|
Technical Debt
In software development and other information technology fields, technical debt (also known as design debt or code debt) refers to the implied cost of additional work in the future resulting from choosing an expedient solution over a more robust one. While technical debt can accelerate development in the short term, it may increase future costs and complexity if left unresolved. Analogous to monetary debt, technical debt can accumulate "interest" over time, making future changes more difficult and costly. Properly managing this debt is essential for maintaining software quality and long-term sustainability. In some cases, taking on technical debt can be a strategic choice to meet immediate goals, such as delivering a proof-of-concept or a quick release. However, failure to prioritize and address the debt can result in reduced maintainability, increased development costs, and risks to production systems. Technical debt encompasses various design and implementation decisions that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Software Development
Software development is the process of designing and Implementation, implementing a software solution to Computer user satisfaction, satisfy a User (computing), user. The process is more encompassing than Computer programming, programming, writing source code, code, in that it includes conceiving the goal, evaluating feasibility, analyzing software requirements, requirements, software design, design, software testing, testing and software release life cycle, release. The process is part of software engineering which also includes management, organizational management, Software project management, project management, configuration management and other aspects. Software development involves many skills and job specializations including software programmer, programming, software test, testing, Technical writing, documentation, graphic design, user support, marketing, and fundraising. Software development involves many software tools, tools including: compiler, integrated develo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
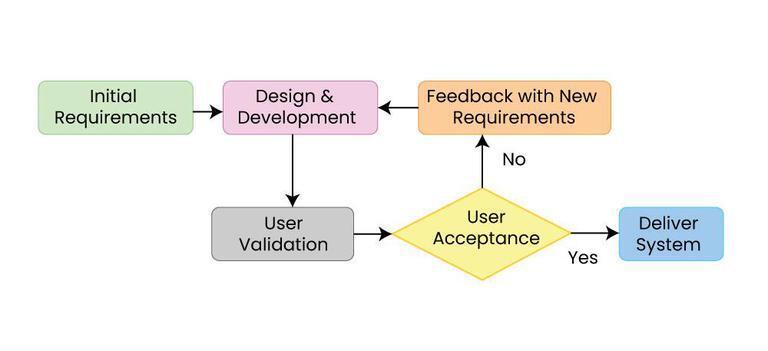
Process
A process is a series or set of activities that interact to produce a result; it may occur once-only or be recurrent or periodic. Things called a process include: Business and management * Business process, activities that produce a specific service or product for customers * Business process modeling, activity of representing processes of an enterprise in order to deliver improvements * Manufacturing process management, a collection of technologies and methods used to define how products are to be manufactured. * Process architecture, structural design of processes, applies to fields such as computers, business processes, logistics, project management * Process area, related processes within an area which together satisfies an important goal for improvements within that area * Process costing, a cost allocation procedure of managerial accounting * Process management (project management), a systematic series of activities directed towards planning, monitoring the performance a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Big Ball Of Mud
An anti-pattern in software engineering, project management, and business processes is a common response to a recurring problem that is usually ineffective and risks being highly counterproductive. The term, coined in 1995 by computer programmer Andrew Koenig (programmer), Andrew Koenig, was inspired by the book ''Design Patterns'' (which highlights a number of design patterns in software development that its authors considered to be highly reliable and effective) and first published in his article in the ''Journal of Object-Oriented Programming''. A further paper in 1996 presented by Michael Ackroyd at the Object World West Conference also documented anti-patterns. It was, however, the 1998 book ''AntiPatterns'' that both popularized the idea and extended its scope beyond the field of software design to include software architecture and project management. Other authors have extended it further since to encompass environmental, organizational, and cultural anti-patterns. Definiti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Code Smell
In computer programming, a code smell is any characteristic in the source code of a program that possibly indicates a deeper problem. Determining what is and is not a code smell is subjective, and varies by language, developer, and development methodology. The term was popularized by Kent Beck on WardsWiki in the late 1990s. Usage of the term increased after it was featured in the 1999 book ''Refactoring: Improving the Design of Existing Code'' by Martin Fowler. It is also a term used by agile programmers. Definition One way to look at smells is with respect to principles and quality: "Smells are certain structures in the code that indicate violation of fundamental design principles and negatively impact design quality". Code smells are usually not bugs; they are not technically incorrect and do not prevent the program from functioning. Instead, they indicate weaknesses in design that may slow down development or increase the risk of bugs or failures in the future. Bad code ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Service-level Agreements
A service-level agreement (SLA) is an agreement between a service provider and a customer. Particular aspects of the service – quality, availability, responsibilities – are agreed between the service provider and the service user. The most common component of an SLA is that the services should be provided to the customer as agreed upon in the contract. As an example, Internet service providers and telcos will commonly include service level agreements within the terms of their contracts with customers to define the level(s) of service being sold in plain language terms. In this case, the SLA will typically have a technical definition of '' mean time between failures'' (MTBF), ''mean time to repair'' or ''mean time to recovery'' (MTTR); identifying which party is responsible for reporting faults or paying fees; responsibility for various data rates; throughput; jitter; or similar measurable details. Overview A service-level agreement is an agreement between two or more ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Estimation (project Management)
Estimation within project management (e.g., for engineering or software development), are the basis of sound project planning. Many processes have been developed to aid project managers in making accurate estimates. Processes (engineering) *Analogy based estimation * Compartmentalization (i.e., breakdown of tasks) * Cost estimate * Delphi method *Documenting estimation results *Educated assumptions *Estimating each task *Examining historical data *Identifying dependencies * Parametric estimating *Risk assessment *Structured planning Processes (software development) Popular estimation processes for software projects include: * Cocomo * Cosysmo * Event chain methodology Event chain methodology is a network theory, network analysis technique that is focused on identifying and managing events and relationships between them (event chains) that affect project schedules. It is an uncertainty modeling schedule techniqu ... * Function points * Planning poker * Program Eval ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Product Backlog
Within agile project management, product backlog refers to a prioritized list of functionality which a product should contain. It is sometimes referred to as a to-do list, and is considered an 'artifact' (a form of documentation) within the Scrum (software development), scrum software development framework. The product backlog is referred to with different names in different project management frameworks, such as ''product backlog'' in scrum, work item list in Disciplined agile delivery, disciplined agile, and option pool in Lean manufacturing, lean. In the scrum framework, creation and continuous maintenance of the product backlog is part of the responsibility of the Scrum (software development), product owner. A sprint backlog consists of selected elements from the product backlog which are planned to be developed within that particular Scrum_(software_development)#Sprint, sprint. In scrum, coherence is defined as a measure of the relationships between backlog items which make th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Upstream (software Development)
In software development, when software has been forked or uses a chain of libraries/ dependencies, upstream refers to an issue that occurs in software related to the chain. It is the direction that is toward the original authors or maintainers of software. It is usually used in the context of a version, a bug, or a patch. Upstream development allows other distributions to benefit from it when they pick up the future release or merge recent (or all) upstream patches. Likewise, the original authors (maintaining upstream) can benefit from contributions that originate from custom distributions, if their users send patches upstream. The term also pertains to bugs; responsibility for a bug is said to lie upstream when it is not caused through the distribution's porting, non-upstream modification or integration efforts. Examples * A patch ''sent upstream'' is offered to the original authors or maintainers of the software. If accepted, the authors or maintainers will include the p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Software Framework
In computer programming, a software framework is a software abstraction that provides generic functionality which developers can extend with custom code to create applications. It establishes a standard foundation for building and deploying software, offering reusable components and design patterns that handle common programming tasks within a larger software platform or environment. Unlike libraries where developers call functions as needed, frameworks implement inversion of control by dictating program structure and calling user code at specific points, while also providing default behaviors, structured extensibility mechanisms, and maintaining a fixed core that accepts extensions without direct modification. Frameworks also differ from regular applications that can be modified (like web browsers through extensions, video games through mods), in that frameworks are intentionally incomplete scaffolding meant to be extended through well-defined extension points and followin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Test Suite
In software development, a test suite, less commonly known as a validation suite, is a collection of test cases that are intended to be used to test a software program to show that it has some specified set of behaviors. A test suite often contains detailed instructions or goals for each collection of test cases and information on the system configuration to be used during testing. A group of test cases may also contain prerequisite states or steps and descriptions of the following tests. Collections of test cases are sometimes termed a test plan, a test script, or even a test scenario. Types Occasionally, test suites are used to group similar test cases together. A system might have a smoke test suite that consists only of smoke tests or a test suite for some specific functionality in the system. It may also contain all tests and signify if a test should be used as a smoke test or for some specific functionality. In model-based testing, one distinguishes between ''abstract ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Coupling (computer Programming)
A coupling is a device used to connect two shafts together at their ends for the purpose of transmitting power. The primary purpose of couplings is to join two pieces of rotating equipment while permitting some degree of misalignment or end movement or both. In a more general context, a coupling can also be a mechanical device that serves to connect the ends of adjacent parts or objects. Couplings do not normally allow disconnection of shafts during operation, however there are torque-limiting couplings which can slip or disconnect when some torque limit is exceeded. Selection, installation and maintenance of couplings can lead to reduced maintenance time and maintenance cost. Uses Shaft couplings are used in machinery for several purposes. A primary function is to transfer power from one end to another end (ex: motor transfer power to pump through coupling). Other common uses: * To alter the vibration characteristics of rotating units * To connect the driving and the driven ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Code Rewriting
A rewrite in computer programming is the act or result of re-implementing a large portion of existing functionality without re-use of its source code. When the rewrite uses no existing code at all, it is common to speak of a rewrite from scratch. Motivations A piece of software is typically rewritten when one or more of the following apply: *its source code is not available or is only available under an incompatible license *its code cannot be adapted to a new target platform *its existing code has become too difficult to handle and extend *the task of debugging it seems too complicated *the programmer finds it difficult to understand its source code *developers learn new techniques or wish to do a big feature overhaul which requires much change *the programming language of the source code has to be changed Risks Several software engineers, such as Joel Spolsky have warned against total rewrites, especially under schedule constraints or competitive pressures. While developers m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |