|
Scrypt
In cryptography, scrypt (pronounced "ess crypt") is a password-based key derivation function created by Colin Percival in March 2009, originally for the Tarsnap online backup service. The algorithm was specifically designed to make it costly to perform large-scale custom hardware attacks by requiring large amounts of memory. In 2016, the scrypt algorithm was published by Internet Engineering Task Force, IETF as RFC 7914. A simplified version of scrypt is used as a proof-of-work scheme by a number of Cryptocurrency, cryptocurrencies, first implemented by an anonymous programmer called ArtForz in Tenebrix and followed by Fairbrix and Litecoin soon after. Introduction A password-based key derivation function (password-based KDF) is generally designed to be computationally intensive, so that it takes a relatively long time to compute (say on the order of several hundred milliseconds). Legitimate users only need to perform the function once per operation (e.g., authentication), a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Proof-of-work
Proof of work (also written as proof-of-work, an abbreviated PoW) is a form of Cryptography, cryptographic proof (truth), proof in which one party (the ''prover'') proves to others (the ''verifiers'') that a certain amount of a specific computational effort has been expended. Verifiers can subsequently confirm this expenditure with minimal effort on their part. The concept was first implemented in Hashcash by Moni Naor and Cynthia Dwork in 1993 as a way to deter denial-of-service attacks and other service abuses such as spam (electronic), spam on a network by requiring some work from a service requester, usually meaning processing time by a computer. The term "proof of work" was first coined and formalized in a 1999 paper by Markus Jakobsson and Ari Juels. The concept was adapted to digital tokens by Hal Finney (computer scientist), Hal Finney in 2004 through the idea of "reusable proof of work" using the 160-bit secure hash algorithm 1 (SHA-1). Proof of work was later popularized ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Litecoin
Litecoin (Abbreviation: LTC; sign: Ł) is a decentralized peer-to-peer cryptocurrency and open-source software project released under the MIT/X11 license. Inspired by Bitcoin, Litecoin was the second cryptocurrency starting in October 2011. In technical details, the Litecoin main chain shares a slightly modified Bitcoin codebase. The practical effects of those codebase differences are lower transaction fees, faster transaction confirmations, and faster mining difficulty retargeting. Due to its underlying similarities to Bitcoin, Litecoin has historically been referred to as the "silver to Bitcoin's gold."Ismail, Ashiana. "Permissioned blockchains for real world applications." PhD diss., 2020. In 2022, Litecoin added optional privacy features via soft Fork (blockchain), fork through the MWEB (MimbleWimble extension block) upgrade. History Pre-Litecoin By 2011, Bitcoin mining was largely General-purpose computing on graphics processing units, performed by GPUs. This raised conc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Bcrypt
bcrypt is a password-hashing function designed by Niels Provos and David Mazières. It is based on the Blowfish (cipher), Blowfish cipher and presented at USENIX in 1999. Besides incorporating a salt (cryptography), salt to protect against rainbow table attacks, bcrypt is an adaptive function: over time, the iteration count can be increased to make it slower, so it remains resistant to brute-force search attacks even with increasing computation power. The bcrypt function is the default password hash algorithm for OpenBSD, and was the default for some Linux distributions such as SUSE Linux. There are implementations of bcrypt in C (programming language), C, C++, C Sharp (programming language), C#, Embarcadero Delphi, Elixir (programming language), Elixir, Go (programming language), Go, Java (programming language), Java, JavaScript, Perl, PHP, Ruby (programming language), Ruby, Python (programming language), Python, Rust (programming language), Rust,V (programming language), V ( ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Dogecoin
Dogecoin ( or , Abbreviation: DOGE; sign: Ð) is a cryptocurrency created by software engineers Billy Markus and Jackson Palmer, who decided to create a payment system as a joke, making fun of the wild speculation in cryptocurrencies at the time. It is considered both the first " meme coin", and more specifically the first "dog coin". Despite its satirical nature, some consider it a legitimate investment prospect. Dogecoin features the face of Kabosu from the " doge" meme as its logo and namesake.''A History of Dogecoin'' . Dogecoin Analysis Report. Social Science Research Network (SSRN). Accessed December 28, 2017. It was introduced on December 6, 2013, and quickly developed its own |
Colin Percival
Colin A. Percival (born 1980) is a Canadian computer scientist and computer security researcher. He completed his undergraduate education at Simon Fraser University and a doctorate at the University of Oxford. While at university he joined the FreeBSD project, and achieved some notoriety for discovering a security weakness in Intel's hyper-threading technology. Besides his work in delta compression and the introduction of memory-hard functions, he is also known for developing the Tarsnap online backup service, which became his full-time job. Education Percival began taking mathematics courses at Simon Fraser University (SFU) at age 13, as a student at Burnaby Central Secondary School. He graduated from Burnaby Central and officially enrolled at SFU in 1998. At SFU he studied number theory under Peter Borwein, and competed in the William Lowell Putnam Mathematical Competition, placing in the top 15 in 1998 and as a Putnam Fellow (in the top six) in 1999. From 1998 to 2000 he ran t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Salsa20
Salsa20 and the closely related ChaCha are stream ciphers developed by Daniel J. Bernstein. Salsa20, the original cipher, was designed in 2005, then later submitted to the eSTREAM European Union cryptographic validation process by Bernstein. ChaCha is a modification of Salsa20 published in 2008. It uses a new round function that increases diffusion and increases performance on some architectures. Both ciphers are built on a pseudorandom function based on add–rotate–XOR (ARX) operations — 32-bit addition, bitwise addition (XOR) and rotation operations. The core function maps a 256-bit key, a 64-bit nonce, and a 64-bit counter to a 512-bit block of the key stream (a Salsa version with a 128-bit key also exists). This gives Salsa20 and ChaCha the unusual advantage that the user can efficiently seek to any position in the key stream in constant time. Salsa20 offers speeds of around 4–14 cycles per byte in software on modern x86 processors, and reasonable hardware perfo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
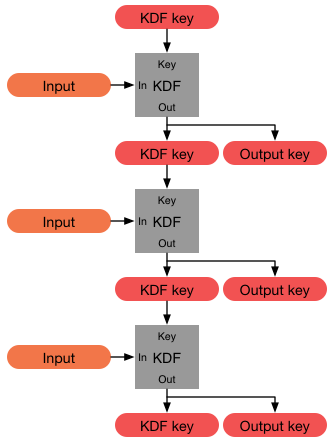
Key Derivation Function
In cryptography, a key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation. History The first deliberately slow (key stretching) password-based key derivation function was called "crypt" (or "crypt(3)" after its man page), and was invented by Robert Morris in 1978. It would encrypt a constant (zero), using the first 8 characters of the user's password as the key, by performing 25 iterations of a modified DES encryption algorithm (in which a 12-b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Ccrypt
ccrypt is a utility for the secure encryption and decryption of files and streams. It was designed as a replacement for the standard UNIX crypt utility, which is notorious for using a very weak encryption algorithm. ccrypt is based on the Rijndael cypher, the same cipher used in the AES standard. However, in the AES standard a 128-bit block size is used, whereas ccrypt uses a 256-bit block size. ccrypt commonly uses the .cpt file extension for encrypted files. ccrypt does not provide an authenticated encryption scheme and therefore does not protect the integrity of encrypted data. See also * bcrypt * crypt (Unix) * mcrypt * scrypt In cryptography, scrypt (pronounced "ess crypt") is a password-based key derivation function created by Colin Percival in March 2009, originally for the Tarsnap online backup service. The algorithm was specifically designed to make it costly t ... References External links ccrypt homepage Cryptographic software {{crypto-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Crypt (Unix)
In Unix computing, crypt or enigma is a utility program used for encryption. Due to the ease of breaking it, it is considered to be obsolete. The program is usually used as a filter, and it has traditionally been implemented using a "rotor machine" algorithm based on the Enigma machine. It is considered to be cryptographically far too weak to provide any security against brute-force attacks by modern, commodity personal computers. Some versions of Unix shipped with an even weaker version of the ''crypt(1)'' command in order to comply with contemporaneous laws and regulations that limited the exportation of cryptographic software. Some of these were simply implementations of the Caesar cipher (effectively no more secure than ROT13, which is implemented as a Caesar cipher with a well-known key). History Cryptographer Robert Morris wrote a M-209-based , which first appeared in Version 3 Unix, to encourage codebreaking experiments; Morris managed to break by hand. Dennis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Crypt (C)
crypt is a C POSIX librar, POSIX C library function. It is typically used to compute the cryptographic hash function, hash of user account passwords. The function outputs a text string which also code, encodes the salt (cryptography), salt (usually the first two characters are the salt itself and the rest is the hashed result), and identifies the hash algorithm used Detailing to the Traditional one explained be This output string forms a password which is usually stored in a text file. More formally, crypt provides cryptographic key derivation functions for password validation and storage on Unix systems. Relationship to Unix crypt utility There is an unrelated Crypt (Unix), crypt utility in Unix, which is often confused with the C library function. To distinguish between the two, writers often refer to the utility program as ''crypt(1)'', because it is documented in section 1 of the Unix Manual page (Unix), manual pages, and refer to the C library function as ''crypt(3)'', be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Password Hashing Competition
The Password Hashing Competition was an open competition announced in 2013 to select one or more password hash functions that can be recognized as a recommended standard. It was modeled after the successful Advanced Encryption Standard process and NIST hash function competition, but directly organized by cryptographers and security practitioners. On 20 July 2015, Argon2 was selected as the final PHC winner, with special recognition given to four other password hashing schemes: Catena, Lyra2, yescrypt and Makwa. One goal of the Password Hashing Competition was to raise awareness of the need for strong password hash algorithms, hopefully avoiding a repeat of previous password breaches involving weak or no hashing, such as the ones involving RockYou (2009), JIRA, Gawker (2010), PlayStation Network outage, Battlefield Heroes (2011), eHarmony, LinkedIn, Adobe, ASUS, South Carolina Department of Revenue (2012), Evernote, Ubuntu Forums (2013), etc. Danielle Walker"Black Hat: Crack ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Argon2
Argon2 is a key derivation function that was selected as the winner of the 2015 Password Hashing Competition. It was designed by Alex Biryukov, Daniel Dinu, and Dmitry Khovratovich from the University of Luxembourg. The reference implementation of Argon2 is released under a Creative Commons CC0 license (i.e. public domain) or the Apache License, Apache License 2.0, and provides three related versions: *Argon2d maximizes resistance to GPU Password cracking, cracking attacks. It accesses the memory array in a password dependent order, which reduces the possibility of time–memory trade-off (TMTO) attacks, but introduces possible side-channel attacks. *Argon2i is optimized to resist side-channel attacks. It accesses the memory array in a password independent order. *Argon2id is a hybrid version. It follows the Argon2i approach for the first half pass over memory and the Argon2d approach for subsequent passes. recommends using Argon2id if you do not know the difference between the t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |