|
Software Regression
A software regression is a type of software bug where a feature that has worked before stops working. This may happen after changes are applied to the software's source code, including the addition of new features and bug fixes. They may also be introduced by changes to the environment in which the software is running, such as system upgrades, system patching or a change to daylight saving time. A software performance regression is a situation where the software still functions correctly, but performs more slowly or uses more memory or resources than before. Various types of software regressions have been identified in practice, including the following: * ''Local'' – a change introduces a new bug in the changed module or component. * ''Remote'' – a change in one part of the software breaks functionality in another module or component. * ''Unmasked'' – a change unmasks an already existing bug that had no effect before the change. Regressions are often caused by encompassed b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Bug
A software bug is an error, flaw or fault (technology), fault in the design, development, or operation of computer software that causes it to produce an incorrect or unexpected result, or to behave in unintended ways. The process of finding and correcting bugs is termed "debugging" and often uses formal techniques or tools to pinpoint bugs. Since the 1950s, some computer systems have been designed to deter, detect or auto-correct various computer bugs during operations. Bugs in software can arise from mistakes and errors made in interpreting and extracting users' requirements, planning a program's software architecture, design, writing its source code, and from interaction with humans, hardware and programs, such as operating systems or Library (computing), libraries. A program with many, or serious, bugs is often described as ''buggy''. Bugs can trigger errors that may have ripple effects. The effects of bugs may be subtle, such as unintended text formatting, through to more o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Variance
In probability theory and statistics, variance is the expectation of the squared deviation of a random variable from its population mean or sample mean. Variance is a measure of dispersion, meaning it is a measure of how far a set of numbers is spread out from their average value. Variance has a central role in statistics, where some ideas that use it include descriptive statistics, statistical inference, hypothesis testing, goodness of fit, and Monte Carlo sampling. Variance is an important tool in the sciences, where statistical analysis of data is common. The variance is the square of the standard deviation, the second central moment of a distribution, and the covariance of the random variable with itself, and it is often represented by \sigma^2, s^2, \operatorname(X), V(X), or \mathbb(X). An advantage of variance as a measure of dispersion is that it is more amenable to algebraic manipulation than other measures of dispersion such as the expected absolute deviatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Profiling (computer Programming)
In software engineering, profiling ("program profiling", "software profiling") is a form of dynamic program analysis that measures, for example, the space (memory) or time complexity of a program, the usage of particular instructions, or the frequency and duration of function calls. Most commonly, profiling information serves to aid program optimization, and more specifically, performance engineering. Profiling is achieved by instrumenting either the program source code or its binary executable form using a tool called a ''profiler'' (or ''code profiler''). Profilers may use a number of different techniques, such as event-based, statistical, instrumented, and simulation methods. Gathering program events Profilers use a wide variety of techniques to collect data, including hardware interrupts, code instrumentation, instruction set simulation, operating system hooks, and performance counters. Use of profilers The output of a profiler may be: * A statistical '' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data-flow Analysis
In computing, dataflow is a broad concept, which has various meanings depending on the application and context. In the context of software architecture, data flow relates to stream processing or reactive programming. Software architecture Dataflow computing is a software paradigm based on the idea of representing computations as a directed graph, where nodes are computations and data flow along the edges. Dataflow can also be called stream processing or reactive programming. There have been multiple data-flow/stream processing languages of various forms (see Stream processing). Data-flow hardware (see Dataflow architecture) is an alternative to the classic von Neumann architecture. The most obvious example of data-flow programming is the subset known as reactive programming with spreadsheets. As a user enters new values, they are instantly transmitted to the next logical "actor" or formula for calculation. Distributed data flows have also been proposed as a programming a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
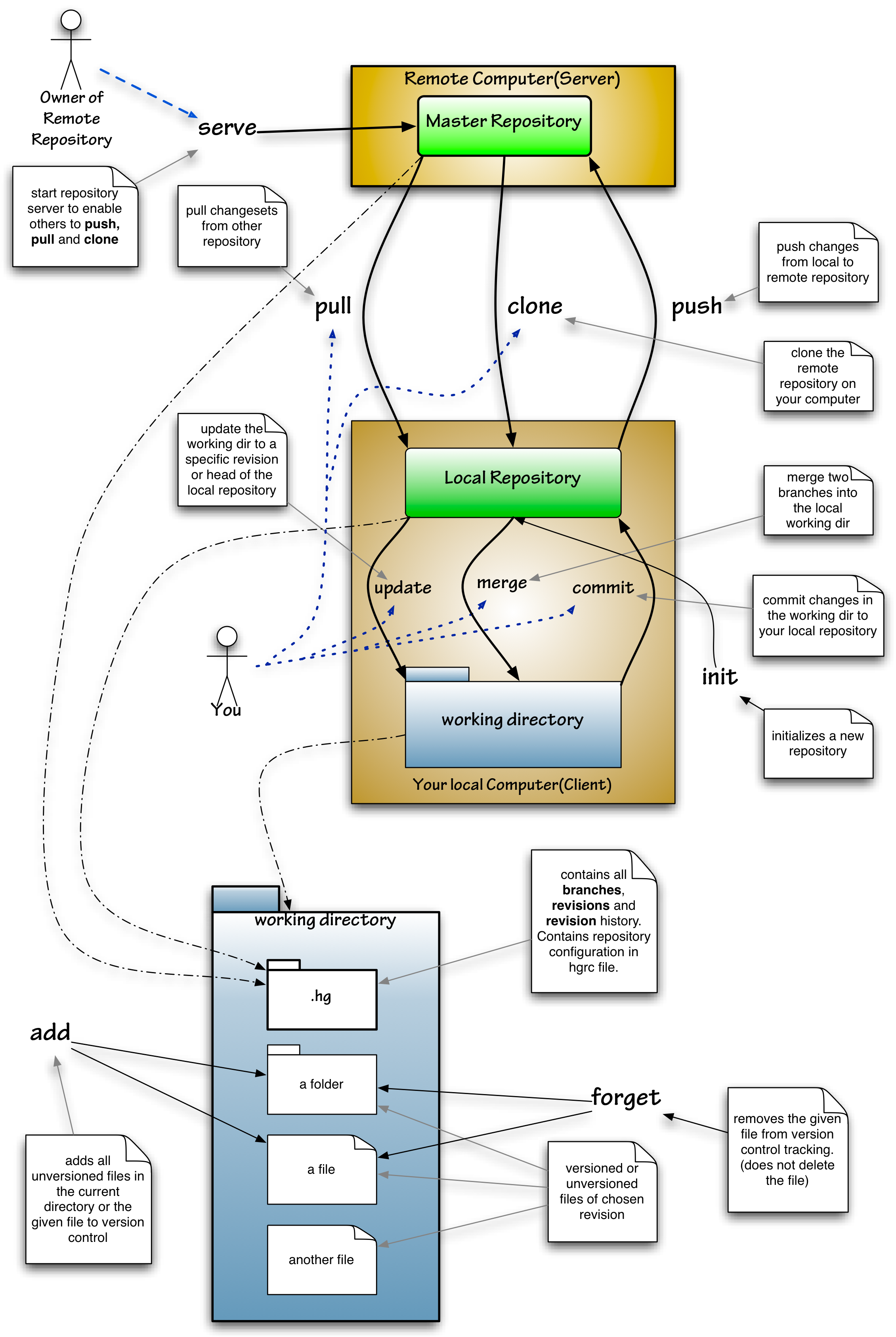
Mercurial
Mercurial is a distributed revision control tool for software developers. It is supported on Microsoft Windows and Unix-like systems, such as FreeBSD, macOS, and Linux. Mercurial's major design goals include high performance and scalability, decentralization, fully distributed collaborative development, robust handling of both plain text and binary files, and advanced branching and merging capabilities, while remaining conceptually simple. It includes an integrated web-interface. Mercurial has also taken steps to ease the transition for users of other version control systems, particularly Subversion. Mercurial is primarily a command-line driven program, but graphical user interface extensions are available, e.g. TortoiseHg, and several IDEs offer support for version control with Mercurial. All of Mercurial's operations are invoked as arguments to its driver program hg (a reference to Hg – the chemical symbol of the element mercury). Olivia Mackall originated Mercu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Version Control
In software engineering, version control (also known as revision control, source control, or source code management) is a class of systems responsible for managing changes to computer programs, documents, large web sites, or other collections of information. Version control is a component of software configuration management. Changes are usually identified by a number or letter code, termed the "revision number", "revision level", or simply "revision". For example, an initial set of files is "revision 1". When the first change is made, the resulting set is "revision 2", and so on. Each revision is associated with a timestamp and the person making the change. Revisions can be compared, restored, and, with some types of files, merged. The need for a logical way to organize and control revisions has existed for almost as long as writing has existed, but revision control became much more important, and complicated, when the era of computing began. The numbering of book editions ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bisection (software Engineering)
Bisection is a method used in software development to identify change sets that result in a specific behavior change. It is mostly employed for finding the patch that introduced a bug. Another application area is finding the patch that indirectly fixed a bug. Overview The process of locating the changeset that introduced a specific regression was described as "source change isolation" in 1997 by Brian Ness and Viet Ngo of Cray Research. Regression testing was performed on Cray's compilers in editions comprising one or more changesets. Editions with known regressions could not be validated until developers addressed the problem. Source change isolation narrowed the cause to a single changeset that could then be excluded from editions, unblocking them with respect to this problem, while the author of the change worked on a fix. Ness and Ngo outlined linear search and binary search methods of performing this isolation. Code bisection has the goal of minimizing the effort to fi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Program Slicing
In computer programming, program slicing is the computation of the set of program statements, the program slice, that may affect the values at some point of interest, referred to as a slicing criterion. Program slicing can be used in debugging to locate source of errors more easily. Other applications of slicing include software maintenance, optimization, program analysis, and information flow control. Slicing techniques have been seeing a rapid development since the original definition by Mark Weiser. At first, slicing was only static, i.e., applied on the source code with no other information than the source code. Bogdan Korel and Janusz Laski introduced ''dynamic slicing'', which works on a specific execution of the program (for a given execution trace). Other forms of slicing exist, for instance path slicing. Static slicing Based on the original definition of Weiser, informally, a static program slice S consists of all statements in program P that may affect the value of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Breakpoint
In software development, a breakpoint is an intentional stopping or pausing place in a program, put in place for debugging purposes. It is also sometimes simply referred to as a pause. More generally, a breakpoint is a means of acquiring knowledge about a program during its execution. During the interruption, the programmer inspects the test environment (general purpose registers, memory, logs, files, etc.) to find out whether the program is functioning as expected. In practice, a breakpoint consists of one or more conditions that determine when a program's execution should be interrupted. Breakpoints were invented for ENIAC, one of the earliest digital computers, by programmer Betty Holberton. In the initial design of ENIAC, program flow was set by plugging cables from one unit to another. To make the program stop at a certain point, a cable was removed, called a ''breakpoint''. Machine breakpoints Early mainframe computers, such as the IBM/360, had console switches/dial ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lint (software)
Lint, or a linter, is a static code analysis tool used to flag programming errors, bugs, stylistic errors and suspicious constructs. The term originates from a Unix utility that examined C language source code. History Stephen C. Johnson, a computer scientist at Bell Labs, came up with lint in 1978 while debugging the yacc grammar he was writing for C and dealing with portability issues stemming from porting Unix to a 32-bit machine. The term "lint" was derived from lint, the name for the tiny bits of fiber and fluff shed by clothing, as the command should act like the lint trap in a clothes dryer, detecting small errors to great effect. In 1979, lint was used outside of Bell Labs for the first time, in the seventh version ( V7) of Unix. Over the years, different versions of lint have been developed for many C and C++ compilers, and while modern-day compilers have lint-like functions, lint-like tools have also advanced their capabilities. For example, Gimpel's PC-Lint, intro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Change Impact Analysis
Change impact analysis (IA) or impact analysis is the analysis of changes within a deployed product or application and their potential consequences. Change impact analysis is defined by Bohnner and Arnold as "identifying the potential consequences of a change, or estimating what needs to be modified to accomplish a change", and they focus on IA in terms of scoping changes within the details of a design. In contrast, Pfleeger and Atlee focus on the risks associated with changes and state that IA is: "the evaluation of the many risks associated with the change, including estimates of the effects on resources, effort, and schedule". Both the design details and risks associated with modifications are critical to performing IA within the change management processes. A technical colloquial term is also mentioned sometimes in this context, dependency hell. Types of impact analysis techniques IA techniques can be classified into three types: * Trace * Dependency * Experiential Bohne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Code Repository
In version control systems, a repository is a data structure that stores metadata for a set of files or directory structure. Depending on whether the version control system in use is distributed, like Git or Mercurial, or centralized, like Subversion, CVS CVS may refer to: Organizations * CVS Health, a US pharmacy chain ** CVS Pharmacy ** CVS Caremark, a prescription benefit management subsidiary * Council for Voluntary Service, England * Cable Video Store, former US pay-per-view service * CVS F ..., or Perforce, the whole set of information in the repository may be duplicated on every user's system or may be maintained on a single server. Some of the metadata that a repository contains includes, among other things, a historical record of changes in the repository, a set of commit objects, and a set of references to commit objects, called ''heads''. The main purpose of a repository is to store a set of files, as well as the history of changes made to those files. Exactly ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |



.png)