|
Biometric
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, behavioral profiling, and credentials. Some researchers have coined the term behaviometrics to describe the latter class ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometric Island, Gdansk University Of Technology 2021
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, behavioral profiling, and credentials. Some researchers have coined the term behaviometrics to describe the latter class ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometric System Diagram
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, behavioral profiling, and credentials. Some researchers have coined the term behaviometrics to describe the latter class o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometric Passport
A biometric passport (also known as an e-passport or a digital passport) is a traditional passport that has an embedded electronic microprocessor chip which contains biometric information that can be used to authenticate the identity of the passport holder. It uses contactless smart card technology, including a microprocessor chip (computer chip) and antenna (for both power to the chip and communication) embedded in the front or back cover, or centre page, of the passport. The passport's critical information is printed on the data page of the passport, repeated on the machine readable lines and stored in the chip. Public key infrastructure (PKI) is used to authenticate the data stored electronically in the passport chip, making it expensive and difficult to forge when all security mechanisms are fully and correctly implemented. Many countries are moving towards issuing biometric passports to their citizens. Malaysia was the first country to issue biometric passports in 1998. I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Iris Recognition
Iris recognition is an automated method of biometric identification that uses mathematical pattern-recognition techniques on video images of one or both of the irises of an individual's eyes, whose complex patterns are unique, stable, and can be seen from some distance. The discriminating powers of all biometric technologies depend on the amount of entropy they are able to encode and use in matching. Iris recognition is exceptional in this regard, enabling the avoidance of "collisions" (False Matches) even in cross-comparisons across massive populations. Its major limitation is that image acquisition from distances greater than a meter or two, or without cooperation, can be very difficult. Retinal scanning is a different, ocular-based biometric technology that uses the unique patterns on a person's retina blood vessels and is often confused with iris recognition. Iris recognition uses video camera technology with subtle near infrared illumination to acquire images of the detail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Facial Recognition System
A facial recognition system is a technology capable of matching a human face from a digital image or a video frame against a database of faces. Such a system is typically employed to authenticate users through ID verification services, and works by pinpointing and measuring facial features from a given image. Development began on similar systems in the 1960s, beginning as a form of computer application. Since their inception, facial recognition systems have seen wider uses in recent times on smartphones and in other forms of technology, such as robotics. Because computerized facial recognition involves the measurement of a human's physiological characteristics, facial recognition systems are categorized as biometrics. Although the accuracy of facial recognition systems as a biometric technology is lower than iris recognition and fingerprint recognition, it is widely adopted due to its contactless process. Facial recognition systems have been deployed in advanced human–compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fingerprint
A fingerprint is an impression left by the friction ridges of a human finger. The recovery of partial fingerprints from a crime scene is an important method of forensic science. Moisture and grease on a finger result in fingerprints on surfaces such as glass or metal. Deliberate impressions of entire fingerprints can be obtained by ink or other substances transferred from the peaks of friction ridges on the skin to a smooth surface such as paper. Fingerprint records normally contain impressions from the pad on the last joint of fingers and thumbs, though fingerprint cards also typically record portions of lower joint areas of the fingers. Human fingerprints are detailed, nearly unique, difficult to alter, and durable over the life of an individual, making them suitable as long-term markers of human identity. They may be employed by police or other authorities to identify individuals who wish to conceal their identity, or to identify people who are incapacitated or deceased and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Smart Card
A smart card, chip card, or integrated circuit card (ICC or IC card) is a physical electronic authentication device, used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, mobile phones (SIM), public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card, or SIM card, is also a type of smart card. , 10.5billion smart card IC chips are manufactured annually, including 5.44billion SIM card IC chips. Hist ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as Human intelligence (intelligence gathering), human intelligence gathering and postal interception. Surveillance is used by citizens for protecting their neighborhoods. And by governments for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to Industrial espionage, gather intelligence on criminals, their competitors, suppliers or customers. Religious organisations charged with detecting he ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hand Geometry
Hand geometry is a biometric that identifies users from the shape of their hands. Hand geometry readers measure a user's palm and fingers along many dimensions including length, width, deviation, and angle and compare those measurements to measurements stored in a file. History Viable hand geometry devices have been manufactured since the early 1970s, making hand geometry the first biometric to find widespread computerized use. Robert Miller realized the distinctive features of hand sizes and shapes could be used for identification and patented the first automated hand geometry device at the Stanford Research Institute in 1971. The device would measure the hand, and the numbers needed to match the punched holes of a user ID card to activate the circuit to be identified. David Sidlauskas was also a major player in the hand geometry device production, and he patented Handkey ID3D, the first hand scanner that worked in 3D that involved an optical measuring plate, camera, and numer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
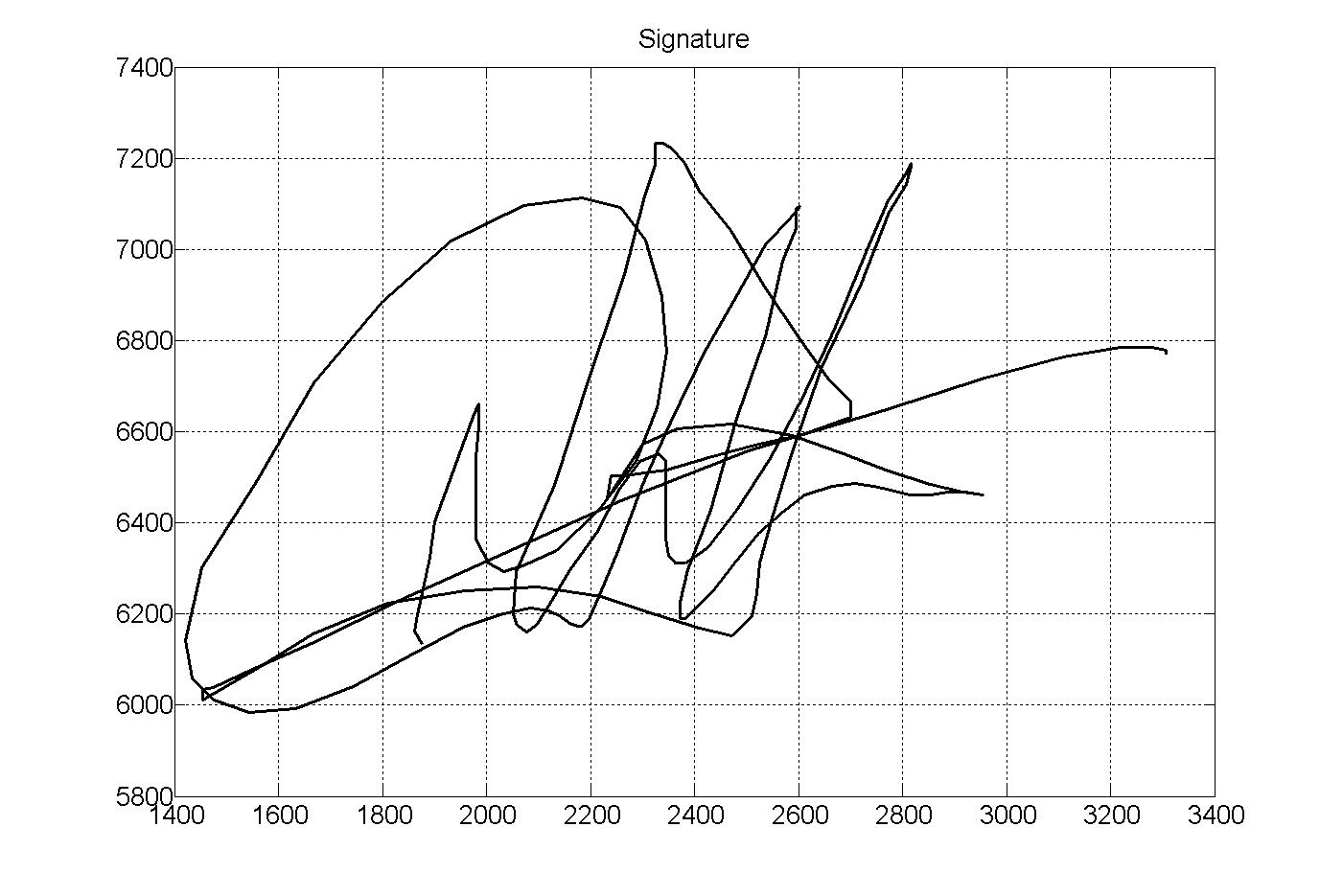
Signature Recognition
Signature recognition is an example of behavioral biometrics that identifies a person based on their handwriting. It can be operated in two different ways: Static: In this mode, users write their signature on paper, and after the writing is complete, it is digitized through an optical scanner or a camera to turn the signature image into bits. The biometric system then recognizes the signature analyzing its shape. This group is also known as "off-line". Dynamic: In this mode, users write their signature in a digitizing tablet, which acquires the signature in real time. Another possibility is the acquisition by means of stylus-operated PDAs. Some systems also operate on smart-phones or tablets with a capacitive screen, where users can sign using a finger or an appropriate pen. Dynamic recognition is also known as "on-line". Dynamic information usually consists of the following information: * spatial coordinate x(t) * spatial coordinate y(t) * pressure p(t) * azimuth az(t) * inclinat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Passport
A passport is an official travel document issued by a government that contains a person's identity. A person with a passport can travel to and from foreign countries more easily and access consular assistance. A passport certifies the personal identity and nationality of its holder. It is typical for passports to contain the full name, photograph, place and date of birth, signature, and the expiration date of the passport. While passports are typically issued by national governments, certain subnational governments are authorised to issue passports to citizens residing within their borders. Many nations issue (or plan to issue) biometric passports that contain an embedded microchip, making them machine-readable and difficult to counterfeit. , there were over 150 jurisdictions issuing e-passports. Previously issued non-biometric machine-readable passports usually remain valid until their respective expiration dates. A passport holder is normally entitled to enter the country ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multi-factor Authentication
Multi-factor authentication (MFA; encompassing two-factor authentication, or 2FA, along with similar terms) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something only the user knows), possession (something only the user has), and inherence (something only the user is). MFA protects user data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password. A ''third-party authenticator'' (TPA) app enables two-factor authentication, usually by showing a randomly generated and frequently changing code to use for authentication. Factors Authentication takes place when someone tries to log into a computer resource (such as a network, device, or application). The resource requires the u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |





.jpg)