|
Sandboxed
In computer security, a sandbox is a security mechanism for separating running programs, usually in an effort to mitigate system failures and/or software Vulnerability (computing), vulnerabilities from spreading. The isolation metaphor is taken from the idea of children who do not play well together, so each is given their own sandpit , sandbox to play in alone. It is often used to execute untested or untrusted programs or code, possibly from unverified or untrusted third parties, suppliers, users or websites, without risking harm to the host machine or operating system. A sandbox typically provides a tightly controlled set of resources for guest programs to run in, such as storage and memory scratch space. Network access, the ability to inspect the host system, or read from input devices are usually disallowed or heavily restricted. In the sense of providing a highly controlled environment, sandboxes may be seen as a specific example of virtualization. Sandboxing is frequently ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google Chrome
Google Chrome is a cross-platform web browser developed by Google. It was first released in 2008 for Microsoft Windows, built with free software components from Apple WebKit and Mozilla Firefox. Versions were later released for Linux, macOS, iOS, and also for Android, where it is the default browser. The browser is also the main component of ChromeOS, where it serves as the platform for web applications. Most of Chrome's source code comes from Google's free and open-source software project ''Chromium'', but Chrome is licensed as proprietary freeware. WebKit was the original rendering engine, but Google eventually forked it to create the Blink engine; all Chrome variants except iOS now use Blink. , StatCounter estimates that Chrome has a 67% worldwide browser market share (after peaking at 72.38% in November 2018) on personal computers (PC), is most used on tablets (having surpassed Safari), and is also dominant on smartphones and at 65% across all platforms combined. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mac App Store
The App Store (also known as the Mac App Store) is a digital distribution platform for macOS apps, often referred to as Mac apps, created and maintained by Apple Inc. The platform was announced on October 20, 2010, at Apple's "Back to the Mac" event. Apple began accepting app submissions from registered developers on November 3, 2010, in preparation for its launch. The Mac App Store was launched on January 6, 2011, as part of the free Mac OS X 10.6.6 update for all current Snow Leopard users. After 24 hours of release, Apple announced that there were over one million downloads. Regulations Like the App Store on iOS and iPadOS, the Mac App Store is regulated by Apple. To submit an app for consideration, the developer must be a member of the Apple Developer Program. As of June 2019, the membership fee is US$99 a year. Apps must be approved by Apple before becoming available on the store. Disallowed types of apps revealed by Apple include apps that: * change the native user int ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
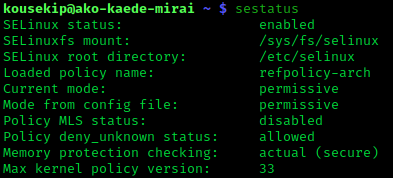
SELinux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allows ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribution, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apple Inc
Apple Inc. is an American multinational technology company headquartered in Cupertino, California, United States. Apple is the largest technology company by revenue (totaling in 2021) and, as of June 2022, is the world's biggest company by market capitalization, the fourth-largest personal computer vendor by unit sales and second-largest mobile phone manufacturer. It is one of the Big Five American information technology companies, alongside Alphabet, Amazon, Meta, and Microsoft. Apple was founded as Apple Computer Company on April 1, 1976, by Steve Wozniak, Steve Jobs and Ronald Wayne to develop and sell Wozniak's Apple I personal computer. It was incorporated by Jobs and Wozniak as Apple Computer, Inc. in 1977 and the company's next computer, the Apple II, became a best seller and one of the first mass-produced microcomputers. Apple went public in 1980 to instant financial success. The company developed computers featuring innovative graphical user inter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trojan Virus
In computing, a Trojan horse is any malware that misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. Trojans generally spread by some form of social engineering; for example, where a user is duped into executing an email attachment disguised to appear innocuous (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller who can then have unauthorized access to the affected computer. Ransomware attacks are often carried out using a Trojan. Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Use of the term It's not clear where or when the concept, and this term for it, was first used, but by 1971 the first Unix manual assumed it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Hosting
Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name. The term virtual hosting is usually used in reference to web servers but the principles do carry over to other Internet services. One widely used application is shared web hosting. The price for shared web hosting is lower than for a dedicated web server because many customers can be hosted on a single server. It is also very common for a single entity to want to use multiple names on the same machine so that the names can reflect services offered rather than where those services happen to be hosted. There are two main types of virtual hosting, name-based and IP-based. Name-based virtual hosting uses the host name presented by the client. This saves IP addresses and the associated administrat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating-system-level Virtualization
OS-level virtualization is an operating system (OS) paradigm in which the kernel allows the existence of multiple isolated user space instances, called ''containers'' ( LXC, Solaris containers, Docker, Podman), ''zones'' (Solaris containers), ''virtual private servers'' (OpenVZ), ''partitions'', ''virtual environments'' (VEs), ''virtual kernels'' (DragonFly BSD), or ''jails'' (FreeBSD jail or chroot jail). Such instances may look like real computers from the point of view of programs running in them. A computer program running on an ordinary operating system can see all resources (connected devices, files and folders, network shares, CPU power, quantifiable hardware capabilities) of that computer. However, programs running inside of a container can only see the container's contents and devices assigned to the container. On Unix-like operating systems, this feature can be seen as an advanced implementation of the standard chroot mechanism, which changes the apparent root folder ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Emulator
In computing, an emulator is Computer hardware, hardware or software that enables one computer system (called the ''host'') to behave like another computer system (called the ''guest''). An emulator typically enables the host system to run software or use peripheral devices designed for the guest system. Emulation refers to the ability of a computer program in an electronic device to emulate (or imitate) another program or device. Many Printer (computing), printers, for example, are designed to emulate Hewlett-Packard, HP LaserJet printers because so much software is written for HP printers. If a non-HP printer emulates an HP printer, any software written for a real HP printer will also run in the non-HP printer emulation and produce equivalent printing. Since at least the 1990s, many video game enthusiasts and hobbyists have used emulators to play classic arcade games from the 1980s using the games' original 1980s machine code and data, which is interpreted by a current-era s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Machine
In computing, a virtual machine (VM) is the virtualization/emulation of a computer system. Virtual machines are based on computer architectures and provide functionality of a physical computer. Their implementations may involve specialized hardware, software, or a combination. Virtual machines differ and are organized by their function, shown here: * '' System virtual machines'' (also termed full virtualization VMs) provide a substitute for a real machine. They provide functionality needed to execute entire operating systems. A hypervisor uses native execution to share and manage hardware, allowing for multiple environments which are isolated from one another, yet exist on the same physical machine. Modern hypervisors use hardware-assisted virtualization, virtualization-specific hardware, primarily from the host CPUs. * Process virtual machines are designed to execute computer programs in a platform-independent environment. Some virtual machine emulators, such as QEMU and video ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google
Google LLC () is an American multinational technology company focusing on search engine technology, online advertising, cloud computing, computer software, quantum computing, e-commerce, artificial intelligence, and consumer electronics. It has been referred to as "the most powerful company in the world" and one of the world's most valuable brands due to its market dominance, data collection, and technological advantages in the area of artificial intelligence. Its parent company Alphabet is considered one of the Big Five American information technology companies, alongside Amazon, Apple, Meta, and Microsoft. Google was founded on September 4, 1998, by Larry Page and Sergey Brin while they were PhD students at Stanford University in California. Together they own about 14% of its publicly listed shares and control 56% of its stockholder voting power through super-voting stock. The company went public via an initial public offering (IPO) in 2004. In 2015, Google was reor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows 10 Pro
Windows 10 has several editions, all with varying feature sets, use cases, or intended devices. Certain editions are distributed only on devices directly from an original equipment manufacturer (OEM), while editions such as ''Enterprise'' and ''Education'' are only available through volume licensing channels. Microsoft also makes editions of Windows 10 available to device manufacturers for use on specific classes of devices, including IoT devices and previously marketed Windows 10 Mobile for smartphones. Baseline editions Baseline editions are the only editions available as standalone purchases in retail outlets. PCs often come pre-installed with one of these editions. ; : Windows 10 Home is designed for use in PCs, tablets and 2-in-1 PCs. It includes all features directed at ''consumers''. ; : Windows 10 Pro includes all features of Windows 10 Home, with additional capabilities that are oriented towards ''professionals'' and ''business environments'', such as Active Direct ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |