Government surveillance on:
[Wikipedia]
[Google]
[Amazon]

 Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing,
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing,
 The vast majority of computer surveillance involves the monitoring of
The vast majority of computer surveillance involves the monitoring of

 Surveillance cameras, or security cameras, are video cameras used for the purpose of observing an area. They are often connected to a recording device or
Surveillance cameras, or security cameras, are video cameras used for the purpose of observing an area. They are often connected to a recording device or  The
The
 One common form of surveillance is to create maps of
One common form of surveillance is to create maps of
 Biometric surveillance is a technology that measures and analyzes human physical and/or behavioral characteristics for authentication, identification, or screening purposes. Examples of physical characteristics include fingerprints, DNA, and facial patterns. Examples of mostly behavioral characteristics include gait (a person's manner of walking) or voice.
Facial recognition is the use of the unique configuration of a person's facial features to accurately identify them, usually from surveillance video. Both the Department of Homeland Security and
Biometric surveillance is a technology that measures and analyzes human physical and/or behavioral characteristics for authentication, identification, or screening purposes. Examples of physical characteristics include fingerprints, DNA, and facial patterns. Examples of mostly behavioral characteristics include gait (a person's manner of walking) or voice.
Facial recognition is the use of the unique configuration of a person's facial features to accurately identify them, usually from surveillance video. Both the Department of Homeland Security and
Facial thermographs
are in development, which allow machines to identify certain emotions in people such as fear or stress, by measuring the temperature generated by blood flow to different parts of the face. Law enforcement officers believe that this has potential for them to identify when a suspect is nervous, which might indicate that they are hiding something, lying, or worried about something. I
his paper
in
 Aerial surveillance is the gathering of surveillance, usually visual imagery or video, from an airborne vehicleŌĆösuch as an
Aerial surveillance is the gathering of surveillance, usually visual imagery or video, from an airborne vehicleŌĆösuch as an  The
The
United States v. Miller
' (1976), data held by third parties is generally not subject to Fourth Amendment warrant requirements.
 One of the simplest forms of identification is the carrying of credentials. Some nations have an
One of the simplest forms of identification is the carrying of credentials. Some nations have an
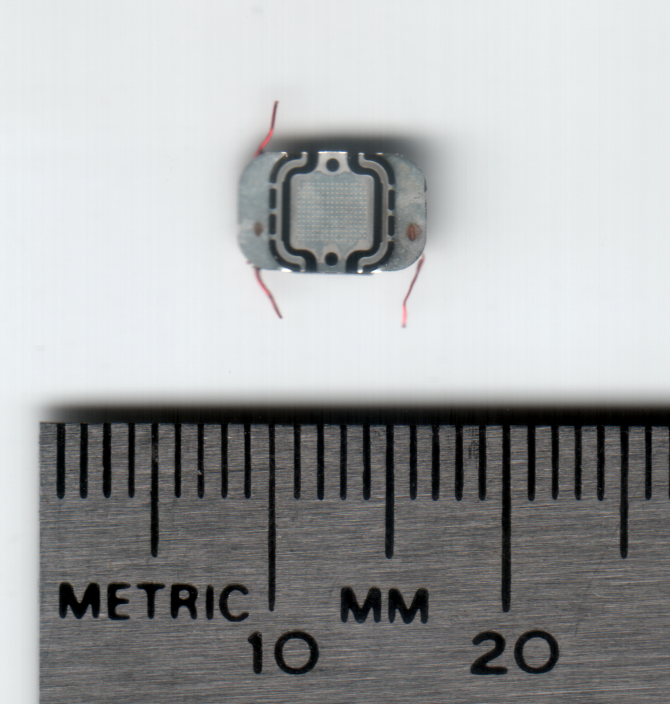
 A human microchip implant is an identifying integrated circuit device or
A human microchip implant is an identifying integrated circuit device or
 In the U.S., police have planted hidden
In the U.S., police have planted hidden

Jeroen van Rest Another method on how surveillance can be used to fight criminal activity is by linking the information stream obtained from them to a recognition system (for instance, a camera system that has its feed run through a facial recognition system). This can for instance auto-recognize fugitives and direct police to their location. A distinction here has to be made however on the type of surveillance employed. Some people that say support video surveillance in city streets may not support indiscriminate telephone taps and vice versa. Besides the types, the way in how this surveillance is done also matters a lot; i.e. indiscriminate telephone taps are supported by much fewer people than say telephone taps done only to people suspected of engaging in illegal activities. Surveillance can also be used to give human operatives a tactical advantage through improved situational awareness, or through the use of automated processes, i.e.

 With the advent of programs such as the
With the advent of programs such as the
 Programs such as the
Programs such as the
"Your Face is not a bar code: arguments against automatic face recognition in public places"
Retrieved November 14, 2004. Surveillance techniques are not created equal; among the many
ACLU, "The Surveillance-Industrial Complex: How the American Government Is Conscripting Businesses and Individuals in the Construction of a Surveillance Society"
Balkin, Jack M. (2008). "The Constitution in the National Surveillance State", Yale Law School
Bibo, Didier and Delmas-Marty, "The State and Surveillance: Fear and Control"
EFF Privacy Resources
ICO. (September 2006). "A Report on the Surveillance Society for the Information Commissioner by the Surveillance Studies Network".
*
ĆöFBI counterintelligence programs designed to neutralize political dissidents
ŌĆō A Short History of Electronic Surveillance in the United States
EFF Legal CasesGuide to lawful intercept legislation around the world

 Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing,
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing
Management (or managing) is the administration of an organization, whether it is a business, a nonprofit organization, or a government body. It is the art and science of managing resources of the business.
Management includes the activities o ...
or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television
Closed-circuit television (CCTV), also known as video surveillance, is the use of video cameras to transmit a signal to a specific place, on a limited set of monitors. It differs from broadcast television in that the signal is not openly t ...
(CCTV), or interception of electronically transmitted information like Internet traffic
Internet traffic is the flow of data within the entire Internet, or in certain network links of its constituent networks. Common traffic measurements are total volume, in units of multiples of the byte, or as transmission rates in bytes per cert ...
. It can also include simple technical methods, such as human intelligence gathering and postal interception
Postal interception is the act of retrieving another person's mail for the purpose of either ensuring that the mail is not delivered to the recipient, or to spy on them.
For instance, the American Central Intelligence Agency (CIA) and Federal Bur ...
.
Surveillance is used by citizens for protecting their neighborhoods. And by government
A government is the system or group of people governing an organized community, generally a state.
In the case of its broad associative definition, government normally consists of legislature, executive, and judiciary. Government is a ...
s for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to gather intelligence on criminals, their competitors, suppliers or customers. Religious
Religion is usually defined as a social system, social-cultural system of designated religious behaviour, behaviors and practices, morality, morals, beliefs, worldviews, religious text, texts, sacred site, sanctified places, prophecy, prophecie ...
organisations charged with detecting heresy
Heresy is any belief or theory that is strongly at variance with established beliefs or customs, in particular the accepted beliefs of a church or religious organization. The term is usually used in reference to violations of important religi ...
and heterodoxy
In religion, heterodoxy (from Ancient Greek: , "other, another, different" + , "popular belief") means "any opinions or doctrines at variance with an official or orthodox position". Under this definition, heterodoxy is similar to unorthodoxy, wh ...
may also carry out surveillance.
Auditor
An auditor is a person or a firm appointed by a company to execute an audit.Practical Auditing, Kul Narsingh Shrestha, 2012, Nabin Prakashan, Nepal To act as an auditor, a person should be certified by the regulatory authority of accounting and au ...
s carry out a form of surveillance.
A byproduct of surveillance is that it can unjustifiably violate people's privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
The domain of privacy partially overlaps with security, which can include the concepts of a ...
and is often criticized by civil liberties
Civil liberties are guarantees and freedoms that governments commit not to abridge, either by constitution, legislation, or judicial interpretation, without due process. Though the scope of the term differs between countries, civil liberties may ...
activists. Liberal democracies
Liberal democracy is the combination of a liberal political ideology that operates under an indirect democratic form of government. It is characterized by elections between multiple distinct political parties, a separation of powers into diff ...
may have laws that seek to restrict governmental and private use of surveillance, whereas authoritarian
Authoritarianism is a political system characterized by the rejection of political plurality, the use of strong central power to preserve the political ''status quo'', and reductions in the rule of law, separation of powers, and democratic votin ...
governments seldom have any domestic restrictions.
Espionage
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangibl ...
is by definition covert and typically illegal according to the rules of the observed party, whereas most types of surveillance are overt and are considered legitimate. International espionage
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangibl ...
seems to be common among all types of countries.
Methods
Computer
 The vast majority of computer surveillance involves the monitoring of
The vast majority of computer surveillance involves the monitoring of data
In the pursuit of knowledge, data (; ) is a collection of discrete values that convey information, describing quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted ...
and traffic
Traffic comprises pedestrians, vehicles, ridden or herded animals, trains, and other conveyances that use public ways (roads) for travel and transportation.
Traffic laws govern and regulate traffic, while rules of the road include traffic ...
on the Internet
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a '' network of networks'' that consists of private, pub ...
. In the United States for example, under the Communications Assistance For Law Enforcement Act
The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton (Pub. L. No. 103-414, 108 Stat. 4279, codified at 47 ...
, all phone calls and broadband Internet traffic (emails, web traffic, instant messaging, etc.) are required to be available for unimpeded real-time monitoring by federal law enforcement agencies.
There is far too much data on the Internet for human investigators to manually search through all of it. Therefore, automated Internet surveillance computers sift through the vast amount of intercepted Internet traffic to identify and report to human investigators the traffic that is considered interesting or suspicious. This process is regulated by targeting certain "trigger" words or phrases, visiting certain types of web sites, or communicating via email or online chat with suspicious individuals or groups. Billions of dollars per year are spent by agencies, such as the NSA
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collecti ...
, the FBI
The Federal Bureau of Investigation (FBI) is the domestic Intelligence agency, intelligence and Security agency, security service of the United States and its principal Federal law enforcement in the United States, federal law enforcement age ...
and the now-defunct Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology ...
, to develop, purchase, implement, and operate systems such as Carnivore
A carnivore , or meat-eater (Latin, ''caro'', genitive ''carnis'', meaning meat or "flesh" and ''vorare'' meaning "to devour"), is an animal or plant whose food and energy requirements derive from animal tissues (mainly muscle, fat and other sof ...
, NarusInsight
Narus Inc. was a Software industry, software company and Independent software vendor, vendor of big data analytics for cybersecurity.
History
In 1997, Ori Cohen, Vice President of Business and Technology Development for VDONet, founded Narus with ...
, and ECHELON
ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the five signatory states to the UKUSA Security Agreement:Given the 5 dialects that use ...
to intercept and analyze all of this data to extract only the information which is useful to law enforcement and intelligence agencies.
Computers can be a surveillance target because of the personal data stored on them. If someone is able to install software, such as the FBI's Magic Lantern
The magic lantern, also known by its Latin name , is an early type of image projector that used picturesŌĆöpaintings, prints, or photographsŌĆöon transparent plates (usually made of glass), one or more lenses, and a light source. Because a si ...
and CIPAV
The Computer and Internet Protocol Address Verifier (CIPAV) is a data gathering tool that the Federal Bureau of Investigation (FBI) uses to track and gather location data on suspects under electronic surveillance. The software operates on the targ ...
, on a computer system, they can easily gain unauthorized access to this data. Such software could be installed physically or remotely. Another form of computer surveillance, known as van Eck phreaking
Van Eck phreaking, also known as Van Eck radiation, is a form of eavesdropping in which special equipment is used to pick up side-band electromagnetic emissions from electronic devices that correlate to hidden signals or data to recreate these sig ...
, involves reading electromagnetic emanations from computing devices in order to extract data from them at distances of hundreds of meters. The NSA runs a database known as "Pinwale
Pinwale is the code name for a National Security Agency (NSA) collection and retrieval system for so-called "Digital Network Intelligence", including internet e-mail., pag1at archive. It is searchable by monitored NSA analysts.
The existence o ...
", which stores and indexes large numbers of emails of both American citizens and foreigners. Additionally, the NSA runs a program known as PRISM
Prism usually refers to:
* Prism (optics), a transparent optical component with flat surfaces that refract light
* Prism (geometry), a kind of polyhedron
Prism may also refer to:
Science and mathematics
* Prism (geology), a type of sedimentary ...
, which is a data mining system that gives the United States government direct access to information from technology companies. Through accessing this information, the government is able to obtain search history, emails, stored information, live chats, file transfers, and more. This program generated huge controversies in regards to surveillance and privacy, especially from U.S. citizens.
Telephones
The official and unofficial tapping of telephone lines is widespread. In theUnited States
The United States of America (U.S.A. or USA), commonly known as the United States (U.S. or US) or America, is a country primarily located in North America. It consists of 50 states, a federal district, five major unincorporated territorie ...
for instance, the Communications Assistance For Law Enforcement Act (CALEA) requires that all telephone and VoIP communications be available for real-time wiretapping by Federal law enforcement and intelligence agencies. Two major telecommunications companies in the U.S.ŌĆö AT&T Inc. and Verizon
Verizon Communications Inc., commonly known as Verizon, is an American multinational telecommunications conglomerate and a corporate component of the Dow Jones Industrial Average. The company is headquartered at 1095 Avenue of the Americas in ...
ŌĆöhave contracts with the FBI, requiring them to keep their phone call records easily searchable and accessible for Federal agencies, in return for $1.8 million per year. Between 2003 and 2005, the FBI sent out more than 140,000 "National Security Letter
A national security letter (NSL) is an administrative subpoena issued by the United States government to gather information for national security purposes. NSLs do not require prior approval from a judge. The Stored Communications Act, Fair Cred ...
s" ordering phone companies to hand over information about their customers' calling and Internet histories. About half of these letters requested information on U.S. citizens.
Human agents are not required to monitor most calls. Speech-to-text
Speech recognition is an interdisciplinary subfield of computer science and computational linguistics that develops methodologies and technologies that enable the recognition and translation of spoken language into text by computers with the mai ...
software creates machine-readable text from intercepted audio, which is then processed by automated call-analysis programs, such as those developed by agencies such as the Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology ...
, or companies such as Verint
Verint Systems is a Melville, New York-based analytics company which was founded in 2002. The company sells software and hardware products for customer engagement management and business intelligence. Their products are designed to assist clie ...
, and Narus, which search for certain words or phrases, to decide whether to dedicate a human agent to the call.
Law enforcement and intelligence services in the United Kingdom and the United States possess technology to activate the microphones in cell phones remotely, by accessing phones' diagnostic or maintenance features in order to listen to conversations that take place near the person who holds the phone.
The StingRay
Stingrays are a group of sea rays, which are cartilaginous fish related to sharks. They are classified in the suborder Myliobatoidei of the order Myliobatiformes and consist of eight families: Hexatrygonidae (sixgill stingray), Plesiobatidae ( ...
tracker is an example of one of these tools used to monitor cell phone usage in the United States and the United Kingdom. Originally developed for counterterrorism purposes by the military, they work by broadcasting powerful signals that cause nearby cell phones to transmit their IMSI number, just as they would to normal cell phone towers. Once the phone is connected to the device, there is no way for the user to know that they are being tracked. The operator of the stingray is able to extract information such as location, phone calls, and text messages, but it is widely believed that the capabilities of the StingRay extend much further. A lot of controversy surrounds the StingRay because of its powerful capabilities and the secrecy that surrounds it.
Mobile phones are also commonly used to collect location data. The geographical location of a mobile phone (and thus the person carrying it) can be determined easily even when the phone is not being used, using a technique known as multilateration Trilateration is the use of distances (or "ranges") for determining the unknown position coordinates of a point of interest, often around Earth (geopositioning).
When more than three distances are involved, it may be called multilateration, for emph ...
to calculate the differences in time for a signal to travel from the cell phone to each of several cell towers
A cell site, cell tower, or cellular base station is a cellular-enabled mobile device site where antennas and electronic communications equipment are placed (typically on a radio mast, tower, or other raised structure) to create a cell, or adjac ...
near the owner of the phone. The legality of such techniques has been questioned in the United States, in particular whether a court warrant is required. Records for ''one'' carrier alone (Sprint), showed that in a given year federal law enforcement agencies requested customer location data 8 million times.
In response to customers' privacy concerns in the post Edward Snowden
Edward Joseph Snowden (born June 21, 1983) is an American and naturalized Russian former computer intelligence consultant who leaked highly classified information from the National Security Agency (NSA) in 2013, when he was an employee and su ...
era, Apple's iPhone 6 has been designed to disrupt investigative wiretapping
Telephone tapping (also wire tapping or wiretapping in American English) is the monitoring of telephone and Internet-based conversations by a third party, often by covert means. The wire tap received its name because, historically, the monitorin ...
efforts. The phone encrypts e-mails, contacts, and photos with a code generated by a complex mathematical algorithm that is unique to an individual phone, and is inaccessible to Apple. The encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decip ...
feature on the iPhone 6 has drawn criticism from FBI director James B. Comey and other law enforcement officials since even lawful requests to access user content on the iPhone 6 will result in Apple supplying "gibberish" data that requires law enforcement personnel to either break the code themselves or to get the code from the phone's owner. Because the Snowden leaks demonstrated that American agencies can access phones anywhere in the world, privacy concerns in countries with growing markets for smart phones have intensified, providing a strong incentive for companies like Apple
An apple is an edible fruit produced by an apple tree (''Malus domestica''). Apple fruit tree, trees are agriculture, cultivated worldwide and are the most widely grown species in the genus ''Malus''. The tree originated in Central Asia, wh ...
to address those concerns in order to secure their position in the global market.
Although the CALEA requires telecommunication
Telecommunication is the transmission of information by various types of technologies over wire, radio, optical, or other electromagnetic systems. It has its origin in the desire of humans for communication over a distance greater than that fe ...
companies to build into their systems the ability to carry out a lawful wiretap, the law has not been updated to address the issue of smart phones and requests for access to e-mails
Electronic mail (email or e-mail) is a method of exchanging messages ("mail") between people using electronic devices. Email was thus conceived as the electronic (digital) version of, or counterpart to, mail, at a time when "mail" meant ...
and metadata
Metadata is "data that provides information about other data", but not the content of the data, such as the text of a message or the image itself. There are many distinct types of metadata, including:
* Descriptive metadata ŌĆō the descriptive ...
. The Snowden leaks show that the NSA
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collecti ...
has been taking advantage of this ambiguity in the law by collecting metadata on "at least hundreds of millions" of "incidental" targets from around the world. The NSA uses an analytic tool known as CO-TRAVELER in order to track people whose movements intersect and to find any hidden connections with persons of interest.
The Snowden leaks have also revealed that the British Government Communications Headquarters
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the Un ...
(GCHQ) can access information collected by the NSA on American citizens. Once the data has been collected, the GCHQ can hold on to it for up to two years. The deadline can be extended with the permission of a "senior UK official".
Cameras
 Surveillance cameras, or security cameras, are video cameras used for the purpose of observing an area. They are often connected to a recording device or
Surveillance cameras, or security cameras, are video cameras used for the purpose of observing an area. They are often connected to a recording device or IP network
The Internet protocol suite, commonly known as TCP/IP, is a framework for organizing the set of communication protocols used in the Internet and similar computer networks according to functional criteria. The foundational protocols in the suit ...
, and may be watched by a security guard
A security guard (also known as a security inspector, security officer, or protective agent) is a person employed by a government or private party to protect the employing party's assets (property, people, equipment, money, etc.) from a variety ...
or law enforcement officer
A law enforcement officer (LEO), or peace officer in North American English, is a Public sector, public-sector employee whose duties primarily involve the Law enforcement, enforcement of laws. The phrase can include campaign disclosure specialist ...
. Cameras and recording equipment used to be relatively expensive and required human personnel to monitor camera footage, but analysis of footage has been made easier by automated software that organizes digital video footage into a searchable database
In computing, a database is an organized collection of data stored and accessed electronically. Small databases can be stored on a file system, while large databases are hosted on computer clusters or cloud storage. The design of databases sp ...
, and by video analysis software (such as VIRAT Virat or Viraat is an Indian male given name that may refer to the following people:
*Viraat Badhwar (born 1995), Australian golfer
*Virat Kohli (born 1988), Indian cricketer
*Virat Singh (born 1997), Indian cricketer
See also
*VIRAT
*Viraat (di ...
and HumanID). The amount of footage is also drastically reduced by motion sensors which record only when motion is detected. With cheaper production techniques, surveillance cameras are simple and inexpensive enough to be used in home security systems, and for everyday surveillance. Video cameras are one of the most common methods of surveillance.
As of 2016, there are about 350 million surveillance cameras worldwide. About 65% of these cameras are installed in Asia. The growth of CCTV has been slowing in recent years. In 2018, China was reported to have a huge surveillance network of over 170 million CCTV cameras with 400 million new cameras expected to be installed in the next three years, many of which use facial recognition technology
A facial recognition system is a technology capable of matching a human face from a digital image or a video frame against a database of faces. Such a system is typically employed to authenticate users through ID verification services, and ...
.
In the United States
The United States of America (U.S.A. or USA), commonly known as the United States (U.S. or US) or America, is a country primarily located in North America. It consists of 50 states, a federal district, five major unincorporated territorie ...
, the Department of Homeland Security
The United States Department of Homeland Security (DHS) is the U.S. federal executive department responsible for public security, roughly comparable to the interior or home ministries of other countries. Its stated missions involve anti-terr ...
awards billions of dollars per year in Homeland Security grants
Homeland Security Grant Program (HSGP) is a program in the United States established in 2003 and was designated to incorporate all projects that provide funding to local, state, and Federal government agencies by the Department of Homeland Securit ...
for local, state, and federal agencies to install modern video surveillance equipment. For example, the city of Chicago
(''City in a Garden''); I Will
, image_map =
, map_caption = Interactive Map of Chicago
, coordinates =
, coordinates_footnotes =
, subdivision_type = Country
, subdivision_name ...
, Illinois, recently used a $5.1 million Homeland Security grant to install an additional 250 surveillance cameras, and connect them to a centralized monitoring center, along with its preexisting network of over 2000 cameras, in a program known as Operation Virtual Shield
Operation Virtual Shield is a program implemented by Chicago, IL mayor Richard M. Daley, which created the most extensive video surveillance network in the United States by linking more than 3000 surveillance cameras to a centralized monitoring ...
. Speaking in 2009, Chicago Mayor Richard Daley announced that Chicago would have a surveillance camera on every street corner by 2016. New York City
New York, often called New York City or NYC, is the List of United States cities by population, most populous city in the United States. With a 2020 population of 8,804,190 distributed over , New York City is also the L ...
received a $350 million grant towards the development of the Domain Awareness System The Domain Awareness System is the largest digital surveillance system in the world as part of the Lower Manhattan Security Initiative in partnership between the New York Police Department and Microsoft to monitor New York City. It allows the NYPD t ...
, which is an interconnected system of sensors including 18,000 CCTV cameras used for continual surveillance of the city by both police officers and artificial intelligence systems.
In the United Kingdom
The United Kingdom of Great Britain and Northern Ireland, commonly known as the United Kingdom (UK) or Britain, is a country in Europe, off the north-western coast of the continental mainland. It comprises England, Scotland, Wales and North ...
, the vast majority of video surveillance cameras are not operated by government bodies, but by private individuals or companies, especially to monitor the interiors of shops and businesses. According to 2011 Freedom of Information Act Freedom of Information Act may refer to the following legislations in different jurisdictions which mandate the national government to disclose certain data to the general public upon request:
* Freedom of Information Act 1982, the Australian act
* ...
requests, the total number of local government operated CCTV cameras was around 52,000 over the entirety of the UK. The prevalence of video surveillance in the UK is often overstated due to unreliable estimates being requoted;; for example one report in 2002 extrapolated from a very small sample to estimate the number of cameras in the UK at 4.2 million (of which 500,000 were in Greater London
Greater may refer to:
*Greatness, the state of being great
*Greater than, in inequality (mathematics), inequality
*Greater (film), ''Greater'' (film), a 2016 American film
*Greater (flamingo), the oldest flamingo on record
*Greater (song), "Greate ...
). More reliable estimates put the number of private and local government operated cameras in the United Kingdom at around 1.85 million in 2011.
In the Netherlands, one example city where there are cameras is The Hague. There, cameras are placed in city districts in which the most illegal activity is concentrated. Examples are the red-light district
A red-light district or pleasure district is a part of an urban area where a concentration of prostitution and sex-oriented businesses, such as sex shops, strip clubs, and adult theaters, are found. In most cases, red-light districts are particu ...
s and the train stations.
As part of China's Golden Shield Project
The Golden Shield Project (), also named National Public Security Work Informational Project, is the Chinese nationwide network-security fundamental constructional project by the e-government of the People's Republic of China. This project in ...
, several U.S. corporations, including IBM, General Electric
General Electric Company (GE) is an American multinational conglomerate founded in 1892, and incorporated in New York state and headquartered in Boston. The company operated in sectors including healthcare, aviation, power, renewable energ ...
, and Honeywell
Honeywell International Inc. is an American publicly traded, multinational conglomerate corporation headquartered in Charlotte, North Carolina. It primarily operates in four areas of business: aerospace, building technologies, performance ma ...
, have been working closely with the Chinese government
The Government of the People's Republic of China () is an authoritarian political system in the People's Republic of China under the exclusive political leadership of the Chinese Communist Party (CCP). It consists of legislative, executive, mili ...
to install millions of surveillance cameras throughout China
China, officially the People's Republic of China (PRC), is a country in East Asia. It is the world's most populous country, with a population exceeding 1.4 billion, slightly ahead of India. China spans the equivalent of five time zones and ...
, along with advanced video analytics Video content analysis or video content analytics (VCA), also known as video analysis or video analytics (VA), is the capability of automatically analyzing video to detect and determine temporal and spatial events.
This technical capability is used ...
and facial recognition software, which will identify and track individuals everywhere they go. They will be connected to a centralized database and monitoring station, which will, upon completion of the project, contain a picture of the face of every person in China: over 1.3 billion people. Lin Jiang Huai, the head of China's "Information Security Technology" office (which is in charge of the project), credits the surveillance systems in the United States and the U.K. as the inspiration for what he is doing with the Golden Shield Project.
 The
The Defense Advanced Research Projects Agency
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military.
Originally known as the Adv ...
(DARPA) is funding a research project called Combat Zones That See that will link up cameras across a city to a centralized monitoring station, identify and track individuals and vehicles as they move through the city, and report "suspicious" activity (such as waving arms, looking side-to-side, standing in a group, etc.).
At Super Bowl XXXV
Super Bowl XXXV was an American football game between the American Football Conference (AFC) champion Baltimore Ravens and the National Football Conference (NFC) champion New York Giants to decide the National Football League (NFL) champion for ...
in January 2001, police in Tampa, Florida, used Identix's facial recognition software, FaceIt, to scan the crowd for potential criminals and terrorists in attendance at the event (it found 19 people with pending arrest warrants).
Governments often initially claim that cameras are meant to be used for traffic control
Traffic management is a key branch within logistics. It concerns the planning control and purchasing of transport services needed to physically move vehicles (for example aircraft, road vehicles, rolling stock and watercraft) and freight.
Traffic ...
, but many of them end up using them for general surveillance. For example, Washington, D.C. had 5,000 "traffic" cameras installed under this premise, and then after they were all in place, networked them all together and then granted access to the Metropolitan Police Department, so they could perform "day-to-day monitoring".
The development of centralized networks of CCTV cameras watching public areas ŌĆō linked to computer databases of people's pictures and identity (biometric
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify in ...
data), able to track people's movements throughout the city, and identify whom they have been with ŌĆō has been argued by some to present a risk to civil liberties
Civil liberties are guarantees and freedoms that governments commit not to abridge, either by constitution, legislation, or judicial interpretation, without due process. Though the scope of the term differs between countries, civil liberties may ...
. Trapwire is an example of such a network.
Social network analysis
 One common form of surveillance is to create maps of
One common form of surveillance is to create maps of social networks
A social network is a social structure made up of a set of social actors (such as individuals or organizations), sets of dyadic ties, and other social interactions between actors. The social network perspective provides a set of methods for an ...
based on data from social networking sites
A social networking service or SNS (sometimes called a social networking site) is an online platform which people use to build social networks or social relationships with other people who share similar personal or career content, interests, act ...
such as Facebook
Facebook is an online social media and social networking service owned by American company Meta Platforms. Founded in 2004 by Mark Zuckerberg with fellow Harvard College students and roommates Eduardo Saverin, Andrew McCollum, Dustin M ...
, MySpace, Twitter
Twitter is an online social media and social networking service owned and operated by American company Twitter, Inc., on which users post and interact with 280-character-long messages known as "tweets". Registered users can post, like, and ...
as well as from traffic analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication, it can be performed even when the messages are encrypted. In general, the greater the number of messages observed ...
information from phone call records such as those in the NSA call database
MAINWAY is a database maintained by the United States' National Security Agency (NSA) containing metadata for hundreds of billions of telephone calls made through the largest telephone carriers in the United States, including AT&T, Verizon, and ...
, and others. These social network
A social network is a social structure made up of a set of social actors (such as individuals or organizations), sets of dyadic ties, and other social interactions between actors. The social network perspective provides a set of methods for an ...
"maps" are then data mined to extract useful information such as personal interests, friendships & affiliations, wants, beliefs, thoughts, and activities.
Many U.S. government agencies such as the Defense Advanced Research Projects Agency
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military.
Originally known as the Adv ...
(DARPA), the National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collecti ...
(NSA), and the Department of Homeland Security
The United States Department of Homeland Security (DHS) is the U.S. federal executive department responsible for public security, roughly comparable to the interior or home ministries of other countries. Its stated missions involve anti-terr ...
(DHS) are investing heavily in research involving social network analysis. The intelligence community believes that the biggest threat to U.S. power comes from decentralized, leaderless, geographically dispersed groups of terrorists
Terrorism, in its broadest sense, is the use of criminal violence to provoke a state of terror or fear, mostly with the intention to achieve political or religious aims. The term is used in this regard primarily to refer to intentional violen ...
, subversives, extremists
Extremism is "the quality or state of being extreme" or "the advocacy of extreme measures or views". The term is primarily used in a political or religious sense to refer to an ideology that is considered (by the speaker or by some implied shar ...
, and dissidents
A dissident is a person who actively challenges an established political or religious system, doctrine, belief, policy, or institution. In a religious context, the word has been used since the 18th century, and in the political sense since the 20th ...
. These types of threats are most easily countered by finding important nodes in the network, and removing them. To do this requires a detailed map of the network.
Jason Ethier of Northeastern University, in his study of modern social network analysis, said the following of the Scalable Social Network Analysis Program developed by the Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology ...
:
AT&T developed a programming language called "Hancock", which is able to sift through enormous databases of phone call and Internet traffic records, such as the NSA call database
MAINWAY is a database maintained by the United States' National Security Agency (NSA) containing metadata for hundreds of billions of telephone calls made through the largest telephone carriers in the United States, including AT&T, Verizon, and ...
, and extract "communities of interest"ŌĆögroups of people who call each other regularly, or groups that regularly visit certain sites on the Internet. AT&T originally built the system to develop "marketing leads", but the FBI has regularly requested such information from phone companies such as AT&T without a warrant, and, after using the data, stores all information received in its own databases, regardless of whether or not the information was ever useful in an investigation.
Some people believe that the use of social networking sites is a form of "participatory surveillance", where users of these sites are essentially performing surveillance on themselves, putting detailed personal information on public websites where it can be viewed by corporations and governments. In 2008, about 20% of employers reported using social networking sites to collect personal data on prospective or current employees.
Biometric
 Biometric surveillance is a technology that measures and analyzes human physical and/or behavioral characteristics for authentication, identification, or screening purposes. Examples of physical characteristics include fingerprints, DNA, and facial patterns. Examples of mostly behavioral characteristics include gait (a person's manner of walking) or voice.
Facial recognition is the use of the unique configuration of a person's facial features to accurately identify them, usually from surveillance video. Both the Department of Homeland Security and
Biometric surveillance is a technology that measures and analyzes human physical and/or behavioral characteristics for authentication, identification, or screening purposes. Examples of physical characteristics include fingerprints, DNA, and facial patterns. Examples of mostly behavioral characteristics include gait (a person's manner of walking) or voice.
Facial recognition is the use of the unique configuration of a person's facial features to accurately identify them, usually from surveillance video. Both the Department of Homeland Security and DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military.
Originally known as the Adv ...
are heavily funding research into facial recognition systems. The Information Processing Technology Office
The Information Processing Techniques Office (IPTO), originally "Command and Control Research",Lyon, Matthew; Hafner, Katie (1999-08-19). ''Where Wizards Stay Up Late: The Origins Of The Internet'' (p. 39). Simon & Schuster. Kindle Edition. was par ...
ran a program known as Human Identification at a Distance
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology ...
which developed technologies that are capable of identifying a person at up to by their facial features.
Another form of behavioral biometrics, based on affective computing
Affective computing is the study and development of systems and devices that can recognize, interpret, process, and simulate human affects. It is an interdisciplinary field spanning computer science, psychology, and cognitive science. While some ...
, involves computers recognizing a person's emotional state based on an analysis of their facial expressions, how fast they are talking, the tone and pitch of their voice, their posture, and other behavioral traits. This might be used for instance to see if a person's behavior is suspect (looking around furtively, "tense" or "angry" facial expressions, waving arms, etc.).
A more recent development is DNA profiling
DNA profiling (also called DNA fingerprinting) is the process of determining an individual's DNA characteristics. DNA analysis intended to identify a species, rather than an individual, is called DNA barcoding.
DNA profiling is a forensic tec ...
, which looks at some of the major markers in the body's DNA to produce a match. The FBI is spending $1 billion to build a new biometric database, which will store DNA, facial recognition data, iris/retina (eye) data, fingerprints, palm prints, and other biometric data of people living in the United States. The computers running the database are contained in an underground facility about the size of two American football field
The rectangular field of play used for American football games measures long between the goal lines, and (53.3 yards) wide. The field may be made of grass or artificial turf. In addition, there are end zones extending another past the goal li ...
s.
The Los Angeles Police Department is installing automated facial recognition and license plate recognition
Automatic number-plate recognition (ANPR; see also #Other names, other names below) is a technology that uses optical character recognition on images to read vehicle registration plates to create vehicle location data. It can use existing close ...
devices in its squad cars, and providing handheld face scanners, which officers will use to identify people while on patrol.Facial thermographs
are in development, which allow machines to identify certain emotions in people such as fear or stress, by measuring the temperature generated by blood flow to different parts of the face. Law enforcement officers believe that this has potential for them to identify when a suspect is nervous, which might indicate that they are hiding something, lying, or worried about something. I
his paper
in
Ethics and Information Technology
''Ethics and Information Technology'' is a quarterly peer-reviewed scientific journal covering the intersection between moral philosophy and the field of information and communications technology. It was established in 1999 by Jeroen van den Hoven ...
, Avi Marciano maps the harms caused by biometric surveillance, traces their theoretical origins, and brings these harms together in one integrative framework to elucidate their cumulative power. Marciano proposes four types of harms: Unauthorized use of bodily information, denial or limitation of access to physical spaces, bodily social sorting, and symbolic ineligibility through construction of marginality and otherness. Biometrics' social power, according to Marciano, derives from three main features: their complexity as "enigmatic technologies", their objective-scientific image, and their increasing agency, particularly in the context of automatic decision-making.
Aerial
 Aerial surveillance is the gathering of surveillance, usually visual imagery or video, from an airborne vehicleŌĆösuch as an
Aerial surveillance is the gathering of surveillance, usually visual imagery or video, from an airborne vehicleŌĆösuch as an unmanned aerial vehicle
An unmanned aerial vehicle (UAV), commonly known as a drone, is an aircraft without any human pilot, crew, or passengers on board. UAVs are a component of an unmanned aircraft system (UAS), which includes adding a ground-based controller ...
, helicopter
A helicopter is a type of rotorcraft in which lift and thrust are supplied by horizontally spinning rotors. This allows the helicopter to take off and land vertically, to hover, and to fly forward, backward and laterally. These attributes ...
, or spy plane. Military surveillance aircraft
A surveillance aircraft is an aircraft used for surveillance. They are operated by military forces and other government agencies in roles such as intelligence gathering, battlefield surveillance, airspace surveillance, reconnaissance, observa ...
use a range of sensors (e.g. radar) to monitor the battlefield.
Digital imaging technology, miniaturized computers, and numerous other technological advances over the past decade have contributed to rapid advances in aerial surveillance hardware such as micro-aerial vehicles, forward-looking infrared
Forward-looking infrared (FLIR) cameras, typically used on military and civilian aircraft, use a thermographic camera that senses infrared radiation.
The sensors installed in forward-looking infrared cameras, as well as those of other thermal ...
, and high-resolution imagery capable of identifying objects at extremely long distances. For instance, the MQ-9 Reaper
The General Atomics MQ-9 Reaper (sometimes called Predator B) is an unmanned aerial vehicle (UAV) capable of remotely controlled or autonomous flight operations developed by General Atomics Aeronautical Systems (GA-ASI) primarily for the Unit ...
, a U.S. drone plane used for domestic operations by the Department of Homeland Security
The United States Department of Homeland Security (DHS) is the U.S. federal executive department responsible for public security, roughly comparable to the interior or home ministries of other countries. Its stated missions involve anti-terr ...
, carries cameras that are capable of identifying an object the size of a milk carton from altitudes of , and has forward-looking infrared
Forward-looking infrared (FLIR) cameras, typically used on military and civilian aircraft, use a thermographic camera that senses infrared radiation.
The sensors installed in forward-looking infrared cameras, as well as those of other thermal ...
devices that can detect the heat from a human body at distances of up to . In an earlier instance of commercial aerial surveillance, the Killington Mountain
Killington Peak is the second highest summit in the Green Mountains and in the U.S. state of Vermont. It is located east of Rutland in south-central Vermont. Killington Peak is a stop on the Long Trail, which here shares its route with the Appa ...
ski resort hired 'eye in the sky' aerial photography of its competitors' parking lots to judge the success of its marketing initiatives as it developed starting in the 1950s.
 The
The United States
The United States of America (U.S.A. or USA), commonly known as the United States (U.S. or US) or America, is a country primarily located in North America. It consists of 50 states, a federal district, five major unincorporated territorie ...
Department of Homeland Security
The United States Department of Homeland Security (DHS) is the U.S. federal executive department responsible for public security, roughly comparable to the interior or home ministries of other countries. Its stated missions involve anti-terr ...
is in the process of testing UAVs to patrol the skies over the United States for the purposes of critical infrastructure protection
Critical infrastructure protection (CIP) is a concept that relates to the preparedness and response to serious incidents that involve the critical infrastructure of a region or nation.
The American Presidential directive PDD-63 of May 1998 set up ...
, border patrol, " transit monitoring", and general surveillance of the U.S. population. Miami-Dade police department ran tests with a vertical take-off and landing UAV from Honeywell
Honeywell International Inc. is an American publicly traded, multinational conglomerate corporation headquartered in Charlotte, North Carolina. It primarily operates in four areas of business: aerospace, building technologies, performance ma ...
, which is planned to be used in SWAT
In the United States, a SWAT team (special weapons and tactics, originally special weapons assault team) is a police tactical unit that uses specialized or military equipment and tactics. Although they were first created in the 1960s to ...
operations. Houston's police department has been testing fixed-wing UAVs for use in "traffic control".
The United Kingdom
The United Kingdom of Great Britain and Northern Ireland, commonly known as the United Kingdom (UK) or Britain, is a country in Europe, off the north-western coast of the continental mainland. It comprises England, Scotland, Wales and North ...
, as well, is working on plans to build up a fleet of surveillance UAVs ranging from micro-aerial vehicles to full-size drones, to be used by police forces throughout the U.K.
In addition to their surveillance capabilities, MAVs are capable of carrying taser
A taser is an electroshock weapon used to incapacitate people, allowing them to be approached and handled in an unresisting and thus safe manner. It is sold by Axon, formerly TASER International. It fires two small barbed darts intended to ...
s for "crowd control
Crowd control is a public security practice in which large crowds are managed in order to prevent the outbreak of crowd crushes, affray, fights involving drunk and disorderly people or riots. Crowd crushes in particular can cause many hundreds ...
", or weapons for killing enemy combatants.
Programs such as the Heterogeneous Aerial Reconnaissance Team program developed by DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military.
Originally known as the Adv ...
have automated much of the aerial surveillance process. They have developed systems consisting of large teams drone planes that pilot themselves, automatically decide who is "suspicious" and how to go about monitoring them, coordinate their activities with other drones nearby, and notify human operators if something suspicious is occurring. This greatly increases the amount of area that can be continuously monitored, while reducing the number of human operators required. Thus a swarm of automated, self-directing drones can automatically patrol a city and track suspicious individuals, reporting their activities back to a centralized monitoring station.
In addition, researchers also investigate possibilities of autonomous surveillance by large groups of micro aerial vehicles stabilized by decentralized bio-inspired swarming rules.
Corporate
Corporate surveillance is the monitoring of a person or group's behavior by a corporation. The data collected is most often used for marketing purposes or sold to other corporations, but is also regularly shared with government agencies. It can be used as a form ofbusiness intelligence
Business intelligence (BI) comprises the strategies and technologies used by enterprises for the data analysis and management of business information. Common functions of business intelligence technologies include reporting, online analytical pr ...
, which enables the corporation to better tailor their products and/or services to be desirable by their customers. Although there is a common belief that monitoring can increase productivity, it can also create consequences such as increasing chances of deviant behavior and creating punishments that are not equitable to their actions. Additionally, monitoring can cause resistance and backlash because it insinuates an employer's suspicion and lack of trust.
Data mining and profiling
Data mining is the application of statistical techniques and programmatic algorithms to discover previously unnoticed relationships within the data.Data profiling
Data profiling is the process of examining the data available from an existing information source (e.g. a database or a file) and collecting statistics or informative summaries about that data. The purpose of these statistics may be to:
# Find ou ...
in this context is the process of assembling information about a particular individual or group in order to generate a profile ŌĆö that is, a picture of their patterns and behavior. Data profiling can be an extremely powerful tool for psychological and social network analysis
Social network analysis (SNA) is the process of investigating social structures through the use of networks and graph theory. It characterizes networked structures in terms of ''nodes'' (individual actors, people, or things within the network) a ...
. A skilled analyst can discover facts about a person that they might not even be consciously aware of themselves.
Economic (such as credit card purchases) and social (such as telephone calls and emails) transactions in modern society create large amounts of stored data
In the pursuit of knowledge, data (; ) is a collection of discrete values that convey information, describing quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted ...
and records. In the past, this data was documented in paper records, leaving a "paper trail
An audit is an "independent examination of financial information of any entity, whether profit oriented or not, irrespective of its size or legal form when such an examination is conducted with a view to express an opinion thereon.ŌĆØ Auditing ...
", or was simply not documented at all. Correlation of paper-based records was a laborious processŌĆöit required human intelligence operators to manually dig through documents, which was time-consuming and incomplete, at best.
But today many of these records are electronic, resulting in an " electronic trail". Every use of a bank machine, payment by credit card, use of a phone card, call from home, checked out library book, rented video, or otherwise complete recorded transaction generates an electronic record. Public recordsŌĆösuch as birth, court, tax and other recordsŌĆöare increasingly being digitized and made available online. In addition, due to laws like CALEA, web traffic and online purchases are also available for profiling. Electronic record-keeping makes data easily collectable, storable, and accessibleŌĆöso that high-volume, efficient aggregation and analysis is possible at significantly lower costs.
Information relating to many of these individual transactions is often easily available because it is generally not guarded in isolation, since the information, such as the title of a movie a person has rented, might not seem sensitive. However, when many such transactions are aggregated they can be used to assemble a detailed profile revealing the actions, habits, beliefs, locations frequented, social connections, and preferences of the individual. This profile is then used, by programs such as ADVISE
ADVISE (Analysis, Dissemination, Visualization, Insight, and Semantic Enhancement) is a research and development program within the United States Department of Homeland Security (DHS) Threat and Vulnerability Testing and Assessment (TVTA) portfoli ...
and TALON
Talon or talons may refer to:
Science and technology
* Talon (anatomy), the claw of a bird of prey
* Brodifacoum, a rodenticide, also known as the brand Talon
* TALON (database), a database maintained by the US Air Force
* Talon, an anti-vehicle- ...
, to determine whether the person is a military, criminal, or political threat.
In addition to its own aggregation and profiling tools, the government is able to access information from third parties ŌĆö for example, banks, credit companies or employers, etc. ŌĆö by requesting access informally, by compelling access through the use of subpoenas or other procedures, or by purchasing data from commercial data aggregators or data brokers. The United States has spent $370 million on its 43 planned fusion centers
In the United States, fusion centers are designed to promote information sharing at the federal level between agencies such as the Federal Bureau of Investigation, the U.S. Department of Homeland Security, the U.S. Department of Justice, and sta ...
, which are national network of surveillance centers that are located in over 30 states. The centers will collect and analyze vast amounts of data on U.S. citizens. It will get this data by consolidating personal information from sources such as state driver's licensing agencies, hospital records, criminal records, school records, credit bureaus, banks, etc. ŌĆō and placing this information in a centralized database that can be accessed from all of the centers, as well as other federal law enforcement and intelligence agencies.
Under United States v. Miller
' (1976), data held by third parties is generally not subject to Fourth Amendment warrant requirements.
Human operatives
A tail may surreptitiously track and report on the movements and contacts of a person of interest. Such following by one or more people may provide useful in formation in relatively densely populated urban environments. Organizations that have enemies who wish to gather information about the groups' members or activities face the issue of potential infiltration. In addition to operatives' infiltrating an organization, the surveilling party may exert pressure on certain members of the target organization to act asinformants
An informant (also called an informer or, as a slang term, a ŌĆ£snitchŌĆØ) is a person who provides privileged information about a person or organization to an agency. The term is usually used within the law-enforcement world, where informan ...
(i.e., to disclose the information they hold on the organization and its members).
Fielding operatives is very expensive, and governments with wide-reaching electronic surveillance tools Surveillance tools are all means technological provided and used by the surveillance industry, police or military intelligence, and national security institutions that enable individual surveillance and mass surveillance.
Steven Ashley in 2008 liste ...
at their disposal, rather than gathering the sort of information which operatives can provide, may use less problematic forms of surveillance - such as those mentioned above. Nevertheless, the use of human infiltrators remains common. For instance, in 2007 documents surfaced showing that the FBI
The Federal Bureau of Investigation (FBI) is the domestic Intelligence agency, intelligence and Security agency, security service of the United States and its principal Federal law enforcement in the United States, federal law enforcement age ...
planned to field a total of 15,000 undercover agents and informants in response to an anti-terrorism directive (issued by President George W. Bush
George Walker Bush (born July 6, 1946) is an American politician who served as the 43rd president of the United States from 2001 to 2009. A member of the Republican Party, Bush family, and son of the 41st president George H. W. Bush, he ...
in 2004) that ordered intelligence and law-enforcement agencies to increase their HUMINT
Human intelligence (abbreviated HUMINT and pronounced as ''hyoo-mint'') is Intelligence (information gathering), intelligence gathered by means of interpersonal contact, as opposed to the List of intelligence gathering disciplines, more technical ...
capabilities.
Satellite imagery
On May 25, 2007, the U.S.Director of National Intelligence
The director of national intelligence (DNI) is a senior, cabinet-level United States government official, required by the Intelligence Reform and Terrorism Prevention Act of 2004 to serve as executive head of the United States Intelligence Commu ...
Michael McConnell authorized the National Applications Office (NAO) of the Department of Homeland Security
The United States Department of Homeland Security (DHS) is the U.S. federal executive department responsible for public security, roughly comparable to the interior or home ministries of other countries. Its stated missions involve anti-terr ...
to allow local, state, and domestic Federal agencies to access imagery from military intelligence
Military intelligence is a military discipline that uses information collection and analysis approaches to provide guidance and direction to assist commanders in their decisions. This aim is achieved by providing an assessment of data from a ...
Reconnaissance satellite
A reconnaissance satellite or intelligence satellite (commonly, although unofficially, referred to as a spy satellite) is an Earth observation satellite or communications satellite deployed for military or intelligence applications.
The ...
s and Reconnaissance aircraft
A reconnaissance aircraft (colloquially, a spy plane) is a military aircraft designed or adapted to perform aerial reconnaissance with roles including collection of imagery intelligence (including using photography), signals intelligence, as ...
sensors which can now be used to observe the activities of U.S. citizens. The satellites and aircraft sensors will be able to penetrate cloud cover, detect chemical traces, and identify objects in buildings and "underground bunkers", and will provide real-time video at much higher resolutions than the still-images produced by programs such as Google Earth
Google Earth is a computer program that renders a 3D computer graphics, 3D representation of Earth based primarily on satellite imagery. The program maps the Earth by superimposition, superimposing satellite images, aerial photography, and geog ...
.
Identification and credentials
 One of the simplest forms of identification is the carrying of credentials. Some nations have an
One of the simplest forms of identification is the carrying of credentials. Some nations have an identity card
An identity document (also called ID or colloquially as papers) is any documentation, document that may be used to prove a person's identity. If issued in a small, standard credit card size form, it is usually called an identity card (IC, ID c ...
system to aid identification, whilst others are considering it but face public opposition. Other documents, such as passport
A passport is an official travel document issued by a government that contains a person's identity. A person with a passport can travel to and from foreign countries more easily and access consular assistance. A passport certifies the personal ...
s, driver's license
A driver's license is a legal authorization, or the official document confirming such an authorization, for a specific individual to operate one or more types of motorized vehiclesŌĆösuch as motorcycles, cars, trucks, or busesŌĆöon a public ...
s, library card
A library card can refer to several cards traditionally used for the management of books and patrons in a library. In its most common use, a library card serves similar functions as a corporate membership card. A person who holds a library card ...
s, banking or credit card
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt (i.e., promise to the card issuer to pay them for the amounts plus the o ...
s are also used to verify identity.
If the form of the identity card is "machine-readable", usually using an encoded magnetic stripe or identification number (such as a Social Security number
In the United States, a Social Security number (SSN) is a nine-digit number issued to U.S. citizens, permanent residents, and temporary (working) residents under section 205(c)(2) of the Social Security Act, codified as . The number is issued to ...
), it corroborates the subject's identifying data. In this case it may create an electronic trail when it is checked and scanned, which can be used in profiling, as mentioned above.
Wireless Tracking
This section refers to methods that involve the monitoring oftracking device
A tracking system, also known as a locating system, is used for the observing of persons or objects on the move and supplying a timely ordered sequence of location data for further processing. It is important to be aware of human tracking, fur ...
s through the aid of wireless signals.
Mobile phones
Mobile carrier antennas are also commonly used to collect geolocation data on mobile phones. The geographical location of a powered mobile phone (and thus the person carrying it) can be determined easily (whether it is being used or not), using a technique known asmultilateration Trilateration is the use of distances (or "ranges") for determining the unknown position coordinates of a point of interest, often around Earth (geopositioning).
When more than three distances are involved, it may be called multilateration, for emph ...
to calculate the differences in time for a signal to travel from the cell phone to each of several cell towers
A cell site, cell tower, or cellular base station is a cellular-enabled mobile device site where antennas and electronic communications equipment are placed (typically on a radio mast, tower, or other raised structure) to create a cell, or adjac ...
near the owner of the phone. Dr. Victor Kappeler of Eastern Kentucky University indicates that police surveillance is a strong concern, stating the following statistics from 2013:
A comparatively new off-the-shelf surveillance device is an IMSI-catcher
An international mobile subscriber identity-catcher, or IMSI-catcher, is a Telephone tapping, telephone eavesdropping device used for intercepting mobile phone traffic and tracking location data of mobile phone users. Essentially a "fake" cell sit ...
, a telephone eavesdropping device used to intercept mobile phone traffic and track the movement of mobile phone users. Essentially a "fake" mobile tower acting between the target mobile phone and the service provider's real towers, it is considered a man-in-the-middle
In cryptography and computer security, a man-in-the-middle, monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle, meddler-in-the-middle, manipulator-in-the-middle (MITM), person-in-the-middle (PITM) or adversary-in-the-middle (AiTM) ...
(MITM) attack. IMSI-catchers are used in some countries by law enforcement
Law enforcement is the activity of some members of government who act in an organized manner to enforce the law by discovering, deterring, rehabilitating, or punishing people who violate the rules and norms governing that society. The term en ...
and intelligence agencies
An intelligence agency is a government agency responsible for the collection, analysis, and exploitation of information in support of law enforcement, national security, military, public safety, and foreign policy objectives.
Means of informatio ...
, but their use has raised significant civil liberty and privacy concerns and is strictly regulated in some countries.
In March 2020, British daily The Guardian
''The Guardian'' is a British daily newspaper. It was founded in 1821 as ''The Manchester Guardian'', and changed its name in 1959. Along with its sister papers ''The Observer'' and ''The Guardian Weekly'', ''The Guardian'' is part of the Gu ...
, based on the claims of a whistleblower
A whistleblower (also written as whistle-blower or whistle blower) is a person, often an employee, who reveals information about activity within a private or public organization that is deemed illegal, immoral, illicit, unsafe or fraudulent. Whi ...
, accused the government of Saudi Arabia
Saudi Arabia, officially the Kingdom of Saudi Arabia (KSA), is a country in Western Asia. It covers the bulk of the Arabian Peninsula, and has a land area of about , making it the fifth-largest country in Asia, the second-largest in the A ...
of exploiting global mobile telecom network weaknesses to spy on its citizens traveling around the United States
The United States of America (U.S.A. or USA), commonly known as the United States (U.S. or US) or America, is a country primarily located in North America. It consists of 50 states, a federal district, five major unincorporated territorie ...
. The data shared by the whistleblower in support of the claims, showed that a systematic spying
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangibl ...
campaign was being run by the kingdom exploiting the flaws of SS7, a global messaging system. The data showed that millions of secret tracking commands originated from Saudi in a duration of four-months, starting from November 2019.
RFID tagging

Radio Frequency Identification
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter. When triggered by an electromag ...
(RFID) tagging is the use of very small electronic devices (called "RFID tags") which are applied to or incorporated into a product, animal, or person for the purpose of identification and tracking using radio waves. The tags can be read from several meters away. They are extremely inexpensive, costing a few cents per piece, so they can be inserted into many types of everyday products without significantly increasing the price, and can be used to track and identify these objects for a variety of purposes.
Some companies appear to be "tagging" their workers by incorporating RFID tags in employee ID badges. Workers in U.K. considered strike action
Strike action, also called labor strike, labour strike, or simply strike, is a work stoppage caused by the mass refusal of employees to Labor (economics), work. A strike usually takes place in response to grievance (labour), employee grievance ...
in protest of having themselves tagged; they felt that it was dehumanizing to have all of their movements tracked with RFID chips. Some critics have expressed fears that people will soon be tracked and scanned everywhere they go. On the other hand, RFID tags in newborn baby ID bracelets put on by hospitals have foiled kidnappings.
In a 2003 editorial, CNET News.com's chief political correspondent, Declan McCullagh, speculated that, soon, every object that is purchased, and perhaps ID cards, will have RFID devices in them, which would respond with information about people as they walk past scanners (what type of phone they have, what type of shoes they have on, which books they are carrying, what credit cards or membership cards they have, etc.). This information could be used for identification, tracking, or targeted marketing
Targeted advertising is a form of advertising, including online advertising, that is directed towards an audience with certain traits, based on the product or person the advertiser is promoting. These traits can either be demographic with a focus ...
. , this has largely not come to pass.
RFID tagging on humans
 A human microchip implant is an identifying integrated circuit device or
A human microchip implant is an identifying integrated circuit device or RFID
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter. When triggered by an electromag ...
transponder encased in silicate glass
Glass is a non-crystalline, often transparent, amorphous solid that has widespread practical, technological, and decorative use in, for example, window panes, tableware, and optics. Glass is most often formed by rapid cooling (quenching) of ...
and implanted in the body of a human being. A subdermal implant
A subdermal implant refers to a body modification that is placed underneath the skin, therefore allowing the body to heal over the implant and creating a raised design. Such implants fall under the broad category of body modification. Many subderma ...
typically contains a unique ID number that can be linked to information contained in an external database, such as personal identification, medical history, medications, allergies, and contact information.
Several types of microchips have been developed in order to control and monitor certain types of people, such as criminals, political figures and spies, a "killer" tracking chip patent was filed at the German Patent and Trademark Office (DPMA) around May 2009.
Verichip
A human microchip implant is any electronic device implanted subcutaneously (subdermally) usually via an injection. Examples include an identifying integrated circuit RFID device encased in silicate glass which is implanted in the body of a human ...
is an RFID device produced by a company called Applied Digital Solutions (ADS). Verichip is slightly larger than a grain of rice, and is injected under the skin. The injection reportedly feels similar to receiving a shot
Shot may refer to:
Arts, entertainment, and media
* ''Shot'' (album), by The Jesus Lizard
*''Shot, Illusion, New God'', an EP by Gruntruck
*'' Shot Rev 2.0'', a video album by The Sisters of Mercy
* "Shot" (song), by The Rasmus
* ''Shot'' (2017 f ...
. The chip is encased in glass, and stores a "VeriChip Subscriber Number" which the scanner uses to access their personal information, via the Internet, from Verichip Inc.'s database, the "Global VeriChip Subscriber Registry". Thousands of people have already had them inserted. In Mexico, for example, 160 workers at the Attorney General's office were required to have the chip injected for identity verification and access control
In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of ''accessing'' may mean consuming ...
purposes.
Implantable microchips have also been used in healthcare settings, but ethnographic researchers have identified a number of ethical problems with such uses; these problems include unequal treatment, diminished trust, and possible endangerment of patients.
Radar
Geolocation devices
Global Positioning System
 In the U.S., police have planted hidden
In the U.S., police have planted hidden GPS
The Global Positioning System (GPS), originally Navstar GPS, is a Radionavigation-satellite service, satellite-based radionavigation system owned by the United States government and operated by the United States Space Force. It is one of t ...
tracking devices in people's vehicles to monitor their movements, without a warrant. In early 2009, they were arguing in court that they have the right to do this.
Several cities are running pilot projects to require parolees to wear GPS devices to track their movements when they get out of prison.
Devices
Covert listening device
A covert listening device, more commonly known as a bug or a wire, is usually a combination of a miniature radio transmitter with a microphone. The use of bugs, called bugging, or wiretapping is a common technique in surveillance, espionage and ...
s and video devices, or "bugs", are hidden electronic devices which are used to capture, record, and/or transmit data to a receiving party such as a law enforcement agency.
The U.S. has run numerous domestic intelligence operations, such as COINTELPRO
COINTELPRO ( syllabic abbreviation derived from Counter Intelligence Program; 1956ŌĆō1971) was a series of covert and illegal projects actively conducted by the United States Federal Bureau of Investigation (FBI) aimed at surveilling, infiltrati ...
, which have bugged the homes, offices, and vehicles of thousands of U.S. citizens, usually political activists
Activism (or Advocacy) consists of efforts to promote, impede, direct or intervene in social, political, economic or environmental reform with the desire to make changes in society toward a perceived greater good. Forms of activism range fro ...
, subversives, and criminals
In ordinary language, a crime is an unlawful act punishable by a State (polity), state or other authority. The term ''crime'' does not, in modern criminal law, have any simple and universally accepted definition,Farmer, Lindsay: "Crime, definit ...
.
Law enforcement and intelligence services in the U.K. and the United States possess technology to remotely activate the microphones in cell phones, by accessing the phone's diagnostic/maintenance features, in order to listen to conversations that take place nearby the person who holds the phone.
Postal services
As more people use faxes and e-mail the significance of surveilling the postal system is decreasing, in favor of Internet and telephone surveillance. But interception of post is still an available option for law enforcement and intelligence agencies, in certain circumstances. This is not a common practice, however, and entities like the US Army require high levels of approval to conduct. The U.S.Central Intelligence Agency
The Central Intelligence Agency (CIA ), known informally as the Agency and historically as the Company, is a civilian foreign intelligence service of the federal government of the United States, officially tasked with gathering, processing, ...
and Federal Bureau of Investigation
The Federal Bureau of Investigation (FBI) is the domestic intelligence and security service of the United States and its principal federal law enforcement agency. Operating under the jurisdiction of the United States Department of Justice, ...
have performed twelve separate mail-opening campaigns targeted towards U.S. citizens. In one of these programs, more than 215,000 communications were intercepted, opened, and photographed.
Stakeout
A stakeout is the coordinated surveillance of a location or person. Stakeouts are generally performed covertly and for the purpose of gatheringevidence
Evidence for a proposition is what supports this proposition. It is usually understood as an indication that the supported proposition is true. What role evidence plays and how it is conceived varies from field to field.
In epistemology, evidenc ...
related to criminal activity
In ordinary language, a crime is an unlawful act punishable by a state or other authority. The term ''crime'' does not, in modern criminal law, have any simple and universally accepted definition,Farmer, Lindsay: "Crime, definitions of", in Can ...
. The term derives from the practice by land surveyor
Surveying or land surveying is the technique, profession, art, and science of determining the terrestrial two-dimensional or three-dimensional positions of points and the distances and angles between them. A land surveying professional is ca ...
s of using survey stakes
{{engineering-stub
Control of alignment and grade during construction is established through the use of survey stakes. Stakes are generally made of wood in different sizes. Based on the use of the stake they are called ''alignment stakes'', ''o ...
to measure out an area before the main building project begins.
Internet of things
TheInternet of Things
The Internet of things (IoT) describes physical objects (or groups of such objects) with sensors, processing ability, software and other technologies that connect and exchange data with other devices and systems over the Internet or other comm ...
(IoT) is a term that refers to the future of technology in which data can be collected without human and computer interaction. IoTs can be used for identification, monitoring, location tracking, and health tracking. While IoTs have the benefit of being a time-saving tool that makes activities simpler, they raise the concern of government surveillance and privacy regarding how data will be used.
Controversy

Support
Supporters of surveillance systems believe that these tools can help protect society fromterrorists
Terrorism, in its broadest sense, is the use of criminal violence to provoke a state of terror or fear, mostly with the intention to achieve political or religious aims. The term is used in this regard primarily to refer to intentional violen ...
and criminals
In ordinary language, a crime is an unlawful act punishable by a State (polity), state or other authority. The term ''crime'' does not, in modern criminal law, have any simple and universally accepted definition,Farmer, Lindsay: "Crime, definit ...
. They argue that surveillance can reduce crime by three means: by deterrence, by observation, and by reconstruction. Surveillance can deter by increasing the chance of being caught, and by revealing the modus operandi
A ''modus operandi'' (often shortened to M.O.) is someone's habits of working, particularly in the context of business or criminal investigations, but also more generally. It is a Latin phrase, approximately translated as "mode (or manner) of op ...
. This requires a minimal level of invasiveness.Deviant Behaviour ŌĆō Socially accepted observation of behaviour for securityJeroen van Rest Another method on how surveillance can be used to fight criminal activity is by linking the information stream obtained from them to a recognition system (for instance, a camera system that has its feed run through a facial recognition system). This can for instance auto-recognize fugitives and direct police to their location. A distinction here has to be made however on the type of surveillance employed. Some people that say support video surveillance in city streets may not support indiscriminate telephone taps and vice versa. Besides the types, the way in how this surveillance is done also matters a lot; i.e. indiscriminate telephone taps are supported by much fewer people than say telephone taps done only to people suspected of engaging in illegal activities. Surveillance can also be used to give human operatives a tactical advantage through improved situational awareness, or through the use of automated processes, i.e.
video analytics Video content analysis or video content analytics (VCA), also known as video analysis or video analytics (VA), is the capability of automatically analyzing video to detect and determine temporal and spatial events.
This technical capability is used ...
. Surveillance can help reconstruct an incident and prove guilt through the availability of footage for forensics experts. Surveillance can also influence subjective security if surveillance resources are visible or if the consequences of surveillance can be felt.
Some of the surveillance systems (such as the camera system that has its feed run through a facial recognition system mentioned above) can also have other uses besides countering criminal activity. For instance, it can help on retrieving runaway children, abducted or missing adults and mentally disabled people.
Other supporters simply believe that there is nothing that can be done about the loss of privacy, and that people must become accustomed to having no privacy. As Sun Microsystems
Sun Microsystems, Inc. (Sun for short) was an American technology company that sold computers, computer components, software, and information technology services and created the Java programming language, the Solaris operating system, ZFS, the ...
CEO Scott McNealy
Scott McNealy (born November 13, 1954) is an American businessman. He is most famous for co-founding the computer technology company Sun Microsystems in 1982 along with Vinod Khosla, Bill Joy, and Andy Bechtolsheim. In 2004, while still at Sun, ...
said: "You have zero privacy anyway. Get over it."
Another common argument is: " If you aren't doing something wrong then you don't have anything to fear." Which follows that if one is engaging in unlawful activities, in which case they do not have a legitimate justification for their privacy. However, if they are following the law the surveillance would not affect them.
Opposition

 With the advent of programs such as the
With the advent of programs such as the Total Information Awareness
Total Information Awareness (TIA) was a mass detection program by the United States Information Awareness Office. It operated under this title from February to May 2003 before being renamed Terrorism Information Awareness.
Based on the concep ...
program and ADVISE
ADVISE (Analysis, Dissemination, Visualization, Insight, and Semantic Enhancement) is a research and development program within the United States Department of Homeland Security (DHS) Threat and Vulnerability Testing and Assessment (TVTA) portfoli ...
, technologies such as high speed surveillance computers and biometrics
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify in ...
software, and laws such as the Communications Assistance for Law Enforcement Act
The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton (Pub. L. No. 103-414, 108 Stat. 4279, codified at 47 ...
, governments now possess an unprecedented ability to monitor the activities of their subjects. Many civil rights
Civil and political rights are a class of rights that protect individuals' freedom from infringement by governments, social organizations, and private individuals. They ensure one's entitlement to participate in the civil and political life of ...
and privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
The domain of privacy partially overlaps with security, which can include the concepts of a ...
groups, such as the Electronic Frontier Foundation
The Electronic Frontier Foundation (EFF) is an international non-profit digital rights group based in San Francisco, California. The foundation was formed on 10 July 1990 by John Gilmore, John Perry Barlow and Mitch Kapor to promote Internet ci ...
and American Civil Liberties Union
The American Civil Liberties Union (ACLU) is a nonprofit organization founded in 1920 "to defend and preserve the individual rights and liberties guaranteed to every person in this country by the Constitution and laws of the United States". T ...
, have expressed concern that by allowing continual increases in government surveillance of citizens we will end up in a mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizati ...
society, with extremely limited, or non-existent political and/or personal freedoms. Fears such as this have led to numerous lawsuits such as '' Hepting v. AT&T''.
Some critics state that the claim made by supporters should be modified to read: "As long as we do what we're told, we have nothing to fear.". For instance, a person who is part of a political group which opposes the policies of the national government, might not want the government to know their names and what they have been reading, so that the government cannot easily subvert their organization, arrest, or kill them. Other critics state that while a person might not have anything to hide right now, the government might later implement policies that they do wish to oppose, and that opposition might then be impossible due to mass surveillance enabling the government to identify and remove political threats. Further, other critics point to the fact that most people ''do'' have things to hide. For example, if a person is looking for a new job, they might not want their current employer to know this. Also if an employer wishes total privacy to watch over their own employee and secure their financial information it may become impossible, and they may not wish to hire those under surveillance.
In December 2017, the Government of China took steps to oppose widespread surveillance by security-company cameras, webcams, and IP camera
An Internet Protocol camera, or IP camera, is a type of digital video camera that receives control data and sends image data via an IP network. They are commonly used for surveillance, but, unlike analog closed-circuit television (CCTV) cameras, ...
s after tens-of-thousands were made accessible for internet viewing by IT company Qihoo
Qihoo 360 (; approximate pronunciation CHEE-hoo), full name 360 Security Technology Inc., is a Chinese internet security company that has developed the antivirus software programs 360 Safeguard and 360 Mobile Safe, the Web browser 360 Secure Brow ...
Totalitarianism
 Programs such as the
Programs such as the Total Information Awareness
Total Information Awareness (TIA) was a mass detection program by the United States Information Awareness Office. It operated under this title from February to May 2003 before being renamed Terrorism Information Awareness.
Based on the concep ...
program, and laws such as the Communications Assistance For Law Enforcement Act
The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton (Pub. L. No. 103-414, 108 Stat. 4279, codified at 47 ...
have led many groups to fear that society is moving towards a state of mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizati ...
with severely limited personal, social, political freedoms, where dissenting individuals or groups will be strategically removed in COINTELPRO
COINTELPRO ( syllabic abbreviation derived from Counter Intelligence Program; 1956ŌĆō1971) was a series of covert and illegal projects actively conducted by the United States Federal Bureau of Investigation (FBI) aimed at surveilling, infiltrati ...
-like purges.
Kate Martin, of the Center For National Security Studies said of the use of military spy satellites being used to monitor the activities of U.S. citizens: "They are laying the bricks one at a time for a police state."
Some point to the blurring of lines between public and private places, and the privatization of places traditionally seen as public (such as shopping malls and industrial parks) as illustrating the increasing legality of collecting personal information. Traveling through many public places such as government offices is hardly optional for most people, yet consumers have little choice but to submit to companies' surveillance practices.Agre, Philip E. (2003)"Your Face is not a bar code: arguments against automatic face recognition in public places"
Retrieved November 14, 2004. Surveillance techniques are not created equal; among the many
biometric
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify in ...
identification technologies, for instance, face recognition
A facial recognition system is a technology capable of matching a human face from a digital image or a video frame against a database of faces. Such a system is typically employed to authenticate users through ID verification services, and wo ...
requires the least cooperation. Unlike automatic fingerprint reading, which requires an individual to press a finger against a machine, this technique is subtle and requires little to no consent.
Psychological/social effects
Some critics, such asMichel Foucault
Paul-Michel Foucault (, ; ; 15 October 192625 June 1984) was a French philosopher, historian of ideas, writer, political activist, and literary critic. Foucault's theories primarily address the relationship between power and knowledge, and how ...
, believe that in addition to its obvious function of identifying and capturing individuals who are committing undesirable acts, surveillance also functions to create in everyone a feeling of always being watched, so that they become self-policing. This allows the State to control the populace without having to resort to physical force, which is expensive and otherwise problematic.
With the development of digital technology, individuals have become increasingly perceptible to one another, as surveillance becomes virtual. Online surveillance is the utilization of the internet to observe one's activity. Corporations, citizens, and governments participate in tracking others' behaviours for motivations that arise out of business relations, to curiosity, to legality. In her book ''Superconnected'', Mary Chayko differentiates between two types of surveillance: vertical and horizontal. Vertical surveillance occurs when there is a dominant force, such as the government that is attempting to control or regulate the actions of a given society. Such powerful authorities often justify their incursions as a means to protect society from threats of violence or terrorism. Some individuals question when this becomes an infringement on civil rights.
Horizontal diverges from vertical surveillance as the tracking shifts from an authoritative source to an everyday figure, such as a friend, coworker, or stranger that is interested in one's mundane activities. Individuals leave traces of information when they are online that reveal their interests and desires of which others observe. While this can allow people to become interconnected and develop social connections online, it can also increase potential risk to harm, such as cyberbullying
Cyberbullying or cyberharassment is a form of bullying or harassment using electronic means. Cyberbullying and cyberharassment are also known as online bullying. It has become increasingly common, especially among teenagers, as the digital ...
or censoring/stalking by strangers, reducing privacy.
In addition, Simone Browne
Simone Arlene Browne (born 1973) is an author and educator. She is on the faculty at the University of Texas at Austin, and the author of ''Dark Matters: On the Surveillance of Blackness''.
Early life and education
Browne was born in 1973, and ...
argues that surveillance wields an immense racializing quality such that it operates as "racializing surveillance." Browne uses racializing surveillance to refer to moments when enactments of surveillance are used to reify boundaries, borders, and bodies along racial lines and where the outcome is discriminatory treatment of those who are negatively racialized by such surveillance. Browne argues racializing surveillance pertains to policing what is "in or out of place."
Privacy
Numerouscivil rights
Civil and political rights are a class of rights that protect individuals' freedom from infringement by governments, social organizations, and private individuals. They ensure one's entitlement to participate in the civil and political life of ...
groups and privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
The domain of privacy partially overlaps with security, which can include the concepts of a ...
groups oppose surveillance as a violation of people's right to privacy. Such groups include: Electronic Privacy Information Center
Electronic Privacy Information Center (EPIC) is an independent nonprofit research center in Washington, D.C. EPIC's mission is to focus public attention on emerging privacy and related human rights issues. EPIC works to protect privacy, freedom o ...
, Electronic Frontier Foundation
The Electronic Frontier Foundation (EFF) is an international non-profit digital rights group based in San Francisco, California. The foundation was formed on 10 July 1990 by John Gilmore, John Perry Barlow and Mitch Kapor to promote Internet ci ...
, American Civil Liberties Union
The American Civil Liberties Union (ACLU) is a nonprofit organization founded in 1920 "to defend and preserve the individual rights and liberties guaranteed to every person in this country by the Constitution and laws of the United States". T ...
and Privacy International
Privacy International (PI) is a UK-based registered charity that defends and promotes the right to privacy across the world. First formed in 1990, registered as a non-profit company in 2002 and as a charity in 2012, PI is based in London. Its cu ...
.
There have been several lawsuits such as Hepting v. AT&T and EPIC v. Department of Justice
EPIC v. Department of Justice is a 2014 case in the United States District Court for the District of Columbia between the Electronic Privacy Information Center (EPIC) and the U.S. Department of Justice (DOJ) where EPIC seeks court action to en ...
by groups or individuals, opposing certain surveillance activities.
Legislative proceedings such as those that took place during the Church Committee
The Church Committee (formally the United States Senate Select Committee to Study Governmental Operations with Respect to Intelligence Activities) was a US Senate select committee in 1975 that investigated abuses by the Central Intelligence ...
, which investigated domestic intelligence programs such as COINTELPRO
COINTELPRO ( syllabic abbreviation derived from Counter Intelligence Program; 1956ŌĆō1971) was a series of covert and illegal projects actively conducted by the United States Federal Bureau of Investigation (FBI) aimed at surveilling, infiltrati ...
, have also weighed the pros and cons of surveillance.
Court cases
''People vs. Diaz'' (2011) was a court case in the realm of cell phone privacy, even though the decision was later overturned. In this case, Gregory Diaz was arrested during a sting operation for attempting to sell ecstasy. During his arrest, police searched Diaz's phone and found more incriminating evidence including SMS text messages and photographs depicting illicit activities. During his trial, Diaz attempted to have the information from his cell phone removed from evidence, but the courts deemed it as lawful and Diaz's appeal was denied on the California State Court level and, later, the Supreme Court level. Just three short years after, this decision was overturned in the case ''Riley vs. California'' (2014). ''Riley vs. California'' (2014) was aU.S. Supreme Court
The Supreme Court of the United States (SCOTUS) is the highest court in the federal judiciary of the United States. It has ultimate appellate jurisdiction over all U.S. federal court cases, and over state court cases that involve a point o ...
case in which a man was arrested for his involvement in a drive-by shooting. A few days after the shooting the police made an arrest of the suspect (Riley), and, during the arrest, the police searched him. However, this search was not only of Riley's person, but also the police opened and searched his cell phone, finding pictures of other weapons, drugs, and of Riley showing gang signs. In court, the question arose whether searching the phone was lawful or if the search was protected by the 4th amendment of the constitution. The decision held that the search of Riley's cell phone during the arrest was illegal, and that it was protected by the 4th Amendment.
Countersurveillance, inverse surveillance, sousveillance
Countersurveillance
Countersurveillance refers to measures that are usually undertaken by the public to prevent surveillance, including covert surveillance. Countersurveillance may include electronic methods such as technical surveillance counter-measures, which is ...
is the practice of avoiding surveillance or making surveillance difficult. Developments in the late twentieth century have caused counter surveillance to dramatically grow in both scope and complexity, such as the Internet, increasing prevalence of electronic security systems
Security is protection from, or resilience against, potential harm (or other unwanted coercive change) caused by others, by restraining the freedom of others to act. Beneficiaries (technically referents) of security may be of persons and social ...
, high-altitude (and possibly armed) UAVs
An unmanned aerial vehicle (UAV), commonly known as a drone, is an aircraft without any human pilot, crew, or passengers on board. UAVs are a component of an unmanned aircraft system (UAS), which includes adding a ground-based controlle ...
, and large corporate and government computer databases.
Inverse surveillance
Sousveillance ( ) is the recording of an activity by a member of the public, rather than a person or organisation in authority, typically by way of small wearable or portable personal technologies. The term, coined by Steve Mann, stems from th ...
is the practice of the reversal of surveillance on other individuals or groups (e.g., citizens photographing police). Well-known examples include George Holliday's recording of the Rodney King
Rodney Glen King (April 2, 1965June 17, 2012) was an African American man who was a victim of police brutality. On March 3, 1991, he was beaten by Los Angeles Police Department (LAPD) officers during his arrest after a pursuit for driving whi ...
beating and the organization Copwatch
Copwatch (also Cop Watch or Cop-Watch) is a network of activist organizations, typically autonomous and focused in local areas, in the United States, Canada and Europe that observe and document police activity while looking for signs of police mis ...
, which attempts to monitor police officers to prevent police brutality
Police brutality is the excessive and unwarranted use of force by law enforcement against an individual or a group. It is an extreme form of police misconduct and is a civil rights violation. Police brutality includes, but is not limited to, ...
. Counter-surveillance can be also used in applications to prevent corporate spying, or to track other criminals by certain criminal entities. It can also be used to deter stalking methods used by various entities and organizations.
''Sousveillance
Sousveillance ( ) is the recording of an activity by a member of the public, rather than a person or organisation in authority, typically by way of small wearable or portable personal technologies. The term, coined by Steve Mann, stems from th ...
'' is inverse surveillance, involving the recording by private individuals, rather than government or corporate entities.
Popular culture
In literature
*George Orwell
Eric Arthur Blair (25 June 1903 ŌĆō 21 January 1950), better known by his pen name George Orwell, was an English novelist, essayist, journalist, and critic. His work is characterised by lucid prose, social criticism, opposition to totalitar ...
's novel ''Nineteen Eighty-Four
''Nineteen Eighty-Four'' (also stylised as ''1984'') is a dystopian social science fiction novel and cautionary tale written by the English writer George Orwell. It was published on 8 June 1949 by Secker & Warburg as Orwell's ninth and final ...
'' portrays a fictional totalitarian
Totalitarianism is a form of government and a political system that prohibits all opposition parties, outlaws individual and group opposition to the state and its claims, and exercises an extremely high if not complete degree of control and regul ...
surveillance society with a very simple mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizati ...
system consisting of human operatives, informants, and two-way "telescreens" in people's homes. Because of the impact of this book, mass-surveillance technologies are commonly called "Orwellian" when they are considered problematic.
* The novel ''mistrust
Distrust is a formal way of not trusting any one party too much in a situation of grave risk or deep doubt. It is commonly expressed in civics as a division or balance of powers, or in politics as means of validating treaty terms. Systems based o ...
'' highlights the negative effects from the overuse of surveillance at Reflection House. The central character Kerryn installs secret cameras to monitor her housemates ŌĆō see also Paranoia
Paranoia is an instinct or thought process that is believed to be heavily influenced by anxiety or fear, often to the point of delusion and irrationality. Paranoid thinking typically includes persecutory beliefs, or beliefs of conspiracy concer ...
.
* The book ''The Handmaid's Tale
''The Handmaid's Tale'' is a futuristic dystopian novel by Canadian author Margaret Atwood and published in 1985. It is set in a near-future New England in a patriarchal, totalitarian theonomic state known as the Republic of Gilead, which h ...
'', as well as a film and TV series based on it, portray a totalitarian Christian theocracy
Theocracy is a form of government in which one or more deity, deities are recognized as supreme ruling authorities, giving divine guidance to human intermediaries who manage the government's daily affairs.
Etymology
The word theocracy origina ...
where all citizens are kept under constant surveillance.
* In the book ''The Girl with the Dragon Tattoo
''The Girl with the Dragon Tattoo'' (original title in sv, M├żn som hatar kvinnor , lit=''Men Who Hate Women'') is a psychological thriller novel by Swedish author and journalist Stieg Larsson (1954ŌĆō2004). It was published posthumously in 2 ...
'', Lisbeth Salander
Lisbeth Salander is a fictional character created by Swedish author and journalist Stieg Larsson in his award-winning ''Millennium'' series. She first appeared in the 2005 novel ''The Girl with the Dragon Tattoo'', as an asocial computer hacker ...
uses computers to get information on people, as well as other common surveillance methods, as a freelancer.
* ''V for Vendetta
''V for Vendetta'' is a British graphic novel written by Alan Moore and illustrated by David Lloyd (with additional art by Tony Weare). Initially published between 1982 and 1985 in black and white as an ongoing serial in the British antholog ...
,'' a British graphic novel
A graphic novel is a long-form, fictional work of sequential art. The term ''graphic novel'' is often applied broadly, including fiction, non-fiction, and anthologized work, though this practice is highly contested by comic scholars and industry ...
written by Alan Moore
Alan Moore (born 18 November 1953) is an English author known primarily for his work in comic books including ''Watchmen'', ''V for Vendetta'', ''The Ballad of Halo Jones'', ''Swamp Thing'', ''Batman:'' ''The Killing Joke'', and ''From Hell' ...
* David Egger's novel '' The Circle'' exhibits a world where a single company called "The Circle" produces all of the latest and highest quality technologies from computers and smartphones, to surveillance cameras known as "See-Change cameras". This company becomes associated with politics when starting a movement where politicians go "transparent" by wearing See-Change cameras on their body to prevent keeping secrets from the public about their daily work activity. In this society, it becomes mandatory to share personal information and experiences because it is The Circle's belief that everyone should have access to all information freely. However, as Eggers illustrates, this takes a toll on the individuals and creates a disruption of power between the governments and the private company. The Circle presents extreme ideologies surrounding mandatory surveillance. Eamon Bailey, one of the Wise Men, or founders of The Circle, believes that possessing the tools to access information about anything or anyone, should be a human right given to all of the world's citizens. By eliminating all secrets, any behaviour that has been deemed shameful will either become normalized or no longer considered shocking. Negative actions will eventually be eradicated from society altogether, through the fear of being exposed to other citizens This would be achieved in part by everyone going transparent, something that Bailey highly supports, although it's notable that none of the Wise Men ever became transparent themselves. One major goal of The Circle is to have all of the world's information filtered through The Circle, a process they call "Completion". A single, private company would then have full access and control over all information and privacy of individuals and governments. Ty Gospodinov, the first founder of The Circle, has major concerns about the completion of the circle. He warns that this step would give The Circle too much power and control, and would quickly lead to totalitarianism
Totalitarianism is a form of government and a political system that prohibits all opposition parties, outlaws individual and group opposition to the state and its claims, and exercises an extremely high if not complete degree of control and reg ...
.
In music
* TheDead Kennedys
Dead Kennedys are an American punk rock band that formed in San Francisco, California, in 1978. The band was one of the defining punk rock, punk bands during its initial eight-year run.
Dead Kennedys' lyrics were usually political in nature, sa ...
' song "I Am The Owl" is about government surveillance and social engineering of political groups.
* The Vienna Teng
Cynthia Yih Shih (born October 3, 1978, Saratoga, California), better known by her stage name Vienna Teng, is an American pianist and singer-songwriter who was based in Detroit, Michigan and now lives in Washington, DC. Teng has released five s ...
song "Hymn of Acxiom" is about corporate data collection and surveillance.
Onscreen
* The film ''Gattaca
''Gattaca'' is a 1997 American dystopian science fiction thriller film written and directed by Andrew Niccol in his filmmaking debut. It stars Ethan Hawke and Uma Thurman with Jude Law, Loren Dean, Ernest Borgnine, Gore Vidal, and Alan Arkin ap ...
'' portrays a society that uses biometric
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify in ...
surveillance to distinguish between people who are genetically engineered "superior" humans and genetically natural "inferior" humans.
* In the movie ''Minority Report
Minority Report may refer to:
* Minority report (Poor Law), published by the UK Royal Commission on the Poor Laws and Relief of Distress 1905ŌĆō09
* "Minority Report", a 1949 science fiction short story by Theodore Sturgeon
* "The Minority Report ...
'', the police and government intelligence agencies use micro aerial vehicles in SWAT
In the United States, a SWAT team (special weapons and tactics, originally special weapons assault team) is a police tactical unit that uses specialized or military equipment and tactics. Although they were first created in the 1960s to ...
operations and for surveillance purposes.
* HBO
Home Box Office (HBO) is an American premium television network, which is the flagship property of namesake parent subsidiary Home Box Office, Inc., itself a unit owned by Warner Bros. Discovery. The overall Home Box Office business unit is ba ...
's crime-drama series ''The Sopranos
''The Sopranos'' is an American Crime film#Crime drama, crime drama television series created by David Chase. The story revolves around Tony Soprano (James Gandolfini), a New Jersey-based American Mafia, Italian-American mobster, portraying h ...
'' regularly portrays the FBI's surveillance of the DiMeo Crime Family
The Soprano family (originally the DiMeo family) is a fictional Italian-American crime family featured in the HBO series ''The Sopranos'' and the prequel film '' The Many Saints of Newark''. Based in New Jersey, the family consists of an administ ...
. Audio devices they use include " bugs" placed in strategic locations (e.g., in "I Dream of Jeannie Cusamano
"I Dream of Jeannie Cusamano" is the 13th episode of the HBO original series ''The Sopranos'' and the finale of the show's first season. Written by David Chase and directed by John Patterson, it originally aired on April 4, 1999.
Starring
* Ja ...
" and "Mr. Ruggerio's Neighborhood
"Mr. Ruggerio's Neighborhood" is the 27th episode of the HBO original series ''The Sopranos'' and the first of the show's third season. It was written by David Chase and directed by Allen Coulter, and originally aired on March 4, 2001.
Starring
* ...
") and hidden microphones worn by operatives (e.g., in "Rat Pack
The Rat Pack was an informal group of entertainers, the second iteration of which ultimately made films and appeared together in Las Vegas casino venues. They originated in the late 1940s and early 1950s as a group of A-list show business frie ...
") and informants (e.g., in "Funhouse
A funhouse or fun house is an amusement facility found on amusement park and funfair midways and is where patrons encounter and interact with various devices designed to surprise, challenge, and amuse them. Unlike thrill rides or dark rides, fu ...
", " Proshai, Livushka" and " Members Only"). Visual devices include hidden still cameras (e.g., in "Pax Soprana
"Pax Soprana" is the sixth episode of the HBO original series ''The Sopranos''. It was written by Frank Renzulli, directed by Alan Taylor and originally aired on February 14, 1999.
Starring
* James Gandolfini as Tony Soprano
* Lorraine Bracco ...
") and video cameras (e.g., in "Long Term Parking
"Long Term Parking" is the 64th episode of the HBO original series ''The Sopranos'' and the 12th of the show's fifth season. Written by Terence Winter and directed by Tim Van Patten, it originally aired on May 23, 2004.
Starring
* James Gandolf ...
").
* The movie ''THX-1138
''THX 1138'' is a 1971 American social science fiction film co-written and directed by George Lucas in his directorial debut. Produced by Francis Ford Coppola and co-written by Walter Murch, the film stars Robert Duvall and Donald Pleasence, wit ...
'' portrays a society wherein people are drugged with sedatives and antidepressants, and have surveillance cameras watching them everywhere they go.
* The movie ''The Lives of Others
''The Lives of Others'' (german: link=no, Das Leben der Anderen, ) is a 2006 German drama film written and directed by Florian Henckel von Donnersmarck marking his feature film directorial debut. The plot is about the monitoring of East Berlin ...
'' portrays the monitoring of East Berlin
East Berlin was the ''de facto'' capital city of East Germany from 1949 to 1990. Formally, it was the Allied occupation zones in Germany, Soviet sector of Berlin, established in 1945. The American, British, and French sectors were known as ...
by agents of the Stasi
The Ministry for State Security, commonly known as the (),An abbreviation of . was the Intelligence agency, state security service of the East Germany from 1950 to 1990.
The Stasi's function was similar to the KGB, serving as a means of maint ...
, the GDR's secret police.
* The movie ''The Conversation
''The Conversation'' is a 1974 American mystery thriller film written, produced, and directed by Francis Ford Coppola and starring Gene Hackman, John Cazale, Allen Garfield, Cindy Williams, Frederic Forrest, Harrison Ford, Teri Garr, and Rober ...
'' portrays many methods of audio surveillance.
* The movie ''V for Vendetta
''V for Vendetta'' is a British graphic novel written by Alan Moore and illustrated by David Lloyd (with additional art by Tony Weare). Initially published between 1982 and 1985 in black and white as an ongoing serial in the British antholog ...
'', a 2005 dystopian
A dystopia (from Ancient Greek ╬┤ŽģŽā- "bad, hard" and ŽäŽīŽĆ╬┐Žé "place"; alternatively cacotopiaCacotopia (from ╬║╬▒╬║ŽīŽé ''kakos'' "bad") was the term used by Jeremy Bentham in his 1818 Plan of Parliamentary Reform (Works, vol. 3, p. 493). ...
political thriller film
A political thriller is a thriller that is set against the backdrop of a political power struggle, high stakes and suspense is the core of the story. The genre often forces the audiences to consider and understand the importance of politics. The ...
directed by James McTeigue
James McTeigue (born December 29, 1967) is an Australian film and television director. He has been an assistant director on many films, including '' Dark City'' (1998), the ''Matrix'' trilogy (1999ŌĆō2003) and '' Star Wars: Episode II ŌĆō Atta ...
and written by the Wachowskis
Lana Wachowski (born June 21, 1965, formerly known as Larry Wachowski) and Lilly Wachowski (born December 29, 1967, formerly known as Andy Wachowski) are American film and television directors, writers and producers. The sisters are both trans ...
, is about British government trying to brainwash people by media, obtain their support by fearmongering, monitor them by mass surveillance devices, and suppress or kill any political or social objection.
* The movie ''Enemy of the State
An enemy of the state is a person accused of certain crimes against the state such as treason, among other things. Describing individuals in this way is sometimes a manifestation of political repression. For example, a government may purport to ...
'' a 1998 American action
Action may refer to:
* Action (narrative), a literary mode
* Action fiction, a type of genre fiction
* Action game, a genre of video game
Film
* Action film, a genre of film
* ''Action'' (1921 film), a film by John Ford
* ''Action'' (1980 fil ...
-thriller film
Thriller film, also known as suspense film or suspense thriller, is a broad film genre that evokes excitement and suspense in the audience. The suspense element found in most films' plots is particularly exploited by the filmmaker in this genre ...
directed by Tony Scott
Anthony David Leighton Scott (21 June 1944 ŌĆō 19 August 2012) was an English film director and producer. He was known for directing highly successful action and thriller films such as ''Top Gun'' (1986), ''Beverly Hills Cop II'' (1987), ''Day ...
is about using U.S. citizens' data to search their background and surveillance devices to capture everyone that is identified as "enemy".
*The British TV series '' The Capture'' explores the potential for video surveillance to be manipulated in order to support a conviction to pursue a political agenda.
See also
*Computer and network surveillance
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be comple ...
* Mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizati ...
* Sousveillance
Sousveillance ( ) is the recording of an activity by a member of the public, rather than a person or organisation in authority, typically by way of small wearable or portable personal technologies. The term, coined by Steve Mann, stems from th ...
* Surveillance art Surveillance art is the use of technology intended to record human behavior in a way that offers commentary on the process of surveillance or the technology used to surveil. Surveillance art manifests itself in many different forms, from short film ...
* Surveillance capitalism
Surveillance capitalism is a concept in political economics which denotes the widespread collection and commodification of personal data by corporations. This phenomenon is distinct from government surveillance, though the two can reinforce each ...
* Surveillance system monitor
Surveillance system monitors are tasked with monitoring premises of public transportation terminals to detect crimes or disturbances, using closed-circuit television monitors, and notifying authorities by telephone of need for corrective action. ...
* Trapwire
* Participatory surveillance
Participatory surveillance is community-based monitoring of other individuals. This term can be applied to both digital media studies and ecological field studies. In the realm of media studies, it refers to how users surveil each other using the ...
* PRISM (surveillance program)
Prism usually refers to:
* Prism (optics), a transparent optical component with flat surfaces that refract light
* Prism (geometry), a kind of polyhedron
Prism may also refer to:
Science and mathematics
* Prism (geology), a type of sedimentary ...
* The Age of Surveillance Capitalism
''The Age of Surveillance Capitalism: The Fight for a Human Future at the New Frontier of Power'' is a 2019 non-fiction book by Shoshana Zuboff which looks at the development of digital companies like Google and Amazon, and suggests that their b ...
* Data Mining
References
Further reading
* Allmer, Thomas. (2012). ''Towards a Critical Theory of Surveillance in Informational Capitalism''. Frankfurt am Main: Peter Lang. * Andrejevic, Mark. 2007. ''iSpy: Surveillance and Power in the Interactive Era''. Lawrence, KS: University Press of Kansas. * Ball, Kirstie, Kevin D. Haggerty, and David Lyon, eds. (2012). ''Routledge Handbook of Surveillance Studies''. New York: Routledge. * Brayne, Sarah. (2020). ''Predict and Surveil: Data, Discretion, and the Future of Policing''. New York: Oxford University Press. * Browne, Simone. (2015). ''Dark Matters: On the Surveillance of Blackness''. Durham: Duke University Press. * Coleman, Roy, and Michael McCahill. 2011. ''Surveillance & Crime''. Thousand Oaks, Calif.: Sage. * Feldman, Jay. (2011). ''Manufacturing Hysteria: A History of Scapegoating, Surveillance, and Secrecy in Modern America''. New York, NY: Pantheon Books. * Fuchs, Christian, Kees Boersma, Anders Albrechtslund, and Marisol Sandoval, eds. (2012). "Internet and Surveillance: The Challenges of Web 2.0 and Social Media". New York: Routledge. * Garfinkel, Simson, ''Database Nation; The Death of Privacy in the 21st Century''. O'Reilly & Associates, Inc. * Gilliom, John. (2001). ''Overseers of the Poor: Surveillance, Resistance, and the Limits of Privacy'', University Of Chicago Press, * Haque, Akhlaque. (2015). Surveillance, Transparency and Democracy: Public Administration in the Information Age. University of Alabama Press, Tuscaloosa, AL. * Harris, Shane. (2011). ''The Watchers: The Rise of America's Surveillance State''. London, UK: Penguin Books Ltd. * Hier, Sean P., & Greenberg, Joshua (Eds.). (2009). ''Surveillance: Power, Problems, and Politics''. Vancouver, CA: UBC Press. * Jensen, Derrick and Draffan, George (2004) ''Welcome to the Machine: Science, Surveillance, and the Culture of Control'' Chelsea Green Publishing Company. * Lewis, Randolph. (2017). ''Under Surveillance: Being Watched in Modern America''. Austin: University of Texas Press. * Lyon, David (2001). ''Surveillance Society: Monitoring in Everyday Life''. Philadelphia: Open University Press. * Lyon, David (Ed.). (2006). ''Theorizing Surveillance: The Panopticon and Beyond''. Cullompton, UK: Willan Publishing. * Lyon, David (2007) ''Surveillance Studies: An Overview''. Cambridge: Polity Press. * Matteralt, Armand. (2010). ''The Globalization of Surveillance''. Cambridge, UK: Polity Press. * Monahan, Torin, ed. (2006). ''Surveillance and Security: Technological Politics and Power in Everyday Life''. New York: Routledge. * Monahan, Torin. (2010). ''Surveillance in the Time of Insecurity''. New Brunswick: Rutgers University Press. * Monahan, Torin, and David Murakami Wood, eds. (2018). ''Surveillance Studies: A Reader''. New York: Oxford University Press. * Parenti, Christian ''The Soft Cage: Surveillance in America From Slavery to the War on Terror'', Basic Books, * Petersen, J.K. (2012) ''Handbook of Surveillance Technologies, Third Edition'', Taylor & Francis: CRC Press, 1020 pp., * Staples, William G. (2000). ''Everyday Surveillance: Vigilance and Visibility in Post-Modern Life''. Lanham, MD: Rowman & Littlefield Publishers. * Yan, W. (2019). ''Introduction to Intelligent Surveillance: Surveillance Data Capture, Transmission, and Analytics ''. Springer Publishers.General information
* (Volume 66, Number 3, JulyŌĆōAugust)ACLU, "The Surveillance-Industrial Complex: How the American Government Is Conscripting Businesses and Individuals in the Construction of a Surveillance Society"
Balkin, Jack M. (2008). "The Constitution in the National Surveillance State", Yale Law School
Bibo, Didier and Delmas-Marty, "The State and Surveillance: Fear and Control"
EFF Privacy Resources
ICO. (September 2006). "A Report on the Surveillance Society for the Information Commissioner by the Surveillance Studies Network".
*
Historical information
ĆöFBI counterintelligence programs designed to neutralize political dissidents
ŌĆō A Short History of Electronic Surveillance in the United States
Legal resources
EFF Legal Cases
External links
* {{Authority control Crime prevention Espionage techniques Law enforcement Law enforcement techniques National security Privacy Security