|
Crypt (C)
crypt is a POSIX C library function. It is typically used to compute the hash of user account passwords. The function outputs a text string which also encodes the salt (usually the first two characters are the salt itself and the rest is the hashed result), and identifies the hash algorithm used (defaulting to the "traditional" one explained below). This output string forms a password record, which is usually stored in a text file. More formally, crypt provides cryptographic key derivation functions for password validation and storage on Unix systems. Relationship to Unix crypt utility There is an unrelated crypt utility in Unix, which is often confused with the C library function. To distinguish between the two, writers often refer to the utility program as ''crypt(1)'', because it is documented in section 1 of the Unix manual pages, and refer to the C library function as ''crypt(3)'', because its documentation is in manual section 3. Details This same ''crypt'' functio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C POSIX Library
The C POSIX library is a specification of a C standard library for POSIX systems. It was developed at the same time as the ANSI C ANSI C, ISO C, and Standard C are successive standards for the C programming language published by the American National Standards Institute (ANSI) and ISO/IEC JTC 1/SC 22/WG 14 of the International Organization for Standardization (ISO) and th ... standard. Some effort was made to make POSIX compatible with standard C; POSIX includes additional functions to those introduced in standard C. C POSIX library header files References Official List of headers in the POSIX library on opengroup.org* Further reading * {{CProLang POSIX ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Encryption Standard
The Data Encryption Standard (DES ) is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography. Developed in the early 1970s at IBM and based on an earlier design by Horst Feistel, the algorithm was submitted to the National Bureau of Standards (NBS) following the agency's invitation to propose a candidate for the protection of sensitive, unclassified electronic government data. In 1976, after consultation with the National Security Agency (NSA), the NBS selected a slightly modified version (strengthened against differential cryptanalysis, but weakened against brute-force attacks), which was published as an official Federal Information Processing Standard (FIPS) for the United States in 1977. The publication of an NSA-approved encryption standard led to its quick international adoption and widespread academic scruti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
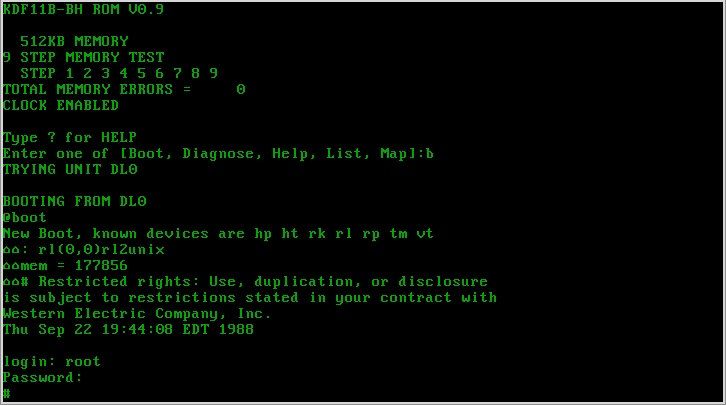
/etc/passwd
passwd is a command on Unix, Plan 9, Inferno, and most Unix-like operating systems used to change a user's password. The password entered by the user is run through a key derivation function to create a hashed version of the new password, which is saved. Only the hashed version is stored; the entered password is not saved for security reasons. When the user logs on, the password entered by the user during the log on process is run through the same key derivation function and the resulting hashed version is compared with the saved version. If the hashes are identical, the entered password is considered to be correct, and the user is authenticated. In theory, it is possible for two different passwords to produce the same hash. However, cryptographic hash functions are designed in such a way that finding any password that produces the same hash is very difficult and practically infeasible, so if the produced hash matches the stored one, the user can be authenticated. The passwd ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dictionary Attack
In cryptanalysis and computer security, a dictionary attack is an attack using a restricted subset of a keyspace to defeat a cipher or authentication mechanism by trying to determine its decryption key or passphrase, sometimes trying thousands or millions of likely possibilities often obtained from lists of past security breaches. Technique A dictionary attack is based on trying all the strings in a pre-arranged listing. Such attacks originally used words found in a dictionary (hence the phrase ''dictionary attack''); however, now there are much larger lists available on the open Internet containing hundreds of millions of passwords recovered from past data breaches. There is also cracking software that can use such lists and produce common variations, such as substituting numbers for similar-looking letters. A dictionary attack tries only those possibilities which are deemed most likely to succeed. Dictionary attacks often succeed because many people have a tendency to choose sh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Known Plaintext
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib), and its encrypted version (ciphertext). These can be used to reveal further secret information such as secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Base64
In computer programming, Base64 is a group of binary-to-text encoding schemes that represent binary data (more specifically, a sequence of 8-bit bytes) in sequences of 24 bits that can be represented by four 6-bit Base64 digits. Common to all binary-to-text encoding schemes, Base64 is designed to carry data stored in binary formats across channels that only reliably support text content. Base64 is particularly prevalent on the World Wide Web where one of its uses is the ability to embed image files or other binary assets inside textual assets such as HTML and CSS files. Base64 is also widely used for sending e-mail attachments. This is required because SMTP – in its original form – was designed to transport 7-bit ASCII characters only. This encoding causes an overhead of 33–37% (33% by the encoding itself; up to 4% more by the inserted line breaks). Design Each Base64 digit can take on 64 different values, encoding 6 bits of data. Which characters are chosen to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Seventh Edition Unix
Seventh Edition Unix, also called Version 7 Unix, Version 7 or just V7, was an important early release of the Unix operating system. V7, released in 1979, was the last Bell Laboratories release to see widespread distribution before the commercialization of Unix by AT&T Corporation in the early 1980s. V7 was originally developed for Digital Equipment Corporation's PDP-11 minicomputers and was later ported to other platforms. Overview Unix versions from Bell Labs were designated by the edition of the user's manual with which they were accompanied. Released in 1979, the Seventh Edition was preceded by Sixth Edition, which was the first version licensed to commercial users. Development of the Research Unix line continued with the Eighth Edition, which incorporated development from 4.1BSD, through the Tenth Edition, after which the Bell Labs researchers concentrated on developing Plan 9. V7 was the first readily portable version of Unix. As this was the era of minicomputers, with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password
A password, sometimes called a passcode (for example in Apple devices), is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services that a typical individual accesses can make memorization of unique passwords for each service impractical. Using the terminology of the NIST Digital Identity Guidelines, the secret is held by a party called the ''claimant'' while the party verifying the identity of the claimant is called the ''verifier''. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity. In general, a password is an arbitrary string of characters including letters, digits, or other symbols. If the permissible characters are constrained to be numeric, the corresponding secret is sometimes called a personal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
M-209
In cryptography, the M-209, designated CSP-1500 by the United States Navy (C-38 by the manufacturer) is a portable, mechanical cipher machine used by the US military primarily in World War II, though it remained in active use through the Korean War. The M-209 was designed by Swedish cryptographer Boris Hagelin in response to a request for such a portable cipher machine, and was an improvement of an earlier machine, the C-36. The M-209 is about the size of a lunchbox, in its final form measuring and weighing (plus for the case). It represented a brilliant achievement for pre-electronic technology. It was a rotor machine similar to a telecipher machine, such as the Lorenz cipher and the Geheimfernschreiber. Basic operation Basic operation of the M-209 is relatively straightforward. Six adjustable ''key wheels'' on top of the box each display a letter of the alphabet. These six wheels comprise the external key for the machine, providing an initial state, similar to an initial ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Yescrypt
The Password Hashing Competition was an open competition announced in 2013 to select one or more password hash functions that can be recognized as a recommended standard. It was modeled after the successful Advanced Encryption Standard process and NIST hash function competition, but directly organized by cryptographers and security practitioners. On 20 July 2015, Argon2 was selected as the final PHC winner, with special recognition given to four other password hashing schemes: Catena, Lyra2, yescrypt and Makwa. One goal of the Password Hashing Competition was to raise awareness of the need for strong password hash algorithms, hopefully avoiding a repeat of previous password breaches involving weak or no hashing, such as the ones involving RockYou (2009), JIRA, Gawker (2010), PlayStation Network outage, Battlefield Heroes (2011), eHarmony, LinkedIn, Adobe, ASUS, South Carolina Department of Revenue (2012), Evernote, Ubuntu Forums (2013), etc. Danielle Walker"Black Hat: Cracka ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHA-1
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographically broken but still widely used hash function which takes an input and produces a 160-bit (20- byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard. Since 2005, SHA-1 has not been considered secure against well-funded opponents; as of 2010 many organizations have recommended its replacement. NIST formally deprecated use of SHA-1 in 2011 and disallowed its use for digital signatures in 2013, and declared that it should be phased out by 2030. , chosen-prefix attacks against SHA-1 are practical. As such, it is recommended to remove SHA-1 from products as soon as possible and instead use SHA-2 or SHA-3. Replacing SHA-1 is urgent where it is used for digital signatures. All major web browser vendors ceased acceptance of SHA-1 SSL certificates in 2017. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PBKDF1
In cryptography, PBKDF1 and PBKDF2 (Password-Based Key Derivation Function 1 and 2) are key derivation functions with a sliding computational cost, used to reduce vulnerabilities of brute-force attacks. PBKDF2 is part of RSA Laboratories' Public-Key Cryptography Standards (PKCS) series, specifically PKCS#5 v2.0, also published as Internet Engineering Task Force's RFC2898. It supersedes PBKDF1, which could only produce derived keys up to 160 bits long. RFC8018 (PKCS#5 v2.1), published in 2017, recommends PBKDF2 for password hashing. Purpose and operation PBKDF2 applies a pseudorandom function, such as hash-based message authentication code (HMAC), to the input password or passphrase along with a salt value and repeats the process many times to produce a ''derived key'', which can then be used as a cryptographic key in subsequent operations. The added computational work makes password cracking much more difficult, and is known as key stretching. When the standard was written ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |