|
Spamtrap
A spamtrap is a honeypot (computing), honeypot used to collect spam (electronic), spam. Spamtraps are usually e-mail addresses that are created not for communication, but rather to lure spam. In order to prevent legitimate email from being invited, the e-mail address will typically only be published in a location hidden from view such that an automated e-mail address harvester (used by spammers) can find the email address, but no sender would be encouraged to send messages to the email address for any legitimate purpose. Since no e-mail is solicited by the owner of this spamtrap e-mail address, any e-mail messages sent to this address are immediately considered unsolicited. The term is a Portmanteau, compound of the words "spam" and "trap", because a spam analyst will lay out spamtraps to catch spam in the same way that a fur trapper lays out traps to catch wild animals. The provenance of this term is unknown, but several competing anti-spam organizations claim trademark over it. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Honeypot (computing)
In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site which contains information or resources of value to attackers. It is actually isolated, monitored, and capable of blocking or analyzing the attackers. This is similar to police sting operations, colloquially known as "baiting" a suspect. Types Honeypots can be classified based on their deployment (use/action) and based on their level of involvement. Based on deployment, honeypots may be classified as: * production honeypots * research honeypots Production honeypots are easy to use, capture only limited information, and are used primarily by corporations. Production honeypots are placed inside the production network with other production servers by an organization to improve their overa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-spam Techniques (e-mail)
Various anti-spam techniques are used to prevent email spam (unsolicited bulk email). No technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate email (false positives) as opposed to not rejecting all spam email (false negatives) – and the associated costs in time, effort, and cost of wrongfully obstructing good mail. Anti-spam techniques can be broken into four broad categories: those that require actions by individuals, those that can be automated by email administrators, those that can be automated by email senders and those employed by researchers and law enforcement officials. End-user techniques There are a number of techniques that individuals can use to restrict the availability of their email addresses, with the goal of reducing their chance of receiving spam. Discretion Sharing an email address only among a limited group of correspondents is one way to limit the chance that the address will be "harveste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stopping E-mail Abuse
Various anti-spam techniques are used to prevent email spam (unsolicited bulk email). No technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate email (false positives) as opposed to not rejecting all spam email (false negatives) – and the associated costs in time, effort, and cost of wrongfully obstructing good mail. Anti-spam techniques can be broken into four broad categories: those that require actions by individuals, those that can be automated by email administrators, those that can be automated by email senders and those employed by researchers and law enforcement officials. End-user techniques There are a number of techniques that individuals can use to restrict the availability of their email addresses, with the goal of reducing their chance of receiving spam. Discretion Sharing an email address only among a limited group of correspondents is one way to limit the chance that the address will be "harveste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Portmanteau
A portmanteau word, or portmanteau (, ) is a blend of wordsGarner's Modern American Usage , p. 644. in which parts of multiple words are combined into a new word, as in ''smog'', coined by blending ''smoke'' and ''fog'', or ''motel'', from ''motor'' and ''hotel''. In , a portmanteau is a single morph that is analyzed as representing two (or more) underlying s. When portmanteaus shorten es ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Opt-in Email
Opt-in email is a term used when someone is not initially added to an emailing list and is instead given the option to join the emailing list. Typically, this is some sort of mailing list, newsletter, or advertising. Opt-out emails do not ask for permission to send emails, these emails are typically criticized as unsolicited bulk emails, better known as spam. Forms There are several common forms of opt-in email: Unconfirmed opt-in/single opt-in Someone first gives an email address to the list software (for instance, on a Web page), but no steps are taken to make sure that this address belongs to the person submitting it. This can cause email from the mailing list to be considered spam because simple typos of the email address can cause the email to be sent to someone else. Malicious subscriptions are also possible, as are subscriptions that are due to spammers forging email addresses that are sent to the email address used to subscribe to the mailing list. Confirmed o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backscatter (e-mail)
Backscatter (also known as outscatter, misdirected bounces, blowback or collateral spam) is incorrectly automated bounce messages sent by mail servers, typically as a side effect of incoming spam. Recipients of such messages see them as a form of unsolicited bulk email or spam, because they were not solicited by the recipients, are substantially similar to each other, and are delivered in bulk quantities. Systems that generate email backscatter may be listed on various email blacklists and may be in violation of internet service providers' Terms of Service. Backscatter occurs because worms and spam messages often forge their sender addresses. Instead of simply rejecting a spam message, a misconfigured mail server sends a bounce message to such a forged address. This normally happens when a mail server is configured to relay a message to an after-queue processing step, for example, an antivirus scan or spam check, which then fails, and at the time the antivirus scan or spam check ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Usenet
Usenet () is a worldwide distributed discussion system available on computers. It was developed from the general-purpose Unix-to-Unix Copy (UUCP) dial-up network architecture. Tom Truscott and Jim Ellis conceived the idea in 1979, and it was established in 1980.''From Usenet to CoWebs: interacting with social information spaces'', Christopher Lueg, Danyel Fisher, Springer (2003), , Users read and post messages (called ''articles'' or ''posts'', and collectively termed ''news'') to one or more topic categories, known as newsgroups. Usenet resembles a bulletin board system (BBS) in many respects and is the precursor to the Internet forums that have become widely used. Discussions are threaded, as with web forums and BBSs, though posts are stored on the server sequentially.The jargon file v4.4.7 , Jargon File Archive. [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
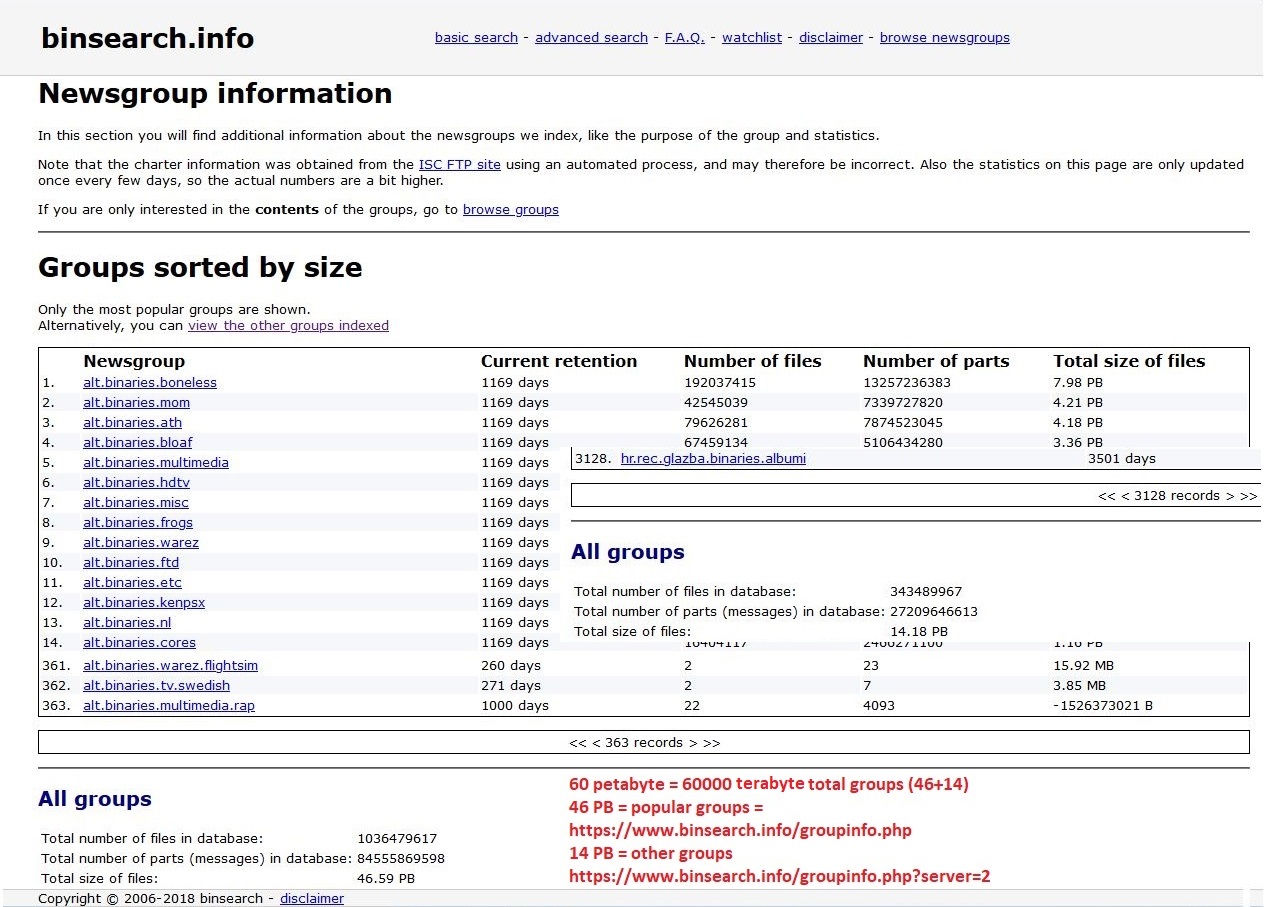
Newsgroup
A Usenet newsgroup is a repository usually within the Usenet system, for messages posted from users in different locations using the Internet. They are discussion groups and are not devoted to publishing news. Newsgroups are technically distinct from, but functionally similar to, discussion forums on the World Wide Web. Newsreader software is used to read the content of newsgroups. Before the adoption of the World Wide Web, Usenet newsgroups were among the most popular Internet services, and have retained their noncommercial nature in contrast to the increasingly ad-laden web. In recent years, this form of open discussion on the Internet has lost considerable ground to individually-operated browser-accessible forums and big media social networks such as Facebook and Twitter. Communication is facilitated by the Network News Transfer Protocol (NNTP) which allows connection to Usenet servers and data transfer over the internet. Similar to another early (yet still used) protocol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam (electronic)
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, for the purpose of non-commercial proselytizing, for any prohibited purpose (especially the fraudulent purpose of phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyingly sing "Spam" repeatedly. Spamming remains economically viable because advertisers have no ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Newsgroup Charter
A charter is the grant of authority or rights, stating that the granter formally recognizes the prerogative of the recipient to exercise the rights specified. It is implicit that the granter retains superiority (or sovereignty), and that the recipient admits a limited (or inferior) status within the relationship, and it is within that sense that charters were historically granted, and it is that sense which is retained in modern usage of the term. The word entered the English language from the Old French ''charte'', via Latin ''charta'', and ultimately from Greek χάρτης (''khartes'', meaning "layer of papyrus"). It has come to be synonymous with a document that sets out a grant of rights or privileges. Other usages The term is used for a special case (or as an exception) of an institutional charter. A charter school, for example, is one that has different rules, regulations, and statutes from a state school. Charter can be used as a synonym for "hire" or "lease", as in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Project Honey Pot
Project Honey Pot is a web-based honeypot network operated by Unspam Technologies, Inc. It uses software embedded in web sites. It collects information about the IP addresses used when harvesting e-mail addresses in spam, bulk mailing, and other e-mail fraud. The project solicits the donation of unused MX entries from domain owners. In 2007, the Project began a number of new initiatives including a QuickLinks program that makes it easier for more people to participate, as well as a system to track comment spam. The Project has also launched a free new service called http:BL, which leverages the data to allow website administrators to keep malicious web robots off their sites. In addition to collecting information, which is made available on a "top 25" list at periodic intervals, the project organizers also help various law enforcement agencies combat private and commercial unsolicited bulk mailing offenses and, overall, work to reduce the amount of spam being sent and rec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Address Munging
Address munging is the practice of disguising an e-mail address to prevent it from being automatically collected by unsolicited bulk e-mail providers. Address munging is intended to disguise an e-mail address in a way that prevents computer software from seeing the real address, or even any address at all, but still allows a human reader to reconstruct the original and contact the author: an email address such as, "no-one@example.com", becomes "no-one at example dot com", for instance. Any e-mail address posted in public is likely to be automatically collected by computer software used by bulk emailers (a process known as e-mail address scavenging). Addresses posted on webpages, Usenet or chat rooms are particularly vulnerable to this. Private e-mail sent between individuals is highly unlikely to be collected, but e-mail sent to a mailing list that is archived and made available via the web, or passed onto a Usenet news server and made public, may eventually be scanned and collec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)
.jpg)