|
Modem Dialer
A dialer (American English) or dialler (British English) is an electronic device that is connected to a telephone line to monitor the dialed numbers and alter them to seamlessly provide services that otherwise require lengthy National or International access codes to be dialed. A dialer automatically inserts and modifies the numbers depending on the time of day, country or area code dialed, allowing the user to subscribe to the service providers who offer the best rates. For example, a dialer could be programmed to use one service provider for international calls and another for cellular calls. This process is known as prefix insertion or least cost routing. A line powered dialer does not need any external power but instead takes the power it needs from the telephone line. Another type of dialer is a computer program which creates a connection to the Internet or another computer network over the analog telephone or Integrated Services Digital Network (ISDN). Many operating system ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
American English
American English, sometimes called United States English or U.S. English, is the set of varieties of the English language native to the United States. English is the most widely spoken language in the United States and in most circumstances is the de facto common language used in government, education and commerce. Since the 20th century, American English has become the most influential form of English worldwide. American English varieties include many patterns of pronunciation, vocabulary, grammar and particularly spelling that are unified nationwide but distinct from other English dialects around the world. Any American or Canadian accent perceived as lacking noticeably local, ethnic or cultural markers is popularly called "General" or "Standard" American, a fairly uniform accent continuum native to certain regions of the U.S. and associated nationally with broadcast mass media and highly educated speech. However, historical and present linguistic evidence does not sup ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
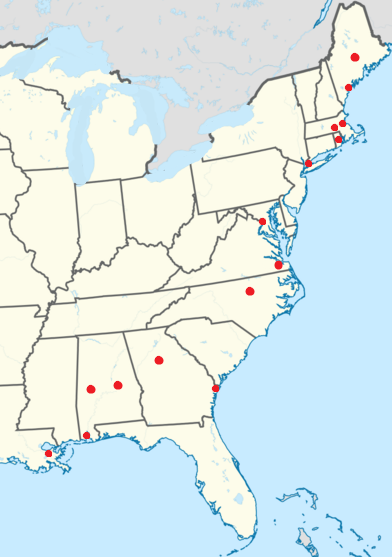
Avaya
Avaya Holdings Corp., often shortened to Avaya (), is an American multinational technology company headquartered in Durham, North Carolina, that provides cloud communications and workstream collaboration services. The company's platform includes unified communications (UCaaS), contact center other services. The company provides services to 220,000 customer locations in 190 countries. History In 1995, Lucent Technologies was spun off from AT&T, and Lucent subsequently spun off units of its own in an attempt to restructure its struggling operations. ">/sup> Avaya was then spun off from Lucent as its own company in 2000 (Lucent merged with Alcatel SA in 2006, becoming Alcatel-Lucent, which was purchased in turn by Nokia in 2016). It remained a public company from 2000 to 2007. In October 2007, Avaya was acquired by two private-equity firms, TPG Capital and Silver Lake Partners, for $8.2 billion. On January 19, 2017, Avaya filed for Chapter 11 bankruptcy. On December ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Subscriber Line
Digital subscriber line (DSL; originally digital subscriber loop) is a family of technologies that are used to transmit digital data over telephone lines. In telecommunications marketing, the term DSL is widely understood to mean asymmetric digital subscriber line (ADSL), the most commonly installed DSL technology, for Internet access. DSL service can be delivered simultaneously with wired telephone service on the same telephone line since DSL uses higher frequency bands for data. On the customer premises, a DSL filter on each non-DSL outlet blocks any high-frequency interference to enable simultaneous use of the voice and DSL services. The bit rate of consumer DSL services typically ranges from 256 kbit/s to over 100 Mbit/s in the direction to the customer ( downstream), depending on DSL technology, line conditions, and service-level implementation. Bit rates of 1 Gbit/s have been reached. In ADSL, the data throughput in the upstream direction (the dire ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keygen
A key generator (key-gen) is a computer program that generates a product licensing key, such as a serial number, necessary to activate for use of a software application. Keygens may be legitimately distributed by software manufacturers for licensing software in commercial environments where software has been licensed in bulk for an entire site or enterprise, or they may be distributed illegitimately in circumstances of copyright infringement or software piracy. Illegitimate key generators are typically distributed by software crackers in the warez scene and demoscene. These keygens often play "Keygen music", which may include the genres dubstep or chiptunes in the background and have artistic user interfaces. Software licensing A software license is a legal instrument that governs the usage and distribution of computer software. Often, such licenses are enforced by implementing in the software a product activation or digital rights management (DRM) mechanism, seeking to prev ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Crack
Software cracking (known as "breaking" mostly in the 1980s) is the modification of software to remove or disable features which are considered undesirable by the person cracking the software (software cracker), especially copy protection features (including protection against the manipulation of software, serial number, hardware key, date checks and disc check) or software annoyances like nag screens and adware. A crack refers to the means of achieving, for example a stolen serial number or a tool that performs that act of cracking. Some of these tools are called keygen, patch, loader, or no-disc crack. A keygen is a handmade product serial number generator that often offers the ability to generate working serial numbers in your own name. A patch is a small computer program that modifies the machine code of another program. This has the advantage for a cracker to not include a large executable in a release when only a few bytes are changed. A loader modifies the startup ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Black Hat Hacking
A Black Hat (Black Hat Hacker or Blackhat) is a computer hacker who usually violates laws or typical ethical standards. The term originates from the 1950s westerns, when bad guys typically wore black hats and good guys white hats. Black hat hackers aim to hack into any system for their own profit or out of malice. Black hat is contrasted with white hat. A third category is sometimes added, the gray hat, who hacks with good intentions but at times without permission. History The terms "Black hat" come from the color scheme used in westerns from the 1950s, in which the bad guys wore black hats, and the good guys wore white or other light colors. Criminals who intentionally enter computer networks are known as "black hat hackers". They may also distribute malware that steals passwords, credit card numbers, and other personal information, holds computers hostage, or destroys files. Even though hacking has become an important tool for governments to gather intelligence, Black Hats ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pornography
Pornography (often shortened to porn or porno) is the portrayal of sexual subject matter for the exclusive purpose of sexual arousal. Primarily intended for adults,"Kids Need Porn Literacy" – Marty Klein, ''Psychology Today'', 30 October 2016 pornography is presented in a variety of media, including magazines, art, , |
Trojan Horse (computing)
In computing, a Trojan horse is any malware that misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. Trojans generally spread by some form of social engineering; for example, where a user is duped into executing an email attachment disguised to appear innocuous (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller who can then have unauthorized access to the affected computer. Ransomware attacks are often carried out using a Trojan. Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Use of the term It's not clear where or when the concept, and this term for it, was first used, but by 1971 the first Unix manual assumed it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Piracy
Piracy is an act of robbery or criminal violence by ship or boat-borne attackers upon another ship or a coastal area, typically with the goal of stealing cargo and other valuable goods. Those who conduct acts of piracy are called pirates, vessels used for piracy are pirate ships. The earliest documented instances of piracy were in the 14th century BC, when the Sea Peoples, a group of ocean raiders, attacked the ships of the Aegean and Mediterranean civilisations. Narrow channels which funnel shipping into predictable routes have long created opportunities for piracy, as well as for privateering and commerce raiding. Historic examples include the waters of Gibraltar, the Strait of Malacca, Madagascar, the Gulf of Aden, and the English Channel, whose geographic structures facilitated pirate attacks. The term ''piracy'' generally refers to maritime piracy, although the term has been generalized to refer to acts committed on land, in the air, on computer networks, and (in s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Security Vulnerability
Vulnerabilities are flaws in a computer system that weaken the overall security of the device/system. Vulnerabilities can be weaknesses in either the hardware itself, or the software that runs on the hardware. Vulnerabilities can be exploited by a threat actor, such as an attacker, to cross privilege boundaries (i.e. perform unauthorized actions) within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerabilities are also known as the attack surface. Vulnerability management is a cyclical practice that varies in theory but contains common processes which include: discover all assets, prioritize assets, assess or perform a complete vulnerability scan, report on results, remediate vulnerabilities, verify remediation - repeat. This practice generally refers to software vulnerabilities in computing systems. Agile vulnerability management refers preventing attacks ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Broadband Internet Access
Internet access is the ability of individuals and organizations to connect to the Internet using computer terminals, computers, and other devices; and to access services such as email and the World Wide Web. Internet access is sold by Internet service providers (ISPs) delivering connectivity at a wide range of data signaling rate, data transfer rates via various networking technologies. Many organizations, including a growing number of municipal entities, also provide cost-free wireless access and landlines. Availability of Internet access was once limited, but has grown rapidly. In 1995, only percent of the world's population had access, with well over half of those living in the United States, and consumer use was through dial-up Internet access, dial-up. By the first decade of the 21st century, many consumers in developed nations used faster broadband technology, and by 2014, 41 percent of the world's population had access, broadband was almost ubiquitous worldwide, and glob ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
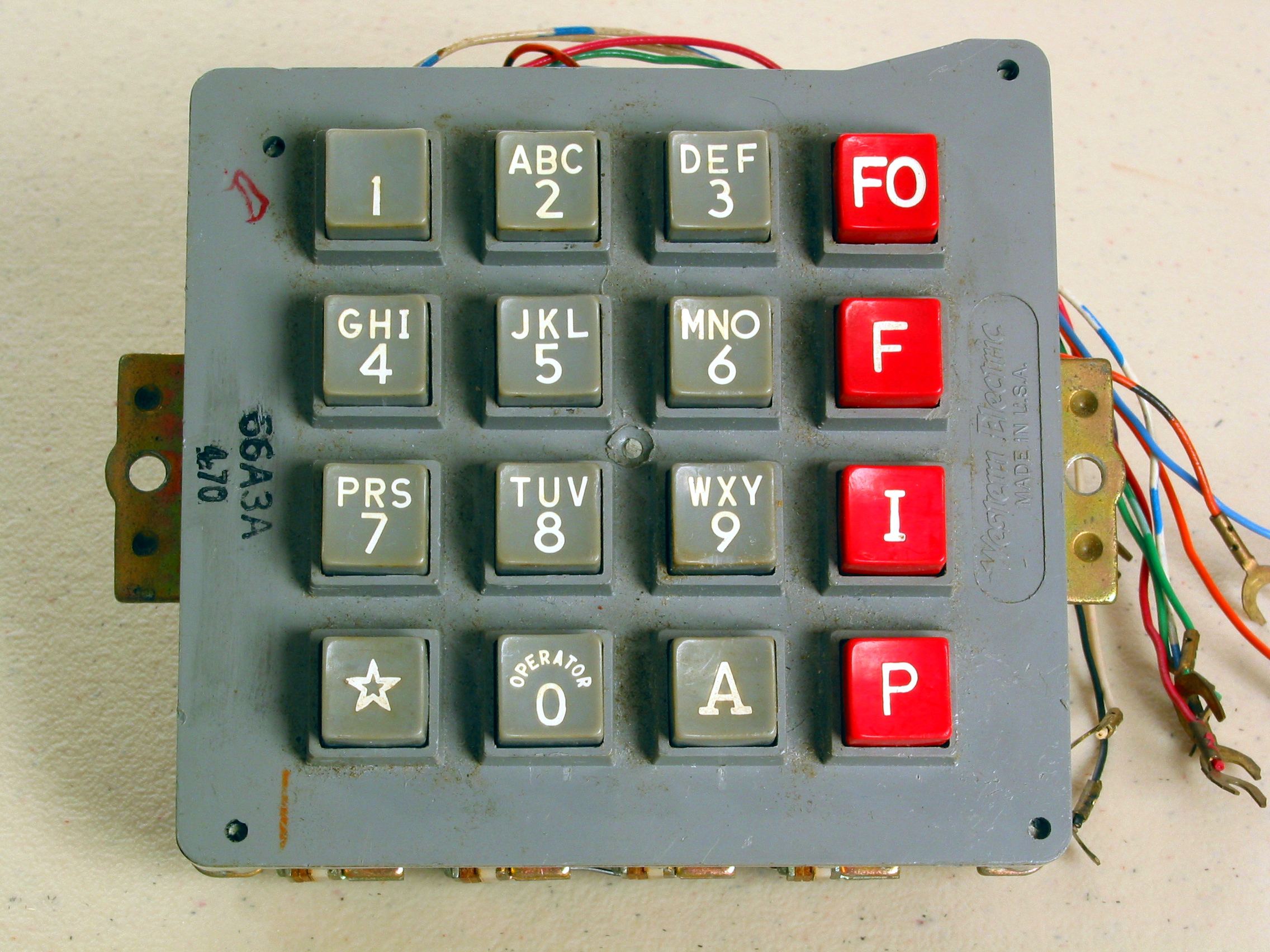
Dual-tone Multi-frequency Signaling
Dual-tone multi-frequency signaling (DTMF) is a telecommunication signaling system using the voice-frequency band over telephone lines between telephone equipment and other communications devices and switching centers. DTMF was first developed in the Bell System in the United States, and became known under the trademark Touch-Tone for use in push-button telephones supplied to telephone customers, starting in 1963. DTMF is standardized as ITU-T Recommendation Q.23. It is also known in the UK as ''MF4''. The Touch-Tone system using a telephone keypad gradually replaced the use of rotary dial and has become the industry standard for landline and mobile service. Other multi-frequency systems are used for internal signaling within the telephone network. Multifrequency signaling Before the development of DTMF, telephone numbers were dialed by users with a loop-disconnect (LD) signaling, more commonly known as pulse dialing (dial pulse, DP) in the United States. It functions by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |