|
Sudo
() is a shell (computing), shell command (computing), command on Unix-like operating systems that enables a user to run a program with the security privileges of another user, by default the superuser. It originally stood for "superuser do", as that was all it did, and this remains its most common usage; however, the official Sudo project page lists it as "su 'do. The current Linux manual pages define as "substitute user", making the correct meaning of "substitute user, do", because can run a command as other users as well. Unlike the similar command Su (Unix), su, users must, by default, supply their own password for authentication, rather than the password of the target user. After authentication, and if the configuration file (typically #Configuration, /etc/sudoers) permits the user access, the system invokes the requested command. The configuration file offers detailed access permissions, including enabling commands only from the invoking terminal; requiring a password p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Sudo Warning
() is a shell command on Unix-like operating systems that enables a user to run a program with the security privileges of another user, by default the superuser. It originally stood for "superuser do", as that was all it did, and this remains its most common usage; however, the official Sudo project page lists it as "su 'do. The current Linux manual pages define as "substitute user", making the correct meaning of "substitute user, do", because can run a command as other users as well. Unlike the similar command su, users must, by default, supply their own password for authentication, rather than the password of the target user. After authentication, and if the configuration file (typically /etc/sudoers) permits the user access, the system invokes the requested command. The configuration file offers detailed access permissions, including enabling commands only from the invoking terminal; requiring a password per user or group; requiring re-entry of a password every time or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Superuser
In computing, the superuser is a special user account used for system administration. Depending on the operating system (OS), the actual name of this account might be root, administrator, admin or supervisor. In some cases, the actual name of the account is not the determining factor; on Unix-like systems, for example, the user with a user identifier (UID) of zero is the superuser .e., uid=0 regardless of the name of that account; and in systems which implement a r model, any user with the role of superuser (or its synonyms) can carry out all actions of the superuser account. The principle of least privilege recommends that most users and applications run under an ordinary account to perform their work, as a superuser account is capable of making unrestricted, potentially adverse, system-wide changes. Unix and Unix-like In Unix-like computer OSes (such as Linux), ''root'' is the conventional name of the user who has all rights or permissions (to all files and programs) in all mod ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Su (Unix)
The Unix command , which stands for "substitute user" (or historically "superuser"), is used by a computer user to execute commands with the privileges of another user account. When executed it invokes a shell (Unix), shell without changing the current working directory or the user environment. When the command is used without specifying the new user id as a Command line#Arguments, command line argument, it defaults to using the superuser account (user id 0) of the system. History The command , including the Unix permissions system and the setuid system call, was part of Version 1 Unix. Encrypted passwords appeared in Version 3 Unix, Version 3. The command is available as a separate package for Microsoft Windows as part of the UnxUtils collection of Native (computing), native Windows API, Win32 porting, ports of common GNU Unix-like utilities. The command was removed from GNU_Core_Utilities, GNU coreutils as of release 8.18 (2012-08-12) and is currently included in the util-l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
OpenBSD
OpenBSD is a security-focused operating system, security-focused, free software, Unix-like operating system based on the Berkeley Software Distribution (BSD). Theo de Raadt created OpenBSD in 1995 by fork (software development), forking NetBSD 1.0. The OpenBSD project emphasizes software portability, portability, software standard, standardization, software bug, correctness, proactive computer security, security, and integrated cryptography. The OpenBSD project maintains portable versions of many subsystems as package manager, packages for other operating systems. Because of the project's preferred BSD license, which allows binary redistributions without the source code, many components are reused in proprietary and corporate-sponsored software projects. The firewall (computing), firewall code in Apple Inc., Apple's macOS is based on OpenBSD's PF (firewall), PF firewall code, Android (operating system), Android's Bionic (software), Bionic C standard library is based on OpenBSD c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Role-based Access Control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users, and to implementing mandatory access control (MAC) or discretionary access control, discretionary access control (DAC). Role-based access control is a policy-neutral access control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations. RBAC can be used to facilitate administration of security in large organizations with hundreds of users and thousands of permissions. Although RBAC is different from MAC and DAC access control frameworks, it can enforce these policies without any complication. Design Within an organization, role (computer science), roles are created for various job functions. The permiss ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
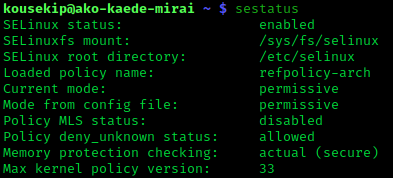
SELinux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allows th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
File Locking
File locking is a mechanism that restricts access to a computer file, or to a region of a file, by allowing only one user or process to modify or delete it at a specific time, and preventing reading of the file while it's being modified or deleted. Systems implement locking to prevent an ''interceding update'' scenario, which is an example of a race condition, by enforcing the serialization of update processes to any given file. The following example illustrates the interceding update problem: # Process A reads a customer record from a file containing account information, including the customer's account balance and phone number. # Process B now reads the same record from the same file, so it has its own copy. # Process A changes the account balance in its copy of the customer record and writes the record back to the file. # Process B, which still has the original ''stale'' value for the account balance in its copy of the customer record, updates the account balance and writes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
MacOS
macOS, previously OS X and originally Mac OS X, is a Unix, Unix-based operating system developed and marketed by Apple Inc., Apple since 2001. It is the current operating system for Apple's Mac (computer), Mac computers. Within the market of Desktop computer, desktop and laptop computers, it is the Usage share of operating systems#Desktop and laptop computers, second most widely used desktop OS, after Microsoft Windows and ahead of all Linux distributions, including ChromeOS and SteamOS. , the most recent release of macOS is MacOS Sequoia, macOS 15 Sequoia, the 21st major version of macOS. Mac OS X succeeded classic Mac OS, the primary Mac operating systems, Macintosh operating system from 1984 to 2001. Its underlying architecture came from NeXT's NeXTSTEP, as a result of NeXT#1997–2006: Acquisition by Apple, Apple's acquisition of NeXT, which also brought Steve Jobs back to Apple. The first desktop version, Mac OS X 10.0, was released on March 24, 2001. Mac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Xkcd
''xkcd'' is a serial webcomic created in 2005 by American author Randall Munroe. Sometimes styled ''XKCD'', the comic's tagline describes it as "a webcomic of romance, sarcasm, math, and language". Munroe states on the comic's website that the name of the comic is not an acronym but "just a word with no phonetic pronunciation". The subject matter of the comic varies from statements on life and love to Mathematical joke, mathematical, Programming language, programming, and science, scientific in-jokes. Some strips feature simple humor or pop-culture references. It has a cast of stick figures, and the comic occasionally features landscapes, graphs, charts, and intricate mathematical patterns such as fractals. New cartoons are added three times a week, on Mondays, Wednesdays, and Fridays, with few exceptions. Munroe has released six spin-off (media), spinoff books from the comic. The first book, published in 2010 and titled ''xkcd: volume 0'', was a series of select comics from h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Linux Distribution
A Linux distribution, often abbreviated as distro, is an operating system that includes the Linux kernel for its kernel functionality. Although the name does not imply product distribution per se, a distro—if distributed on its own—is often obtained via a website intended specifically for the purpose. Distros have been designed for a wide variety of systems ranging from personal computers (for example, Linux Mint) to servers (for example, Red Hat Enterprise Linux) and from embedded devices (for example, OpenWrt) to supercomputers (for example, Rocks Cluster Distribution). A distro typically includes many components in addition to the Linux kernel. Commonly, it includes a package manager, an init system (such as systemd, OpenRC, or runit), GNU tools and libraries, documentation, IP network configuration utilities, the getty TTY setup program, and many more. To provide a desktop experience (most commonly the Mesa userspace graphics drivers) a display server (the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Easter Egg (media)
An Easter egg is a message, image, or feature hidden in software, a video game, a film, or another—usually electronic—medium. The term used in this manner was coined around 1979 by Steve Wright, the then-Director of Software Development in the Atari Consumer Division, to describe a hidden message in the Atari video game ''Adventure (Atari 2600), Adventure'', in reference to an egg hunt, Easter egg hunt. The earliest known video game Easter egg is in the 1973 video game ''Lunar Lander (video game genre)#Graphical games, Moonlander'', in which the player tries to land a Lunar module on Moon, the Moon; if the player opts to fly the module horizontally through several of the game's screens, they encounter a McDonald's restaurant, and if they land next to it, the astronaut will visit it instead of standing next to the ship. The earliest known Easter egg in software in general is one placed in the "make" command for PDP-6/PDP-10 computers sometime in October 1967–October 1968, wh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |