|
Transient-key Cryptography
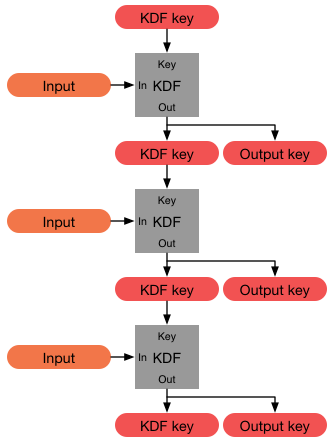
Transient-key cryptography is a form of public-key cryptography wherein keypairs are generated and assigned to brief intervals of time instead of to individuals or organizations, and the blocks of cryptographic data are chained through time. In a transient-key system, private keys are used briefly and then destroyed, which is why it is sometimes nicknamed “disposable crypto.” Data encrypted with a private key associated with a specific time interval can be irrefutably linked to that interval, making transient-key cryptography particularly useful for digital trusted timestamping. Transient-key cryptography was invented in 1997 by Michael Doyle of Eolas, and has been adopted in the ANSI ASC X9.95 Standard for trusted timestamps. Public-key vs. transient-key Both public key and transient-key systems can be used to generate digital signatures that assert that a given piece of data has not changed since it was signed. But the similarities end there. In a traditional public key s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public-key Cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. There are many kinds of public-key cryptosystems, with different security goals, including digital signature, Diffie–Hellman key exchange, Key encapsulation mechanism, public-key key encapsulation, and public-key encryption. Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols that offer assurance of the confidentiality and authenticity of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security, T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Log
A data logger (also datalogger or data recorder) is an electronic device that records data over time or about location either with a built-in instrument or sensor or via external instruments and sensors. Increasingly, but not entirely, they are based on a digital processor (or computer), and called digital data loggers (DDL). They generally are small, battery-powered, portable, and equipped with a microprocessor, internal memory for data storage, and sensors. Some data loggers interface with a personal computer and use software to activate the data logger and view and analyze the collected data, while others have a local interface device (keypad, LCD) and can be used as a stand-alone device. Data loggers vary from general-purpose devices for various measurement applications to very specific devices for measuring in one environment or application type only. While it is common for general-purpose types to be programmable, many remain static machines with only a limited number o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blockchain (database)
The blockchain is a distributed ledger with growing lists of records (''blocks'') that are securely linked together via cryptographic hashes. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree, where data nodes are represented by leaves). Since each block contains information about the previous block, they effectively form a ''chain'' (compare linked list data structure), with each additional block linking to the ones before it. Consequently, blockchain transactions are resistant to alteration because, once recorded, the data in any given block cannot be changed retroactively without altering all subsequent blocks and obtaining network consensus to accept these changes. Blockchains are typically managed by a peer-to-peer (P2P) computer network for use as a public distributed ledger, where nodes collectively adhere to a consensus algorithm protocol to add and validate new transaction blo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bitcoin
Bitcoin (abbreviation: BTC; Currency symbol, sign: ₿) is the first Decentralized application, decentralized cryptocurrency. Based on a free-market ideology, bitcoin was invented in 2008 when an unknown entity published a white paper under the pseudonym of Satoshi Nakamoto. Use of bitcoin as a currency began in 2009, with the release of its open-source software, open-source implementation. In 2021, Bitcoin in El Salvador, El Salvador adopted it as legal tender. It is mostly seen as an investment and has been described by some scholars as an economic bubble. As bitcoin is pseudonymous, Cryptocurrency and crime, its use by criminals has attracted the attention of regulators, leading to Legality of cryptocurrency by country or territory, its ban by several countries . Bitcoin works through the collaboration of computers, each of which acts as a Node (networking), node in the peer-to-peer bitcoin network. Each node maintains an independent copy of a public distributed ledger of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forward Secrecy
In cryptography, forward secrecy (FS), also known as perfect forward secrecy (PFS), is a feature of specific key-agreement protocols that gives assurances that session keys will not be compromised even if long-term secrets used in the session key exchange are compromised, limiting damage. For TLS, the long-term secret is typically the private key of the server. Forward secrecy protects past sessions against future compromises of keys or passwords. By generating a unique session key for every session a user initiates, the compromise of a single session key will not affect any data other than that exchanged in the specific session protected by that particular key. This by itself is not sufficient for forward secrecy which additionally requires that a long-term secret compromise does not affect the security of past session keys. Forward secrecy protects data on the transport layer of a network that uses common transport layer security protocols, including OpenSSL, when its long-te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Visible Embryo Project
The Visible Embryo Project (VEP) is a multi-institutional, multidisciplinary research project originally created in the early 1990s as a collaboration between the Developmental Anatomy Center at the National Museum of Health and Medicine and the Biomedical Visualization Laboratory (BVL) at the University of Illinois at Chicago, "to develop software strategies for the development of distributed biostructural databases using cutting-edge technologies for high-performance computing and communications (HPCC), and to implement these tools in the creation of a large-scale digital archive of multidimensional data on normal and abnormal human development." This project related to BVL's other research in the areas of health informatics, educational multimedia, and biomedical imaging science. Over the following decades, the list of VEP collaborators grew to include over a dozen universities, national laboratories, and companies around the world. An early (1993) goal of the project was to enab ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map (mathematics), map of an arbitrary binary string to a binary string with a fixed size of n bits) that has special properties desirable for a cryptography, cryptographic application: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (as for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is infeasible, ''assuming all input strings are equally likely.'' The ''resistance'' to such search is quantified as security strength: a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits, unless the space of possible input values is significantly smaller than 2^ (a practical example can be found in ); * a ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Persistence (computer Science)
In computer science, persistence refers to the characteristic of State (computer science), state of a system that outlives (persists for longer than) the Process (computing), process that created it. This is achieved in practice by storing the state as data in computer data storage. Programs have to transfer data to and from storage devices and have to provide mappings from the native Programming language, programming-language Data structure, data structures to the storage device data structures. Picture editing programs or Word processor, word processors, for example, achieve State (computer science), state persistence by saving their documents to computer file, files. Orthogonal or transparent persistence Persistence is said to be "Orthogonality#Computer science, orthogonal" or "transparent" when it is implemented as an intrinsic property of the execution environment of a program. An orthogonal persistence environment does not require any specific actions by programs running i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Verification
File verification is the process of using an algorithm for verifying the integrity of a computer file, usually by checksum. This can be done by comparing two files bit-by-bit, but requires two copies of the same file, and may miss systematic corruptions which might occur to both files. A more popular approach is to generate a hash of the copied file and comparing that to the hash of the original file. Integrity verification File integrity can be compromised, usually referred to as the file becoming corrupted. A file can become corrupted by a variety of ways: faulty storage media, errors in transmission, write errors during copying or moving, software bugs, and so on. Hash-based verification ensures that a file has not been corrupted by comparing the file's hash value to a previously calculated value. If these values match, the file is presumed to be unmodified. Due to the nature of hash functions, hash collisions may result in false positives, but the likelihood of co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database
In computing, a database is an organized collection of data or a type of data store based on the use of a database management system (DBMS), the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an application associated with the database. Before digital storage and retrieval of data have become widespread, index cards were used for data storage in a wide range of applications and environments: in the home to record and store recipes, shopping lists, contact information and other organizational data; in business to record presentation notes, project research and notes, and contact information; in schools as flash c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Archive
An archive is an accumulation of historical records or materials, in any medium, or the physical facility in which they are located. Archives contain primary source documents that have accumulated over the course of an individual or organization's lifetime, and are kept to show the history and function of that person or organization. Professional archivists and historians generally understand archives to be records that have been naturally and necessarily generated as a product of regular legal, commercial, administrative, or social activities. They have been metaphorically defined as "the secretions of an organism", and are distinguished from documents that have been consciously written or created to communicate a particular message to posterity. In general, archives consist of records that have been selected for permanent or long-term preservation on the grounds of their enduring cultural, historical, or evidentiary value. Archival records are normally unpublished and a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hierarchy
A hierarchy (from Ancient Greek, Greek: , from , 'president of sacred rites') is an arrangement of items (objects, names, values, categories, etc.) that are represented as being "above", "below", or "at the same level as" one another. Hierarchy is an important concept in a wide variety of fields, such as architecture, philosophy, design, mathematics, computer science, organizational theory, systems theory, systematic biology, and the social sciences (especially political science). A hierarchy can link entities either directly or indirectly, and either vertically or diagonally. The only direct links in a hierarchy, insofar as they are hierarchical, are to one's immediate superior or to one of one's subordinates, although a system that is largely hierarchical can also incorporate alternative hierarchies. Hierarchical links can extend "vertically" upwards or downwards via multiple links in the same direction, following a path (graph theory), path. All parts of the hierarchy that are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |