditions within the Rule fail to evalua ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
ALFA (XACML)
The Abbreviated Language for Authorization (ALFA) is a domain-specific language used in the formulation of access-control policies. History Origin XACML, the eXtensible Access Control Markup Language, uses XML as its main encoding language. Writing XACML policies directly in XACML leads to bloated, human-unfriendly text, therefore a new, more lightweight, notation was necessary. Axiomatics researcher, Pablo Giambiagi, therefore designed ALFA, the Axiomatics Language for Authorization. ALFA maps directly into XACML. ALFA contains the same structural elements as XACML i.e. PolicySet, Policy, and Rule. Axiomatics donates ALFA to OASIS In March 2014, Axiomatics announced it was donating ALFA to the OASIS XACML Technical Committee in order to advance its standardization. ALFA was consequently renamed Abbreviated Language for Authorization and filed for standardization. Sample use cases * Medical use case: doctors can view the medical records of patients they have a rela ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
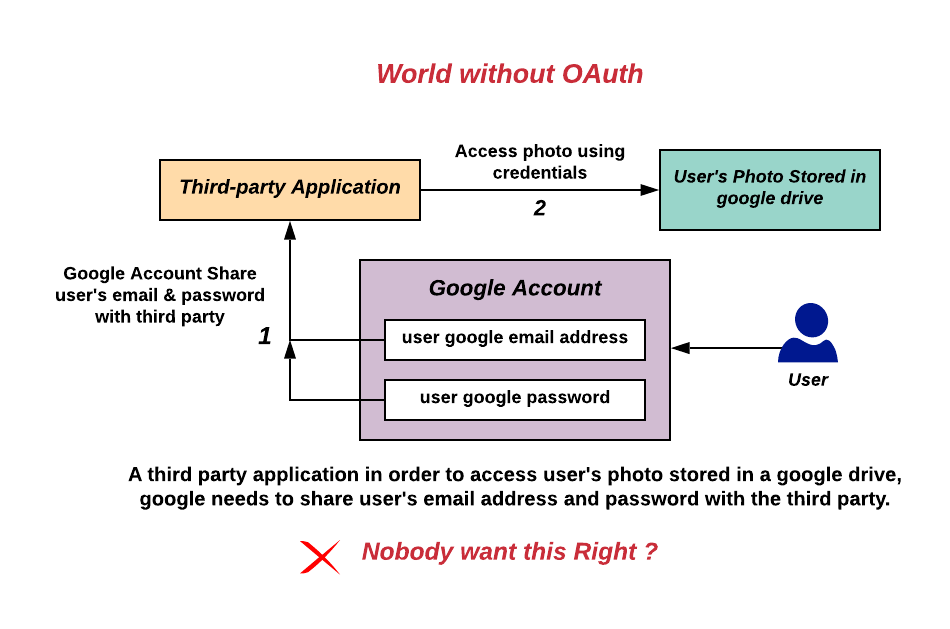
OAuth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Attribute-based Access Control
Attribute-based access control (ABAC), also known as policy-based access control for IAM, defines an access control paradigm whereby a subject's authorization to perform a set of operations is determined by evaluating attributes associated with the subject, object, requested operations, and, in some cases, environment attributes. ABAC is a method of implementing access control policies that is highly adaptable and can be customized using a wide range of attributes, making it suitable for use in distributed or rapidly changing environments. The only limitations on the policies that can be implemented with ABAC are the capabilities of the computational language and the availability of relevant attributes. ABAC policy rules are generated as Boolean functions of the subject's attributes, the object's attributes, and the environment attributes. Unlike role-based access control (RBAC), which defines roles that carry a specific set of privileges associated with them and to which subjects ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
OASIS (organization)
The Organization for the Advancement of Structured Information Standards (OASIS; ) is an Trade association, industry consortium that develops Technical standard, technical standards for information technology. History OASIS was founded under the name "SGML Open" in 1993. It began as a trade association of Standard Generalized Markup Language (SGML) tool vendors to cooperatively promote the adoption of SGML through mainly educational activities, though some amount of technical activity was also pursued including an update of the CALS Table Model specification and specifications for fragment interchange and entity management. In 1998, with the movement of the industry to XML, SGML Open changed its emphasis from SGML to XML, and changed its name to OASIS Open to be inclusive of XML and reflect an expanded scope of technical work and standards. The focus of the consortium's activities also moved from promoting adoption (as XML was getting much attention on its own) to developing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
PERMIS
PERMIS (PrivilEge and Role Management Infrastructure Standards) is a sophisticated policy-based authorization system that implements an enhanced version of the U.S. National Institute of Standards and Technology (NIST) standard Role-Based Access Control (RBAC) model. PERMIS supports the distributed assignment of both roles and attributes to users by multiple distributed attribute authorities, unlike the NIST model which assumes the centralised assignment of roles to users. PERMIS provides a cryptographically secure privilege management infrastructure ( PMI) using public key encryption technologies and X.509 Attribute certificates to maintain users' attributes. PERMIS does not provide any authentication mechanism, but leaves it up to the application to determine what to use. PERMIS's strength comes from its ability to be integrated into virtually any application and any authentication scheme like Shibboleth (Internet2), Kerberos, username/passwords, Grid proxy certificates and Pub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Model-driven Security
Model-driven security (MDS) means applying model-driven approaches (and especially the concepts behind model-driven software development) to security. Development of the concept The general concept of Model-driven security in its earliest forms has been around since the late 1990s (mostly in university research), and was first commercialized around 2002. There is also a body of later scientific research in this area, which continues to this day. A more specific definition of Model-driven security specifically applies model-driven approaches to automatically generate technical security implementations from security requirements models. In particular, "Model driven security (MDS) is the tool supported process of modelling security requirements at a high level of abstraction, and using other information sources available about the system (produced by other stakeholders). These inputs, which are expressed in Domain Specific Languages (DSL), are then transformed into enforceable secur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Role-based Access Control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users, and to implementing mandatory access control (MAC) or discretionary access control, discretionary access control (DAC). Role-based access control is a policy-neutral access control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations. RBAC can be used to facilitate administration of security in large organizations with hundreds of users and thousands of permissions. Although RBAC is different from MAC and DAC access control frameworks, it can enforce these policies without any complication. Design Within an organization, role (computer science), roles are created for various job functions. The permiss ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Security Assertion Markup Language
Security Assertion Markup Language (SAML, pronounced ''SAM-el'', ) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based markup language for security assertions (statements that service providers use to make access-control decisions). SAML is also: * A set of XML-based protocol messages * A set of protocol message bindings * A set of profiles (utilizing all of the above) An important use case that SAML addresses is web-browser single sign-on (SSO). Single sign-on is relatively easy to accomplish within a security domain (using cookies, for example) but extending SSO across security domains is more difficult and resulted in the proliferation of non-interoperable proprietary technologies. The SAML Web Browser SSO profile was specified and standardized to promote interoperability.J. Hughes et al. ''Profiles for the OASIS Security Assertion Markup Langu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Authorization
Authorization or authorisation (see American and British English spelling differences#-ise, -ize (-isation, -ization), spelling differences), in information security, computer security and identity management, IAM (Identity and Access Management), is the function of specifying rights/privileges for accessing resources, in most cases through an access policy, and then deciding whether a particular ''subject'' has privilege to access a particular ''resource''. Examples of ''subjects'' include human users, computer software and other Computer hardware, hardware on the computer. Examples of ''resources'' include individual files or an item's data, computer programs, computer Computer hardware, devices and functionality provided by computer applications. For example, user accounts for human resources staff are typically configured with authorization for accessing employee records. Authorization is closely related to access control, which is what enforces the authorization policy by d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
SAML
Security Assertion Markup Language (SAML, pronounced ''SAM-el'', ) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider (SAML), identity provider and a service provider (SAML), service provider. SAML is an XML-based markup language for security assertions (statements that service providers use to make access-control decisions). SAML is also: * A set of XML-based protocol messages * A set of protocol message bindings * A set of profiles (utilizing all of the above) An important use case that SAML addresses is web browser, web-browser single sign-on (SSO). Single sign-on is relatively easy to accomplish within a security domain (using HTTP cookie, cookies, for example) but extending SSO across security domains is more difficult and resulted in the proliferation of non-interoperable proprietary technologies. The SAML Web Browser SSO profile was specified and standardized to promote interoperability.J.&nb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Access Control
In physical security and information security, access control (AC) is the action of deciding whether a subject should be granted or denied access to an object (for example, a place or a resource). The act of ''accessing'' may mean consuming, entering, or using. It is often used interchangeably with authorization, although the authorization may be granted well in advance of the access control decision. Access control on digital platforms is also termed admission control. The protection of external databases is essential to preserve digital security. Access control is considered to be a significant aspect of privacy that should be further studied. Access control policy (also access policy) is part of an organization’s security policy. In order to verify the access control policy, organizations use an access control model. General security policies require designing or selecting appropriate security controls to satisfy an organization's risk appetite - access policies ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |