Hill Cipher on:
[Wikipedia]
[Google]
[Amazon]
 In
In
PDF
* Lester S. Hill, Concerning Certain Linear Transformation Apparatus of Cryptography, ''The American Mathematical Monthly'' Vol.38, 1931, pp. 135–154. * Jeffrey Overbey, William Traves, and Jerzy Wojdylo, On the Keyspace of the Hill Cipher, '' Cryptologia'', Vol.29, No.1, January 2005, pp59–72.
CiteSeerX
PDF
Hill Cipher Web App
implements the Hill cipher and shows the matrices involved *
Hill Cipher Explained
illustrates the linear algebra behind the Hill Cipher *
Hill's Cipher Calculator
outlines the Hill Cipher with a Web page {{DEFAULTSORT:Hill Cipher Classical ciphers
 In
In classical cryptography
In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern cryptographic algorithms, most classical ciphers can be practically computed and solved by hand. ...
, the Hill cipher is a polygraphic substitution cipher based on linear algebra
Linear algebra is the branch of mathematics concerning linear equations such as:
:a_1x_1+\cdots +a_nx_n=b,
linear maps such as:
:(x_1, \ldots, x_n) \mapsto a_1x_1+\cdots +a_nx_n,
and their representations in vector spaces and through matrices.
...
. Invented by Lester S. Hill
Lester S. Hill (1891–1961) was an American mathematician and educator who was interested in applications of mathematics to communications. He received a bachelor's degree from Columbia College (1911) and a Ph.D. from Yale University (19 ...
in 1929, it was the first polygraphic cipher in which it was practical (though barely) to operate on more than three symbols at once.
The following discussion assumes an elementary knowledge of matrices
Matrix most commonly refers to:
* ''The Matrix'' (franchise), an American media franchise
** ''The Matrix'', a 1999 science-fiction action film
** "The Matrix", a fictional setting, a virtual reality environment, within ''The Matrix'' (franchis ...
.
Encryption
Each letter is represented by a number modulo 26. Though this is not an essential feature of the cipher, this simple scheme is often used: To encrypt a message, each block of ''n'' letters (considered as an ''n''-componentvector
Vector most often refers to:
*Euclidean vector, a quantity with a magnitude and a direction
*Vector (epidemiology), an agent that carries and transmits an infectious pathogen into another living organism
Vector may also refer to:
Mathematic ...
) is multiplied by an invertible ''n'' × ''n'' matrix
Matrix most commonly refers to:
* ''The Matrix'' (franchise), an American media franchise
** ''The Matrix'', a 1999 science-fiction action film
** "The Matrix", a fictional setting, a virtual reality environment, within ''The Matrix'' (franchis ...
, against modulus 26. To decrypt the message, each block is multiplied by the inverse of the matrix used for encryption.
The matrix used for encryption is the cipher key
Key or The Key may refer to:
Common meanings
* Key (cryptography), a piece of information that controls the operation of a cryptography algorithm
* Key (lock), device used to control access to places or facilities restricted by a lock
* Key (map ...
, and it should be chosen randomly from the set of invertible ''n'' × ''n'' matrices ( modulo 26). The cipher can, of course, be adapted to an alphabet with any number of letters; all arithmetic just needs to be done modulo the number of letters instead of modulo 26.
Consider the message 'ACT', and the key below (or GYBNQKURP in letters):
:
Since 'A' is 0, 'C' is 2 and 'T' is 19, the message is the vector:
:
Thus the enciphered vector is given by:
:
which corresponds to a ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
of 'POH'. Now, suppose that our message is instead 'CAT', or:
:
This time, the enciphered vector is given by:
:
which corresponds to a ciphertext of 'FIN'. Every letter has changed. The Hill cipher has achieved Shannon's diffusion
Diffusion is the net movement of anything (for example, atoms, ions, molecules, energy) generally from a region of higher concentration to a region of lower concentration. Diffusion is driven by a gradient in Gibbs free energy or chemical p ...
, and an ''n''-dimensional Hill cipher can diffuse fully across ''n'' symbols at once.
Decryption
In order to decrypt, we turn the ciphertext back into a vector, then simply multiply by theinverse matrix
In linear algebra, an -by- square matrix is called invertible (also nonsingular or nondegenerate), if there exists an -by- square matrix such that
:\mathbf = \mathbf = \mathbf_n \
where denotes the -by- identity matrix and the multiplicati ...
of the key matrix (IFKVIVVMI in letters). We find that, modulo 26, the inverse of the matrix used in the previous example is:
:
Taking the previous example ciphertext of 'POH', we get:
:
which gets us back to 'ACT', as expected.
Two complications exist in picking the encrypting matrix:
# Not all matrices have an inverse. The matrix will have an inverse if and only if its determinant
In mathematics, the determinant is a scalar value that is a function of the entries of a square matrix. It characterizes some properties of the matrix and the linear map represented by the matrix. In particular, the determinant is nonzero if and ...
is not zero.
# The determinant of the encrypting matrix must not have any common factors with the modular base.
Thus, if we work modulo 26 as above, the determinant must be nonzero, and must not be divisible by 2 or 13. If the determinant is 0, or has common factors with the modular base, then the matrix cannot be used in the Hill cipher, and another matrix must be chosen (otherwise it will not be possible to decrypt). Fortunately, matrices which satisfy the conditions to be used in the Hill cipher are fairly common.
For our example key matrix:
:
So, modulo 26, the determinant is 25. Since and , 25 has no common factors with 26, and this matrix can be used for the Hill cipher.
The risk of the determinant having common factors with the modulus can be eliminated by making the modulus prime
A prime number (or a prime) is a natural number greater than 1 that is not a product of two smaller natural numbers. A natural number greater than 1 that is not prime is called a composite number. For example, 5 is prime because the only ways ...
. Consequently, a useful variant of the Hill cipher adds 3 extra symbols (such as a space, a period and a question mark) to increase the modulus to 29.
Example
Let : be the key and suppose the plaintext message is 'HELP'. Then this plaintext is represented by two pairs : Then we compute : and : and continue encryption as follows: : The matrix ''K'' is invertible, hence exists such that . The inverse of ''K'' can be computed by using theformula
In science, a formula is a concise way of expressing information symbolically, as in a mathematical formula or a ''chemical formula''. The informal use of the term ''formula'' in science refers to the general construct of a relationship betwee ...
This formula still holds after a modular reduction if a modular multiplicative inverse In mathematics, particularly in the area of arithmetic, a modular multiplicative inverse of an integer is an integer such that the product is congruent to 1 with respect to the modulus .. In the standard notation of modular arithmetic this congr ...
is used to compute Hence in this case, we compute
:
:
Then we compute
: and
:
Therefore,
:.
Security
The basic Hill cipher is vulnerable to aknown-plaintext attack
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib), and its encrypted version (ciphertext). These can be used to reveal further secret information such as secr ...
because it is completely linear
Linearity is the property of a mathematical relationship (''function'') that can be graphically represented as a straight line. Linearity is closely related to '' proportionality''. Examples in physics include rectilinear motion, the linear r ...
. An opponent who intercepts plaintext/ciphertext character pairs can set up a linear system which can (usually) be easily solved; if it happens that this system is indeterminate, it is only necessary to add a few more plaintext/ciphertext pairs. Calculating this solution by standard linear algebra algorithms then takes very little time.
While matrix multiplication alone does not result in a secure cipher it is still a useful step when combined with other non-linear
In mathematics and science, a nonlinear system is a system in which the change of the output is not proportional to the change of the input. Nonlinear problems are of interest to engineers, biologists, physicists, mathematicians, and many other ...
operations, because matrix multiplication can provide diffusion
Diffusion is the net movement of anything (for example, atoms, ions, molecules, energy) generally from a region of higher concentration to a region of lower concentration. Diffusion is driven by a gradient in Gibbs free energy or chemical p ...
. For example, an appropriately chosen matrix can guarantee that small differences before the matrix multiplication will result in large differences after the matrix multiplication. Indeed, some modern ciphers use a matrix multiplication step to provide diffusion. For example, the MixColumns step in AES is a matrix multiplication. The function ''g'' in Twofish
In cryptography, Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists of the Advanced Encryption Standard contest, but it was not selected for standardization. Twof ...
is a combination of non-linear S-boxes with a carefully chosen matrix multiplication (MDS).
Key space size
The key space is the set of all possible keys. The key space size is the number of possible keys. The effectivekey size
In cryptography, key size, key length, or key space refer to the number of bits in a key used by a cryptographic algorithm (such as a cipher).
Key length defines the upper-bound on an algorithm's security (i.e. a logarithmic measure of the faste ...
, in number of bits, is the binary logarithm
In mathematics, the binary logarithm () is the power to which the number must be raised to obtain the value . That is, for any real number ,
:x=\log_2 n \quad\Longleftrightarrow\quad 2^x=n.
For example, the binary logarithm of is , the b ...
of the key space size.
There are matrices of dimension ''n'' × ''n''. Thus or about is an upper bound on the key size of the Hill cipher using ''n'' × ''n'' matrices. This is only an upper bound because not every matrix is invertible and thus usable as a key. The number of invertible matrices can be computed via the Chinese Remainder Theorem
In mathematics, the Chinese remainder theorem states that if one knows the remainders of the Euclidean division of an integer ''n'' by several integers, then one can determine uniquely the remainder of the division of ''n'' by the product of thes ...
. I.e., a matrix is invertible modulo 26 if and only if it is invertible both modulo 2 and modulo 13.
The number of invertible ''n'' × ''n'' matrices modulo 2 is equal to the order of the general linear group
In mathematics, the general linear group of degree ''n'' is the set of invertible matrices, together with the operation of ordinary matrix multiplication. This forms a group, because the product of two invertible matrices is again invertible, ...
GL(n,Z2). It is
:
Equally, the number of invertible matrices modulo 13 (i.e. the order of GL(n,Z13)) is
:
The number of invertible matrices modulo 26 is the product of those two numbers. Hence it is
:
Additionally it seems to be prudent to avoid too many zeroes in the key matrix, since they reduce diffusion. The net effect is that the effective keyspace of a basic Hill cipher is about . For a 5 × 5 Hill cipher, that is about 114 bits. Of course, key search is not the most efficient known attack.
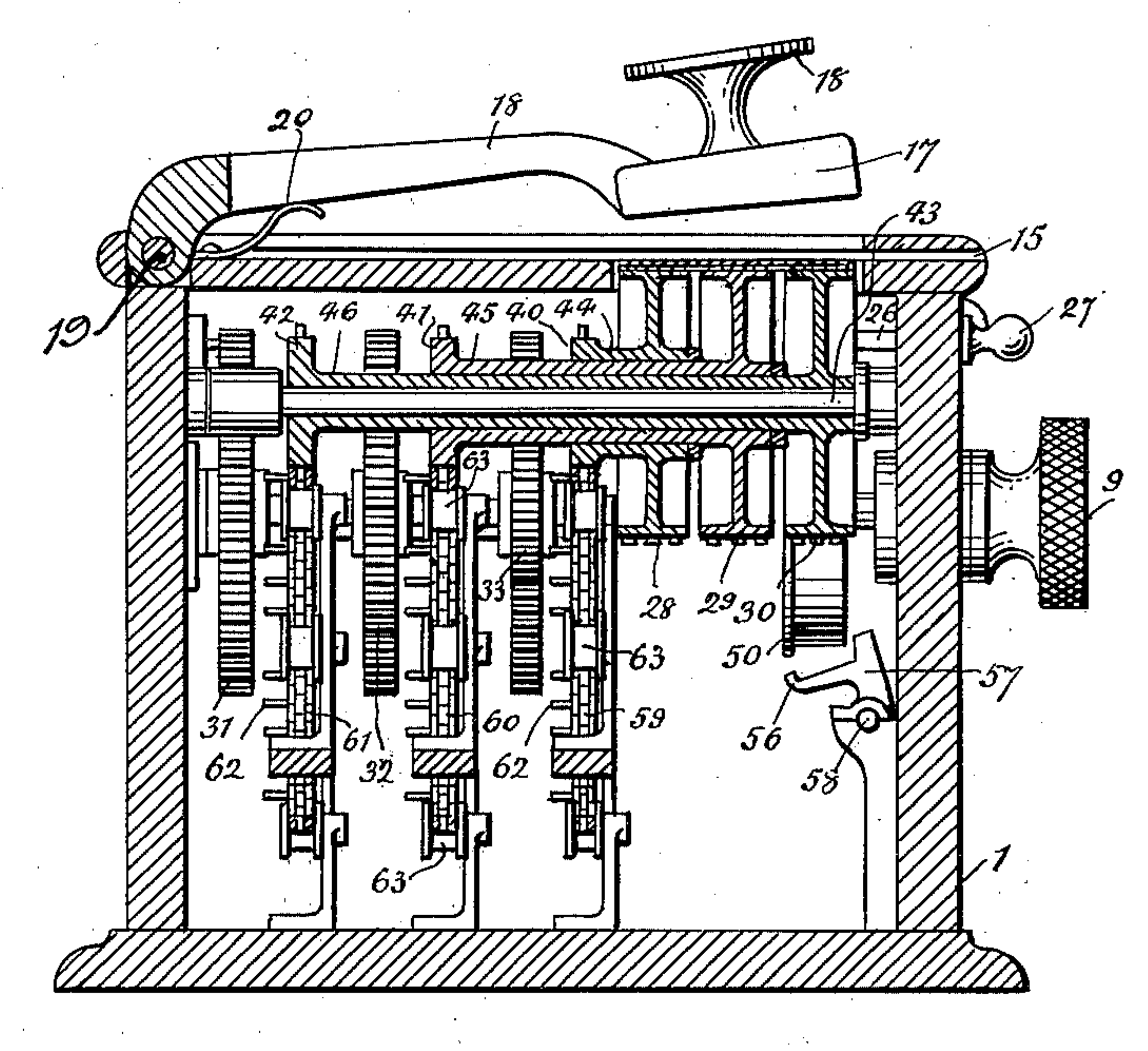
Mechanical implementation
When operating on 2 symbols at once, a Hill cipher offers no particular advantage over Playfair or thebifid cipher
In classical cryptography, the bifid cipher is a cipher which combines the Polybius square with transposition, and uses fractionation to achieve diffusion. It was invented around 1901 by Felix Delastelle.
Operation
First, a mixed alphabet Poly ...
, and in fact is weaker than either, and slightly more laborious to operate by pencil-and-paper. As the dimension increases, the cipher rapidly becomes infeasible for a human to operate by hand.
A Hill cipher of dimension 6 was implemented mechanically. Hill and a partner were awarded a patent
A patent is a type of intellectual property that gives its owner the legal right to exclude others from making, using, or selling an invention for a limited period of time in exchange for publishing an enabling disclosure of the invention."A p ...
() for this device, which performed a 6 × 6 matrix multiplication modulo 26 using a system of gears and chains.
Unfortunately the gearing arrangements (and thus the key) were fixed for any given machine, so triple encryption was recommended for security: a secret nonlinear step, followed by the wide diffusive step from the machine, followed by a third secret nonlinear step. (The much later Even-Mansour cipher also uses an unkeyed diffusive middle step). Such a combination was actually very powerful for 1929, and indicates that Hill apparently understood the concepts of a meet-in-the-middle attack as well as confusion and diffusion. Unfortunately, his machine did not sell.
See also
Other practical "pencil-and-paper" polygraphic ciphers include: *Playfair cipher
The Playfair cipher or Playfair square or Wheatstone–Playfair cipher is a manual symmetric encryption technique and was the first literal digram substitution cipher. The scheme was invented in 1854 by Charles Wheatstone, but bears the name of ...
* Bifid cipher
In classical cryptography, the bifid cipher is a cipher which combines the Polybius square with transposition, and uses fractionation to achieve diffusion. It was invented around 1901 by Felix Delastelle.
Operation
First, a mixed alphabet Poly ...
* Trifid cipher The trifid cipher is a classical cipher invented by Félix Delastelle and described in 1902. Extending the principles of Delastelle's earlier bifid cipher, it combines the techniques of fractionation and transposition to achieve a certain amount of ...
References
* Lester S. Hill, Cryptography in an Algebraic Alphabet, ''The American Mathematical Monthly'' Vol.36, June–July 1929, pp. 306–312.* Lester S. Hill, Concerning Certain Linear Transformation Apparatus of Cryptography, ''The American Mathematical Monthly'' Vol.38, 1931, pp. 135–154. * Jeffrey Overbey, William Traves, and Jerzy Wojdylo, On the Keyspace of the Hill Cipher, '' Cryptologia'', Vol.29, No.1, January 2005, pp59–72.
CiteSeerX
External links
*Hill Cipher Web App
implements the Hill cipher and shows the matrices involved *
Hill Cipher Explained
illustrates the linear algebra behind the Hill Cipher *
Hill's Cipher Calculator
outlines the Hill Cipher with a Web page {{DEFAULTSORT:Hill Cipher Classical ciphers