|
Video Hash
Video fingerprinting or video hashing are a class of dimension reduction techniques in which a system identifies, extracts, and then summarizes characteristic components of a video as a unique or a set of multiple perceptual hashes, enabling that video to be uniquely identified. This technology has proven to be effective at searching and comparing video files. History and process Video fingerprinting was first developed into practical use by Philips in 2002.Oostveen, J., Kalker, T., & Haitsma, J. (2002, March). Feature extraction and a database strategy for video fingerprinting. In ''International Conference on Advances in Visual Information Systems'' (pp. 117-128). Springer, Berlin, Heidelberg. Different methods exist for video fingerprinting. Van Oostveen relied on changes in patterns of image intensity over successive video frames. This makes the video fingerprinting robust against limited changes in color - or the transformation of color into gray scale of the original video ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
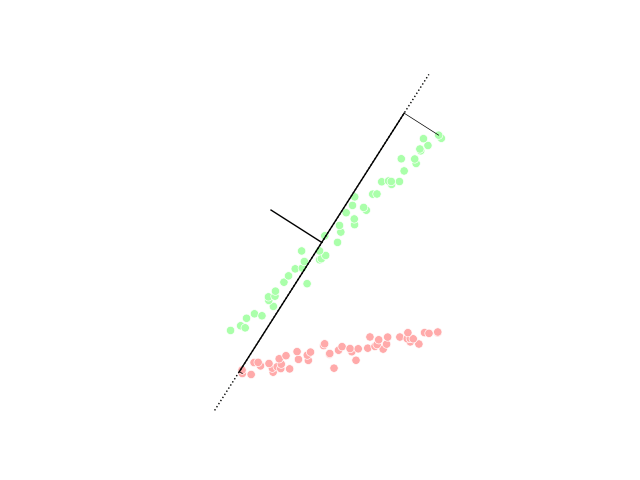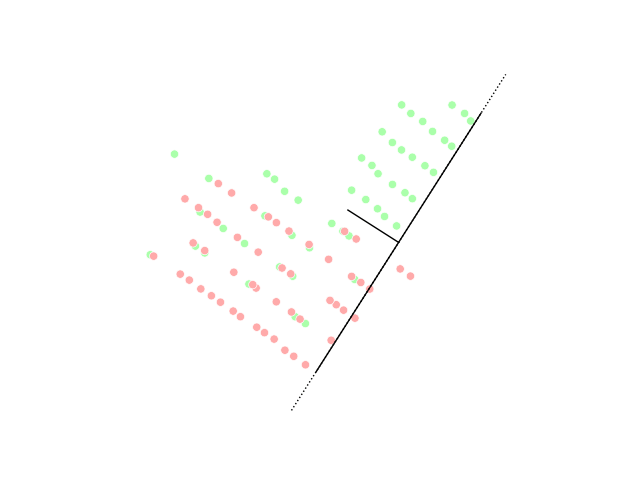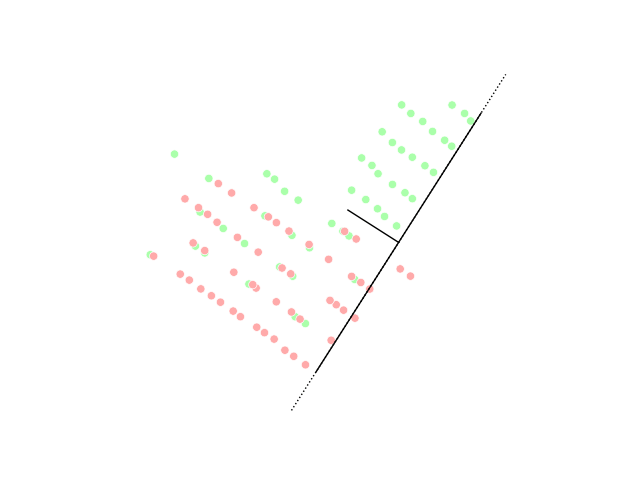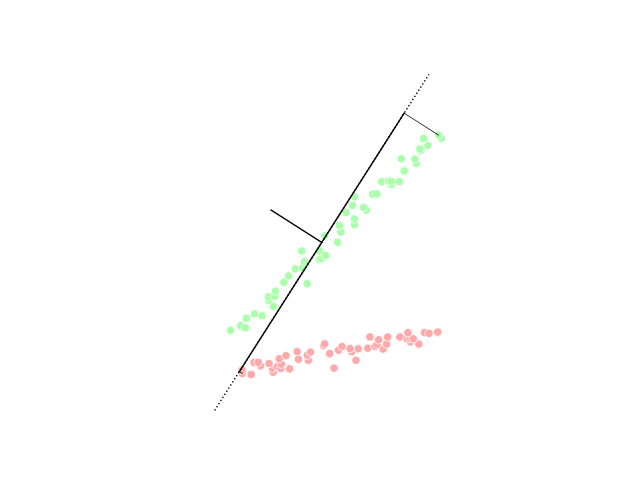
Dimensionality Reduction
Dimensionality reduction, or dimension reduction, is the transformation of data from a high-dimensional space into a low-dimensional space so that the low-dimensional representation retains some meaningful properties of the original data, ideally close to its intrinsic dimension. Working in high-dimensional spaces can be undesirable for many reasons; raw data are often sparse as a consequence of the curse of dimensionality, and analyzing the data is usually computationally intractable (hard to control or deal with). Dimensionality reduction is common in fields that deal with large numbers of observations and/or large numbers of variables, such as signal processing, speech recognition, neuroinformatics, and bioinformatics. Methods are commonly divided into linear and nonlinear approaches. Approaches can also be divided into feature selection and feature extraction. Dimensionality reduction can be used for noise reduction, data visualization, cluster analysis, or as an intermediat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HDNet
AXS TV is an American cable television channel. Majority-owned by Anthem Sports & Entertainment, it is devoted primarily to music-related programming (such as concert films, documentaries, and reality series involving musicians) and combat sports – including boxing, mixed martial arts and professional wrestling. The network was originally established in 2001 as HDNet, with investor Mark Cuban as a founding partner. HDNet was originally intended as an exclusively- high-definition network, carrying films and acquired television series, concerts, news programming, and sporting events produced in the format. HDNet's original niche became increasingly redundant as more cable networks established their own HD feeds. In 2012, HDNet sold ownership stakes to Anschutz Entertainment Group (AEG), Creative Artists Agency, and Ryan Seacrest, with Cuban retaining a majority stake. It then relaunched under its current name–taken from AEG's online ticket platform AXS.com–on July 2, 2012, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Video Content Analysis
Video content analysis or video content analytics (VCA), also known as video analysis or video analytics (VA), is the capability of automatically analyzing video to detect and determine temporal and spatial events. This technical capability is used in a wide range of domains including entertainment,KINECT , add-on peripheral for the console and video browsing, health-care, retail, automotive, transport, home automation< ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Perceptual Hashing
Perceptual hashing is the use of a fingerprinting algorithm that produces a snippet, hash, or fingerprint of various forms of multimedia. A perceptual hash is a type of locality-sensitive hash, which is analogous if features of the multimedia are similar. This is not to be confused with cryptographic hashing, which relies on the avalanche effect of a small change in input value creating a drastic change in output value. Perceptual hash functions are widely used in finding cases of online copyright infringement as well as in digital forensics because of the ability to have a correlation between hashes so similar data can be found (for instance with a differing watermark). Development The 1980 work of Marr and Hildreth is a seminal paper in this field. The July 2010 thesis of Christoph Zauner is a well-written introduction to the topic. In June 2016 Azadeh Amir Asgari published work on robust image hash spoofing. Asgari notes that perceptual hash function like any other algorit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Acoustic Fingerprint
An acoustic fingerprint is a condensed digital summary, a fingerprint, deterministically generated from an audio signal, that can be used to identify an audio sample or quickly locate similar items in an audio database. Practical uses of acoustic fingerprinting include identifying songs, melodies, tunes, or advertisements; sound effect library management; and video file identification. Media identification using acoustic fingerprints can be used to monitor the use of specific musical works and performances on radio broadcast, records, CDs, streaming media and peer-to-peer networks. This identification has been used in copyright compliance, licensing, and other monetization schemes. Attributes A robust acoustic fingerprint algorithm must take into account the perceptual characteristics of the audio. If two files sound alike to the human ear, their acoustic fingerprints should match, even if their binary representations are quite different. Acoustic fingerprints are not h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Online Service Provider
An online service provider (OSP) can, for example, be an Internet service provider, an email provider, a news provider (press), an entertainment provider (music, movies), a search engine, an e-commerce site, an online banking site, a health site, an official government site, social media, a wiki, or a Usenet newsgroup. In its original more limited definition, it referred only to a commercial computer communication service in which paid members could dial via a computer modem the service's private computer network and access various services and information resources such as bulletin board systems, downloadable files and programs, news articles, chat rooms, and electronic mail services. The term "online service" was also used in references to these dial-up services. The traditional dial-up online service differed from the modern Internet service provider in that they provided a large degree of content that was only accessible by those who subscribed to the online service, while ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Provider
A software publisher is a publishing company in the software industry between the developer and the distributor. In some companies, two or all three of these roles may be combined (and indeed, may reside in a single person, especially in the case of shareware). Software publishers often license software from the original author-developers with specific limitations, such as a time limit or geographical region for a royalty consideration. The terms of licensing vary enormously, and are typically secret. The author-developers may use publishers to reach larger or foreign markets. Typically, the publisher will bear most of the cost of entering these markets. In return they pay the developer an agreed upon royalty payment. The duties of the publisher can vary greatly depending on the agreement reached between the parties. Duties can include: *Translating language elements into the local language *Building demand for the software in the local market *Produce & Design boxed softwar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Child Pornography
Child pornography (also called CP, child sexual abuse material, CSAM, child porn, or kiddie porn) is pornography that unlawfully exploits children for sexual stimulation. It may be produced with the direct involvement or sexual assault of a child (also known as child sexual abuse images) or it may be simulated child pornography. Abuse of the child occurs during the sexual acts or lascivious exhibitions of genitals or pubic areas which are recorded in the production of child pornography. Child pornography may use a variety of mediums, including writings, magazines, photos, sculpture, drawing, painting, animation, sound recording, video, and video games. Child pornography may be created for profit or other reasons. Laws regarding child pornography generally include sexual images involving prepubescents, pubescent, or post-pubescent minors and computer-generated images that appear to involve them. Most possessors of child pornography who are arrested are found to possess images o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Centre For Missing & Exploited Children
The International Centre for Missing & Exploited Children (ICMEC), headquartered in Alexandria, Virginia, with a regional presence in Brazil, Singapore, and Australia, is a private 501(c)(3) non-governmental, nonprofit global organization. It combats child sexual exploitation, child pornography, and child abduction. Formed in 1998, ICMEC heads a global missing children's network of 29 countries. The organization has trained law enforcement personnel from 121 countries, works with law enforcement in over 100 countries, and has worked with legislatures in 100 countries to adopt new laws combating child sexual abuse material. ICMEC also encourages the creation of national operational centers built on a public-private partnership model, and leads global financial and industry coalitions to eradicate child sexual exploitation and child pornography. The Koons Family Institute on International Law and Policy is the International Centre's research arm. In August 2008, ICMEC was granted ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Amsterdam
The University of Amsterdam (abbreviated as UvA, nl, Universiteit van Amsterdam) is a public research university located in Amsterdam, Netherlands. The UvA is one of two large, publicly funded research universities in the city, the other being the Vrije Universiteit Amsterdam (VU). Established in 1632 by municipal authorities and later renamed for the city of Amsterdam, the University of Amsterdam is the third-oldest university in the Netherlands. It is one of the largest research universities in Europe with 31,186 students, 4,794 staff, 1,340 PhD students and an annual budget of €600 million. It is the largest university in the Netherlands by enrollment. The main campus is located in central Amsterdam, with a few faculties located in adjacent boroughs. The university is organised into seven faculties: Humanities, Social and Behavioural Sciences, Economics and Business, Science, Law, Medicine, Dentistry. The University of Amsterdam has produced six Nobel Laureates and fiv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Netherlands Organisation For Applied Scientific Research
Nederlandse Organisatie voor Toegepast Natuurwetenschappelijk Onderzoek (TNO; en, Netherlands Organisation for Applied Scientific Research) is an independent research organisation in the Netherlands that focuses on applied science. The organisation also conducts contract research, offers specialist consulting services, and grants licences for patents and specialist software. TNO tests and certifies products and services, and issues an independent evaluation of quality. Moreover, TNO sets up new companies to market innovations. Background TNO was established by law in 1932 to support companies and governments with innovative, practicable knowledge. As a statutory organisation, TNO has an independent position that allows to give objective, scientifically founded judgments. It is similar to the following: * CSIR in Ghana * CSIR in India * CSIR in South Africa * CSIRO in Australia * Fraunhofer Society in Germany * SINTEF in Norway Furthermore, TNO also held 10% of the Austrian ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Police Corps (Netherlands)
National Police Corps ( nl, Korps Nationale Politie), colloquially in English as Dutch National Police or National Police Force, is divided in ten regional units, a central unit, the police academy, police services center, and national control room cooperation. The law-enforcement purposes of these agencies are the investigation of suspected criminal activity, referral of the results of investigations to the courts, and the temporary detention of suspected criminals pending judicial action. Law enforcement agencies, to varying degrees at different levels of government and in different agencies, are also commonly charged with the responsibilities of deterring criminal activity and preventing the successful commission of crimes in progress. The police commissioner (eerste hoofdcommissaris) in the Netherlands is Henk van Essen since May 1, 2020. Besides police officers, the Netherlands has about 23,500 peace officers. These officers have a Special Enforcement Officer (SEO) status ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |