|
Latency (engineering)
Latency, from a general point of view, is a time delay between the cause and the effect of some physical change in the system being observed. Lag, as it is known in gaming circles, refers to the latency between the input to a simulation and the visual or auditory response, often occurring because of network delay in online games. Latency is physically a consequence of the limited velocity at which any physical interaction can propagate. The magnitude of this velocity is always less than or equal to the speed of light. Therefore, every physical system with any physical separation (distance) between cause and effect will experience some sort of latency, regardless of the nature of the stimulation at which it has been exposed to. The precise definition of latency depends on the system being observed or the nature of the simulation. In communications, the lower limit of latency is determined by the medium being used to transfer information. In reliable two-way communication syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Causality
Causality (also referred to as causation, or cause and effect) is influence by which one event, process, state, or object (''a'' ''cause'') contributes to the production of another event, process, state, or object (an ''effect'') where the cause is partly responsible for the effect, and the effect is partly dependent on the cause. In general, a process has many causes, which are also said to be ''causal factors'' for it, and all lie in its past. An effect can in turn be a cause of, or causal factor for, many other effects, which all lie in its future. Some writers have held that causality is metaphysically prior to notions of time and space. Causality is an abstraction that indicates how the world progresses. As such a basic concept, it is more apt as an explanation of other concepts of progression than as something to be explained by others more basic. The concept is like those of agency and efficacy. For this reason, a leap of intuition may be needed to grasp it. Accordin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
New York Stock Exchange
The New York Stock Exchange (NYSE, nicknamed "The Big Board") is an American stock exchange in the Financial District of Lower Manhattan in New York City. It is by far the world's largest stock exchange by market capitalization of its listed companies at US$30.1 trillion as of February 2018. The average daily trading value was approximately 169 billion in 2013. The NYSE trading floor is at the New York Stock Exchange Building on 11 Wall Street and 18 Broad Street and is a National Historic Landmark. An additional trading room, at 30 Broad Street, was closed in February 2007. The NYSE is owned by Intercontinental Exchange, an American holding company that it also lists (). Previously, it was part of NYSE Euronext (NYX), which was formed by the NYSE's 2007 merger with Euronext. History The earliest recorded organization of securities trading in New York among brokers directly dealing with each other can be traced to the Buttonwood Agreement. Previously, securiti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Iperf
Iperf is a tool for network performance measurement and tuning. It is a cross-platform tool that can produce standardized performance measurements for any network. Iperf has client and server functionality, and can create data streams to measure the throughput between the two ends in one or both directions. Typical iperf output contains a time-stamped report of the amount of data transferred and the throughput measured. The data streams can be either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP): * ''UDP'': When used for testing UDP capacity, iperf allows the user to specify the datagram size and provides results for the datagram throughput and the packet loss. * ''TCP'': When used for testing TCP capacity, iperf measures the throughput of the payload. Iperf uses 1024 × 1024 for mebibytes and 1000 × 1000 for megabytes. Iperf is open-source software written in C, and it runs on various platforms including Linux, Unix and Windows (either natively or inside ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Netperf
Netperf is a software application that provides network bandwidth testing between two hosts on a network. It supports Unix domain sockets, TCP, SCTP, DLPI and UDP via BSD Sockets. Netperf provides a number of predefined tests e.g. to measure bulk (unidirectional) data transfer or request response performance. Netperf was originally developed at Hewlett Packard. See also * Nuttcp * Iperf * NetPIPE * bwping * Flowgrind * Measuring network throughput * Packet generation model A traffic generation model is a stochastic model of the traffic flows or data sources in a communication network, for example a cellular network or a computer network. A packet generation model is a traffic generation model of the packet flows or ... References {{reflist External linksHomepage of netperf Computer network analysis Network performance ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hping
hping is an open-source packet generator and analyzer for the TCP/IP protocol created by Salvatore Sanfilippo (also known as Antirez). It is one of the common tools used for security auditing and testing of firewalls and networks, and was used to exploit the idle scan scanning technique (also invented by the hping author), and now implemented in the Nmap Security Scanner. The new version of hping, hping3, is scriptable using the Tcl language and implements an engine for string based, human-readable description of TCP/IP packets so that the programmer can write scripts related to low level TCP/IP packet manipulation and analysis in a short time. See also {{Portal, Free and open-source software * Nmap Security Scanner: Nmap and hping are often considered complementary to one another. * Mausezahn: Another fast and versatile packet generator that also supports Ethernet header manipulation. * Packet Sender: A packet generator with a focus on ease of use. External linksThe Hping Web ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Traffic Shaping
Traffic shaping is a bandwidth management technique used on computer networks which delays some or all datagrams to bring them into compliance with a desired ''traffic profile''. Traffic shaping is used to optimize or guarantee performance, improve latency, or increase usable bandwidth for some kinds of packets by delaying other kinds. It is often confused with traffic policing, the distinct but related practice of packet dropping and packet marking. The most common type of traffic shaping is application-based traffic shaping. In application-based traffic shaping, fingerprinting tools are first used to identify applications of interest, which are then subject to shaping policies. Some controversial cases of application-based traffic shaping include bandwidth throttling of peer-to-peer file sharing traffic. Many application protocols use encryption to circumvent application-based traffic shaping. Another type of traffic shaping is route-based traffic shaping. Route-based traffi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Service Provider
An Internet service provider (ISP) is an organization that provides services for accessing, using, or participating in the Internet. ISPs can be organized in various forms, such as commercial, community-owned, non-profit, or otherwise privately owned. Internet services typically provided by ISPs can include Internet access, Internet transit, domain name registration, web hosting, Usenet service, and colocation. An ISP typically serves as the access point or the gateway that provides a user access to everything available on the Internet. Such a network can also be called as an eyeball network. History The Internet (originally ARPAnet) was developed as a network between government research laboratories and participating departments of universities. Other companies and organizations joined by direct connection to the backbone, or by arrangements through other connected companies, sometimes using dialup tools such as UUCP. By the late 1980s, a process was set in place towa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Router (computing)
A router is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions between networks and on the global Internet. Data sent through a network, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork (e.g. the Internet) until it reaches its destination node. A router is connected to two or more data lines from different IP networks. When a data packet comes in on one of the lines, the router reads the network address information in the packet header to determine the ultimate destination. Then, using information in its routing table or routing policy, it directs the packet to the next network on its journey. The most familiar type of IP routers are home and small office routers that simply forward IP packets between the home computers and the Internet. More sophisticated routers, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP. TCP is connection-oriented, and a connection between client and server is established before data can be sent. The server must be listening (passive open) for connection requests from clients before a connection is established. Three-way handshake (active open), retransmission, and error detection adds to reliability but lengthens latency. Applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address, for example, an error is indicated when a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). ICMP for IPv4 is defined in RFC 792. A separate ICMPv6, defined by RFC 4443, is used with IPv6. Technical details ICMP is part of the Internet protocol suite as defined in RFC 792. ICMP messages are typically used for diagnostic or control purposes or generated in response to errors in IP operations (as specified in RFC 1122 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
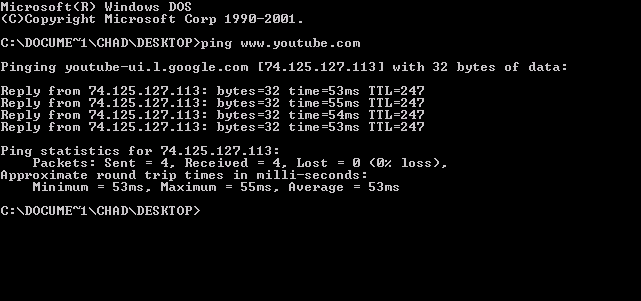
Ping (networking Utility)
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. The command-line options of the ping utility and its output vary between t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Round-trip Delay Time
In telecommunications, round-trip delay (RTD) or round-trip time (RTT) is the amount of time it takes for a signal to be sent ''plus'' the amount of time it takes for acknowledgement of that signal having been received. This time delay includes propagation times for the paths between the two communication endpoints. In the context of computer networks, the signal is typically a data packet. RTT is also known as ping time, and can be determined with the ping command. End-to-end delay is the length of time it takes for a signal to travel in one direction and is often approximated as half the RTT. Protocol design Round-trip delay and bandwidth are independent of each other. As the available bandwidth of networks increases, the round trip time does not similarly decrease, as it depends primarily on constant factors such as physical distance and the speed of signal propagation. Networks with both high bandwidth and a high RTT (and thus high bandwidth-delay product) can have very larg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |